308 Repositories
Python ai-security Libraries

JF⚡can - Super fast port scanning & service discovery using Masscan and Nmap. Scan large networks with Masscan and use Nmap's scripting abilities to discover information about services. Generate report.
Description Killing features Perform a large-scale scans using Nmap! Allows you to use Masscan to scan targets and execute Nmap on detected ports with

Spring4Shell - Spring Core RCE - CVE-2022-22965
Spring Core RCE - CVE-2022-22965 After Spring Cloud, on March 29, another heavyweight vulnerability of Spring broke out on the Internet: Spring Core R
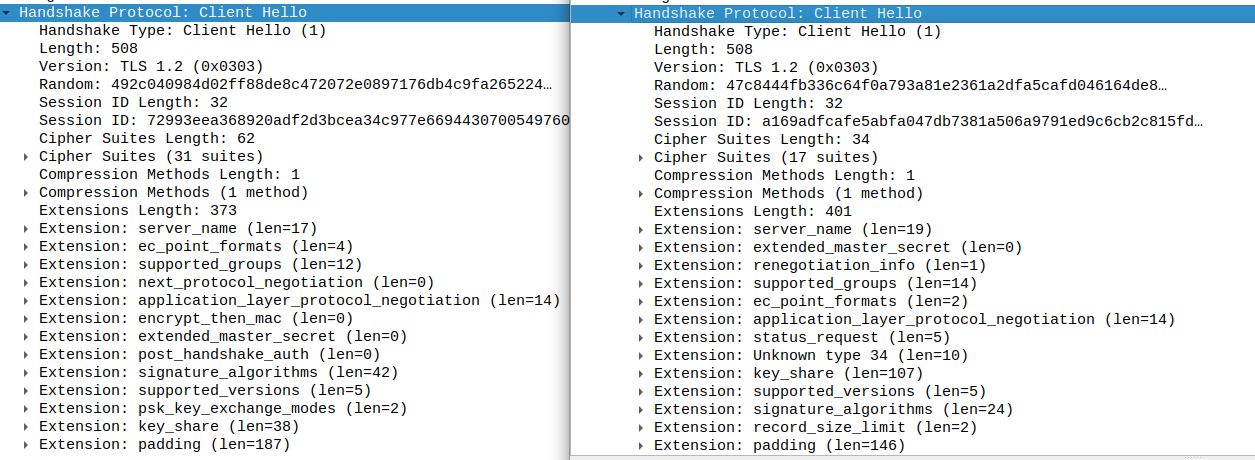
curl-impersonate: A special compilation of curl that makes it impersonate Chrome & Firefox
curl-impersonate A special compilation of curl that makes it impersonate real browsers. It can impersonate the four major browsers: Chrome, Edge, Safa

NIVOS is a hacking tool that allows you to scan deeply , crack wifi, see people on your network
NIVOS is a hacking tool that allows you to scan deeply , crack wifi, see people on your network. It applies to all linux operating systems. And it is improving every day, new packages are added. Thank You For Using NIVOS : [NIVOS Created By NIVO Team]

A simple tool to audit Unix/*BSD/Linux system libraries to find public security vulnerabilities
master_librarian A simple tool to audit Unix/*BSD/Linux system libraries to find public security vulnerabilities. To install requirements: $ sudo pyth

Code for intrusion detection system (IDS) development using CNN models and transfer learning
Intrusion-Detection-System-Using-CNN-and-Transfer-Learning This is the code for the paper entitled "A Transfer Learning and Optimized CNN Based Intrus

A Python Library for Graph Outlier Detection (Anomaly Detection)
PyGOD is a Python library for graph outlier detection (anomaly detection). This exciting yet challenging field has many key applications, e.g., detect
AWS CloudSaga - Simulate security events in AWS
AWS CloudSaga - Simulate security events in AWS AWS CloudSaga is for customers to test security controls and alerts within their Amazon Web Services (

A wordlist generator tool, that allows you to supply a set of words, giving you the possibility to craft multiple variations from the given words, creating a unique and ideal wordlist to use regarding a specific target.
A wordlist generator tool, that allows you to supply a set of words, giving you the possibility to craft multiple variations from the given words, creating a unique and ideal wordlist to use regarding a specific target.

