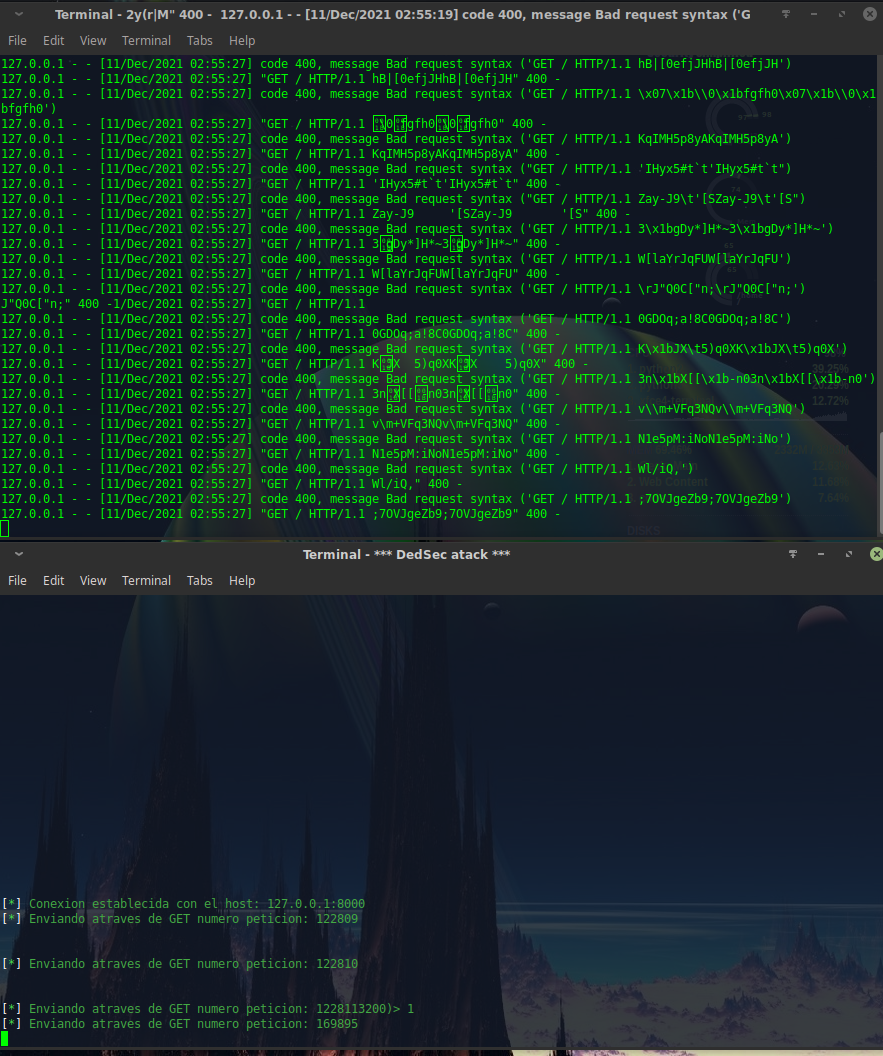
CVE-2021-36798
CVE-2021-36798 Cobalt Strike < 4.3 dos
用法
python3 CVE-2021-36798.py BeaconURL
打瘫Cobalt Strike 只需要一个包
已测试 4.3 4.2
参考:
CVE-2021-36798 Cobalt Strike < 4.3 dos
用法
python3 CVE-2021-36798.py BeaconURL
打瘫Cobalt Strike 只需要一个包
已测试 4.3 4.2
参考:
PocOrExp in Github 聚合Github上已有的Poc或者Exp,CVE信息来自CVE官网 注意:只通过通用的CVE号聚合,因此对于MS17-010等Windows编号漏洞以及著名的有绰号的漏洞,还是自己检索一下比较好 Usage python3 exp.py -h usage: ex
CVE-2022-21907 Description POC for CVE-2022-21907: Windows HTTP协议栈远程代码执行漏洞 creat
CVE-2022-22536 SAP memory pipes desynchronization vulnerability(MPI) CVE-2022-22
cve-2022-23131 cve-2022-23131 zabbix-saml-bypass-exp replace [zbx_signed_session
CVE-2022-22965 - vulnerable app and PoC Trial & error $ docker rm -f rce; docker build -t rce:latest . && docker run -d -p 8080:8080 --name rce rce:la
dos-attacker ❕ Atenção Não ataque sites privados. isto é illegal. 🖥️ Pré-requisitos Ultima versão do Python3. para verificar isto, é bem simples. Bas
script de python que permite usar conexiones cebollas para atacar paginas .onion o paginas convencionales via tor. tiene capacidad de ajustar la cantidad de informacion a enviar, el numero de hilos a usar, el tiempo de duracion del ataque, atacar a un directorio en especial y etc. Su ataque es sencillo, trata de saturar un recurso en base a peticiones GET en rutas del servidor excesivamente lentas.
Bluetooth Simple Denial Of Service (DoS) Legal Note This project is made only for educational purposes and for helping in Proofs of Concept. The autho
laravel-exploits Exploit for CVE-2021-3129
ExProlog ProxyLogon Full Exploit Chain PoC (CVE-2021–26855, CVE-2021–26857, CVE-2021–26858, CVE-2021–27065) Usage: exprolog.py [OPTIONS] ExProlog -
Cobalt Strike Configuration Extractor and Parser Overview Pure Python library and set of scripts to extract and parse configurations (configs) from Co
说明 about author: 我超怕的 blog: https://www.cnblogs.com/iAmSoScArEd/ github: https://github.com/iAmSOScArEd/ date: 2021-12-20 log4j2 dos exploit log4j2 do
dnspooq DNSpooq PoC - dnsmasq cache poisoning (CVE-2020-25686, CVE-2020-25684, CVE-2020-25685) For educational purposes only Requirements Docker compo
ProxyLogon For Python3 ProxyLogon(CVE-2021-26855+CVE-2021-27065) Exchange Server RCE(SSRF->GetWebShell) usage: python ProxyLogon.py --host=exchang
PrintNightmare Python implementation for PrintNightmare (CVE-2021-1675 / CVE-2021-34527) using standard Impacket. Installtion $ pip3 install impacket
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Known issues it will not work outside kali , i will update it
noPac Exploiting CVE-2021-42278 and CVE-2021-42287 原项目noPac在实现上可能有点问题,导致在本地没有打通,于是参考sam-the-admin项目进行修改。 使用 pip3 install -r requirements.txt # GetShel
About Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Changed from sam-the-admin. Usage SAM THE ADMIN CVE-202
CVE-2021-45383 & CVE-2021-45384 There are several network-layer vulnerabilities in the official server of Minecraft: Bedrock Edition (aka Bedrock Serv