61 Repositories
Python malware Libraries
Download archived malware from ActiveState's source code mirror
malware-archivist (ma) Tool to aid security researchers in dissecting malware. Often, repository maintainers will remove malicious packages entirely f

A machine learning malware analysis framework for Android apps.
🕵️ A machine learning malware analysis framework for Android apps. ☢️ DroidDetective is a Python tool for analysing Android applications (APKs) for p

PyExtractor is a decompiler that can fully decompile exe's compiled with pyinstaller or py2exe
PyExtractor is a decompiler that can fully decompile exe's compiled with pyinstaller or py2exe with additional features such as malware checker/detector! Also checks file(s) for suspicious words, discord webhooks, discord invites, pastebins, ips etc..
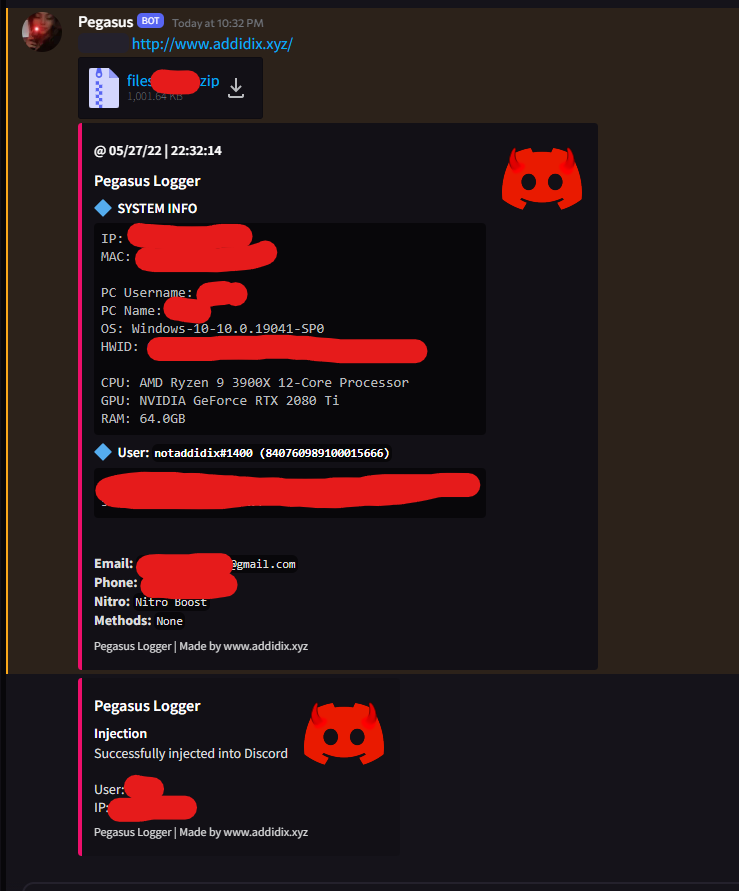
Pull sensitive data from users on windows including discord tokens and chrome data.
⭐ For a 🍪 Pegasus Pull sensitive data from users on windows including discord tokens and chrome data. Features 🟩 Discord tokens 🟩 Geolocation data
The Linux defender anti-virus software ported to work on CentOS Linux.
By: Seanpm2001, Et; Al. Top README.md Read this article in a different language Sorted by: A-Z Sorting options unavailable ( af Afrikaans Afrikaans |
Huskee: Malware made in Python for Educational purposes
𝐇𝐔𝐒𝐊𝐄𝐄 Caracteristicas: Discord Token Grabber Wifi Passwords Grabber Googl

PackMyPayload - Emerging Threat of Containerized Malware
This tool takes a file or directory on input and embeds them into an output file acting as an archive/container.

A Radare2 based Python module for Binary Analysis and Reverse Engineering.
Zepu1chr3 A Radare2 based Python module for Binary Analysis and Reverse Engineering. Installation You can simply run this command. pip3 install zepu1c
Malware-analysis-writeups - Some of my Malware Analysis writeups
About This repo contains some malware analysis writeups i've created over time m
Detection tool of malware(s) by checksum (useful for forensic)
🐍 malware_checker.py Detection tool of malware(s) by checksum (useful for forensic) 📦 Dependencies installation $ pip3 install -r requirements.txt

⛤Keylogger Generator for Windows written in Python⛤
⛤Keylogger Generator for Windows written in Python⛤
A malware to encrypt all the .txt and .jpg files in target computer using RSA algorithms
A malware to encrypt all the .txt and .jpg files in target computer using RSA algorithms. Change the Blackgound image of targets' computer. and decrypt the targets' encrypted files in our own computer

