293 Repositories
Python end-to-end-encryption Libraries

A PyTorch library and evaluation platform for end-to-end compression research
CompressAI CompressAI (compress-ay) is a PyTorch library and evaluation platform for end-to-end compression research. CompressAI currently provides: c
A short code in python, Enchpyter, is able to encrypt and decrypt words as you determine, of course
Enchpyter Enchpyter is a program do encrypt and decrypt any word you want (just letters). You enter how many letters jumps and write the word, so, the
A short code in python, Enchpyter, is able to encrypt and decrypt words as you determine, of course
Enchpyter Enchpyter is a program do encrypt and decrypt any word you want (just letters). You enter how many letters jumps and write the word, so, the
An end to end ASR Transformer model training repo
END TO END ASR TRANSFORMER 本项目基于transformer 6*encoder+6*decoder的基本结构构造的端到端的语音识别系统 Model Instructions 1.数据准备: 自行下载数据,遵循文件结构如下: ├── data │ ├── train │

Linear encryption software programmed with python
Echoder linear encryption software programmed with python How does it work? The text in the text section runs a function with two keys entered keys mu
Enchpyter, is able to encrypt and decrypt words as you determine, of course, according to the alphabet.
Enchpyter is a program do encrypt and decrypt any word you want (just letters). You enter how many letters jumps and write the word, so, the program encrypt for you in seconds.
End-To-End Memory Network using Tensorflow
MemN2N Implementation of End-To-End Memory Networks with sklearn-like interface using Tensorflow. Tasks are from the bAbl dataset. Get Started git clo
Vaccine for STOP/DJVU ransomware, prevents encryption
STOP/DJVU Ransomware Vaccine Prevents STOP/DJVU Ransomware from encrypting your files. This tool does not prevent the infection itself. STOP ransomwar
DUE: End-to-End Document Understanding Benchmark
This is the repository that provide tools to download data, reproduce the baseline results and evaluation. What can you achieve with this guide Based

Stenography encryption script
ImageCrypt Project description Installation Usage Project description Project AlexGyver on Python by TheK4n Design by Пашушка Byte packing in decimal
A Python library to wrap age and minisign to provide key management, encryption/decryption and signing/verification functionality.
A Python library to wrap age and minisign to provide key management, encryption/decryption and signing/verification functionality.

End-2-end speech synthesis with recurrent neural networks
Introduction New: Interactive demo using Google Colaboratory can be found here TTS-Cube is an end-2-end speech synthesis system that provides a full p
FPE - Format Preserving Encryption with FF3 in Python
ff3 - Format Preserving Encryption in Python An implementation of the NIST approved FF3 and FF3-1 Format Preserving Encryption (FPE) algorithms in Pyt
Python Yeelight YLKG07YL/YLKG08YL dimmer handler
With this class you can receive, decrypt and handle Yeelight YLKG07YL/YLKG08YL dimmer bluetooth notifications in your python code.
Sign data using symmetric-key algorithm encryption.
Sign data using symmetric-key algorithm encryption. Validate signed data and identify possible validation errors. Uses sha-(1, 224, 256, 385 and 512)/hmac for signature encryption. Custom hash algorithms are allowed. Useful shortcut functions for signing (and validating) dictionaries and URLs.

Repo to store back end infrastructure for Message in a Bottle
Message in a Bottle Backend API RESTful API for Message in a Bottle frontend application consumption. About The Project • Tools Used • Local Set Up •
End-to-End Referring Video Object Segmentation with Multimodal Transformers
End-to-End Referring Video Object Segmentation with Multimodal Transformers This repo contains the official implementation of the paper: End-to-End Re
Production First and Production Ready End-to-End Keyword Spotting Toolkit
WeKws Production First and Production Ready End-to-End Keyword Spotting Toolkit. The goal of this toolkit it to... Small footprint keyword spotting (K
An end-to-end encrypted chat
An end-to-end encrypted chat, that allows users to anonymously talk without ip logs, personal info, or need for registration.
Pytorch library for end-to-end transformer models training and serving
Pytorch library for end-to-end transformer models training and serving

