238 Repositories
Python apache-log4j-rce-poc Libraries

Spring4Shell Proof Of Concept/And vulnerable application CVE-2022-22965
Spring4Shell-POC (CVE-2022-22965) Spring4Shell (CVE-2022-22965) Proof Of Concept/Information + A vulnerable Tomcat server with a vulnerable spring4she

Dockerized Spring4Shell (CVE-2022-22965) PoC application and exploit
Spring4Shell PoC Application This is a dockerized application that is vulnerable to the Spring4Shell vulnerability (CVE-2022-22965). Full Java source
CVE-2022-22963 PoC
CVE-2022-22963 CVE-2022-22963 PoC Slight modified for English translation and detection of https://github.com/chaosec2021/Spring-cloud-function-SpEL-R

Pocsploit is a lightweight, flexible and novel open source poc verification framework
Pocsploit is a lightweight, flexible and novel open source poc verification framework

Spring4Shell - Spring Core RCE - CVE-2022-22965
Spring Core RCE - CVE-2022-22965 After Spring Cloud, on March 29, another heavyweight vulnerability of Spring broke out on the Internet: Spring Core R
A Safer PoC for CVE-2022-22965 (Spring4Shell)
Safer_PoC_CVE-2022-22965 A Safer PoC for CVE-2022-22965 (Spring4Shell) Functionality Creates a file called CVE_2022-22965_exploited.txt in the tomcat
POC for CVE-2022-1388
CVE-2022-1388 POC for CVE-2022-1388 affecting multiple F5 products. Follow the Horizon3.ai Attack Team on Twitter for the latest security research: Ho

Yet another Airflow plugin using CLI command as RESTful api, supports Airflow v2.X.
中文版文档 Airflow Extended API Plugin Airflow Extended API, which export airflow CLI command as REST-ful API to extend the ability of airflow official API
Containerized Demo of Apache Spark MLlib on a Data Lakehouse (2022)
Spark-DeltaLake-Demo Reliable, Scalable Machine Learning (2022) This project was completed in an attempt to become better acquainted with the latest b

CVE-2022-1388 F5 BIG-IP iControl REST Auth Bypass RCE
CVE-2022-1388 CVE-2022-1388 F5 BIG-IP iControl REST Auth Bypass RCE. POST /mgmt/tm/util/bash HTTP/1.1 Host: Accept-Encoding: gzip, deflate Accept: */

CVE-2022-22965 : about spring core rce
CVE-2022-22965: Spring-Core-Rce EXP 特性: 漏洞探测(不写入 webshell,简单字符串输出) 自定义写入 webshell 文件名称及路径 不会追加写入到同一文件中,每次检测写入到不同名称 webshell 文件 支持写入 冰蝎 webshell 代理支持,可

S2-062 (CVE-2021-31805) / S2-061 / S2-059 RCE
CVE-2021-31805 Remote code execution S2-062 (CVE-2021-31805) Due to Apache Struts2's incomplete fix for S2-061 (CVE-2020-17530), some tag attributes c
Laravel RCE (CVE-2021-3129)
CVE-2021-3129 - Laravel RCE About The script has been made for exploiting the Laravel RCE (CVE-2021-3129) vulnerability. This script allows you to wri
We’re releasing an open-source tool you can use now, which we developed as a homemade Just-In-Time database access control tool for our sensitive database. This tool syncs with our directory service, slack, SIEM, and finally, our Apache Cassandra database.
Cassandra Access Control By Aner Izraeli - Intezer Security Manager ([email protected]) We’re releasing an open-source tool you can use now, which

spring-cloud-gateway-rce CVE-2022-22947
Spring Cloud Gateway Actuator API SpEL表达式注入命令执行(CVE-2022-22947) 1.installation pip3 install -r requirements.txt 2.Usage $ python3 spring-cloud-gateway
Spring Cloud Gateway 3.0.7 & 3.1.1 Code Injection (RCE)
Spring Cloud Gateway 3.0.7 & 3.1.1 Code Injection (RCE) CVE: CVE-2022-22947 CVSS: 10.0 (Vmware - https://tanzu.vmware.com/security/cve-2022-22947)
Files related to PoC||GTFO 21:21 - NSA’s Backdoor of the PX1000-Cr
Files related to PoC||GTFO 21:21 - NSA’s Backdoor of the PX1000-Cr 64bit2key.py

