11 Repositories
Python signatures Libraries
Experimental musig2 python code, not for production use!
musig2-py Experimental musig2 python code, not for production use! This is just for testing things out. All public keys are encoded as 32 bytes, assum
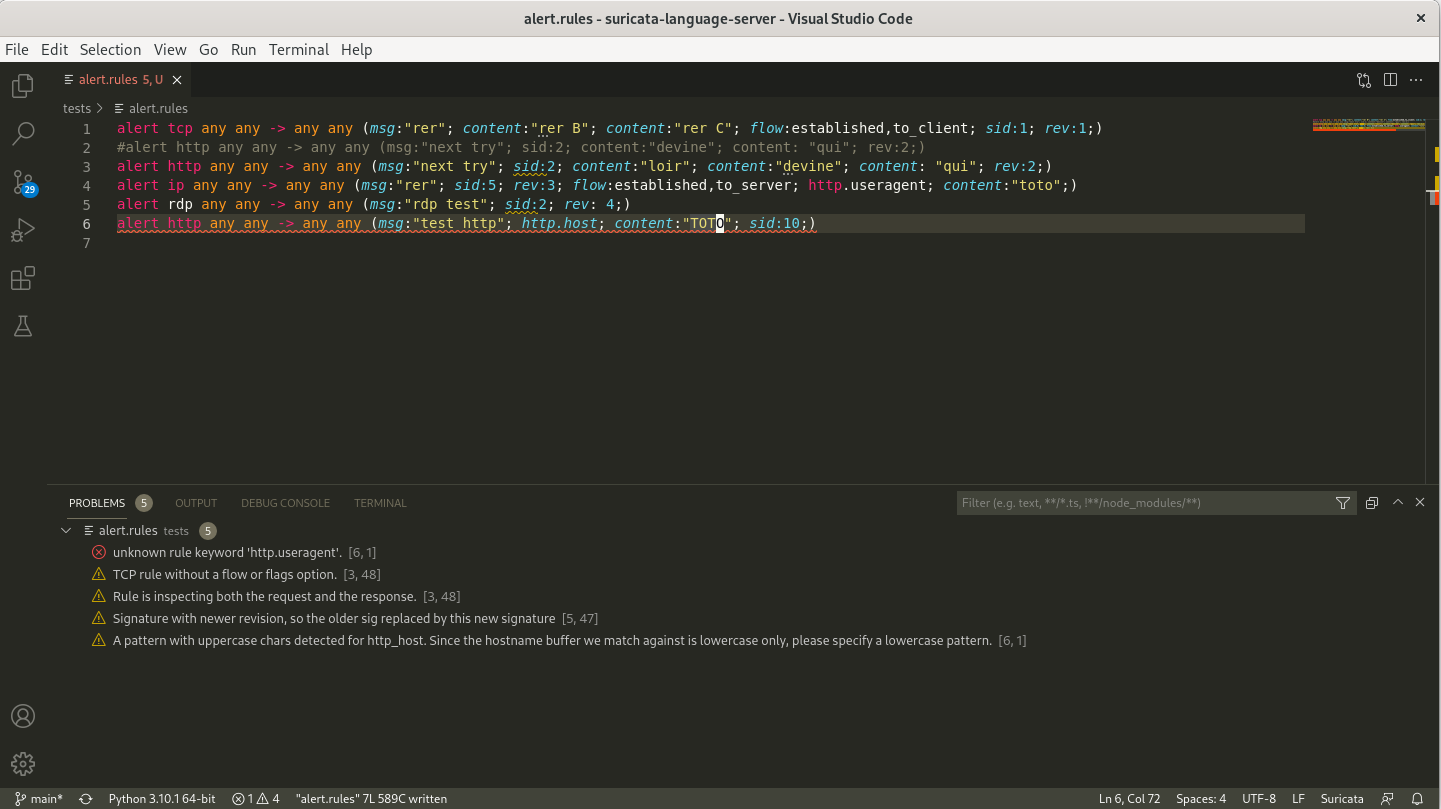
Suricata Language Server is an implementation of the Language Server Protocol for Suricata signatures
Suricata Language Server is an implementation of the Language Server Protocol for Suricata signatures. It adds syntax check, hints and auto-completion to your preferred editor once it is configured.
python implementation of JSON Web Signatures
python-jws 🚨 This is Unmaintained 🚨 This library is unmaintained and you should probably use For histo
Program to extract signatures from documents.
Extracting Signatures from Bank Checks Introduction Ahmed et al. [1] suggest a connected components-based method for segmenting signatures in document
This enforces signatures for CVE-2021-44228 across all policies on a BIG-IP ASM device
f5-waf-enforce-sigs-CVE-2021-44228 This enforces signatures for CVE-2021-44228 across all policies on a BIG-IP ASM device Overview This script enforce
A function decorator for enforcing function signatures
A function decorator for enforcing function signatures
A tool for removing PUPs using signatures
Unwanted program removal tool A tool for removing PUPs using signatures What is the unwanted program removal tool? The unwanted program removal tool i

A simple python program to sign text using either the RSA or ISRSAC algorithm with GUI built using tkinter library.
Digital Signatures using ISRSAC Algorithm A simple python program to sign text using either the RSA or ISRSAC algorithm with GUI built using tkinter l
Signature remover is a NLP based solution which removes email signatures from the rest of the text.
Signature Remover Signature remover is a NLP based solution which removes email signatures from the rest of the text. It helps to enchance data conten
Signatures and IoCs from public Volexity blog posts.
threat-intel This repository contains IoCs related to Volexity public threat intelligence blog posts. They are organised by year, and within each year

Detection of drones using their thermal signatures from thermal camera through YOLO-V3 based CNN with modifications to encapsulate drone motion
Drone Detection using Thermal Signature This repository highlights the work for night-time drone detection using a using an Optris PI Lightweight ther