Bridging Composite and Real: Towards End-to-end Deep Image Matting
Bridging Composite and Real: Towards End-to-end Deep Image Matting Please note that the official repository of the paper Bridging Composite and Real:
Xor encryption and decryption algorithm
Folosire: Pentru encriptare: python encrypt.py parola fișier pentru criptare fișier encriptat(de tip binar) Pentru decriptare: python decrypt.p
Opinionated boilerplate for starting a Django project together with React front-end library and TailwindCSS CSS framework.
Opinionated boilerplate for starting a Django project together with React front-end library and TailwindCSS CSS framework.
Vaulty - Encrypt/Decrypt with ChaCha20-Poly1305
Vaulty Encrypt/Decrypt with ChaCha20-Poly1305 Vaulty is an extremely lightweight encryption/decryption tool which uses ChaCha20-Poly1305 to provide 25

An encryption format offering better security, performance and ease of use than PGP.
An encryption format offering better security, performance and ease of use than PGP. File a bug if you found anything where we are worse than our competition, and we will fix it.

EvDistill: Asynchronous Events to End-task Learning via Bidirectional Reconstruction-guided Cross-modal Knowledge Distillation (CVPR'21)
EvDistill: Asynchronous Events to End-task Learning via Bidirectional Reconstruction-guided Cross-modal Knowledge Distillation (CVPR'21) Citation If y
School Project using Python Sockets and Personal Encryption Method.
Python-Secure-File-Transfer School Project using Python Sockets and Personal Encryption Method. Installation Must have python3 installed on your syste
Project page for End-to-end Recovery of Human Shape and Pose
End-to-end Recovery of Human Shape and Pose Angjoo Kanazawa, Michael J. Black, David W. Jacobs, Jitendra Malik CVPR 2018 Project Page Requirements Pyt
This is a simple Todo web application built Django (back-end) and React JS (front-end)
Django REST Todo app This is a simple Todo web application built with Django (back-end) and React JS (front-end). The project enables you to systemati
Reference PyTorch implementation of "End-to-end optimized image compression with competition of prior distributions"
PyTorch reference implementation of "End-to-end optimized image compression with competition of prior distributions" by Benoit Brummer and Christophe
The next level Python obfuscator, nearly impossible to deobfuscate.
🐸 Kramer 🐸 Kramer is a next level obfuscation tool written in Python3 allowing you to obfuscate your Python3 code easily and securely. It uses Berse

Implementation of DocFormer: End-to-End Transformer for Document Understanding, a multi-modal transformer based architecture for the task of Visual Document Understanding (VDU)
DocFormer - PyTorch Implementation of DocFormer: End-to-End Transformer for Document Understanding, a multi-modal transformer based architecture for t
PyTorch-LIT is the Lite Inference Toolkit (LIT) for PyTorch which focuses on easy and fast inference of large models on end-devices.
PyTorch-LIT PyTorch-LIT is the Lite Inference Toolkit (LIT) for PyTorch which focuses on easy and fast inference of large models on end-devices. With
Doom o’clock is a website/project that features a countdown of “when will the earth end” and a greenhouse gas effect emission prediction that’s predicted
Doom o’clock is a website/project that features a countdown of “when will the earth end” and a greenhouse gas effect emission prediction that’s predicted
End to End toy example of MLOps
churn_model MLOps Toy Example End to End You might find below links useful Connect VSCode to Git MLFlow Port Heroku App Project Organization ├── LICEN

A Python Tool to encrypt all types of files using AES and XOR Algorithm.
DataShield This project intends to protect user’s data, it stores files in encrypted format in device provided the passcode and path of the file. AES
Production First and Production Ready End-to-End Keyword Spotting Toolkit
Production First and Production Ready End-to-End Keyword Spotting Toolkit
MHtyper is an end-to-end pipeline for recognized the Forensic microhaplotypes in Nanopore sequencing data.
MHtyper is an end-to-end pipeline for recognized the Forensic microhaplotypes in Nanopore sequencing data. It is implemented using Python.
A python package containing all the basic functions and classes for python. From simple addition to advanced file encryption.
A python package containing all the basic functions and classes for python. From simple addition to advanced file encryption.
A collection of differentiable SVD methods and also the official implementation of the ICCV21 paper "Why Approximate Matrix Square Root Outperforms Accurate SVD in Global Covariance Pooling?"
Differentiable SVD Introduction This repository contains: The official Pytorch implementation of ICCV21 paper Why Approximate Matrix Square Root Outpe

