282 Repositories
Python sql-injection-attacks Libraries

DDoS Script (DDoS Panel) with Multiple Bypass ( Cloudflare UAM,CAPTCHA,BFM,NOSEC / DDoS Guard / Google Shield / V Shield / Amazon / etc.. )
KARMA DDoS DDoS Script (DDoS Panel) with Multiple Bypass ( Cloudflare UAM,CAPTCHA,BFM,NOSEC / DDoS Guard / Google Shield / V Shield / Amazon / etc.. )

This repository contains the best Data Science free hand-picked resources to equip you with all the industry-driven skills and interview preparation kit.
Best Data Science Resources Hey, Data Enthusiasts out there! Finally, after lots of requests from the community I finally came up with the best free D
Write python locally, execute SQL in your data warehouse
RasgoQL Write python locally, execute SQL in your data warehouse ≪ Read the Docs · Join Our Slack » RasgoQL is a Python package that enables you to ea

Layer 7 DDoS Panel with Cloudflare Bypass ( UAM, CAPTCHA, BFM, etc.. )
Blood Deluxe DDoS DDoS Attack Panel includes CloudFlare Bypass (UAM, CAPTCHA, BFM, etc..)(It works intermittently. Working on it) Don't attack any web
Esse é o meu primeiro repo tratando de fim a fim, uma pipeline de dados abertos do governo brasileiro relacionado a compras de contrato e cronogramas anuais com spark, em pyspark e SQL!
Olá! Esse é o meu primeiro repo tratando de fim a fim, uma pipeline de dados abertos do governo brasileiro relacionado a compras de contrato e cronogr

automatically crawl every URL and find cross site scripting (XSS)
scancss Fastest tool to find XSS. scancss is a fastest tool to detect Cross Site scripting (XSS) automatically and it's also an intelligent payload ge
A utility that allows you to use DI in fastapi without Depends()
fastapi-better-di What is this ? fastapi-better-di is a utility that allows you to use DI in fastapi without Depends() Installation pip install fastap
Weakly Supervised Text-to-SQL Parsing through Question Decomposition
Weakly Supervised Text-to-SQL Parsing through Question Decomposition The official repository for the paper "Weakly Supervised Text-to-SQL Parsing thro
Makes it easier to write raw SQL in Python.
CoolSQL Makes it easier to write raw SQL in Python. Usage Quick Start from coolsql import Field name = Field("name") age = Field("age") condition =

Source code of our TTH paper: Targeted Trojan-Horse Attacks on Language-based Image Retrieval.
Targeted Trojan-Horse Attacks on Language-based Image Retrieval Source code of our TTH paper: Targeted Trojan-Horse Attacks on Language-based Image Re

Code for the CVPR2022 paper "Frequency-driven Imperceptible Adversarial Attack on Semantic Similarity"
Introduction This is an official release of the paper "Frequency-driven Imperceptible Adversarial Attack on Semantic Similarity" (arxiv link). Abstrac
An extension package of 🤗 Datasets that provides support for executing arbitrary SQL queries on HF datasets
datasets_sql A 🤗 Datasets extension package that provides support for executing arbitrary SQL queries on HF datasets. It uses DuckDB as a SQL engine
Spring Cloud Gateway 3.0.7 & 3.1.1 Code Injection (RCE)
Spring Cloud Gateway 3.0.7 & 3.1.1 Code Injection (RCE) CVE: CVE-2022-22947 CVSS: 10.0 (Vmware - https://tanzu.vmware.com/security/cve-2022-22947)

Universal Adversarial Examples in Remote Sensing: Methodology and Benchmark
Universal Adversarial Examples in Remote Sensing: Methodology and Benchmark Yong
BlockUnexpectedPackets - Preventing BungeeCord CPU overload due to Layer 7 DDoS attacks by scanning BungeeCord's logs
BlockUnexpectedPackets This script automatically blocks DDoS attacks that are sp

Dark Finix: All in one hacking framework with almost 100 tools
Dark Finix - Hacking Framework. Dark Finix is a all in one hacking framework wit