CVE-2022-22965 : about spring core rce
CVE-2022-22965: Spring-Core-Rce EXP 特性: 漏洞探测(不写入 webshell,简单字符串输出) 自定义写入 webshell 文件名称及路径 不会追加写入到同一文件中,每次检测写入到不同名称 webshell 文件 支持写入 冰蝎 webshell 代理支持,可
SSEPy: Implementation of searchable symmetric encryption in pure Python
SSEPy: Implementation of searchable symmetric encryption in pure Python Searchable symmetric encryption, one of the research hotspots in applied crypt

Blazing fast GraphQL endpoints finder using subdomain enumeration, scripts analysis and bruteforce.
Graphinder Graphinder is a tool that extracts all GraphQL endpoints from a given domain. Run with docker docker run -it -v $(pwd):/usr/bin/graphinder

A privacy-focused, intelligent security camera system.
Self-Hosted Home Security Camera System A privacy-focused, intelligent security camera system. Features: Multi-camera support w/ minimal configuration
The Linux defender anti-virus software ported to work on CentOS Linux.
By: Seanpm2001, Et; Al. Top README.md Read this article in a different language Sorted by: A-Z Sorting options unavailable ( af Afrikaans Afrikaans |
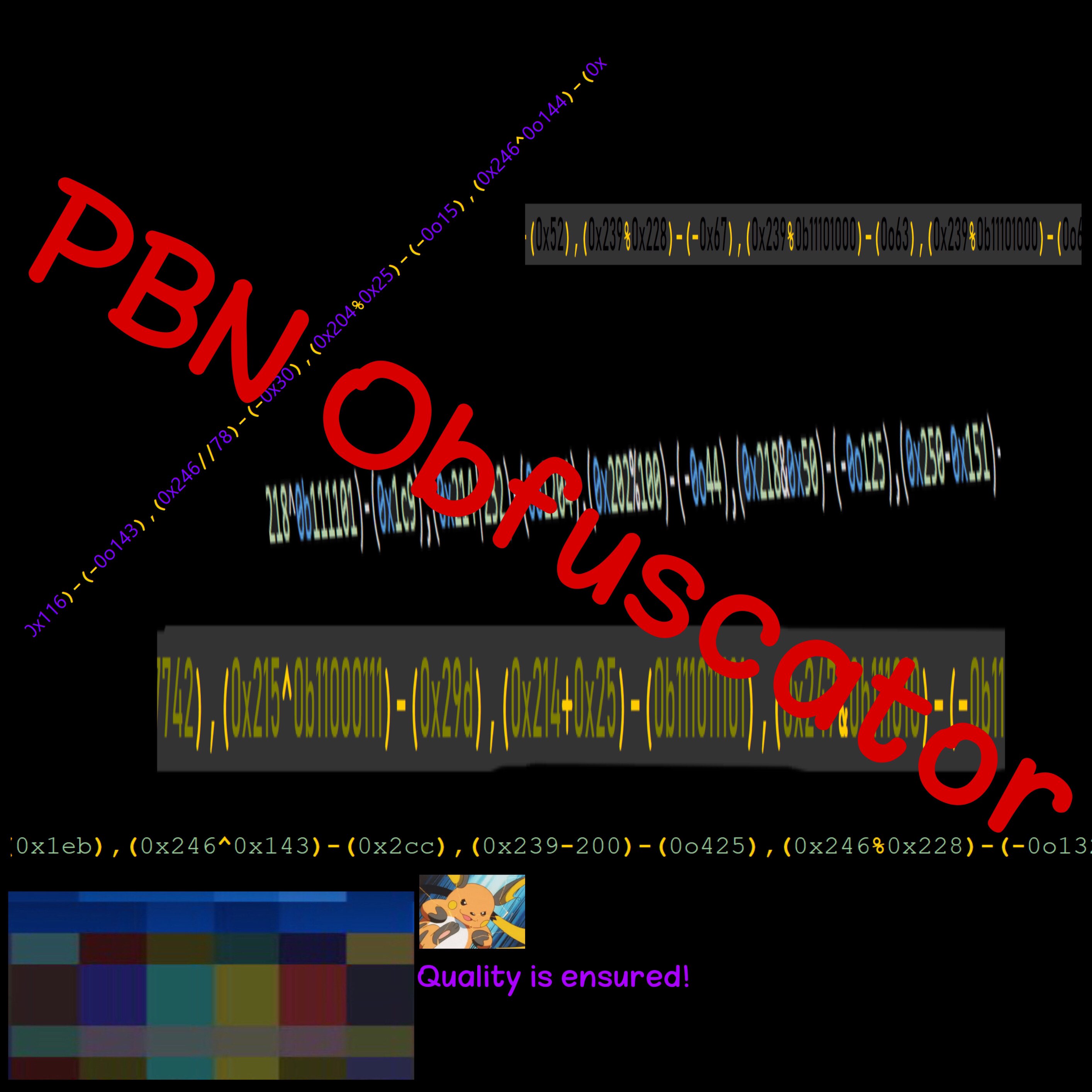
PBN Obfuscator: A overpowered obfuscator for python, which will help you protect your source code
PBN Obfuscator PBN Obfuscator is a overpowered obfuscator for python, which will