MDETR: Modulated Detection for End-to-End Multi-Modal Understanding
MDETR: Modulated Detection for End-to-End Multi-Modal Understanding Website • Colab • Paper This repository contains code and links to pre-trained mod

3D-CariGAN: An End-to-End Solution to 3D Caricature Generation from Normal Face Photos
3D-CariGAN: An End-to-End Solution to 3D Caricature Generation from Normal Face Photos This repository contains the source code and dataset for the pa
A python screen recorder for low-end computers, provides high quality video output.
RecorderX - v1.0 A screen recorder made in Python with the help of OpenCv, it has ability to record your screen in high quality. No matter what your P

Encrypt decrypt files - Programmed in Python | PySimpleGUI
Crypter Programmed in Python | PySimpleGUI If you like it give it a star How it works Crypter program use Fernet for encryption. Fernet guarantees tha
METER: Multimodal End-to-end TransformER
METER Code and pre-trained models will be publicized soon. Citation @article{dou2021meter, title={An Empirical Study of Training End-to-End Vision-a
This is a basic encryption and decryption program made in python.
A basic encryption and decryption program to visualize how the process of protecting data works.
End-To-End Crowdsourcing
End-To-End Crowdsourcing Comparison of traditional crowdsourcing approaches to a state-of-the-art end-to-end crowdsourcing approach LTNet on sentiment
PyTorch implementation of "A Two-Stage End-to-End System for Speech-in-Noise Hearing Aid Processing"
Implementation of the Sheffield entry for the first Clarity enhancement challenge (CEC1) This repository contains the PyTorch implementation of "A Two

The command line interface for Gradient - Gradient is an an end-to-end MLOps platform
Gradient CLI Get started: Create Account • Install CLI • Tutorials • Docs Resources: Website • Blog • Support • Contact Sales Gradient is an an end-to
Crypt Wiki - VimWiki with added support for encryption/decryption
Crypt Wiki - VimWiki with added support for encryption/decryption This project is meant to solve an issue I have ran into recently. I wanted to have a

A complete end-to-end machine learning portal that covers processes starting from model training to the model predicting results using FastAPI.
Machine Learning Portal Goal Application Workflow Process Design Live Project Goal A complete end-to-end machine learning portal that covers processes
REBEL: Relation Extraction By End-to-end Language generation
REBEL: Relation Extraction By End-to-end Language generation This is the repository for the Findings of EMNLP 2021 paper REBEL: Relation Extraction By
Dirty Pixels: Towards End-to-End Image Processing and Perception
Dirty Pixels: Towards End-to-End Image Processing and Perception This repository contains the code for the paper Dirty Pixels: Towards End-to-End Imag
Networkx with neo4j back-end
Dump networkx graph into nodes/relations TSV from neo4jnx.tsv import graph_to_tsv g = pklload('indranet_dir_graph.pkl') graph_to_tsv(g, 'docker/nodes.
Aza this is a text encryption software
Aza text encryptor General info Aza this is a text encryption software Help command: python aza.py --help Examples python aza.py --text "Sample text h
Avalanche RL: an End-to-End Library for Continual Reinforcement Learning
Avalanche RL: an End-to-End Library for Continual Reinforcement Learning Avalanche Website | Getting Started | Examples | Tutorial | API Doc | Paper |
Python program that handles the creation, encryption and storage of log/journal files. Kinda works like a diary of sorts.
LucaSoft J.O.U.R.N.A.L The J.O.U.R.N.A.L (Just anOther User Redaction & Navigation Assistant by Lucaspec72) is a Python program that handles the creat

Python Encryption Name Game
Python 3.9.7 Encryption Name Game Encrypt a name with numbers using a Caesar cipher! You can choose different numbers to encrypt your name from 1 to o
Neural Lexicon Reader: Reduce Pronunciation Errors in End-to-end TTS by Leveraging External Textual Knowledge
Neural Lexicon Reader: Reduce Pronunciation Errors in End-to-end TTS by Leveraging External Textual Knowledge This is an implementation of the paper,

