335 Repositories
Python security-normal Libraries
A repository built on the Flow software package to explore cyber-security attacks on intelligent transportation systems.
A repository built on the Flow software package to explore cyber-security attacks on intelligent transportation systems.
SSLyze is a fast and powerful SSL/TLS scanning tool and Python library.
SSLyze SSLyze is a fast and powerful SSL/TLS scanning tool and Python library. SSLyze can analyze the SSL/TLS configuration of a server by connecting

Official implementation of the article "Unsupervised JPEG Domain Adaptation For Practical Digital Forensics"
Unsupervised JPEG Domain Adaptation for Practical Digital Image Forensics @WIFS2021 (Montpellier, France) Rony Abecidan, Vincent Itier, Jeremie Boulan
Just imagine normal bancho, but you can have multiple profiles and funorange speed up maps ranked
Local osu! server Just imagine normal bancho, but you can have multiple profiles and funorange speed up maps ranked (coming soon)! Windows Setup Insta
🦎 A NeoVim plugin for highlighting visual selections like in a normal document editor!
🦎 HighStr.nvim A NeoVim plugin for highlighting visual selections like in a normal document editor! Demo TL;DR HighStr.nvim is a NeoVim plugin writte

♟️ QR Code display for P4wnP1 (SSH, VNC, any text / URL)
♟️ Display QR Codes on P4wnP1 (p4wnsolo-qr) 🟢 QR Code display for P4wnP1 w/OLED (SSH, VNC, P4wnP1 WebGUI, any text / URL / exfiltrated data) Note: Th

𝗖𝝠𝝦𝝩𝝠𝝞𝝥 𝝦𝗥𝝞𝗖𝝽°™️ 🇱🇰 Is An All In One Media Inline Bot Made For Inline Your Media Effectively With Some Advance Security Tools♥️
𝗖𝝠𝝦𝝩𝝠𝝞𝝥 𝝦𝗥𝝞𝗖𝝽° ™️ 🇱🇰 𝗙𝗘𝝠𝝩𝗨𝗥𝗘𝗦 Auto Filter IMDB Admin Commands Broadcast Index IMDB Search Inline Search Random Pics Ids & User I

A semi-automatic osint/recon framework.
Smog Framework A semi-automatic osint/recon framework. Requirements git Python = 3.8 How to use it

Download a large file from Google Drive (curl/wget fails because of the security notice).
gdown Download a large file from Google Drive. Description Download a large file from Google Drive. If you use curl/wget, it fails with a large file b
Detect secret in source code, scan your repo for leaks. Find secrets with GitGuardian and prevent leaked credentials. GitGuardian is an automated secrets detection & remediation service.
GitGuardian Shield: protect your secrets with GitGuardian GitGuardian shield (ggshield) is a CLI application that runs in your local environment or in
Chapter 1 of the AWS Cookbook
Chapter 1 - Security Set and export your default region: export AWS_REGION=us-east-1 Set your AWS ACCOUNT ID:: AWS_ACCOUNT_ID=$(aws sts get-caller-ide

Automatically replace ONNX's RandomNormal node with Constant node.
onnx-remove-random-normal This is a script to replace RandomNormal node with Constant node. Example Imagine that we have something ONNX model like the
Automatic and platform-independent unpacker for Windows binaries based on emulation
_ _ __ _ __ _ | | | | / / (_) \ \ | | | | | |_ __ | | _ | | _ __ __ _ ___| | _____ _ __
Research Artifact of USENIX Security 2022 Paper: Automated Side Channel Analysis of Media Software with Manifold Learning
Automated Side Channel Analysis of Media Software with Manifold Learning Official implementation of USENIX Security 2022 paper: Automated Side Channel
A Simple File Encryptor/Decryptor
Ec: A Simple File Encryptor/Decryptor This has been made for educational reasons only, any constructive criticism/advice/comments are welcome! Also, p

Collaborative forensic timeline analysis
Timesketch Table of Contents About Timesketch Getting started Community Contributing About Timesketch Timesketch is an open-source tool for collaborat

Security Monkey monitors AWS, GCP, OpenStack, and GitHub orgs for assets and their changes over time.
NOTE: Security Monkey is in maintenance mode and will be end-of-life in 2020. For AWS users, please make use of AWS Config. For GCP users, please make

A simple rest api that classifies pneumonia infection weather it is Normal, Pneumonia Virus or Pneumonia Bacteria from a chest-x-ray image.
This is a simple rest api that classifies pneumonia infection weather it is Normal, Pneumonia Virus or Pneumonia Bacteria from a chest-x-ray image.