Backup dc registry - A simple POC that abuses Backup Operator privileges to remote dump SAM, SYSTEM, and SECURITY
Backup Operator Registry Backup to Domain Compromise A simple POC that abuses Ba

Breaching - Breaching privacy in federated learning scenarios for vision and text
Breaching - A Framework for Attacks against Privacy in Federated Learning This P

EmailAll - a powerful Email Collect tool
EmailAll A powerful Email Collect tool 0x1 介绍 😲 EmailAll is a powerful Email Co
Bugbane - Application security tools for CI/CD pipeline
BugBane Набор утилит для аудита безопасности приложений. Основные принципы и осо
BlackIP-Rep is a tool designed to gather the reputation and information of Bulk IP's.
BlackIP-Rep is a tool designed to gather the reputation and information of Bulk IP's. Focused on increasing the workflow of Security Operations(SOC) team during investigation.
This library attempts to abstract the handling of Sigma rules in Python
This library attempts to abstract the handling of Sigma rules in Python. The rules are parsed using a schema defined with pydantic, and can be easily loaded from YAML files into a structured Python object.
This is the code repository for Mastering Python for Networking and Security – Second Edition
Mastering Python for Networking and Security – Second Edition This is the code repository for Mastering Python for Networking and Security – Second Ed
szrose is an all in one group management bot made for managing your group effectively with some advance security tools & Suit For All Your Needs ❤️
szrose is an all in one group management bot made for managing your group effectively with some advance security tools & Suit For All Your Needs ❤️

RedTeam-Security - In this repo you will get the information of Red Team Security related links
OSINT Passive Discovery Amass - https://github.com/OWASP/Amass (Attack Surface M
Having a weak password is not good for a system that demands high confidentiality and security of user credentials
Having a weak password is not good for a system that demands high confidentiality and security of user credentials. It turns out that people find it difficult to make up a strong password that is strong enough to prevent unauthorized users from memorizing it.

PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1
CVE-2021-45897 PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1 This vulnerability was repor
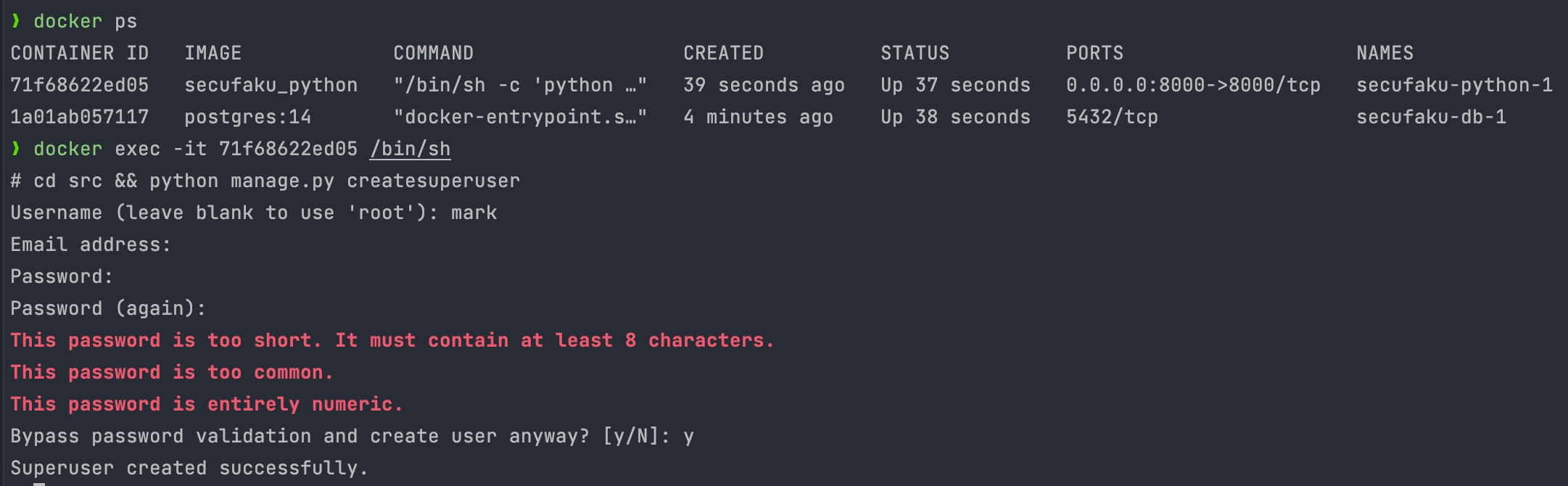
This is sample project needed for security course to connect web service to database
secufaku This is sample project needed for security course to "connect web service to database". Why it suits alignment purpose It connects to postgre

A simple Security Camera created using Opencv in Python where images gets saved in realtime in your Dropbox account at every 5 seconds
Security Camera using Opencv & Dropbox This is a simple Security Camera created using Opencv in Python where images gets saved in realtime in your Dro
Dead simple CSRF security middleware for Starlette ⭐ and Fast API ⚡
csrf-starlette-fastapi Dead simple CSRF security middleware for Starlette ⭐ and Fast API ⚡ Will work with either a input type="hidden" field or ajax
Security system to prevent Shoulder Surfing Attacks
Surf_Sec Security system to prevent Shoulder Surfing Attacks. REQUIREMENTS: Python 3.6+ XAMPP INSTALLED METHOD TO CONFIGURE PROJECT: Clone the repo to