An End-to-End Trainable Neural Network for Image-based Sequence Recognition and Its Application to Scene Text Recognition
CRNN paper:An End-to-End Trainable Neural Network for Image-based Sequence Recognition and Its Application to Scene Text Recognition 1. create your ow
VOneNet: CNNs with a Primary Visual Cortex Front-End
VOneNet: CNNs with a Primary Visual Cortex Front-End A family of biologically-inspired Convolutional Neural Networks (CNNs). VOneNets have the followi
A simple key-based text encryption process that encrypts a string based in a list of characteres pairs.
Simple Cipher Encrypter About | New Features | Exemple | How To Use | License ℹ️ About A simple key-based text encryption process that encrypts a stri
The end-to-end platform for building voice products at scale
Picovoice Made in Vancouver, Canada by Picovoice Picovoice is the end-to-end platform for building voice products on your terms. Unlike Alexa and Goog
Simple one-time pad (OTP) encryption
Introduction What you will make In this resource you will learn how to create and use an encryption technique known as the one-time pad. This method o

KITTI-360 Annotation Tool is a framework that developed based on python(cherrypy + jinja2 + sqlite3) as the server end and javascript + WebGL as the front end.
KITTI-360 Annotation Tool is a framework that developed based on python(cherrypy + jinja2 + sqlite3) as the server end and javascript + WebGL as the front end.

Production First and Production Ready End-to-End Speech Recognition Toolkit
WeNet 中文版 Discussions | Docs | Papers | Runtime (x86) | Runtime (android) | Pretrained Models We share neural Net together. The main motivation of WeN
glow-speak is a fast, local, neural text to speech system that uses eSpeak-ng as a text/phoneme front-end.
Glow-Speak glow-speak is a fast, local, neural text to speech system that uses eSpeak-ng as a text/phoneme front-end. Installation git clone https://g
NVIDIA Merlin is an open source library providing end-to-end GPU-accelerated recommender systems, from feature engineering and preprocessing to training deep learning models and running inference in production.
NVIDIA Merlin NVIDIA Merlin is an open source library designed to accelerate recommender systems on NVIDIA’s GPUs. It enables data scientists, machine
Neural Lexicon Reader: Reduce Pronunciation Errors in End-to-end TTS by Leveraging External Textual Knowledge
Neural Lexicon Reader: Reduce Pronunciation Errors in End-to-end TTS by Leveraging External Textual Knowledge This is an implementation of the paper,
Official implementation of "Synthetic Temporal Anomaly Guided End-to-End Video Anomaly Detection" (ICCV Workshops 2021: RSL-CV).
Official PyTorch implementation of "Synthetic Temporal Anomaly Guided End-to-End Video Anomaly Detection" This is the implementation of the paper "Syn
Teaching end to end workflow of deep learning
Deep-Education This repository is now available for public use for teaching end to end workflow of deep learning. This implies that learners/researche

End-to-End Speech Processing Toolkit
ESPnet: end-to-end speech processing toolkit system/pytorch ver. 1.3.1 1.4.0 1.5.1 1.6.0 1.7.1 1.8.1 1.9.0 ubuntu20/python3.9/pip ubuntu20/python3.8/p
Get the length of the Instagram encrypted password
instagram-weak-encryption Get the length of the Instagram encrypted password Introduction Instagram and Facebook encrypt the password submitted at log

This repository contains the code for "SBEVNet: End-to-End Deep Stereo Layout Estimation" paper by Divam Gupta, Wei Pu, Trenton Tabor, Jeff Schneider
SBEVNet: End-to-End Deep Stereo Layout Estimation This repository contains the code for "SBEVNet: End-to-End Deep Stereo Layout Estimation" paper by D

