1491 Repositories
Python network-scanner Libraries
Repository for GNSS-based position estimation using a Deep Neural Network
Code repository accompanying our work on 'Improving GNSS Positioning using Neural Network-based Corrections'. In this paper, we present a Deep Neural
A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts
log4j-scan A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts Features Support for lists of URLs. Fuzzing for more
Neural network for digit classification powered by cuda
cuda_nn_mnist Neural network library for digit classification powered by cuda Resources The library was built to work with MNIST dataset. python-mnist

Execution After Redirect (EAR) / Long Response Redirection Vulnerability Scanner written in python3
Execution After Redirect (EAR) / Long Response Redirection Vulnerability Scanner written in python3, It Fuzzes All URLs of target website & then scan them for EAR

SE-MSCNN: A Lightweight Multi-scaled Fusion Network for Sleep Apnea Detection Using Single-Lead ECG Signals
SE-MSCNN: A Lightweight Multi-scaled Fusion Network for Sleep Apnea Detection Using Single-Lead ECG Signals Abstract Sleep apnea (SA) is a common slee
Base on browser-time to get har from network, and use python to analyze the data .
base on browser-time to get har from network, and use python to analyze the data
CasualHealthcare's Pneumonia detection with Artificial Intelligence (Convolutional Neural Network)
CasualHealthcare's Pneumonia detection with Artificial Intelligence (Convolutional Neural Network) This is PneumoniaDiagnose, an artificially intellig

Semantic Segmentation in Pytorch. Network include: FCN、FCN_ResNet、SegNet、UNet、BiSeNet、BiSeNetV2、PSPNet、DeepLabv3_plus、 HRNet、DDRNet
🚀 If it helps you, click a star! ⭐ Update log 2020.12.10 Project structure adjustment, the previous code has been deleted, the adjustment will be re-
An AI for Music Generation
An AI for Music Generation

Supporting code for "Autoregressive neural-network wavefunctions for ab initio quantum chemistry".
naqs-for-quantum-chemistry This repository contains the codebase developed for the paper Autoregressive neural-network wavefunctions for ab initio qua
![AMC- Automatic Media Access Control [MAC] Address Spoofing Tool](https://github.com/hexdee606/AMC2.0/raw/main/User/Banner.png)
AMC- Automatic Media Access Control [MAC] Address Spoofing Tool
AMC (Automatic Media Access Control [MAC] Address Spoofing tool), helps you to protect your real network hardware identity. Each entered time interval your hardware address was changed automatically. without interrupting your internet connection.
Human Activity Recognition example using TensorFlow on smartphone sensors dataset and an LSTM RNN. Classifying the type of movement amongst six activity categories - Guillaume Chevalier
LSTMs for Human Activity Recognition Human Activity Recognition (HAR) using smartphones dataset and an LSTM RNN. Classifying the type of movement amon

Simple and ready-to-use tutorials for TensorFlow
TensorFlow World To support maintaining and upgrading this project, please kindly consider Sponsoring the project developer. Any level of support is a
TensorFlow tutorials and best practices.
Effective TensorFlow 2 Table of Contents Part I: TensorFlow 2 Fundamentals TensorFlow 2 Basics Broadcasting the good and the ugly Take advantage of th

TensorFlow (Python API) implementation of Neural Style
neural-style-tf This is a TensorFlow implementation of several techniques described in the papers: Image Style Transfer Using Convolutional Neural Net

Photo-Realistic Single Image Super-Resolution Using a Generative Adversarial Network
Super Resolution Examples We run this script under TensorFlow 2.0 and the TensorLayer2.0+. For TensorLayer 1.4 version, please check release. 🚀 🚀 🚀

Dynamics-aware Adversarial Attack of 3D Sparse Convolution Network
Leaded Gradient Method (LGM) This repository contains the PyTorch implementation for paper Dynamics-aware Adversarial Attack of 3D Sparse Convolution