Continuous Security Group Rule Change Detection & Response at scale
Introduction Get notified of Security Group Changes across all AWS Accounts & Regions in an AWS Organization, with the ability to respond/revert those
Smart-contracts - open sourcing our upcoming smart contracts for better security and transparency
Smart-contracts - open sourcing our upcoming smart contracts for better security and transparency
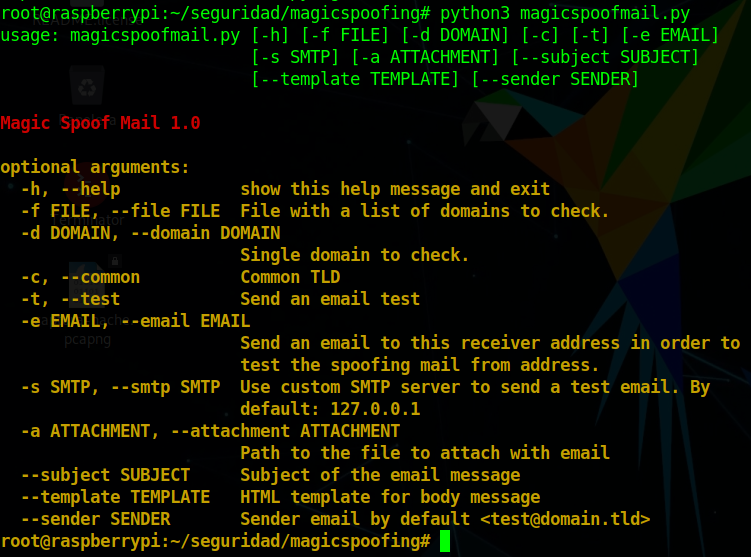
Magicspoofing - A python3 script for search possible misconfiguration in a DNS related to security protections of email service from the domain name
A python3 script for search possible misconfiguration in a DNS related to security protections of email service from the domain name. This project is for educational use, we are not responsible for its misuse.

An curated collection of awesome resources about networking in cybersecurity
An ongoing curated collection of awesome software, libraries, frameworks, talks & videos, best practices, learning tutorials and important practical resources about networking in cybersecurity
This folder contains all the assignment of the course COL759 : Cryptography & Computer Security
Cryptography This folder contains all the assignment of the course COL759 : "Cryptography & Computer Security" Assignment 1 : Encyption, Decryption &

MainCoon - an automated recon framework
MainCoon is an automated recon framework meant for gathering information during penetration testing of web applications.

DIAL(Did I Alert Lambda?) is a centralised security misconfiguration detection framework which completely runs on AWS Managed services like AWS API Gateway, AWS Event Bridge & AWS Lambda
DIAL(Did I Alert Lambda?) is a centralised security misconfiguration detection framework which completely runs on AWS Managed services like AWS API Gateway, AWS Event Bridge & AWS Lambda

⛤Keylogger Generator for Windows written in Python⛤
⛤Keylogger Generator for Windows written in Python⛤
This project is for finding a solution to use Security Onion Elastic data with Jupyter Notebooks.
This project is for finding a solution to use Security Onion Elastic data with Jupyter Notebooks. The goal is to successfully use this notebook project below with Security Onion for beacon detection capabilities.

Epagneul is a tool to visualize and investigate windows event logs
epagneul Epagneul is a tool to visualize and investigate windows event logs. Dep

Best practices for segmentation of the corporate network of any company
Best-practice-for-network-segmentation What is this? This project was created to publish the best practices for segmentation of the corporate network
Spy Ad Network - Spy Ad Network Detection With Python
Spy Ad Network Spy Ad Network Detection Jumps from link to link to access a site

Automated tool to find & created Exploit Poc for Clickjacking Vulnerability
ClickJackPoc This tool will help you automate finding Clickjacking Vulnerability by just passing a file containing list of Targets . Once the Target i
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries by disassembling and analyzing the compiled python byte-code(.pyc) files across all python versions (including Python 3.10.*)

Cloud-native SIEM for intelligent security analytics for your entire enterprise.
Microsoft Sentinel Welcome to the Microsoft Sentinel repository! This repository contains out of the box detections, exploration queries, hunting quer