CVE-2022-23046 - SQL Injection Vulnerability on PhpIPAM v1.4.4
CVE-2022-23046 PhpIPAM v1.4.4 allows an authenticated admin user to inject SQL s
A type based dependency injection framework for Python 3.9+
Alluka A type based dependency injection framework for Python 3.9+. Installation You can install Alluka from PyPI using the following command in any P
This respository contains the source code of the printjack and phonejack attacks.
Printjack-Phonejack This repository contains the source code of the printjack and phonejack attacks. The Printjack directory contains the script to ca
Demonstrating attacks, mitigations, and monitoring on AWS
About Inspectaroo is a web app which allows users to upload images to view metadata. It is designed to show off many AWS services including EC2, Lambd
Definitive Guide to Creating a SQL Database on Cloud with AWS and Python
Definitive Guide to Creating a SQL Database on Cloud with AWS and Python An easy-to-follow comprehensive guide on integrating Amazon RDS, MySQL Workbe

Generate database table diagram from SQL data definition.
sql2diagram Generate database table diagram from SQL data definition. e.g. "CREATE TABLE ..." See Example below How does it works? Analyze the SQL to
Wifi-jammer - Continuously perform deauthentication attacks on all detectable stations
wifi-jammer Continuously perform deauthentication attacks on all detectable stat
This is an injection tool that can inject any xposed modules apk into the debug android app
This is an injection tool that can inject any xposed modules apk into the debug android app, the native code in the xposed module can also be injected.
AnonStress-Stored-XSS-Exploit - An exploit and demonstration on how to exploit a Stored XSS vulnerability in anonstress
AnonStress Stored XSS Exploit An exploit and demonstration on how to exploit a S
A data structure that extends pyspark.sql.DataFrame with metadata information.
MetaFrame A data structure that extends pyspark.sql.DataFrame with metadata info
Projeto de análise de dados com SQL
Project-Analizyng-International-Debt-Statistics- Projeto de análise de dados com SQL - Plataforma Data Camp Descrição do Projeto : Não é que nós human
The Social-Engineer Toolkit (SET) is specifically designed to perform advanced attacks against the human element.
The Social-Engineer Toolkit (SET) The Social-Engineer Toolkit (SET) is specifically designed to perform advanced attacks against the human element. SE

PySpark Structured Streaming ROS Kafka ApacheSpark Cassandra
PySpark-Structured-Streaming-ROS-Kafka-ApacheSpark-Cassandra The purpose of this project is to demonstrate a structured streaming pipeline with Apache

Beyond imagenet attack (accepted by ICLR 2022) towards crafting adversarial examples for black-box domains.
Beyond ImageNet Attack: Towards Crafting Adversarial Examples for Black-box Domains (ICLR'2022) This is the Pytorch code for our paper Beyond ImageNet

fastapi-admin2 is an upgraded fastapi-admin, that supports ORM dialects, true Dependency Injection and extendability
FastAPI2 Admin Introduction fastapi-admin2 is an upgraded fastapi-admin, that supports ORM dialects, true Dependency Injection and extendability. Now

Check out the StyleGAN repo and place it in the same directory hierarchy as the present repo
Variational Model Inversion Attacks Kuan-Chieh Wang, Yan Fu, Ke Li, Ashish Khisti, Richard Zemel, Alireza Makhzani Most commands are in run_scripts. W

Pytorch code for our paper Beyond ImageNet Attack: Towards Crafting Adversarial Examples for Black-box Domains)
Beyond ImageNet Attack: Towards Crafting Adversarial Examples for Black-box Domains (ICLR'2022) This is the Pytorch code for our paper Beyond ImageNet
Security system to prevent Shoulder Surfing Attacks
Surf_Sec Security system to prevent Shoulder Surfing Attacks. REQUIREMENTS: Python 3.6+ XAMPP INSTALLED METHOD TO CONFIGURE PROJECT: Clone the repo to