A deep learning network built with TensorFlow and Keras to classify gender and estimate age.
Convolutional Neural Network (CNN). This repository contains a source code of a deep learning network built with TensorFlow and Keras to classify gend
The Delegate Network: An Interactive Voice Response Delegative Democracy Implementation of Liquid Democracy
The Delegate Network Overview The delegate network is a completely transparent, easy-to-use and understand version of what is sometimes called liquid

A PyTorch based deep learning library for drug pair scoring.
Documentation | External Resources | Datasets | Examples ChemicalX is a deep learning library for drug-drug interaction, polypharmacy side effect and
An experimentation and research platform to investigate the interaction of automated agents in an abstract simulated network environments.
CyberBattleSim April 8th, 2021: See the announcement on the Microsoft Security Blog. CyberBattleSim is an experimentation research platform to investi
![[CVPR 2020] Local Class-Specific and Global Image-Level Generative Adversarial Networks for Semantic-Guided Scene Generation](https://github.com/Ha0Tang/LGGAN/raw/master/imgs/framework.jpg)
[CVPR 2020] Local Class-Specific and Global Image-Level Generative Adversarial Networks for Semantic-Guided Scene Generation
Contents Local and Global GAN Cross-View Image Translation Semantic Image Synthesis Acknowledgments Related Projects Citation Contributions Collaborat
![[CVPR 2019 Oral] Multi-Channel Attention Selection GAN with Cascaded Semantic Guidance for Cross-View Image Translation](https://github.com/Ha0Tang/SelectionGAN/raw/master/imgs/motivation.jpg)
[CVPR 2019 Oral] Multi-Channel Attention Selection GAN with Cascaded Semantic Guidance for Cross-View Image Translation
SelectionGAN for Guided Image-to-Image Translation CVPR Paper | Extended Paper | Guided-I2I-Translation-Papers Citation If you use this code for your
The authors' implementation of Unsupervised Adversarial Learning of 3D Human Pose from 2D Joint Locations
Unsupervised Adversarial Learning of 3D Human Pose from 2D Joint Locations This is the authors' implementation of Unsupervised Adversarial Learning of
3D HourGlass Networks for Human Pose Estimation Through Videos
3D-HourGlass-Network 3D CNN Based Hourglass Network for Human Pose Estimation (3D Human Pose) from videos. This was my summer'18 research project. Dis
Training PyTorch models with differential privacy
Opacus is a library that enables training PyTorch models with differential privacy. It supports training with minimal code changes required on the cli
A Python Scanner for log4j
log4j-Scanner scanner for log4j cat web-urls.txt | python3 log4j.py ID.burpcollaborator.net web-urls.txt http://127.0.0.1:8080 https://www.google.c

A deep learning network built with TensorFlow and Keras to classify gender and estimate age.
Convolutional Neural Network (CNN). This repository contains a source code of a deep learning network built with TensorFlow and Keras to classify gend

DaProfiler allows you to get emails, social medias, adresses, works and more on your target using web scraping and google dorking techniques
DaProfiler allows you to get emails, social medias, adresses, works and more on your target using web scraping and google dorking techniques, based in France Only. The particularity of this program is its ability to find your target's e-mail adresses.
I hacked my own webcam from a Kali Linux VM in my local network, using Ettercap to do the MiTM ARP poisoning attack, sniffing with Wireshark, and using metasploit
plan I - Linux Fundamentals Les utilisateurs et les droits Installer des programmes avec apt-get Surveiller l'activité du système Exécuter des program

PyTorch implementation of Deep HDR Imaging via A Non-Local Network (TIP 2020).
NHDRRNet-PyTorch This is the PyTorch implementation of Deep HDR Imaging via A Non-Local Network (TIP 2020). 0. Differences between Original Paper and
Something I built to test for Log4J vulnerabilities on customer networks.
Log4J-Scanner Something I built to test for Log4J vulnerabilities on customer networks. I'm not responsible if your computer blows up, catches fire or
Codes for building and training the neural network model described in Domain-informed neural networks for interaction localization within astroparticle experiments.
Domain-informed Neural Networks Codes for building and training the neural network model described in Domain-informed neural networks for interaction
An automated header extensive scanner for detecting log4j RCE CVE-2021-44228
log4j An automated header extensive scanner for detecting log4j RCE CVE-2021-44228 Usage $ python3 log4j.py -l urls.txt --dns-log REPLACE_THIS.dnslog.