An effective, simple, and async security library for the Sanic framework.
Sanic Security An effective, simple, and async security library for the Sanic framework. Table of Contents About the Project Getting Started Prerequis
Security audit Python project dependencies against security advisory databases.
Security audit Python project dependencies against security advisory databases.
Bug Alert: a service for alerting security and IT professionals of high-impact and 0day vulnerabilities
Bug Alert Bug Alert is a service for alerting security and IT professionals of h
Security-TXT is a python package for retrieving, parsing and manipulating security.txt files.
Security-TXT is a python package for retrieving, parsing and manipulating security.txt files.
A security system to warn you when people enter your room 🎥
Get Out My Room v0.1 I hate people coming in my room when i'm not there. Get Out My Room is a simple security system that sends notifications with vid

Transferable Unrestricted Attacks, which won 1st place in CVPR’21 Security AI Challenger: Unrestricted Adversarial Attacks on ImageNet.
Transferable Unrestricted Adversarial Examples This is the PyTorch implementation of the Arxiv paper: Towards Transferable Unrestricted Adversarial Ex
People tracker on the Internet: OSINT analysis and research tool by Jose Pino
trape (stable) v2.0 People tracker on the Internet: Learn to track the world, to avoid being traced. Trape is an OSINT analysis and research tool, whi
DevSecOps pipeline for Python based web app using Jenkins, Ansible, AWS, and open-source security tools and checks.
DevSecOps pipeline for Python Web App A Jenkins end-to-end DevSecOps pipeline for Python web application, hosted on AWS Ubuntu 20.04 Note: This projec
CTF (Capture The Flag) started from DEFCON CTF, a competitive game among computer security enthusiasts
CTF Wiki 中文 English Welcome to CTF Wiki! CTF (Capture The Flag) started from DEFCON CTF, a competitive game among computer security enthusiasts, origi
Mina is a new cryptocurrency with a constant size blockchain, improving scaling while maintaining decentralization and security.
Mina Mina is the first cryptocurrency with a lightweight, constant-sized blockchain. This is the main source code repository for the Mina project. It
BleachBit system cleaner for Windows and Linux
BleachBit BleachBit cleans files to free disk space and to maintain privacy. Running from source To run BleachBit without installation, unpack the tar
Low code web framework for real world applications, in Python and Javascript
Full-stack web application framework that uses Python and MariaDB on the server side and a tightly integrated client side library.
labsecurity is a tool that brings together python scripts made for ethical hacking, in a single tool, through a console interface
labsecurity labsecurity is a tool that brings together python scripts made for ethical hacking, in a single tool, through a console interface. Warning
Configure your linux server and check for vulnerabilities with serverlla
serverlla Configure your linux server and check for vulnerabilities with serverlla. Serverlla has a menu with options and allows you to configure your

Advbox is a toolbox to generate adversarial examples that fool neural networks in PaddlePaddle、PyTorch、Caffe2、MxNet、Keras、TensorFlow and Advbox can benchmark the robustness of machine learning models.
Advbox is a toolbox to generate adversarial examples that fool neural networks in PaddlePaddle、PyTorch、Caffe2、MxNet、Keras、TensorFlow and Advbox can benchmark the robustness of machine learning models. Advbox give a command line tool to generate adversarial examples with Zero-Coding.
Securely and anonymously share files, host websites, and chat with friends using the Tor network
OnionShare OnionShare is an open source tool that lets you securely and anonymously share files, host websites, and chat with friends using the Tor ne

ClusterFuzz is a scalable fuzzing infrastructure that finds security and stability issues in software.
ClusterFuzz ClusterFuzz is a scalable fuzzing infrastructure that finds security and stability issues in software. Google uses ClusterFuzz to fuzz all
An interactive python script that enables root access on the T-Mobile (Wingtech) TMOHS1, as well as providing several useful utilites to change the configuration of the device.
TMOHS1 Root Utility Description An interactive python script that enables root access on the T-Mobile (Wingtech) TMOHS1, as well as providing several

Fuzzy-logger - Fuzzy project is here Log all your pc's actions Simple and free to use Security of datas !
Fuzzy-logger - ➡️⭐ Fuzzy ⭐ project is here ! ➡️ Log all your pc's actions ! ➡️ Simple and free to use ➡️ Security of datas !