Neural Tangent Generalization Attacks (NTGA)
Neural Tangent Generalization Attacks (NTGA) ICML 2021 Video | Paper | Quickstart | Results | Unlearnable Datasets | Competitions | Citation Overview
SpyQL - SQL with Python in the middle
SpyQL SQL with Python in the middle Concept SpyQL is a query language that combines: the simplicity and structure of SQL with the power and readabilit
A notebook explaining the principle of adversarial attacks and their defences
TL;DR: A notebook explaining the principle of adversarial attacks and their defences Abstract: Deep neural networks models have been wildly successful
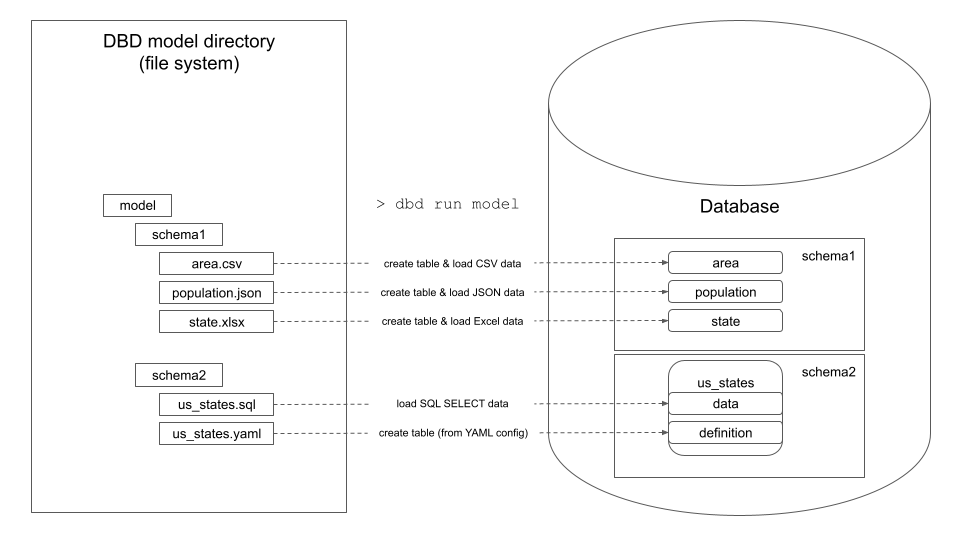
dbd is a database prototyping tool that enables data analysts and engineers to quickly load and transform data in SQL databases.
dbd: database prototyping tool dbd is a database prototyping tool that enables data analysts and engineers to quickly load and transform data in SQL d

ThorFI: A Novel Approach for Network Fault Injection as a Service
ThorFI: a Novel Approach for Network Fault Injection as a Service This repo includes ThorFI, a novel fault injection solution for virtual networks in
Use SQL query in a jupyter notebook!
SQL-query Use SQL query in a jupyter notebook! The table I used can be found on UN Data. Or you can just click the link and download the file undata_s
HatSploit collection of generic payloads designed to provide a wide range of attacks without having to spend time writing new ones.
HatSploit collection of generic payloads designed to provide a wide range of attacks without having to spend time writing new ones.
Dependency injection in python with autoconfiguration
The base is a DynamicContainer to autoconfigure services using the decorators @services for regular services and @command_handler for using command pattern.
This suite consists of two different scripts, made to automate attacks against NoSQL databases.
NoSQL-Attack-Suite This suite consists of two different scripts, made to automate attacks against NoSQL databases. The first one looks for a NoSQL Aut
Pgen is the best brute force password generator and it is improved from the cupp.py
pgen Pgen is the best brute force password generator and it is improved from the cupp.py The pgen tool is dedicated to Leonardo da Vinci -Time stays l

Pizza Orders Data Pipeline Usecase Solved by SQL, Sqoop, HDFS, Hive, Airflow.
PizzaOrders_DataPipeline There is a Tony who is owning a New Pizza shop. He knew that pizza alone was not going to help him get seed funding to expand
POC of CVE-2021-26084, which is Atlassian Confluence Server OGNL Pre-Auth RCE Injection Vulneralibity.
CVE-2021-26084 Description POC of CVE-2021-26084, which is Atlassian Confluence Server OGNL(Object-Graph Navigation Language) Pre-Auth RCE Injection V

This project is related to a No-SQL database, whose data are referred to autoctone botanic species
This project is related to a No-SQL database, whose data are referred to autoctone botanic species. The final goal is creating a function that performs the estimation of the ornamental value, given the specific characteristics of a single species.