Backup dc registry - A simple POC that abuses Backup Operator privileges to remote dump SAM, SYSTEM, and SECURITY
Backup Operator Registry Backup to Domain Compromise A simple POC that abuses Ba
DAMPP (gui) is a Python based program to run simple webservers using MySQL, Php, Apache and PhpMyAdmin inside of Docker containers.
DAMPP (gui) is a Python based program to run simple webservers using MySQL, Php, Apache and PhpMyAdmin inside of Docker containers.
A tool to find good RCE From my series: A powerful Burp extension to make bounties rain
A tool to find good RCE From my series: A powerful Burp extension to make bounties rain
AnonStress-Stored-XSS-Exploit - An exploit and demonstration on how to exploit a Stored XSS vulnerability in anonstress
AnonStress Stored XSS Exploit An exploit and demonstration on how to exploit a S

Jupyter notebooks and AWS CloudFormation template to show how Hudi, Iceberg, and Delta Lake work
Modern Data Lake Storage Layers This repository contains supporting assets for my research in modern Data Lake storage layers like Apache Hudi, Apache

PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1
CVE-2021-45897 PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1 This vulnerability was repor
Piglet-shaders - PoC of custom shaders for Piglet
Piglet custom shader PoC This is a PoC for compiling Piglet fragment shaders usi
PortSwigger Burp Plugin for the Log4j (CVE-2021-44228)
yLog4j This is Y-Sec's @PortSwigger Burp Plugin for the Log4j CVE-2021-44228 vulnerability. The focus of yLog4j is to support mass-scanning of the Log

PySpark Structured Streaming ROS Kafka ApacheSpark Cassandra
PySpark-Structured-Streaming-ROS-Kafka-ApacheSpark-Cassandra The purpose of this project is to demonstrate a structured streaming pipeline with Apache
Python-geoarrow - Storing geometry data in Apache Arrow format
geoarrow Storing geometry data in Apache Arrow format Installation $ pip install

This is a simple PoC for the newly found Polkit error names PwnKit
A Python3 and a BASH PoC for CVE-2021-4034 by Kim Schulz
Simple tool downloads public PoC (refer from nomi-sec)
PoC Collection This is the little script to collect the proof-of-concept which is refered from nomi-sec. The repository now is only develop for linux-
CVE-2022-21907 Vulnerability PoC
CVE-2022-21907 Description POC for CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability. create by antx at 2022-01-17, just some sm
Simple Python Script to Parse Apache Log, Get all Unique IPs and Urls visited by that IP
Parse_Apache_Log Simple Python Script to Parse Apache Log, Get all Unique IPs and Urls visited by that IP. It will create 3 different files. allIP.txt
Event-driven-model-serving - Unified API of Apache Kafka and Google PubSub
event-driven-model-serving Unified API of Apache Kafka and Google PubSub 1. Proj

Proof of concept of CVE-2022-21907 Double Free in http.sys driver, triggering a kernel crash on IIS servers
CVE-2022-21907 - Double Free in http.sys driver Summary An unauthenticated attacker can send an HTTP request with an "Accept-Encoding" HTTP request he
SynapseML - an open source library to simplify the creation of scalable machine learning pipelines
Synapse Machine Learning SynapseML (previously MMLSpark) is an open source library to simplify the creation of scalable machine learning pipelines. Sy
POC of CVE-2021-26084, which is Atlassian Confluence Server OGNL Pre-Auth RCE Injection Vulneralibity.
CVE-2021-26084 Description POC of CVE-2021-26084, which is Atlassian Confluence Server OGNL(Object-Graph Navigation Language) Pre-Auth RCE Injection V

JWT Key Confusion PoC (CVE-2015-9235) Written for the Hack the Box challenge - Under Construction
JWT Key Confusion PoC (CVE-2015-9235) Written for the Hack the Box challenge - Under Construction This script performs a Java Web Token Key Confusion
Unauthenticated Sqlinjection that leads to dump data base but this one impersonated Admin and drops a interactive shell
Unauthenticated Sqlinjection that leads to dump database but this one impersonated Admin and drops a interactive shell
SonicWall SMA-100 Unauth RCE Exploit (CVE-2021-20038)
Bad Blood Bad Blood is an exploit for CVE-2021-20038, a stack-based buffer overflow in the httpd binary of SMA-100 series systems using firmware versi