Ensembling Off-the-shelf Models for GAN Training
Vision-aided GAN video (3m) | website | paper Can the collective knowledge from a large bank of pretrained vision models be leveraged to improve GAN t
This is the official PyTorch implementation of the CVPR 2020 paper "TransMoMo: Invariance-Driven Unsupervised Video Motion Retargeting".
TransMoMo: Invariance-Driven Unsupervised Video Motion Retargeting Project Page | YouTube | Paper This is the official PyTorch implementation of the C
A scanner and a proof of sample exploit for log4j RCE CVE-2021-44228
1.Create a Sample Vulnerable Application . 2.Start a netcat listner . 3.Run the exploit . 5.Use jdk1.8.0_20 for better results . Exploit-db - https://
A small game I made back in think 2011
Navi Network A small game I made back in think 2011. An online game inspired by the self-hosted nature of Minecraft, made with pygame, based on the Me
This Home Assistant custom component adds support for controlling Midea dehumidiferes on local network.
This is a custom component for Home assistant that adds support for Midea dehumidifier appliances via the local area network. midea-dehumidifier-lan H

Ensembling Off-the-shelf Models for GAN Training
Data-Efficient GANs with DiffAugment project | paper | datasets | video | slides Generated using only 100 images of Obama, grumpy cats, pandas, the Br

Automate the case review on legal case documents and find the most critical cases using network analysis
Automation on Legal Court Cases Review This project is to automate the case review on legal case documents and find the most critical cases using netw

A Persistent Embedded Graph Database for Python
Cog - Embedded Graph Database for Python cogdb.io New release: 2.0.5! Installing Cog pip install cogdb Cog is a persistent embedded graph database im
labsecurity is a framework and its use is for ethical hacking and computer security
labsecurity labsecurity is a framework and its use is for ethical hacking and computer security. Warning This tool is only for educational purpose. If

An automated, reliable scanner for the Log4Shell (CVE-2021-44228) vulnerability.
Log4JHunt An automated, reliable scanner for the Log4Shell CVE-2021-44228 vulnerability. Video demo: Usage Here the help usage: $ python3 log4jhunt.py
Using pytorch to implement unet network for liver image segmentation.
Using pytorch to implement unet network for liver image segmentation.
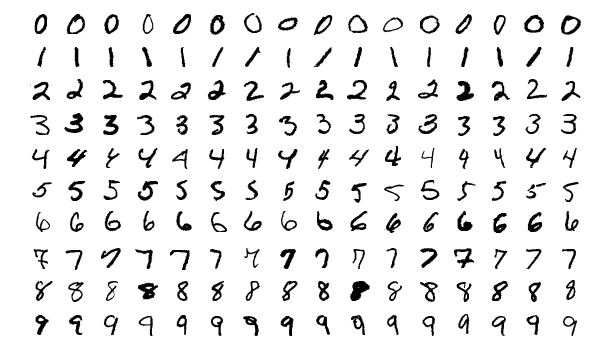
A simple Neural Network that predicts the label for a series of handwritten digits
Neural_Network A simple Neural Network that predicts the label for a series of handwritten numbers This program tries to predict the label (1,2,3 etc.
Unofficial implementation of Google's FNet: Mixing Tokens with Fourier Transforms
FNet: Mixing Tokens with Fourier Transforms Pytorch implementation of Fnet : Mixing Tokens with Fourier Transforms. Citation: @misc{leethorp2021fnet,