KivyPassword - A password generator using both Kivy framework and SQL in order to create a local database for users to generate strong passwords and store them
KivyPassword A password generator using both Kivy framework and SQL in order t

Transferable Unrestricted Attacks, which won 1st place in CVPR’21 Security AI Challenger: Unrestricted Adversarial Attacks on ImageNet.
Transferable Unrestricted Adversarial Examples This is the PyTorch implementation of the Arxiv paper: Towards Transferable Unrestricted Adversarial Ex
All in One CRACKER911181's Tool. This Tool For Hacking and Pentesting.🎭
This is A Python & Bash Programming Based Termux-Tool Created By CRACKER911181. This Tool Created For Hacking and Pentesting. If You Use This Tool To Evil Purpose,The Owner Will Never be Responsible For That.
Import entity definition document into SQLie3. Manage the entity. Also, create a "Create Table SQL file".
EntityDocumentMaker Version 1.00 After importing the entity definition (Excel file), store the data in sqlite3. エンティティ定義(Excelファイル)をインポートした後、データをsqlit
SQL centered, docker process running game
REQUIREMENTS Linux Docker Python/bash set up image "docker build -t game ." create db container "run my_whatever/game_docker/pdb create" # creating po
Logica is a logic programming language that compiles to StandardSQL and runs on Google BigQuery.
Logica: language of Big Data Logica is an open source declarative logic programming language for data manipulation. Logica is a successor to Yedalog,

A SQL linter and auto-formatter for Humans
The SQL Linter for Humans SQLFluff is a dialect-flexible and configurable SQL linter. Designed with ELT applications in mind, SQLFluff also works with

Learnable Boundary Guided Adversarial Training (ICCV2021)
Learnable Boundary Guided Adversarial Training This repository contains the implementation code for the ICCV2021 paper: Learnable Boundary Guided Adve
MongoDB-Injection - This challenge-script is custom-made for web-server running MongoDB which is vulnerable to No-SQL injection
MongoDB-Injection Cheesy Multi-threaded script for NoSQL Injection This challeng
GroupMenter : New Telegram Group Manager Bot🔸Fast 🔸Python🔸Pyrogram 🔸
GroupMenter An PowerFull Group Manager Bot. Written In Pytelethon. Info • A modular Telegram Python bot running on python3. • Can be found on telegram
Find-Xss - Termux Kurulum Dosyası Eklendi Eğer Hata Alıyorsanız Lütfen Resmini Çekip İnstagramdan Bildiriniz
FindXss Waf Bypass Eklendi !!! PRODUCER: Saep UPDATER: Aser-Vant Download: git c

Advbox is a toolbox to generate adversarial examples that fool neural networks in PaddlePaddle、PyTorch、Caffe2、MxNet、Keras、TensorFlow and Advbox can benchmark the robustness of machine learning models.
Advbox is a toolbox to generate adversarial examples that fool neural networks in PaddlePaddle、PyTorch、Caffe2、MxNet、Keras、TensorFlow and Advbox can benchmark the robustness of machine learning models. Advbox give a command line tool to generate adversarial examples with Zero-Coding.
aiosql - Simple SQL in Python
aiosql - Simple SQL in Python SQL is code. Write it, version control it, comment it, and run it using files. Writing your SQL code in Python programs

NS-Defacer: a auto html injecter, In other words It's a auto defacer to deface a lot of websites in less time
Overview NS-Defacer is a auto html injecter, In other words It's a auto defacer
Simplest SQL mapper in Python, probably
SQL MAPPER Basically what it does is: it executes some SQL thru a database connector you fed it, maps it to some model and gives to u. Also it can cre