EchoDNS - Analyze your DNS traffic super easy, shows all requested DNS traffic
EchoDNS - Analyze your DNS traffic super easy, shows all requested DNS traffic
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries by disassembling and analyzing the compiled python byte-code(.pyc) files across all python versions (including Python 3.10.*)

A guide to building basic malware in Python by implementing a keylogger application
Keylogger-Malware-Project A guide to building basic malware in Python by implementing a keylogger application. If you want even more detail on the Pro
Repo for The Crown: Exploratory Analysis of Nim Malware DEF CON 615 talk
Repo for "The Crown: Exploratory Analysis of Nim Malware" DEF CON 615 talk
Malware arcane - Scripts and notes on my malware analysis journey
Malware Arcane Repository of notes and scripts I use when doing malware analysis
AmiEviL - This program uses the Virus Total API to determine if your suspicious file is malicious or not
AmiEviL - This program uses the Virus Total API to determine if your suspicious file is malicious or not. The program requests the hash of the file and outputs information (if any). This version will output: the file type, names seen in the wild, the number of security vendors that have flagged it as malicious, undetected, and unable to process the file.

Virus-Builder - This tool will generate a virus that can only destroy Windows computer
Virus-Builder - This tool will generate a virus that can only destroy Windows computer. You can also configure to auto run in usb drive
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging features for exploit developers & reverse engineers ☢
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging features for exploit developers & reverse engineers ☢
Android Malware (Analysis | Scoring) System
An Obfuscation-Neglect Android Malware Scoring System Quark-Engine is also bundled with Kali Linux, BlackArch. A trust-worthy, practical tool that's r
Malware-Related Sentence Classification
Malware-Related Sentence Classification This repo contains the code for the ICTAI 2021 paper "Enrichment of Features for Malware-Related Sentence Clas
Malware for Discord, designed to steal passwords, tokens, and inject discord folders for long-term use.
Vital What is Vital? Vital is malware primarily used to collect and extract information from the Discord desktop client. While it has other features (

Malware Env for OpenAI Gym
Malware Env for OpenAI Gym Citing If you use this code in a publication please cite the following paper: Hyrum S. Anderson, Anant Kharkar, Bobby Fila
9SPY: a Windows RAT built in Python using sockets
9SPY 👁🗨 9SPY is a Windows RAT built in Python using sockets Features Features will be listed here soon, there are currenly 14 Information This is a

A way to analyse how malware and/or goodware samples vary from each other using Shannon Entropy, Hausdorff Distance and Jaro-Winkler Distance
A way to analyse how malware and/or goodware samples vary from each other using Shannon Entropy, Hausdorff Distance and Jaro-Winkler Distance

Discord Token Stealer Malware Protection
TokenGuard TokenGuard, protect your account, prevent token steal. Totally free and open source Discord Server: https://discord.gg/EmwfaGuBE8 Source Co
Malware Bypass Research using Reinforcement Learning
Malware Bypass Research using Reinforcement Learning
Malware for Discord, designed to steal passwords, tokens, and inject discord folders for long-term use.
Vital What is Vital? Vital is malware primarily used to collect and extract information from the Discord desktop client. While it has other features (
The Malware Open-source Threat Intelligence Family dataset contains 3,095 disarmed PE malware samples from 454 families
MOTIF Dataset The Malware Open-source Threat Intelligence Family (MOTIF) dataset contains 3,095 disarmed PE malware samples from 454 families, labeled

TrollWare 🤡 is the most advanced Discord Malware & RAT
TrollWare 🤡 TrollWare is the most advanced Discord Malware, with a built-in RAT which can be controlled through a Discord Bot Pinned Note: Please giv

Lazarus analysis tools and research report
Lazarus Research This repository publishes analysis reports and analysis tools for Operation Dream Job and Operation JTrack for Lazarus. Tools Python
An easy-to-use library for emulating code in minidump files.
dumpulator Note: This is a work-in-progress prototype, please treat it as such. An easy-to-use library for emulating code in minidump files. Example T
Updated version of A discord token/password grabber thats grabs all of their tokens, passwords, credit card + alot more
Updated version of A discord token/password grabber thats grabs all of their tokens, passwords, credit card + alot more

HashDB is a community-sourced library of hashing algorithms used in malware.
HashDB HashDB is a community-sourced library of hashing algorithms used in malware. How To Use HashDB HashDB can be used as a stand alone hashing libr

An IDA pro python script to decrypt Qbot malware string
Qbot-Strings-Decrypter An IDA pro python script to decrypt Qbot malware strings.
Malware Analysis Neural Network project.
MalanaNeuralNetwork Description Malware Analysis Neural Network project. Table of Contents Getting Started Requirements Installation Clone Set-Up VENV

A Comprehensive Study on Learning-Based PE Malware Family Classification Methods
A Comprehensive Study on Learning-Based PE Malware Family Classification Methods Datasets Because of copyright issues, both the MalwareBazaar dataset

MsfMania is a command line tool developed in Python that is designed to bypass antivirus software on Windows and Linux/Mac in the future
MsfMania MsfMania is a command line tool developed in Python that is designed to bypass antivirus software on Windows and Linux/Mac in the future. Sum
This repository is one of a few malware collections on the GitHub.
This repository is one of a few malware collections on the GitHub.