Obfuscated Gradients Give a False Sense of Security: Circumventing Defenses to Adversarial Examples
Obfuscated Gradients Give a False Sense of Security: Circumventing Defenses to Adversarial Examples Above is an adversarial example: the slightly pert

Checkov is a static code analysis tool for infrastructure-as-code.
Checkov - Prevent cloud misconfigurations during build-time for Terraform, Cloudformation, Kubernetes, Serverless framework and other infrastructure-as-code-languages with Checkov by Bridgecrew.
Omdena-abuja-anpd - Automatic Number Plate Detection for the security of lives and properties using Computer Vision.
Omdena-abuja-anpd - Automatic Number Plate Detection for the security of lives and properties using Computer Vision.
A Python package designed to help users of Cisco's FMC interface with its API.
FMCAPI was originally developed by Dax Mickelson ([email protected]). Dax has moved on to other projects but has kindly transferred the ownership of
Linux Security and Monitoring Scripts
Linux Security and Monitoring Scripts These are a collection of security and monitoring scripts you can use to monitor your Linux installation for sec

Threat Intel Platform for T-POTs
T-Pot 20.06 runs on Debian (Stable), is based heavily on docker, docker-compose
The Multi-Tool Web Vulnerability Scanner.
🟥 RapidScan v1.2 - The Multi-Tool Web Vulnerability Scanner RapidScan has been ported to Python3 i.e. v1.2. The Python2.7 codebase is available on v1

Modern, privacy-friendly, and detailed web analytics that works without cookies or JS.
Modern, privacy-friendly, and cookie-free web analytics. Getting started » Screenshots • Features • Office Hours Motivation There are a lot of web ana
A simple Django middleware for Duo V4 2-factor authentication.
django-duo-universal-auth A lightweight middleware application that adds a layer on top of any number of existing authentication backends, enabling 2F
Detection And Breaking With Python
Detection And Breaking IIIIIIIIIIIIIIIIIIII PPPPPPPPPPPPPPPPP VVVVVVVV VVVVVVVV I::::::::II::::::::I P:::::::
A Python implementation of CWT/COSE.
Python CWT - A Python implementation of CWT/COSE Python CWT is a CBOR Web Token (CWT) and CBOR Object Signing and Encryption (COSE) implementation com
Denial Attacks by Various Methods
Denial Service Attack Denial Attacks by Various Methods IIIIIIIIIIIIIIIIIIII PPPPPPPPPPPPPPPPP VVVVVVVV VVVVVVVV I::
Keep your company's passwords behind the firewall
TeamVault TeamVault is an open-source web-based shared password manager for behind-the-firewall installation. It requires Python 3.3+ and Postgres (wi

PassLock is a medium-security password manager that encrypts passwords using Advanced Encryption Standards (AES)
A medium security python password manager that encrypt passwords using Advanced Encryption Standard (AES) PassLock is a password manager and password
Chromepass - Hacking Chrome Saved Passwords
Chromepass - Hacking Chrome Saved Passwords and Cookies View Demo · Report Bug · Request Feature Table of Contents About the Project AV Detection Gett
PcapXray - A Network Forensics Tool - To visualize a Packet Capture offline as a Network Diagram
PcapXray - A Network Forensics Tool - To visualize a Packet Capture offline as a Network Diagram including device identification, highlight important communication and file extraction
Aircache is an open-source caching and security solution that can be integrated with most decoupled apps that use REST APIs for communicating.
AirCache Aircache is an open-source caching and security solution that can be integrated with most decoupled apps that use REST APIs for communicating