Generate a wordlist to fuzz amounts or any other numerical values.
Generate a wordlist to fuzz amounts or any other numerical values. Based on Common Security Issues in Financially-Oriented Web Applications.
Easy and secure implementation of Azure AD for your FastAPI APIs 🔒 Single- and multi-tenant support.
Easy and secure implementation of Azure AD for your FastAPI APIs 🔒 Single- and multi-tenant support.

Authware API wrapper for Python 3.5+
AuthwarePy Asynchronous wrapper for Authware in Python 3.5+ View our documentation 📲 Installation Run this to install the library via pip: pip instal
Quickstart resources for the WiFi Nugget, a cat themed WiFi Security platform for beginners.
Quickstart resources for the WiFi Nugget, a cat themed WiFi Security platform for beginners.
OMIGOD! OM I GOOD? A free scanner to detect VMs vulnerable to one of the
omigood (OM I GOOD?) This repository contains a free scanner to detect VMs vulnerable to one of the "OMIGOD" vulnerabilities discovered by Wiz's threa
Repository for a project of the course EP2520 Building Networked Systems Security
EP2520_ACME_Project Repository for a project of the course EP2520 Building Networked Systems Security in Royal Institute of Technology (KTH), Stockhol

A simple application that calculates the probability distribution of a normal distribution
probability-density-function General info An application that calculates the probability density and cumulative distribution of a normal distribution
Decentra Network is an open source blockchain that combines speed, security and decentralization.
Decentra Network is an open source blockchain that combines speed, security and decentralization. Decentra Network has very high speeds, scalability, asymptotic security and complete decentralization.

Simulate Attacks With Mininet And Hping3
Miniattack Simulate Attacks With Mininet And Hping3 It measures network load with bwm-ng when the net is under attack and plots the result. This demo
The code is the training example of AAAI2022 Security AI Challenger Program Phase 8: Data Centric Robot Learning on ML models.
Example code of [Tianchi AAAI2022 Security AI Challenger Program Phase 8]
Um keylogger que se disfarça de um app que tira print da tela.
Keylogger_ Um keylogger que se disfarça de um app que tira print da tela. Este programa captura o print da tela e salva ,normalmente, na pasta Picture
Agile Threat Modeling Toolkit
Threagile is an open-source toolkit for agile threat modeling:

Hubble - Network, Service & Security Observability for Kubernetes using eBPF
Network, Service & Security Observability for Kubernetes What is Hubble? Getting Started Features Service Dependency Graph Metrics & Monitoring Flow V
Sign data using symmetric-key algorithm encryption.
Sign data using symmetric-key algorithm encryption. Validate signed data and identify possible validation errors. Uses sha-(1, 224, 256, 385 and 512)/hmac for signature encryption. Custom hash algorithms are allowed. Useful shortcut functions for signing (and validating) dictionaries and URLs.

Demo scripts for the Kubernetes Security Webinar
Kubernetes Security Webinar [in Russian] YouTube video (October 13, 2021) Authors: Artem Yushkovsky (LinkedIn, GitHub) Maxim Mosharov @ Whitespots.io

A multi-platform HTTP(S) Reverse Shell Server and Client in Python 3
Phantom - A multi-platform HTTP(S) Reverse Shell Server and Client Phantom is a multi-platform HTTP(S) Reverse Shell server and client in Python 3. Bi

Fast mesh denoising with data driven normal filtering using deep variational autoencoders
Fast mesh denoising with data driven normal filtering using deep variational autoencoders This is an implementation for the paper entitled "Fast mesh
A free project by a normal kamenrider fan
DEMONS DRIVER Python + OpenCV demons.py采集原视频中led灯珠颜色,并将结果输出到output文件夹 Arduino + WS2812B 基于FastLED 实现DEMONS驱动器的led面板效果 项目未完成,持续更新中 --------------------