Catalogue CRUD Application
This Python program creates a relational SQL database hosted on the Snowflake platform, then opens a CRUD GUI to manipulate and view the data. In this application, it is used as a book catalogue. CURRENTLY WIP
The Python SQL Toolkit and Object Relational Mapper
SQLAlchemy The Python SQL Toolkit and Object Relational Mapper Introduction SQLAlchemy is the Python SQL toolkit and Object Relational Mapper that giv

Faza - Faza terminal, Faza help to beginners for pen testing
Faza terminal simple tool for pen testers Use small letter only for commands Don't use space after command 'help' for more information Installation gi
RestApi_flask_sql.alchemy - Product REST API With Flask & SQL Alchemy
REST API With Flask & SQL Alchemy Products API using Python Flask, SQL Alchemy and Marshmallow Quick Start Using Pipenv # Activate venv $ pipenv shell
Adversarial Attacks are Reversible via Natural Supervision
Adversarial Attacks are Reversible via Natural Supervision ICCV2021 Citation @InProceedings{Mao_2021_ICCV, author = {Mao, Chengzhi and Chiquier

Second version of SQL-PYTHON-Practicas
SQLite-Python Acerca de | Autor Sobre el repositorio Segunda version de SQL-PYTHON-Practicas 💻 Tecnologias Visual Studio Code Python SQLite3 📖 Requi
A quick reference guide to the most commonly used patterns and functions in PySpark SQL
Using PySpark we can process data from Hadoop HDFS, AWS S3, and many file systems. PySpark also is used to process real-time data using Streaming and

Gmail account using brute force attack
Programmed in Python | PySimpleGUI Gmail Hack Python script with PySimpleGUI for hack gmail account using brute force attack If you like it give it
A blind SQL injection script that uses binary search aka bisection method to dump datas from database.
Blind SQL Injection I wrote this script to solve PortSwigger Web Security Academy's particular Blind SQL injection with conditional responses lab. Bec
Automate SQL Jobs Monitoring with python
Automate_SQLJobsMonitoring_python Using python 3rd party modules we can automate
Async-first dependency injection library based on python type hints
Dependency Depression Async-first dependency injection library based on python type hints Quickstart First let's create a class we would be injecting:
A collection of awesome sqlite tools, scripts, books, etc
Awesome Series @ Planet Open Data World (Countries, Cities, Codes, ...) • Football (Clubs, Players, Stadiums, ...) • SQLite (Tools, Books, Schemas, ..
Denial Attacks by Various Methods
Denial Service Attack Denial Attacks by Various Methods IIIIIIIIIIIIIIIIIIII PPPPPPPPPPPPPPPPP VVVVVVVV VVVVVVVV I::
The PicoEMP is a low-cost Electromagnetic Fault Injection (EMFI) tool,
ChipSHOUTER-PicoEMP The PicoEMP is a low-cost Electromagnetic Fault Injection (EMFI) tool, designed specifically for self-study and hobbiest research.
Make Your Company Data Driven. Connect to any data source, easily visualize, dashboard and share your data.
Redash is designed to enable anyone, regardless of the level of technical sophistication, to harness the power of data big and small. SQL users levera
Python lightweight dependency injection library
pythondi pythondi is a lightweight dependency injection library for python Support both sync and async functions Installation pip3 install pythondi Us
blind SQLIpy sebuah alat injeksi sql yang menggunakan waktu sql untuk mendapatkan sebuah server database.
blind SQLIpy Alat blind SQLIpy ini merupakan alat injeksi sql yang menggunakan metode time based blind sql injection metode tersebut membutuhkan waktu

Confluence Server Webwork OGNL injection
CVE-2021-26084 - Confluence Server Webwork OGNL injection An OGNL injection vulnerability exists that would allow an authenticated user and in some in
Stable Neural ODE with Lyapunov-Stable Equilibrium Points for Defending Against Adversarial Attacks
Stable Neural ODE with Lyapunov-Stable Equilibrium Points for Defending Against Adversarial Attacks Stable Neural ODE with Lyapunov-Stable Equilibrium