Automated tool to find & created Exploit Poc for Clickjacking Vulnerability
ClickJackPoc This tool will help you automate finding Clickjacking Vulnerability by just passing a file containing list of Targets . Once the Target i
Validate arbitrary image uploads from incoming data urls while preserving file integrity but removing EXIF and unwanted artifacts and RCE exploit potential
Validate arbitrary base64-encoded image uploads as incoming data urls while preserving image integrity but removing EXIF and unwanted artifacts and mitigating RCE-exploit potential.
⚡ PoC: Hide a c&c botnet in the discord client. (Proof Of Concept)
Discord-BotnetClient Embed C&C botnet into the discord client. Working trought websocket c&c server. How to use. pip3 install websocket_server colored

Log4jScanner is a Log4j Related CVEs Scanner, Designed to Help Penetration Testers to Perform Black Box Testing on given subdomains.
Log4jScanner Log4jScanner is a Log4j Related CVEs Scanner, Designed to Help Penetration Testers to Perform Black Box Testing on given subdomains. Disc
A Time Series Library for Apache Spark
Flint: A Time Series Library for Apache Spark The ability to analyze time series data at scale is critical for the success of finance and IoT applicat
Apache Spark & Python (pySpark) tutorials for Big Data Analysis and Machine Learning as IPython / Jupyter notebooks
Spark Python Notebooks This is a collection of IPython notebook/Jupyter notebooks intended to train the reader on different Apache Spark concepts, fro

CVE-2021-45232-RCE-多线程批量漏洞检测
CVE-2021-45232-RCE CVE-2021-45232-RCE-多线程批量漏洞检测 FOFA 查询 title="Apache APISIX Das

BigDL - Evaluate the performance of BigDL (Distributed Deep Learning on Apache Spark) in big data analysis problems
Evaluate the performance of BigDL (Distributed Deep Learning on Apache Spark) in big data analysis problems.

(D)arth (S)ide of the (L)og4j (F)orce, the ultimate log4j vulnerabilities assessor
DSLF DSLF stands for (D)arth (S)ide of the (L)og4j (F)orce. It is the ultimate log4j vulnerabilities assessor. It comes with four individual Python3 m
Details,PoC and patches for CVE-2021-45383 & CVE-2021-45384
CVE-2021-45383 & CVE-2021-45384 There are several network-layer vulnerabilities in the official server of Minecraft: Bedrock Edition (aka Bedrock Serv

Powering up Apache JMeter with Streamlit and opening the door for machine learning.
Powering up Apache JMeter with Streamlit Overview Apache JMeter is an open source load testing tool written in 100% pure Java. JMeter supports umpteen

Stream-Kafka-ELK-Stack - Weather data streaming using Apache Kafka and Elastic Stack.
Streaming Data Pipeline - Kafka + ELK Stack Streaming weather data using Apache Kafka and Elastic Stack. Data source: https://openweathermap.org/api O

CVE-log4j CheckMK plugin
CVE-2021-44228-log4j discovery (Download the MKP package) This plugin discovers vulnerable files for the CVE-2021-44228-log4j issue. To discover this

Use Jupyter Notebooks to demonstrate how to build a Recommender with Apache Spark & Elasticsearch
Recommendation engines are one of the most well known, widely used and highest value use cases for applying machine learning. Despite this, while there are many resources available for the basics of training a recommendation model, there are relatively few that explain how to actually deploy these models to create a large-scale recommender system.