Physics-Informed Neural Networks (PINN) and Deep BSDE Solvers of Differential Equations for Scientific Machine Learning (SciML) accelerated simulation
NeuralPDE NeuralPDE.jl is a solver package which consists of neural network solvers for partial differential equations using scientific machine learni
PyContinual (An Easy and Extendible Framework for Continual Learning)
PyContinual (An Easy and Extendible Framework for Continual Learning) Easy to Use You can sumply change the baseline, backbone and task, and then read
Scans for Log4j versions effected by CVE-2021-44228
check_mkExtension to check for log4j2 CVE-2021-44228 This Plugin wraps around logpresso/CVE-2021-44228-Scanner (Apache License 2.0) How it works Run i
An implementation of quantum convolutional neural network with MindQuantum. Huawei, classifying MNIST dataset
关于实现的一点说明 山东大学 2020级 苏博南 www.subonan.com 文件说明 tools.py 这里面主要有两个函数: resize(a, lenb) 这其实是我找同学写的一个小算法hhh。给出一个$28\times 28$的方阵a,返回一个$lenb\times lenb$的方阵。因

Providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account.
We are providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account. The script enables security teams to identify external-facing AWS assets by running the exploit on them, and thus be able to map them and quickly patch them
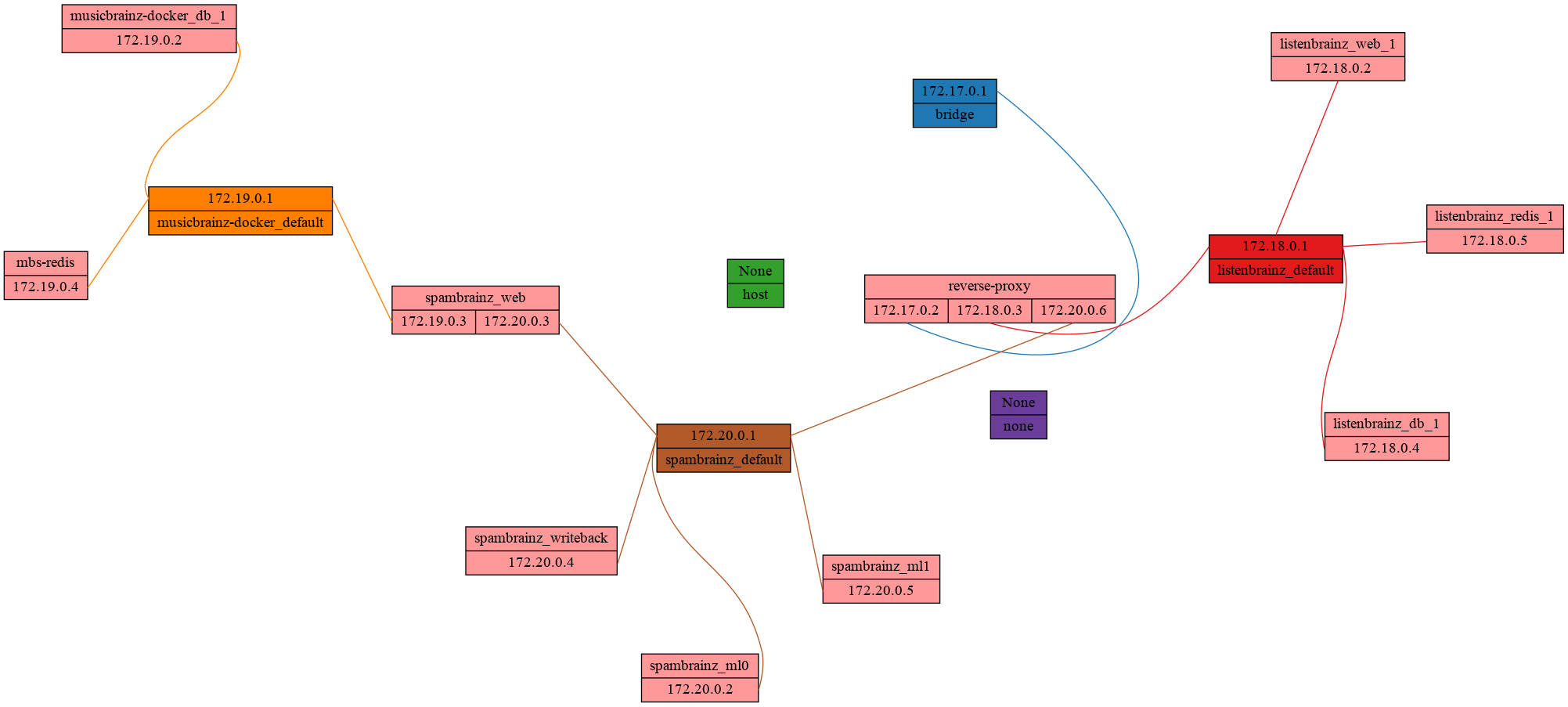
Quickly visualize docker networks with graphviz.
Docker Network Graph Visualize the relationship between Docker networks and containers as a neat graphviz graph. Example Usage usage: docker-net-graph