Hypernets: A General Automated Machine Learning framework to simplify the development of End-to-end AutoML toolkits in specific domains.
A General Automated Machine Learning framework to simplify the development of End-to-end AutoML toolkits in specific domains.
An end-to-end regression problem of predicting the price of properties in Bangalore.
Bangalore-House-Price-Prediction An end-to-end regression problem of predicting the price of properties in Bangalore. Deployed in Heroku using Flask.
Python codes for the server and client end that facilitates file transfers. (Using AWS EC2 instance as the server)
Server-and-Client-File-Transfer Python codes for the server and client end that facilitates file transfers. I will be using an AWS EC2 instance as the
Powerful Tool to encrypt and decrypt files using AES.
AEScryptor Tool Description Encrypt and Decrypt files with AES-128 (16bytes key). AES mode = CFB (cipher Feedback) security = super safe! Usage [1] Ch
Given a string or a text file with plain text , returns his encryption using SHA256 method
Encryption using SHA256 Given a string or a .txt file with plain text. Returns his encryption using SHA256 method Requirements : pip install pyperclip
End-to-end beat and downbeat tracking in the time domain.
WaveBeat End-to-end beat and downbeat tracking in the time domain. | Paper | Code | Video | Slides | Setup First clone the repo. git clone https://git
recover Firefox and more browsers logins
Browser Creds this script will recover saved browsers logins into txt files. It currently only support windows 10. currently support : Chrome Opera Fi

PyTorch implementation of Microsoft's text-to-speech system FastSpeech 2: Fast and High-Quality End-to-End Text to Speech.
An implementation of Microsoft's "FastSpeech 2: Fast and High-Quality End-to-End Text to Speech"

