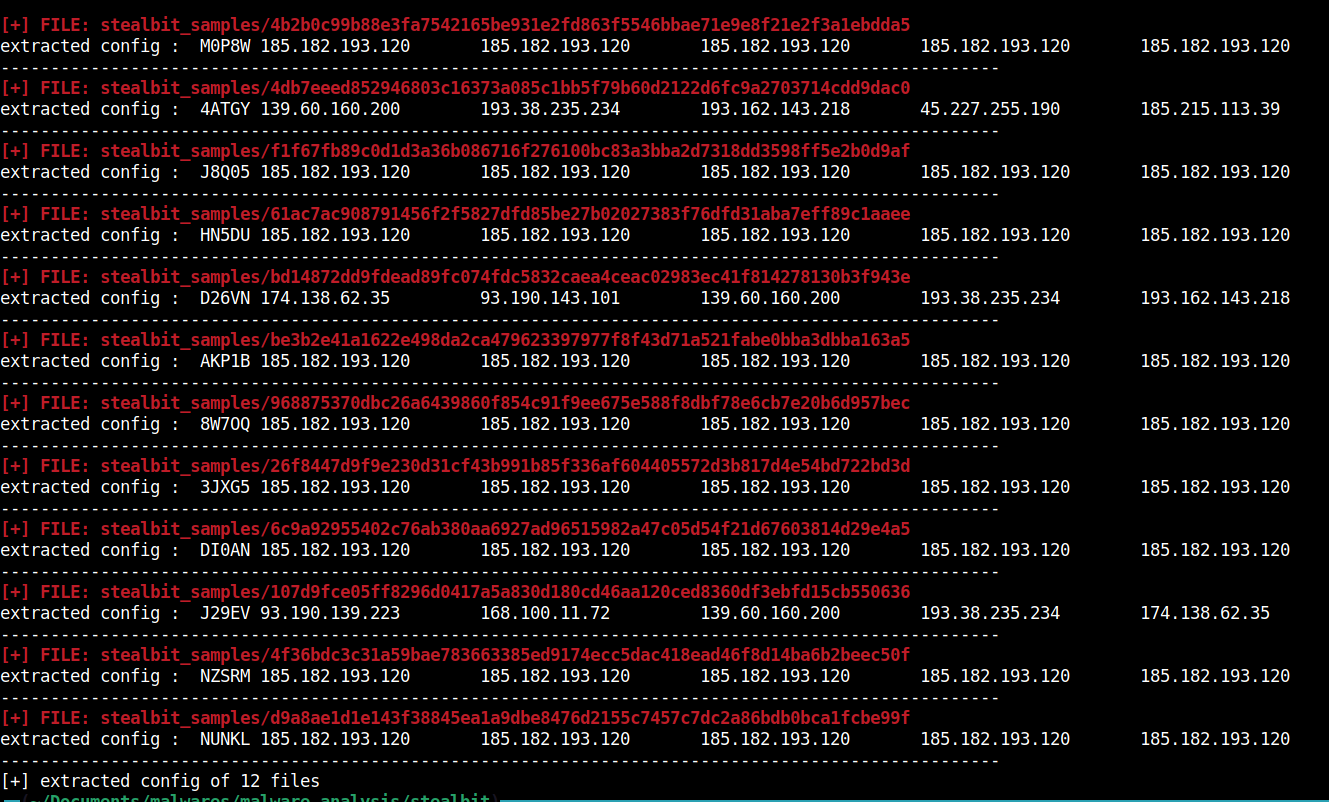
StealBit1.1 and earlier scripts
- Use strings_decryptor.py to extract RC4 encrypted strings from a StealBit1.1 sample(s).
- Use config_extractor.py to extract encrypted configuration(ID and C2s) of a StealBit1.1 sample(s).
Tested on the following samples:
107d9fce05ff8296d0417a5a830d180cd46aa120ced8360df3ebfd15cb5506366c9a92955402c76ab380aa6927ad96515982a47c05d54f21d67603814d29e4a526f8447d9f9e230d31cf43b991b85f336af604405572d3b817d4e54bd722bd3d968875370dbc26a6439860f854c91f9ee675e588f8dbf78e6cb7e20b6d957bec4b2b0c99b88e3fa7542165be931e2fd863f5546bbae71e9e8f21e2f3a1ebdda5bd14872dd9fdead89fc074fdc5832caea4ceac02983ec41f814278130b3f943e4db7eeed852946803c16373a085c1bb5f79b60d2122d6fc9a2703714cdd9dac0be3b2e41a1622e498da2ca479623397977f8f43d71a521fabe0bba3dbba163a54f36bdc3c31a59bae783663385ed9174ecc5dac418ead46f8d14ba6b2beec50fd9a8ae1d1e143f38845ea1a9dbe8476d2155c7457c7dc2a86bdb0bca1fcbe99f61ac7ac908791456f2f5827dfd85be27b02027383f76dfd31aba7eff89c1aaeef1f67fb89c0d1d3a36b086716f276100bc83a3bba2d7318dd3598ff5e2b0d9af