A foreign language learning aid using a neural network to predict probability of translating foreign words
Langy Langy is a reading-focused foreign language learning aid orientated towards young children. Reading is an activity that every child knows. It is
TRACER: Extreme Attention Guided Salient Object Tracing Network implementation in PyTorch
TRACER: Extreme Attention Guided Salient Object Tracing Network This paper was accepted at AAAI 2022 SA poster session. Datasets All datasets are avai
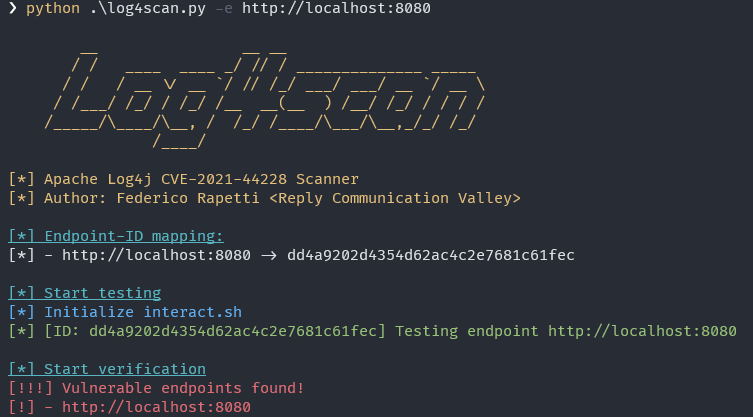
A simple automatic tool for finding vulnerable log4j hosts
Log4Scan A simple automatic tool for finding vulnerable log4j hosts Installation pip3 install -r requirements.txt Usage usage: log4scan.py [-h] (-f FI
Log4j JNDI inj. vuln scanner
Log-4-JAM - Log 4 Just Another Mess Log4j JNDI inj. vuln scanner Requirements pip3 install requests_toolbelt Usage # make sure target list has http/ht
Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228
log4j-honeypot-flask Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228 This can be
Python3 script for scanning CVE-2021-44228 (Log4shell) vulnerable machines.
Log4j_checker.py (CVE-2021-44228) Description This Python3 script tries to look for servers vulnerable to CVE-2021-44228, also known as Log4Shell, a v

Learning Lightweight Low-Light Enhancement Network using Pseudo Well-Exposed Images
Learning Lightweight Low-Light Enhancement Network using Pseudo Well-Exposed Images This repository contains the implementation of the following paper

The source code of the paper "SHGNN: Structure-Aware Heterogeneous Graph Neural Network"
SHGNN: Structure-Aware Heterogeneous Graph Neural Network The source code and dataset of the paper: SHGNN: Structure-Aware Heterogeneous Graph Neural