MS-FSRVP coercion abuse PoC
ShadowCoerce MS-FSRVP coercion abuse PoC Credits: Gilles LIONEL (a.k.a. Topotam)

BurpSuite Extension: Log4j2 RCE Scanner
Log4j2 RCE Scanner 作者:key@元亨实验室 声明:由于传播、利用本项目所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,项目作者不为此承担任何责任。 小广告:实验室纳新招人,岗位方向有安全研究(攻防、漏洞)、威胁情报(APT分析)、内部安全(SDL、安全研发)
CVE-2021-43936 is a critical vulnerability (CVSS3 10.0) leading to Remote Code Execution (RCE) in WebHMI Firmware.
CVE-2021-43936 CVE-2021-43936 is a critical vulnerability (CVSS3 10.0) leading to Remote Code Execution (RCE) in WebHMI Firmware. This vulnerability w

This mini project showcase how to build and debug Apache Spark application using Python
Spark app can't be debugged using normal procedure. This mini project showcase how to build and debug Apache Spark application using Python programming language. There are also options to run Spark application on Spark container

Deobfuscate Log4Shell payloads with ease
Ox4Shell Deobfuscate Log4Shell payloads with ease. Description Since the release
PoC encrypted diary in Python 3
Encrypted diary Sample program to store confidential data. Provides encryption in the form of AES-256 with bcrypt KDF. Does not provide authentication

CVE-2021-44228 log4j 2.x rce漏洞检测工具
#1 使用说明 CVE-2021-44228 log4j 2.x rce漏洞检测工具,对目标链接发起get请求并利用dnslog探测是否有回显 $ python3 log4j-scan.py -h

open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability
CVE-2021-44228-log4jVulnScanner-metasploit open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability pre
Searches filesystem for CVE-2021-44228 and CVE-2021-45046 vulnerable instances of log4j library, including embedded (jar/war/zip) packaged ones.
log4shell_finder Python port of https://github.com/mergebase/log4j-detector log4j-detector is copyright (c) 2021 - MergeBase Software Inc. https://mer
A collection of intelligence about Log4Shell and its exploitation activity
Log4Shell-IOCs Members of the Curated Intelligence Trust Group have compiled a list of IOC feeds and threat reports focused on the recent Log4Shell ex
proof-of-concept running docker container from omero web
docker-from-omero-poc proof-of-concept running docker container from omero web How-to Edit test_script.py so that the BaseClient is created pointing t
log4j2 dos exploit,CVE-2021-45105 exploit,Denial of Service poc
说明 about author: 我超怕的 blog: https://www.cnblogs.com/iAmSoScArEd/ github: https://github.com/iAmSOScArEd/ date: 2021-12-20 log4j2 dos exploit log4j2 do
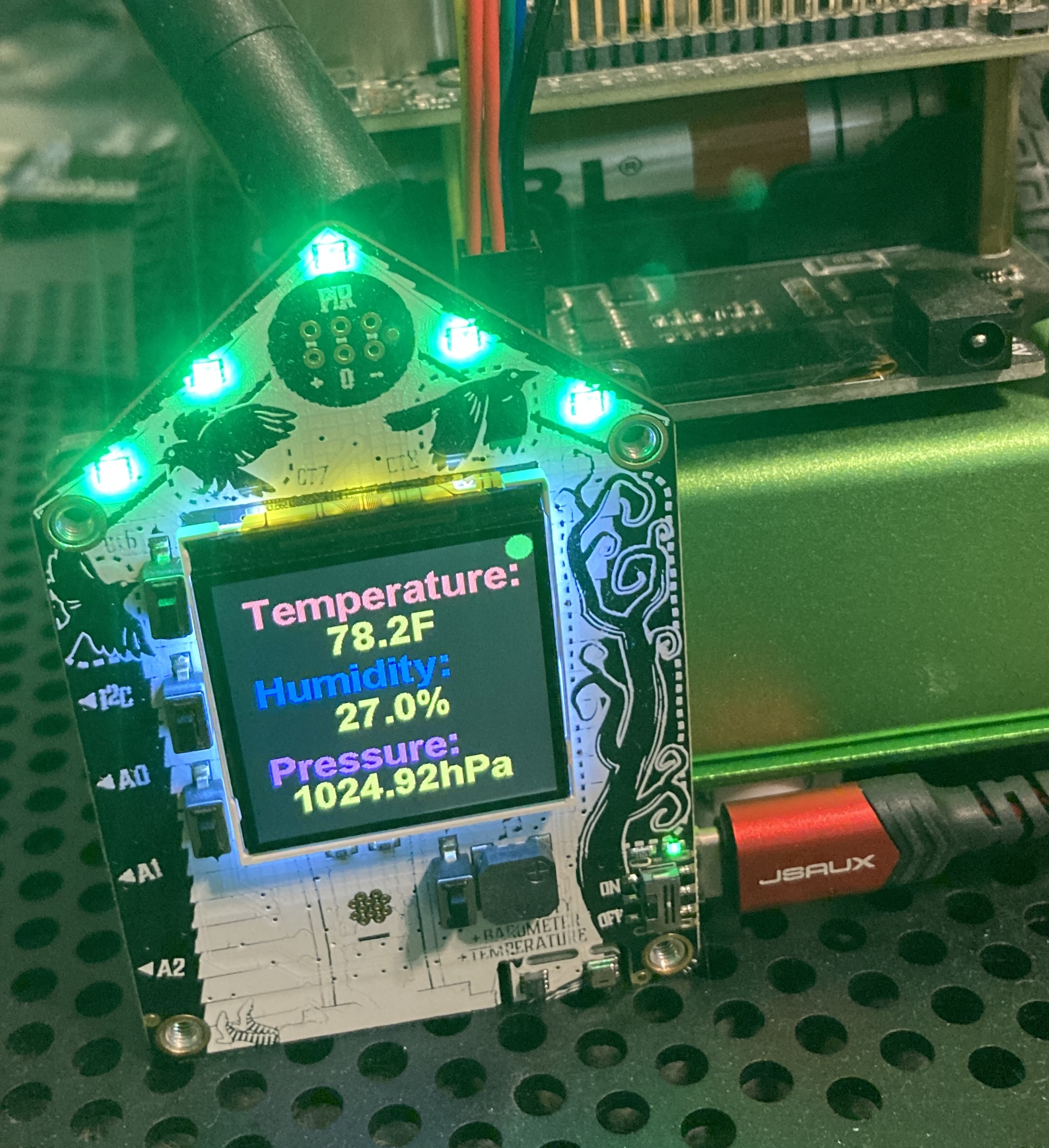
AdaFruit Funhouse publishing Temperature, Humidity and Pressure to MQTT / Apache Pulsar
pulsar-adafruit-funhouse AdaFruit Funhouse publishing Temperature, Humidity and Pressure to MQTT / Apache Pulsar Device Get your own from adafruit Ada
A script to search, scrape and scan for Apache Log4j CVE-2021-44228 affected files using Google dorks
Log4j dork scanner This is an auto script to search, scrape and scan for Apache Log4j CVE-2021-44228 affected files using Google dorks. Installation:
A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts
log4j-scan A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts Features Support for lists of URLs. Fuzzing for more