Lazarus analysis tools and research report
Lazarus Research This repository publishes analysis reports and analysis tools for Operation Dream Job and Operation JTrack for Lazarus. Tools Python
Natas teaches the basics of serverside web-security.
over-the-wire-natas Natas teaches the basics of serverside web-security. Each level of natas consists of its own website located at http://natasX.nata
Exact algorithm for computing two-sided statistical tolerance intervals under a normal distribution assumption using Python.
norm-tol-int Exact algorithm for computing two-sided statistical tolerance intervals under a normal distribution assumption using Python. Methods The

About Hive Burp Suite Extension
Hive Burp Suite Extension Description Hive extension for Burp Suite. This extension allows you to send data from Burp to Hive in one click. Create iss
GitHub action for AppSweep Mobile Application Security Testing
GitHub action for AppSweep can be used to continuously integrate app scanning using AppSweep into your Android app build process

Blinder is a tool that will help you simplify the exploitation of blind SQL injection
Blinder Have you found a blind SQL injection? Great! Now you need to export it, but are you too lazy to sort through the values? Most likely,

An encryption format offering better security, performance and ease of use than PGP.
An encryption format offering better security, performance and ease of use than PGP. File a bug if you found anything where we are worse than our competition, and we will fix it.

Moodle community-based vulnerability scanner
badmoodle Moodle community-based vulnerability scanner Description badmoodle is an unofficial community-based vulnerability scanner for moodle that sc
A Simple Python CLI Lockpicking Tool
Cryptex a simple CLI lockpicking tool What can it do: Encode / Decode Hex Encode / Decode Base64 Break Randomly :D Requirements: Python3 Linux as your

🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.
🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.
A project studying the influence of communication in multi-objective normal-form games
Communication in Multi-Objective Normal-Form Games This repo consists of five different types of agents that we have used in our study of communicatio

Spray365 is a password spraying tool that identifies valid credentials for Microsoft accounts (Office 365 / Azure AD).
What is Spray365? Spray365 is a password spraying tool that identifies valid credentials for Microsoft accounts (Office 365 / Azure AD). How is Spray3
Encrypted Python Password Manager
PyPassKeep Encrypted Python Password Manager About PyPassKeep (PPK for short) is an encrypted python password manager used to secure your passwords fr
Pnuemonia Normal detection by using XRay images.
Pnuemonia Normal detection by using XRay images. Got image datas from kaggle(link is given in sources.txt file) also normal xray images from other site (also link is given) in order to avoid data disbalancing.

ChainJacking is a tool to find which of your Go lang direct GitHub dependencies is susceptible to ChainJacking attack.
ChainJacking is a tool to find which of your Go lang direct GitHub dependencies is susceptible to ChainJacking attack.
A tool that updates all your project's Python dependency files through Pull Requests on GitHub/GitLab.
A tool that updates all your project's Python dependency files through Pull Requests on GitHub/GitLab. About This repo contains the bot that is runnin

Fast and customizable vulnerability scanner For JIRA written in Python
Fast and customizable vulnerability scanner For JIRA. 🤔 What is this? Jira-Lens 🔍 is a Python Based vulnerability Scanner for JIRA. Jira is a propri
A normal phoneNumber tracker made with python.
A normal phoneNumber tracker made with python.

A Python Tool to encrypt all types of files using AES and XOR Algorithm.
DataShield This project intends to protect user’s data, it stores files in encrypted format in device provided the passcode and path of the file. AES
Course: Information Security with Python
Curso: Segurança da Informação com Python Curso realizado atravès da Plataforma da Digital Innovation One Prof: Bruno Dias Conteúdo: Introdução aos co

A Security Tool for Enumerating WebSockets
STEWS: Security Testing and Enumeration of WebSockets STEWS is a tool suite for security testing of WebSockets This research was first presented at OW

An implementation of a discriminant function over a normal distribution to help classify datasets.
CS4044D Machine Learning Assignment 1 By Dev Sony, B180297CS The question, report and source code can be found here. Github Repo Solution 1 Based on t

RINDNet: Edge Detection for Discontinuity in Reflectance, Illumination, Normal and Depth, in ICCV 2021 (oral)
RINDNet RINDNet: Edge Detection for Discontinuity in Reflectance, Illumination, Normal and Depth Mengyang Pu, Yaping Huang, Qingji Guan and Haibin Lin