Implementing Cisco Support APIs into NetBox
NetBox Cisco Support API Plugin NetBox plugin using Cisco Support APIs to gather EoX and Contract coverage information for Cisco devices. Compatibilit
Scrambler - Useful File/Directory Encryption Program
This is a program that is used to scramble/encrypt files on your computer. Do not use this program to do malicious things with. I am not responsible for any damage that you do with this software.
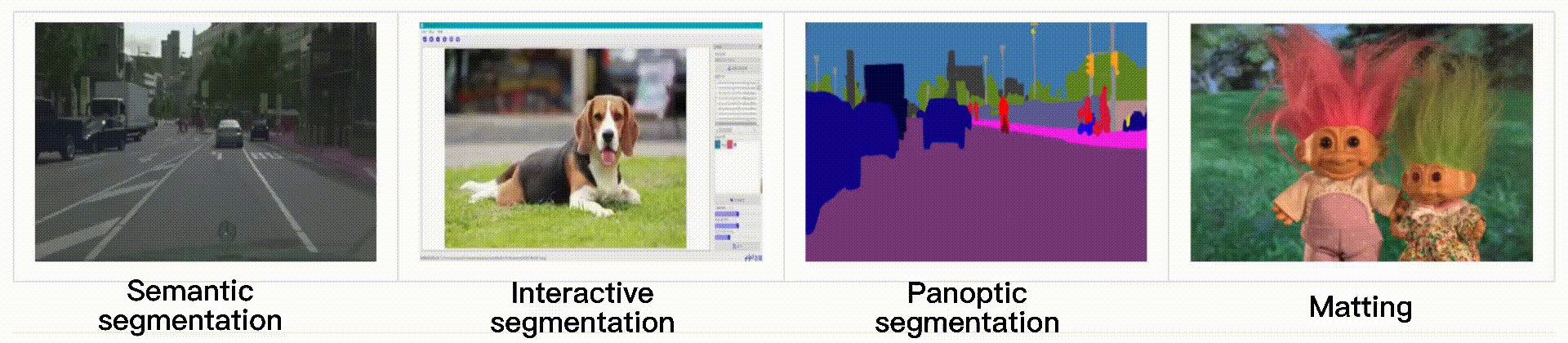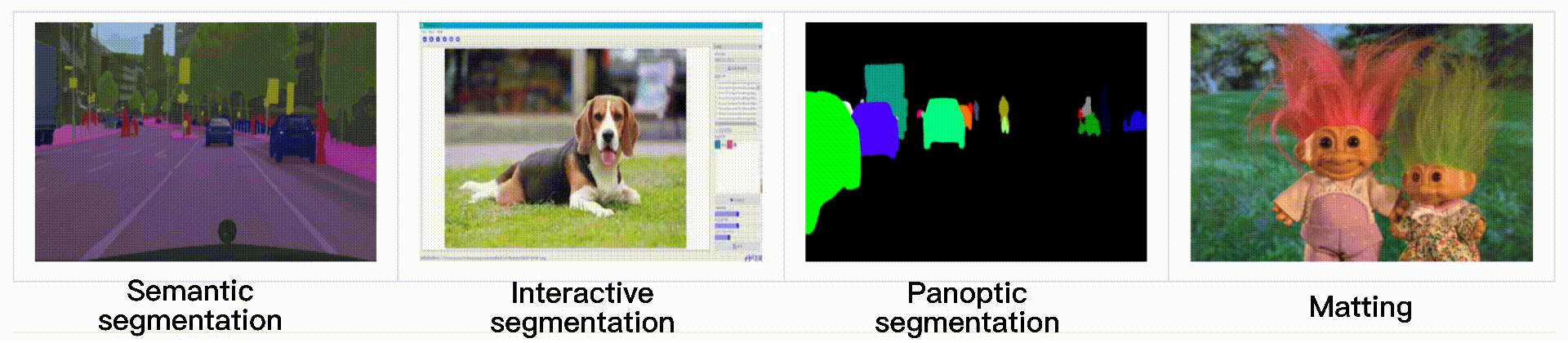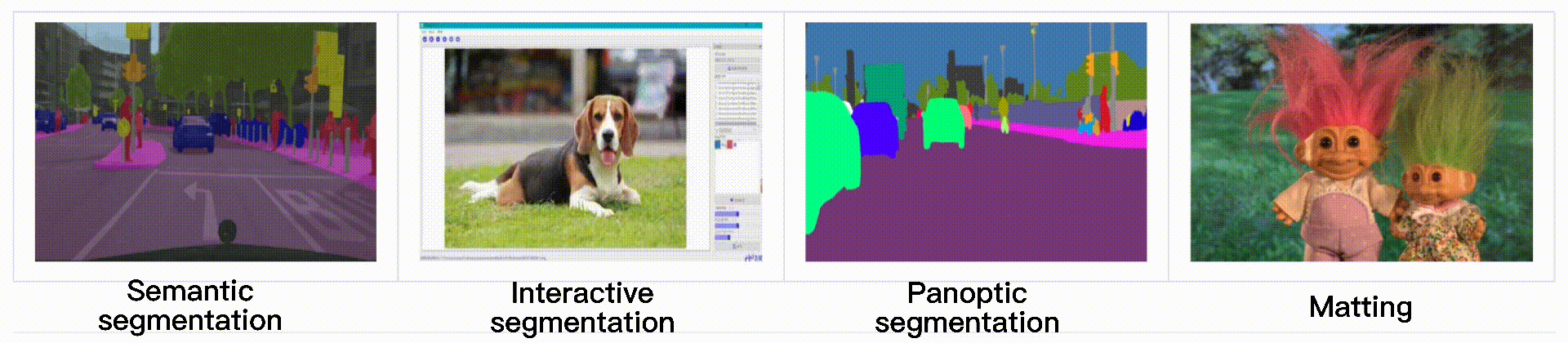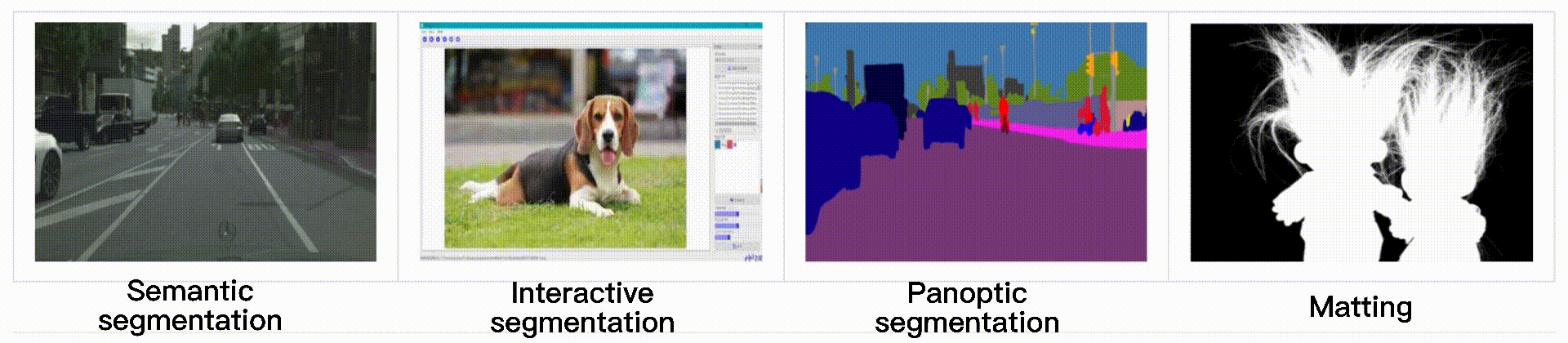
End-to-end image segmentation kit based on PaddlePaddle.
English | 简体中文 PaddleSeg PaddleSeg has released the new version including the following features: Our team won the AutoNUE@CVPR 2021 challenge, where