Log4j-Scanner with Bind-Receipt and custom hostnames
Hrafna - Log4j-Scanner for the masses Features Scanning-system designed to check your own infra for vulnerable log4j-installations start and stop scan
Some code of the implements of Geological Modeling Using 3D Pixel-Adaptive and Deformable Convolutional Neural Network
3D-GMPDCNN Geological Modeling Using 3D Pixel-Adaptive and Deformable Convolutional Neural Network PyTorch implementation of "Geological Modeling Usin
On-demand scanning for container registries
Lacework registry scanner Install & configure Lacework CLI Integrate a Container Registry Go to Lacework Resources Containers Container Image In
Twin-deep neural network for semi-supervised learning of materials properties
Deep Semi-Supervised Teacher-Student Material Synthesizability Prediction Citation: Semi-supervised teacher-student deep neural network for materials

Centroid-UNet is deep neural network model to detect centroids from satellite images.
Centroid UNet - Locating Object Centroids in Aerial/Serial Images Introduction Centroid-UNet is deep neural network model to detect centroids from Aer
Event-driven networking engine written in Python.
Twisted For information on changes in this release, see the NEWS file. What is this? Twisted is an event-based framework for internet applications, su
Impacket is a collection of Python classes for working with network protocols.
What is Impacket? Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmat
A network address manipulation library for Python
netaddr A system-independent network address manipulation library for Python 2.7 and 3.5+. (Python 2.7 and 3.5 support is deprecated). Provides suppor
InDuDoNet+: A Model-Driven Interpretable Dual Domain Network for Metal Artifact Reduction in CT Images
InDuDoNet+: A Model-Driven Interpretable Dual Domain Network for Metal Artifact Reduction in CT Images Hong Wang, Yuexiang Li, Haimiao Zhang, Deyu Men
Network Compression via Central Filter
Network Compression via Central Filter Environments The code has been tested in the following environments: Python 3.8 PyTorch 1.8.1 cuda 10.2 torchsu
A Burp Pro extension that adds log4shell checks to Burp Scanner
scan4log4shell A Burp Pro extension that adds log4shell checks to Burp Scanner, written by Daniel Crowley of IBM X-Force Red. Installation To install
A fully automated, accurate, and extensive scanner for finding log4j RCE CVE-2021-44228
log4j-scan A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts Features Support for lists of URLs. Fuzzing for more

A PyTorch library and evaluation platform for end-to-end compression research
CompressAI CompressAI (compress-ay) is a PyTorch library and evaluation platform for end-to-end compression research. CompressAI currently provides: c
Multi-vendor library to simplify CLI connections to network devices
Netmiko Multi-vendor library to simplify CLI connections to network devices Why Netmiko? Network automation to screen-scraping devices is primarily co
Synthetic Data Generation for tabular, relational and time series data.
An Open Source Project from the Data to AI Lab, at MIT Website: https://sdv.dev Documentation: https://sdv.dev/SDV User Guides Developer Guides Github
GTK and Python based, system performance and usage monitoring tool
System Monitoring Center GTK3 and Python 3 based, system performance and usage monitoring tool. Features: Detailed system performance and usage usage

Code for ShadeGAN (NeurIPS2021) A Shading-Guided Generative Implicit Model for Shape-Accurate 3D-Aware Image Synthesis
A Shading-Guided Generative Implicit Model for Shape-Accurate 3D-Aware Image Synthesis Project Page | Paper A Shading-Guided Generative Implicit Model

Implementation of Heterogeneous Graph Attention Network
HetGAN Implementation of Heterogeneous Graph Attention Network This is the code repository of paper "Prediction of Metro Ridership During the COVID-19
A Dynamic Residual Self-Attention Network for Lightweight Single Image Super-Resolution
DRSAN A Dynamic Residual Self-Attention Network for Lightweight Single Image Super-Resolution Karam Park, Jae Woong Soh, and Nam Ik Cho Environments U
The source code for Adaptive Kernel Graph Neural Network at AAAI2022
AKGNN The source code for Adaptive Kernel Graph Neural Network at AAAI2022. Please cite our paper if you think our work is helpful to you: @inproceedi

