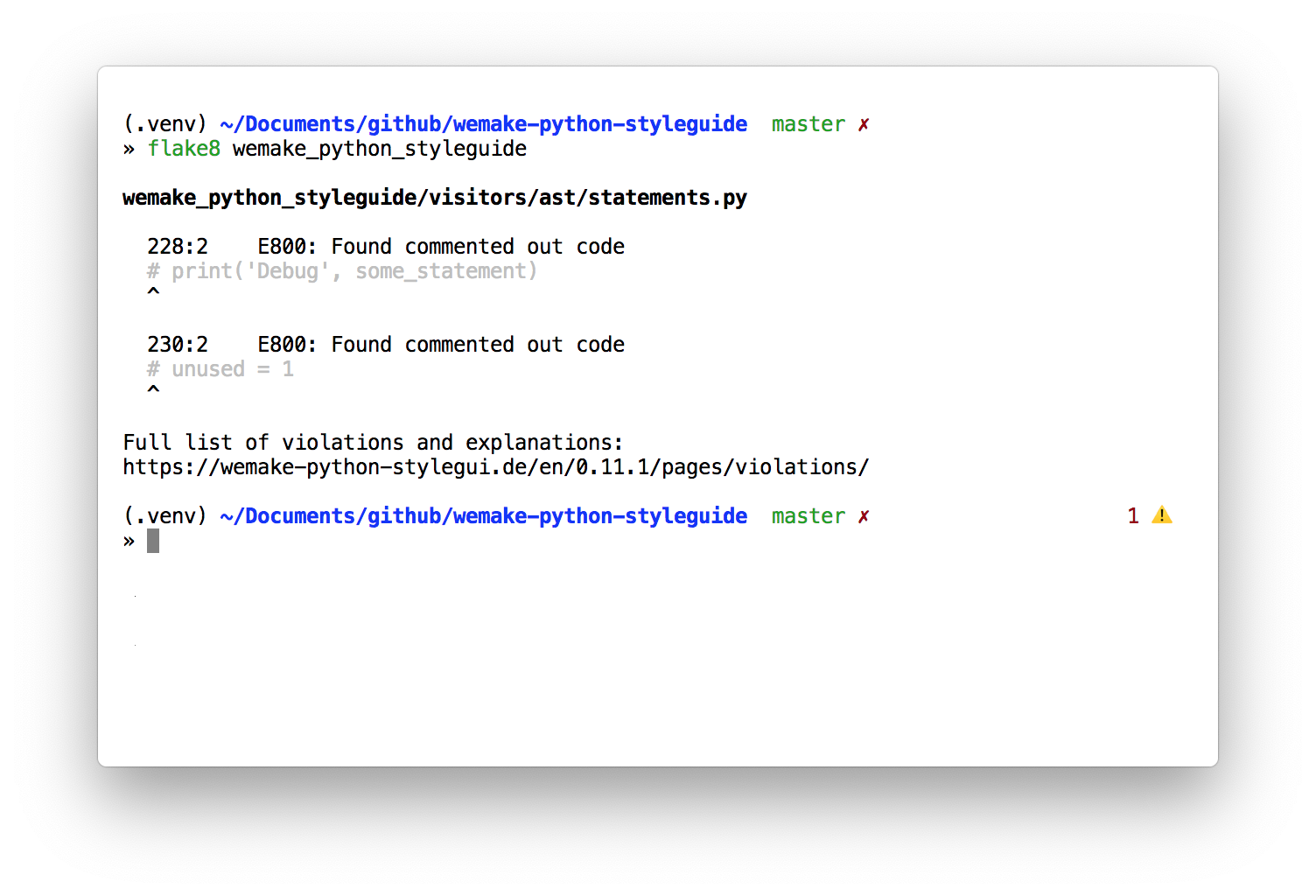
bot deployed to heroku doesn't work, error with bot token format or something similar with config (need config example)
- deployed to heroku
- bot created using @BotFather (token mask something like this
token = os.environ.get('5337.....60:AAE2.....YLq7c') (only without dots for sure)
- log:
heroku logs --tail TypeError: 'NoneType' object is not iterable or another problem
but bot doesn't work
2022-05-18T21:01:18.695184+00:00 heroku[web.1]: Starting process with command `python3 bot.py`
2022-05-18T21:01:20.535054+00:00 app[web.1]: Traceback (most recent call last):
2022-05-18T21:01:20.535078+00:00 app[web.1]: File "/app/bot.py", line 11, in <module>
2022-05-18T21:01:20.535185+00:00 app[web.1]: from whoisbot.callbacks import gatekeep_callback, remove_users_callback,\
2022-05-18T21:01:20.535187+00:00 app[web.1]: File "/app/whoisbot/callbacks.py", line 4, in <module>
2022-05-18T21:01:20.535263+00:00 app[web.1]: from .base import new_chat, new_user, \
2022-05-18T21:01:20.535271+00:00 app[web.1]: File "/app/whoisbot/base.py", line 3, in <module>
2022-05-18T21:01:20.535344+00:00 app[web.1]: from .config import chats, users, bot
2022-05-18T21:01:20.535353+00:00 app[web.1]: File "/app/whoisbot/config.py", line 18, in <module>
2022-05-18T21:01:20.535424+00:00 app[web.1]: bot = Bot(token)
2022-05-18T21:01:20.535436+00:00 app[web.1]: File "/app/.heroku/python/lib/python3.10/site-packages/telegram/bot.py", line 191, in __init__
2022-05-18T21:01:20.535560+00:00 app[web.1]: self.token = self._validate_token(token)
2022-05-18T21:01:20.535571+00:00 app[web.1]: File "/app/.heroku/python/lib/python3.10/site-packages/telegram/bot.py", line 350, in _validate_token
2022-05-18T21:01:20.535750+00:00 app[web.1]: if any(x.isspace() for x in token):
2022-05-18T21:01:20.535780+00:00 app[web.1]: TypeError: 'NoneType' object is not iterable
2022-05-18T21:01:20.759209+00:00 heroku[web.1]: Process exited with status 1
2022-05-18T21:01:20.804964+00:00 heroku[web.1]: State changed from starting to crashed
2022-05-18T21:01:20.808413+00:00 heroku[web.1]: State changed from crashed to starting