That is a example of a Book app on Python, made with support of all JS libraries on React framework
React+Python Books App You can use this repository whenever you want Used for a video Create the database: python -m dbutils Start the web server: pyt

logmap: Log4j2 jndi injection fuzz tool
logmap - Log4j2 jndi injection fuzz tool Used for fuzzing to test whether there are log4j2 jndi injection vulnerabilities in header/body/path Use http
Mypy plugin and stubs for SQLAlchemy
Mypy plugin and stubs for SQLAlchemy This package contains type stubs and a mypy plugin to provide more precise static types and type inference for SQ
Estoult - a Python toolkit for data mapping with an integrated query builder for SQL databases
Estoult Estoult is a Python toolkit for data mapping with an integrated query builder for SQL databases. It currently supports MySQL, PostgreSQL, and
A repository built on the Flow software package to explore cyber-security attacks on intelligent transportation systems.
A repository built on the Flow software package to explore cyber-security attacks on intelligent transportation systems.

Official implementation of the paper "Backdoor Attacks on Self-Supervised Learning".
SSL-Backdoor Abstract Large-scale unlabeled data has allowed recent progress in self-supervised learning methods that learn rich visual representation
Official PyTorch implementation of "Preemptive Image Robustification for Protecting Users against Man-in-the-Middle Adversarial Attacks" (AAAI 2022)
Preemptive Image Robustification for Protecting Users against Man-in-the-Middle Adversarial Attacks This is the code for reproducing the results of th
Making it easy to query APIs via SQL
Shillelagh Shillelagh (ʃɪˈleɪlɪ) is an implementation of the Python DB API 2.0 based on SQLite (using the APSW library): from shillelagh.backends.apsw
SeqAttack: a framework for adversarial attacks on token classification models
A framework for adversarial attacks against token classification models
Microsoft Azure provides a wide number of services for managing and storing data
Microsoft Azure provides a wide number of services for managing and storing data. One product is Microsoft Azure SQL. Which gives us the capability to create and manage instances of SQL Servers hosted in the cloud. This project, demonstrates how to use these services to manage data we collect from different sources.
A database migrations tool for SQLAlchemy.
Alembic is a database migrations tool written by the author of SQLAlchemy. A migrations tool offers the following functionality: Can emit ALTER statem
Records is a very simple, but powerful, library for making raw SQL queries to most relational databases.
Records: SQL for Humans™ Records is a very simple, but powerful, library for making raw SQL queries to most relational databases. Just write SQL. No b
A Python DB-API and SQLAlchemy dialect to Google Spreasheets
Note: shillelagh is a drop-in replacement for gsheets-db-api, with many additional features. You should use it instead. If you're using SQLAlchemy all
A pythonic dependency injection library.
Pinject Pinject is a dependency injection library for python. The primary goal of Pinject is to help you assemble objects into graphs in an easy, main

FollowSpot is a comprehensive audition tracking fullstack web application for entertainment industry professionals.
FollowSpot is a comprehensive audition tracking fullstack web application for entertainment industry professionals. This app allows users to store information/media for all of their auditions while also compiling data and displaying statistics to help track progress.
Riemann Noise Injection With PyTorch
Riemann Noise Injection - PyTorch A module for modeling GAN noise injection based on Riemann geometry, as described in Ruili Feng, Deli Zhao, and Zhen

Python Toolkit containing different Cyber Attacks Tools
Helikopter Python Toolkit containing different Cyber Attacks Tools. Tools in Helikopter Toolkit 1. FattyNigger (PYTHON WORM) 2. Taxes (PYTHON PASS EXT
Runtime fault injection platform by Daniele Rizzieri
GDBitflip [v1.04] Runtime fault injection platform by Daniele Rizzieri (2021) This platform executes N times a binary and during each execution it inj

S-attack library. Official implementation of two papers "Are socially-aware trajectory prediction models really socially-aware?" and "Vehicle trajectory prediction works, but not everywhere".
S-attack library: A library for evaluating trajectory prediction models This library contains two research projects to assess the trajectory predictio