Code for "Adversarial attack by dropping information." (ICCV 2021)
AdvDrop Code for "AdvDrop: Adversarial Attack to DNNs by Dropping Information(ICCV 2021)." Human can easily recognize visual objects with lost informa

Members: Thomas Longuevergne Program: Network Security Course: 1DV501 Date of submission: 2021-11-02
Mini-project report Members: Thomas Longuevergne Program: Network Security Course: 1DV501 Date of submission: 2021-11-02 Introduction This project was

3D-CariGAN: An End-to-End Solution to 3D Caricature Generation from Normal Face Photos
3D-CariGAN: An End-to-End Solution to 3D Caricature Generation from Normal Face Photos This repository contains the source code and dataset for the pa
Security System using OpenCV
Security-System Security System using OpenCV Files in this Repository: email_send.py - This file contains python code to send an email when something

Security evaluation module with onnx, pytorch, and SecML.
🚀 🐼 🔥 PandaVision Integrate and automate security evaluations with onnx, pytorch, and SecML! Installation Starting the server without Docker If you
Use scrapli to retrieve security zone information from a Juniper SRX firewall
Get Security Zones with Scrapli Overview This example will show how to retrieve security zone information on Juniper's SRX firewalls. In addition to t
Arp Spoofer using Python 3.
ARP Spoofer / Wifi Killer By Auax Run: Run the application with the following command: python3 spoof.py -t target_ip_address -lh host_ip_address I
Arp Spoofer using Python 3.
ARP Spoofer / Wifi Killer By Auax Run: Run the application with the following command: python3 spoof.py -t target_ip_address -lh host_ip_address I
[CVPR 2021] NormalFusion: Real-Time Acquisition of Surface Normals for High-Resolution RGB-D Scanning
NormalFusion: Real-Time Acquisition of Surface Normals for High-Resolution RGB-D Scanning Project Page | Paper | Supplemental material #1 | Supplement
🍉一款基于Python-Django的多功能Web安全渗透测试工具,包含漏洞扫描,端口扫描,指纹识别,目录扫描,旁站扫描,域名扫描等功能。
Sec-Tools 项目介绍 系统简介 本项目命名为Sec-Tools,是一款基于 Python-Django 的在线多功能 Web 应用渗透测试系统,包含漏洞检测、目录识别、端口扫描、指纹识别、域名探测、旁站探测、信息泄露检测等功能。本系统通过旁站探测和域名探测功能对待检测网站进行资产收集,通过端
A simple python program to record security cam footage by detecting a face and body of a person in the frame.
SecurityCam A simple python program to record security cam footage by detecting a face and body of a person in the frame. This code was created by me,
This tool parses log data and allows to define analysis pipelines for anomaly detection.
logdata-anomaly-miner This tool parses log data and allows to define analysis pipelines for anomaly detection. It was designed to run the analysis wit
GitGuardian Shield: protect your secrets with GitGuardian
Detect secret in source code, scan your repo for leaks. Find secrets with GitGuardian and prevent leaked credentials. GitGuardian is an automated secrets detection & remediation service.

This tool allows to automatically test for Content Security Policy bypass payloads.
CSPass This tool allows to automatically test for Content Security Policy bypass payloads. Usage [cspass]$ ./cspass.py -h usage: cspass.py [-h] [--no-
A lightweight Python module to interact with the Mitre Att&ck Enterprise dataset.
enterpriseattack - Mitre's Enterprise Att&ck A lightweight Python module to interact with the Mitre Att&ck Enterprise dataset. Built to be used in pro
A (completely native) python3 wifi brute-force attack using the 100k most common passwords (2021)
wifi-bf [LINUX ONLY] A (completely native) python3 wifi brute-force attack using the 100k most common passwords (2021) This script is purely for educa
Tools to assist with the configuration and maintenance of fapolicyd.
Tools to assist with the configuration and maintenance of fapolicyd.
A facial recognition program that plays a alarm (mp3 file) when a person i seen in the room. A basic theif using Python and OpenCV
Home-Security-Demo A facial recognition program that plays a alarm (mp3 file) when a person is seen in the room. A basic theif using Python and OpenCV
ICMP Reverse Shell written in Python 3 and with Scapy (backdoor/rev shell)
icmpdoor - ICMP Reverse Shell icmpdoor is an ICMP rev shell written in Python3 and scapy. Tested on Ubuntu 20.04, Debian 10 (Kali Linux), and Windows
Scrapy-based cyber security news finder
Cyber-Security-News-Scraper Scrapy-based cyber security news finder Goal To keep up to date on the constant barrage of information within the field of
A python open source CMS scanner that automates the process of detecting security flaws of the most popular CMSs
CMSmap CMSmap is a python open source CMS scanner that automates the process of detecting security flaws of the most popular CMSs. The main purpose of
Short PhD seminar on Machine Learning Security (Adversarial Machine Learning)
Short PhD seminar on Machine Learning Security (Adversarial Machine Learning)
Discord-Protect is a simple discord bot allowing you to have some security on your discord server by ordering a captcha to the user who joins your server.
Discord-Protect Discord-Protect is a simple discord bot allowing you to have some security on your discord server by ordering a captcha to the user wh