A Python library for inserting an reverse shell attached to Telegram in any Python application.
py tel reverse shell the reverse shell in your telgram! What is this? This program is a Python library that you can use to put an inverted shell conne
Chopper: An Automated Security Headers Analyzer
____ _ _ / ___| |__ ___ _ __ _ __ ___ _ __| | | | | '_ \ / _ \| '_ \| '_ \ / _ \ '__| | | |___| | | | (_) |
LHXP・Official "LH - Cyber Security" Discord Leveling-Bot
LHXP・Official "LH - Cyber Security" Discord Leveling-Bot Based on nsde/NOVΛLIX Feature Overview /clear @user Requires admin permission Purges all XP

A curated list of resources dedicated to reinforcement learning applied to cyber security.
Awesome Reinforcement Learning for Cyber Security A curated list of resources dedicated to reinforcement learning applied to cyber security. Note that

An Abstract Cyber Security Simulation and Markov Game for OpenAI Gym
gym-idsgame An Abstract Cyber Security Simulation and Markov Game for OpenAI Gym gym-idsgame is a reinforcement learning environment for simulating at
Robot Hacking Manual (RHM). From robotics to cybersecurity. Papers, notes and writeups from a journey into robot cybersecurity.
RHM: Robot Hacking Manual Download in PDF RHM v0.4 ┃ Read online The Robot Hacking Manual (RHM) is an introductory series about cybersecurity for robo

I have baked a custom integration to control Eufy Security Cameras and access RTSP and P2P stream if possible.
I have baked a custom integration to control Eufy Security Cameras and access RTSP (real time streaming protocol) and P2P (peer to peer) stream if pos

A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability
log4j-shell-poc A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability. Recently there was a new vulnerability in log4j, a java loggin
Anonymous Dark Web Tool
Anonymous Dark Web Tool v1.0 Features Anonymous Mode Darkweb Search Engines Check Onion Url/s Scanning Host/IP Keep eyes on v2.0 soon. Requirement Deb
Simulating Log4j Remote Code Execution (RCE) vulnerability in a flask web server using python's logging library with custom formatter that simulates lookup substitution by executing remote exploit code.
py4jshell Simulating Log4j Remote Code Execution (RCE) CVE-2021-44228 vulnerability in a flask web server using python's logging library with custom f

Scout Suite - an open source multi-cloud security-auditing tool,
Description Scout Suite is an open source multi-cloud security-auditing tool, which enables security posture assessment of cloud environments. Using t
labsecurity is a framework and its use is for ethical hacking and computer security
labsecurity labsecurity is a framework and its use is for ethical hacking and computer security. Warning This tool is only for educational purpose. If
Provides script to download and format public IP lists related to the Log4j exploit.
Provides script to download and format public IP lists related to the Log4j exploit. Current format includes: plain list, Cisco ASA Network Group.

Cloud One Container Security Runtime Events Forwarder
Example on how to query events by a RESTful API, compose CEF event format and send the events to an UDP receiver.

Providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account.
We are providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account. The script enables security teams to identify external-facing AWS assets by running the exploit on them, and thus be able to map them and quickly patch them
A repository built on the Flow software package to explore cyber-security attacks on intelligent transportation systems.
A repository built on the Flow software package to explore cyber-security attacks on intelligent transportation systems.
SSLyze is a fast and powerful SSL/TLS scanning tool and Python library.
SSLyze SSLyze is a fast and powerful SSL/TLS scanning tool and Python library. SSLyze can analyze the SSL/TLS configuration of a server by connecting

Official implementation of the article "Unsupervised JPEG Domain Adaptation For Practical Digital Forensics"
Unsupervised JPEG Domain Adaptation for Practical Digital Image Forensics @WIFS2021 (Montpellier, France) Rony Abecidan, Vincent Itier, Jeremie Boulan

♟️ QR Code display for P4wnP1 (SSH, VNC, any text / URL)
♟️ Display QR Codes on P4wnP1 (p4wnsolo-qr) 🟢 QR Code display for P4wnP1 w/OLED (SSH, VNC, P4wnP1 WebGUI, any text / URL / exfiltrated data) Note: Th