A simple malware that tries to explain the logic of computer viruses with Python.
Simple-Virus-With-Python A simple malware that tries to explain the logic of computer viruses with Python. What Is The Virus ? Computer viruses are ma

ThePhish: an automated phishing email analysis tool
ThePhish ThePhish is an automated phishing email analysis tool based on TheHive, Cortex and MISP. It is a web application written in Python 3 and base
Generate YARA rules for OOXML documents using ZIP local header metadata.
apooxml Generate YARA rules for OOXML documents using ZIP local header metadata. To learn more about this tool and the methodology behind it, check ou
A curated list of amazingly awesome Cybersecurity datasets
A curated list of amazingly awesome Cybersecurity datasets

🐸 Identify anything. pyWhat easily lets you identify emails, IP addresses, and more. Feed it a .pcap file or some text and it'll tell you what it is! 🧙♀️
🐸 Identify anything. pyWhat easily lets you identify emails, IP addresses, and more. Feed it a .pcap file or some text and it'll tell you what it is! 🧙♀️
HatSploit native powerful payload generation and shellcode injection tool that provides support for common platforms and architectures.
HatVenom HatSploit native powerful payload generation and shellcode injection tool that provides support for common platforms and architectures. Featu
A token logger for discord + steals Brave/Chrome passwords and usernames
Backdoor Machine - ❗ For educational purposes only ❗ A program made in python for stealing passwords and usernames from Google Chrome/Brave and tokenl

A Feature Rich Modular Malware Configuration Extraction Utility for MalDuck
Malware Configuration Extractor A Malware Configuration Extraction Tool and Modules for MalDuck This project is FREE as in FREE 🍺 , use it commercial

SARA - Simple Android Ransomware Attack
SARA - Simple Android Ransomware Attack Disclaimer The author is not responsible for any issues or damage caused by this program. Features User can cu
Android Malware Behavior Deleter
Android Malware Behavior Deleter UDcide UDcide is a tool that provides alternative way to deal with Android malware. We help you to detect and remove
A Modular MWDB Utility to Collect Fresh Malware Samples
MWDB Feeds A Modular MWDB Utility to Collect Fresh Malware Samples This project is FREE as in FREE 🍺 , use it commercially, privately or however you
Telegram RAT written in Python
teleRAT Python based RAT that uses Telegram for sending commands and receiving data to and from a victim computer. Setup.py Insert your API key into t

Consolidating and extending hosts files from several well-curated sources. You can optionally pick extensions to block pornography, social media, and other categories.
Take Note! With the exception of issues and PRs regarding changes to hosts/data/StevenBlack/hosts, all other issues regarding the content of the produ
Malware Configuration And Payload Extraction
CAPE: Malware Configuration And Payload Extraction CAPE is a malware sandbox. It is derived from Cuckoo and is designed to automate the process of mal
Malware Configuration And Payload Extraction
CAPEv2 (Python3) has now been released CAPEv2 With the imminent end-of-life for Python 2 (January 1 2020), CAPEv1 will be phased out. Please upgrade t

Sentello is python script that simulates the anti-evasion and anti-analysis techniques used by malware.
sentello Sentello is a python script that simulates the anti-evasion and anti-analysis techniques used by malware. For techniques that are difficult t

🍯 16 honeypots in a single pypi package (DNS, HTTP Proxy, HTTP, HTTPS, SSH, POP3, IMAP, STMP, VNC, SMB, SOCKS5, Redis, TELNET, Postgres & MySQL)
Easy to setup customizable honeypots for monitoring network traffic, bots activities and username\password credentials. The current available honeypot
Bitcoin Clipper malware made in Python.
a BTC Clipper or a "Bitcoin Clipper" is a type of malware designed to target cryptocurrency transactions.

RAT-el is an open source penetration test tool that allows you to take control of a windows machine.
To prevent RATel from being detected by antivirus, please do not upload the payload to TOTAL VIRUS. Each month I will test myself if the payload gets detected by antivirus. So you’ll have a photo every month to prove RAtel’s discretion.

A small utility to deal with malware embedded hashes.
Uchihash is a small utility that can save malware analysts the time of dealing with embedded hash values used for various things such as: Dyn
Various capabilities for static malware analysis.
Malchive The malchive serves as a compendium for a variety of capabilities mainly pertaining to malware analysis, such as scripts supporting day to da