AutoExploitSwagger is an automated API security testing exploit tool that can be combined with xray, BurpSuite and other scanners.
AutoExploitSwagger is an automated API security testing exploit tool that can be combined with xray, BurpSuite and other scanners.

Security tool to test different bypass of forbidden
notForbidden Security tool to test different bypass of forbidden Usage python3 notForbidden.py URL Features Bypass with different methods (POST, OPT
Set the draft security HTTP header Permissions-Policy (previously Feature-Policy) on your Django app.
django-permissions-policy Set the draft security HTTP header Permissions-Policy (previously Feature-Policy) on your Django app. Requirements Python 3.
Enrich IP addresses with metadata and security IoC
Stratosphere IP enrich Get an IP address and enrich it with metadata and IoC You need API keys for VirusTotal and PassiveTotal (RiskIQ) How to use fro
BinCat is an innovative login system, with which the account you register will be more secure.
BinCat is an innovative login system, with which the account you register will be more secure. This project is inspired by a conventional token system.
External Network Pentest Automation using Shodan API and other tools.
Chopin External Network Pentest Automation using Shodan API and other tools. Workflow Input a file containing CIDR ranges. Converts CIDR ranges to ind
D(HE)ater is a security tool can perform DoS attack by enforcing the DHE key exchange.
D(HE)ater D(HE)ater is an attacking tool based on CPU heating in that it forces the ephemeral variant of Diffie-Hellman key exchange (DHE) in given cr