PyTorch implementation of convolutional neural networks-based text-to-speech synthesis models
Deepvoice3_pytorch PyTorch implementation of convolutional networks-based text-to-speech synthesis models: arXiv:1710.07654: Deep Voice 3: Scaling Tex
A collection of repositories used to realise various end-to-end high-level synthesis (HLS) flows centering around the CIRCT project.
circt-hls What is this?: A collection of repositories used to realise various end-to-end high-level synthesis (HLS) flows centering around the CIRCT p
Deal or No Deal? End-to-End Learning for Negotiation Dialogues
Introduction This is a PyTorch implementation of the following research papers: (1) Hierarchical Text Generation and Planning for Strategic Dialogue (
Task-based end-to-end model learning in stochastic optimization
Task-based End-to-end Model Learning in Stochastic Optimization This repository is by Priya L. Donti, Brandon Amos, and J. Zico Kolter and contains th
Secret Service Email Encryption/Steganography
SecretService Decoy Encrypted Emailer

Demo for the paper "Overlap-aware low-latency online speaker diarization based on end-to-end local segmentation"
Streaming speaker diarization Overlap-aware low-latency online speaker diarization based on end-to-end local segmentation by Juan Manuel Coria, Hervé

Code & Models for 3DETR - an End-to-end transformer model for 3D object detection
3DETR: An End-to-End Transformer Model for 3D Object Detection PyTorch implementation and models for 3DETR. 3DETR (3D DEtection TRansformer) is a simp

Demo for the paper "Overlap-aware low-latency online speaker diarization based on end-to-end local segmentation"
Streaming speaker diarization Overlap-aware low-latency online speaker diarization based on end-to-end local segmentation by Juan Manuel Coria, Hervé

Roach: End-to-End Urban Driving by Imitating a Reinforcement Learning Coach
CARLA-Roach This is the official code release of the paper End-to-End Urban Driving by Imitating a Reinforcement Learning Coach by Zhejun Zhang, Alexa
Encrypt your code without a worry. Stark utilizes the base64, hashlib and Crypto lib to encrypt your code which cannot be decrypted with any online tools.
Stark Encrypt your code without a worry. Stark utilizes the base64, hashlib and Crypto lib to encrypt your code which cannot be decrypted with any onl
PySETO is a PASETO (Platform-Agnostic SEcurity TOkens) implementation written in Python
A Python implementation of PASETO.
WarpDrive: Extremely Fast End-to-End Deep Multi-Agent Reinforcement Learning on a GPU
WarpDrive is a flexible, lightweight, and easy-to-use open-source reinforcement learning (RL) framework that implements end-to-end multi-agent RL on a single GPU (Graphics Processing Unit).

Sparse R-CNN: End-to-End Object Detection with Learnable Proposals, CVPR2021
End-to-End Object Detection with Learnable Proposal, CVPR2021
Deal or No Deal? End-to-End Learning for Negotiation Dialogues
Introduction This is a PyTorch implementation of the following research papers: (1) Hierarchical Text Generation and Planning for Strategic Dialogue (
PyTorch implementation of SampleRNN: An Unconditional End-to-End Neural Audio Generation Model
samplernn-pytorch A PyTorch implementation of SampleRNN: An Unconditional End-to-End Neural Audio Generation Model. It's based on the reference implem