Official implementation of "A Shared Representation for Photorealistic Driving Simulators" in PyTorch.
A Shared Representation for Photorealistic Driving Simulators The official code for the paper: "A Shared Representation for Photorealistic Driving Sim

log4j burp scanner
log4jscanner log4j burp插件 特点如下: 0x01 基于Cookie字段、XFF头字段、UA头字段发送payload 0x02 基于域名的唯一性,将host带入dnslog中 插件主要识别五种形式: 1.get请求,a=1&b=2&c=3 2.post请求,a=1&b=2&c=
A web service for scanning media hosted by a Matrix media repository
Matrix Content Scanner A web service for scanning media hosted by a Matrix media repository Installation TODO Development In a virtual environment wit
A modular application for performing anomaly detection in networks
Deep-Learning-Models-for-Network-Annomaly-Detection The modular app consists for mainly three annomaly detection algorithms. The system supports model

Pytorch code for paper "Image Compressed Sensing Using Non-local Neural Network" TMM 2021.
NL-CSNet-Pytorch Pytorch code for paper "Image Compressed Sensing Using Non-local Neural Network" TMM 2021. Note: this repo only shows the strategy of
Bayesian Deep Learning and Deep Reinforcement Learning for Object Shape Error Response and Correction of Manufacturing Systems
Bayesian Deep Learning for Manufacturing 2.0 (dlmfg) Object Shape Error Response (OSER) Digital Lifecycle Management - In Process Quality Improvement
Unofficial implementation of "Coordinate Attention for Efficient Mobile Network Design"
Unofficial implementation of "Coordinate Attention for Efficient Mobile Network Design". CoordAttention tensorflow slim
Send files to your friends over network! (100mb max)
PyServed v2.0.1 Made by Shaurya Pratap Singh Installation Using pip(for stable releases.) - $ pip install pyserved Using Git (for latest updates) -
Federated learning on graph, especially on graph neural networks (GNNs), knowledge graph, and private GNN.
Federated learning on graph, especially on graph neural networks (GNNs), knowledge graph, and private GNN.
Generative Handwriting using LSTM Mixture Density Network with TensorFlow
Generative Handwriting Demo using TensorFlow An attempt to implement the random handwriting generation portion of Alex Graves' paper. See my blog post

The Simplest DCGAN Implementation
DCGAN in TensorLayer This is the TensorLayer implementation of Deep Convolutional Generative Adversarial Networks. Looking for Text to Image Synthesis

Unsupervised Image to Image Translation with Generative Adversarial Networks
Unsupervised Image to Image Translation with Generative Adversarial Networks Paper: Unsupervised Image to Image Translation with Generative Adversaria
The implementation code for "DAGAN: Deep De-Aliasing Generative Adversarial Networks for Fast Compressed Sensing MRI Reconstruction"
DAGAN This is the official implementation code for DAGAN: Deep De-Aliasing Generative Adversarial Networks for Fast Compressed Sensing MRI Reconstruct

Neural Network to colorize grayscale images
#colornet Neural Network to colorize grayscale images Results Grayscale Prediction Ground Truth Eiji K used colornet for anime colorization Sources Au
Convolutional Neural Network for Text Classification in Tensorflow
This code belongs to the "Implementing a CNN for Text Classification in Tensorflow" blog post. It is slightly simplified implementation of Kim's Convo
End-To-End Memory Network using Tensorflow
MemN2N Implementation of End-To-End Memory Networks with sklearn-like interface using Tensorflow. Tasks are from the bAbl dataset. Get Started git clo

Spatial Transformer Nets in TensorFlow/ TensorLayer
MOVED TO HERE Spatial Transformer Networks Spatial Transformer Networks (STN) is a dynamic mechanism that produces transformations of input images (or
Lip Reading - Cross Audio-Visual Recognition using 3D Convolutional Neural Networks
Lip Reading - Cross Audio-Visual Recognition using 3D Convolutional Neural Networks - Official Project Page This repository contains the code develope