The ibet-Prime security token management system for ibet network.
ibet-Prime The ibet-Prime security token management system for ibet network. Features ibet-Prime is an API service that enables the issuance and manag
Security offerings for AWS Control Tower
Caylent Security Catalyst Reference Architecture Examples This repository contains solutions for Caylent's Security Catalyst. The Security Catalyst is
A CLI tool to disable and enable security standards controls in AWS Security Hub
Security Hub Controls CLI A CLI tool to disable and enable security standards controls in AWS Security Hub. It is designed to work together with AWS S
Audio Steganography is a technique used to transmit hidden information by modifying an audio signal in an imperceptible manner.
Audio Steganography Audio Steganography is a technique used to transmit hidden information by modifying an audio signal in an imperceptible manner. Ab
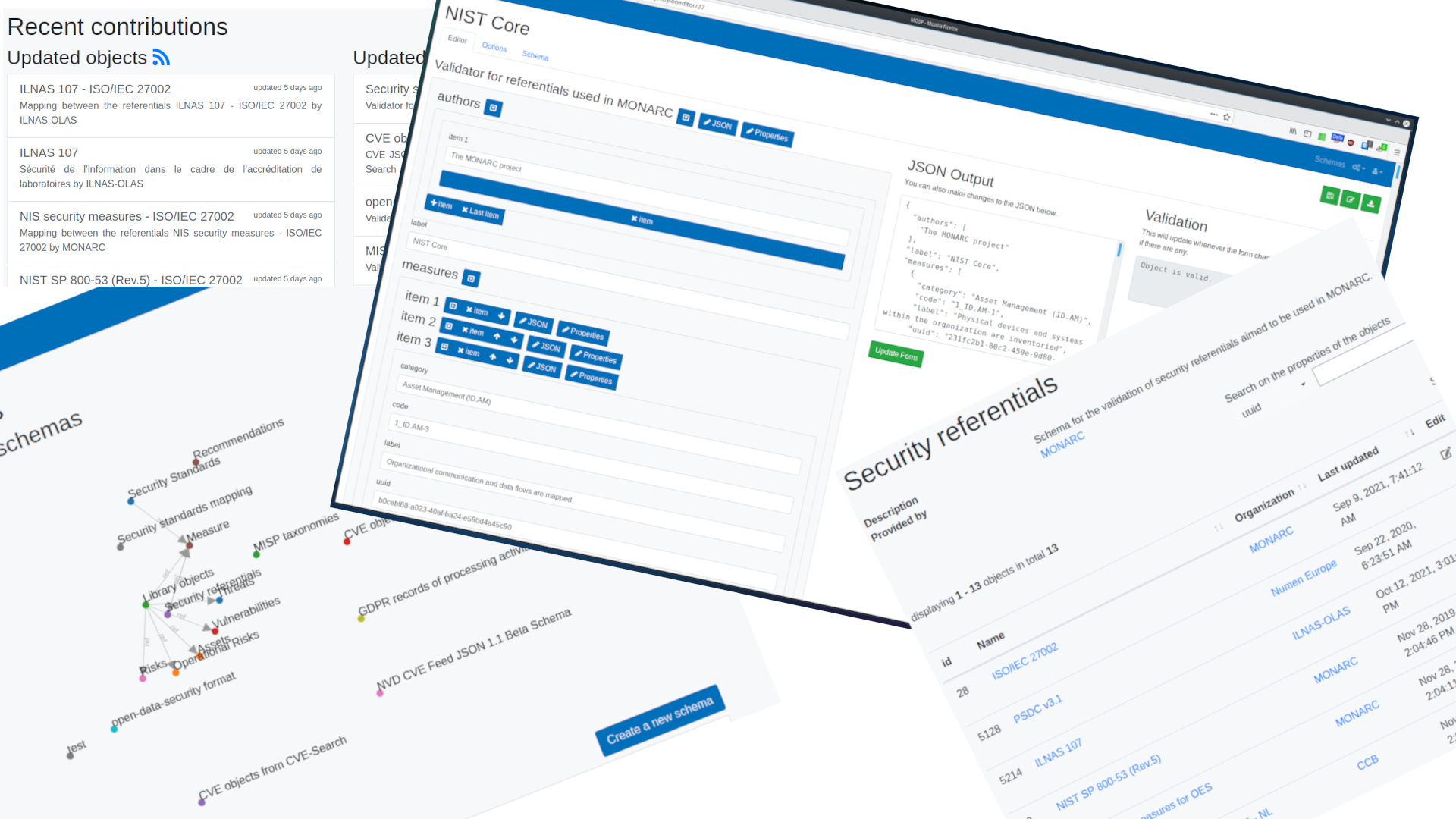
MOSP is a platform for creating, editing and sharing validated JSON objects of any type.
MONARC Objects Sharing Platform Presentation MOSP is a platform for creating, editing and sharing validated JSON objects of any type. You can use any

ONYX SMTP Sender est un tool qui vous serviras à envoyer des email html à une liste d'email (en .txt) c'est la première version du tool et je le sors un peu à la rache donc si le logiciel est obsolète c'est normal j'y taff encore ;)
SMTP-Sender ONYX SMTP Sender est un tool qui vous serviras à envoyer des email html à une liste d'email (en .txt) c'est la première version du tool et

Brute force a JWT token. Script uses multithreading.
JWT BF Brute force a JWT token. Script uses multithreading. Tested on Kali Linux v2021.4 (64-bit). Made for educational purposes. I hope it will help!

boofuzz: Network Protocol Fuzzing for Humans
boofuzz: Network Protocol Fuzzing for Humans Boofuzz is a fork of and the successor to the venerable Sulley fuzzing framework. Besides numerous bug fi

Passhunt is a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords.
Passhunt is a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords.

The core packages of security analyzer web crawler
Security Analyzer 🐍 A large scale web crawler (considered also as vulnerability scanner tool) to take an overview about security of Moroccan sites Cu