Log4j vuln fuzz/scan with python
Log4jFuzz log4j vuln fuzz/scan USE // it's use localhost udp server to check target vuln. python3 log4jFuzz.py [option] optional arguments: -u URL,

CVE-2021-22005 - VMWare vCenter Server File Upload to RCE
CVE-2021-22005 - VMWare vCenter Server File Upload to RCE Analyze Usage ------------------------------------------------------------- [*] CVE-2021-220

Scans all drives for log4j jar files and gets their version from the manifest
log4shell_scanner Scans all drives for log4j jar files and gets their version from the manifest. Windows and Windows Server only.
A Python Scanner for log4j
log4j-Scanner scanner for log4j cat web-urls.txt | python3 log4j.py ID.burpcollaborator.net web-urls.txt http://127.0.0.1:8080 https://www.google.c
Visibility and Mitigation for Log4J vulnerabilities
Visibility and Mitigation for Log4J vulnerabilities Several scripts for the visibility and mitigation of Log4J vulnerabilities. Static Scanner - Linux
Something I built to test for Log4J vulnerabilities on customer networks.
Log4J-Scanner Something I built to test for Log4J vulnerabilities on customer networks. I'm not responsible if your computer blows up, catches fire or
An automated header extensive scanner for detecting log4j RCE CVE-2021-44228
log4j An automated header extensive scanner for detecting log4j RCE CVE-2021-44228 Usage $ python3 log4j.py -l urls.txt --dns-log REPLACE_THIS.dnslog.