2022-05-18T21:01:24.692119+00:00 heroku[web.1]: Starting process with command `python3 bot.py`
2022-05-18T21:01:25.000000+00:00 app[api]: Build succeeded
2022-05-18T21:01:27.013194+00:00 app[web.1]: Traceback (most recent call last):
2022-05-18T21:01:27.013211+00:00 app[web.1]: File "/app/bot.py", line 11, in <module>
2022-05-18T21:01:27.013306+00:00 app[web.1]: from whoisbot.callbacks import gatekeep_callback, remove_users_callback,\
2022-05-18T21:01:27.013309+00:00 app[web.1]: File "/app/whoisbot/callbacks.py", line 4, in <module>
2022-05-18T21:01:27.013371+00:00 app[web.1]: from .base import new_chat, new_user, \
2022-05-18T21:01:27.013381+00:00 app[web.1]: File "/app/whoisbot/base.py", line 3, in <module>
2022-05-18T21:01:27.013442+00:00 app[web.1]: from .config import chats, users, bot
2022-05-18T21:01:27.013453+00:00 app[web.1]: File "/app/whoisbot/config.py", line 18, in <module>
2022-05-18T21:01:27.013514+00:00 app[web.1]: bot = Bot(token)
2022-05-18T21:01:27.013530+00:00 app[web.1]: File "/app/.heroku/python/lib/python3.10/site-packages/telegram/bot.py", line 191, in __init__
2022-05-18T21:01:27.013631+00:00 app[web.1]: self.token = self._validate_token(token)
2022-05-18T21:01:27.013641+00:00 app[web.1]: File "/app/.heroku/python/lib/python3.10/site-packages/telegram/bot.py", line 350, in _validate_token
2022-05-18T21:01:27.013872+00:00 app[web.1]: if any(x.isspace() for x in token):
2022-05-18T21:01:27.013926+00:00 app[web.1]: TypeError: 'NoneType' object is not iterable
2022-05-18T21:01:27.282739+00:00 heroku[web.1]: Process exited with status 1
2022-05-18T21:01:27.364370+00:00 heroku[web.1]: State changed from starting to crashed
2022-05-18T21:02:48.763234+00:00 heroku[router]: at=error code=H10 desc="App crashed" method=GET path="/" host=whoisbotmy.herokuapp.com request_id=84b52fc5-a65c-452e-a38f-77f2c363d62c fwd="78.162.147.110" dyno= connect= service= status=503 bytes= protocol=https
2022-05-18T21:02:50.256201+00:00 heroku[router]: at=error code=H10 desc="App crashed" method=GET path="/favicon.ico" host=whoisbotmy.herokuapp.com request_id=f905210c-ca3e-424d-9a64-ac1dd53d5777 fwd="IP" dyno= connect= service= status=503 bytes= protocol=https