A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability
log4j-shell-poc A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability. Recently there was a new vulnerability in log4j, a java loggin
A scanner and a proof of sample exploit for log4j RCE CVE-2021-44228
1.Create a Sample Vulnerable Application . 2.Start a netcat listner . 3.Run the exploit . 5.Use jdk1.8.0_20 for better results . Exploit-db - https://
Simulating Log4j Remote Code Execution (RCE) vulnerability in a flask web server using python's logging library with custom formatter that simulates lookup substitution by executing remote exploit code.
py4jshell Simulating Log4j Remote Code Execution (RCE) CVE-2021-44228 vulnerability in a flask web server using python's logging library with custom f

Library extending Jupyter notebooks to integrate with Apache TinkerPop and RDF SPARQL.
Graph Notebook: easily query and visualize graphs The graph notebook provides an easy way to interact with graph databases using Jupyter notebooks. Us
A small POC plugin for launching dumpulator emulation within IDA, passing it addresses from your IDA view using the context menu.
Dumpulator-IDA Currently proof-of-concept This project is a small POC plugin for launching dumpulator emulation within IDA, passing it addresses from
This python script will automate the testing for the Log4J vulnerability for HTTP and HTTPS connections.
Log4J-Huntress-Automate-Script This python script will automate the testing for the Log4J vulnerability for HTTP and HTTPS connections. Pre-Requisits
Operational information regarding the vulnerability in the Log4j logging library.
Log4j Vulnerability (CVE-2021-44228) This repo contains operational information regarding the vulnerability in the Log4j logging library (CVE-2021-442
Python script to tamper with pages to test for Log4J Shell vulnerability.
log4jShell Scanner This shell script scans a vulnerable web application that is using a version of apache-log4j 2.15.0. This application is a static
Provides script to download and format public IP lists related to the Log4j exploit.
Provides script to download and format public IP lists related to the Log4j exploit. Current format includes: plain list, Cisco ASA Network Group.

Travis CI testing a Dockerfile based on Palantir's remix of Apache Cassandra, testing IaC, and testing integration health of Debian
Testing Palantir's remix of Apache Cassandra with Snyk & Travis CI This repository is to show Travis CI testing a Dockerfile based on Palantir's remix
Scans for Log4j versions effected by CVE-2021-44228
check_mkExtension to check for log4j2 CVE-2021-44228 This Plugin wraps around logpresso/CVE-2021-44228-Scanner (Apache License 2.0) How it works Run i
log4j-tools: CVE-2021-44228 poses a serious threat to a wide range of Java-based applications
log4j-tools Quick links Click to find: Inclusions of log4j2 in compiled code Calls to log4j2 in compiled code Calls to log4j2 in source code Overview
Log4j command generator: Generate commands for CVE-2021-44228
Log4j command generator Generate commands for CVE-2021-44228. Description The vulnerability exists due to the Log4j processor's handling of log messag
Log4j alternative for Python
Log4p Log4p is the most secure logging library ever created in this and all other universes. Usage: import log4p log4p.log('"Wow, this library is sec

Providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account.
We are providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account. The script enables security teams to identify external-facing AWS assets by running the exploit on them, and thus be able to map them and quickly patch them
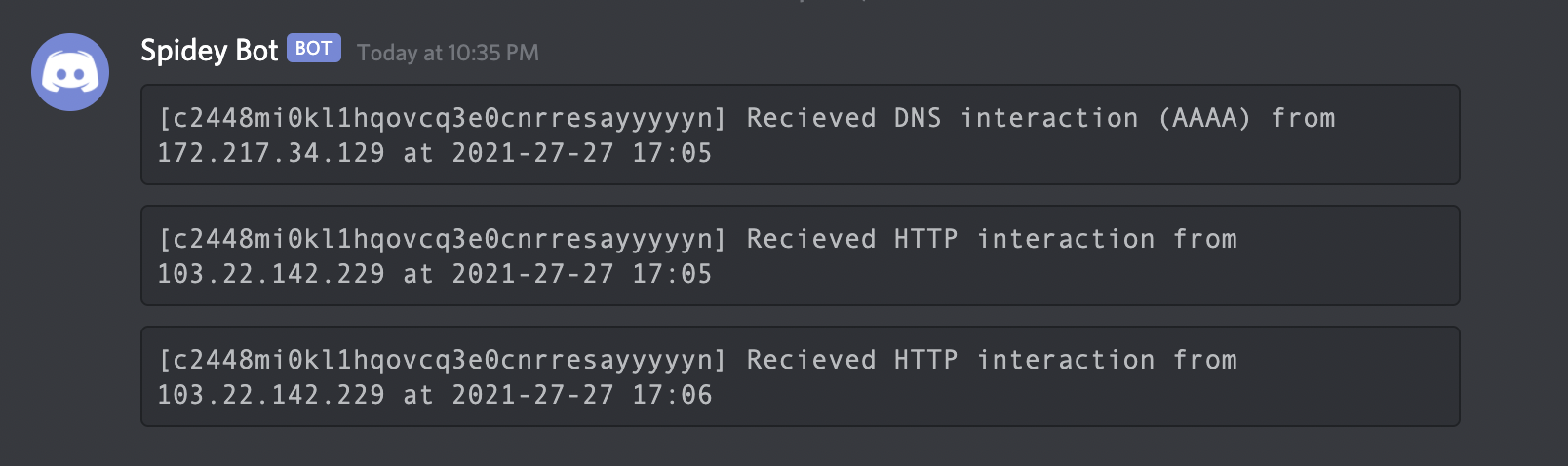
POC for detecting the Log4Shell (Log4J RCE) vulnerability
Interactsh An OOB interaction gathering server and client library Features • Usage • Interactsh Client • Interactsh Server • Interactsh Integration •
Log4j minecraft with python
Apache-Log4j Apache Log4j 远程代码执行 攻击者可直接构造恶意请求,触发远程代码执行漏洞。漏洞利用无需特殊配置,经阿里云安全团队验证,Apache Struts2、Apache Solr、Apache Druid、Apache Flink等均受影响 Steps 【Import
POC for detecting the Log4Shell (Log4J RCE) vulnerability.
log4shell-poc-py POC for detecting the Log4Shell (Log4J RCE) vulnerability. Run on a system with python3 python3 log4shell-poc.py pathToTargetFile
Log4j minecraft with python
log4jminecraft This code DOES NOT promote or encourage any illegal activities! The content in this document is provided solely for educational purpose

Log4j rce test environment and poc
log4jpwn log4j rce test environment See: https://www.lunasec.io/docs/blog/log4j-zero-day/ Experiments to trigger in various software products mentione
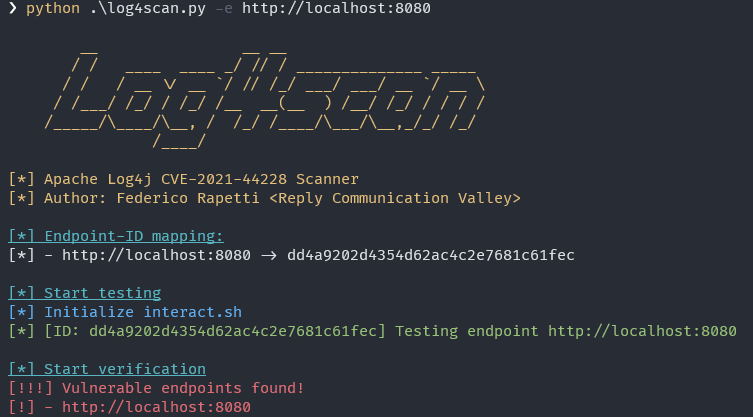
A simple automatic tool for finding vulnerable log4j hosts
Log4Scan A simple automatic tool for finding vulnerable log4j hosts Installation pip3 install -r requirements.txt Usage usage: log4scan.py [-h] (-f FI
Apache (Py)Spark type annotations (stub files).
PySpark Stubs A collection of the Apache Spark stub files. These files were generated by stubgen and manually edited to include accurate type hints. T
Log4j JNDI inj. vuln scanner
Log-4-JAM - Log 4 Just Another Mess Log4j JNDI inj. vuln scanner Requirements pip3 install requests_toolbelt Usage # make sure target list has http/ht
Tools for investigating Log4j CVE-2021-44228
Log4jTools Tools for investigating Log4j CVE-2021-44228 FetchPayload.py (Get java payload from ldap path provided in JNDI lookup). Example command: Re
Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228
log4j-honeypot-flask Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228 This can be
