41 Repositories
Python threat-broadcast Libraries
Implementation of RITA (Real Intelligence Threat Analytics) in Jupyter Notebook with improved scoring algorithm.
RITA (Real Intelligence Threat Analytics) in Jupyter Notebook RITA is an open source framework for network traffic analysis sponsored by Active Counte
Threat research and reporting from IronNet's Threat Research Teams
IronNet Threat Research 🕵️ Overview This repository contains IronNet's Threat Research. Research & Reporting 📝 Project Description Cobalt Strike Res
BlackIP-Rep is a tool designed to gather the reputation and information of Bulk IP's.
BlackIP-Rep is a tool designed to gather the reputation and information of Bulk IP's. Focused on increasing the workflow of Security Operations(SOC) team during investigation.

PackMyPayload - Emerging Threat of Containerized Malware
This tool takes a file or directory on input and embeds them into an output file acting as an archive/container.
Burgeramt-appointments-websockets - Fetch Bürgeramt appointments and broadcast them via websockets
Bürgeramt appointment finder This server looks for Bürgeramt appointment every f

Epagneul is a tool to visualize and investigate windows event logs
epagneul Epagneul is a tool to visualize and investigate windows event logs. Dep
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries by disassembling and analyzing the compiled python byte-code(.pyc) files across all python versions (including Python 3.10.*)

Threat Intel Platform for T-POTs
T-Pot 20.06 runs on Debian (Stable), is based heavily on docker, docker-compose
Threat Intel Platform for T-POTs
GreedyBear The project goal is to extract data of the attacks detected by a TPOT or a cluster of them and to generate some feeds that can be used to p
Websocket 'broadcast' demo using FastAPI/Starlette
fastapi-websocket-broadcast An example of the familiar 'chat' websocket demo app, implemented in FastAPI / Starlette. Run with uvicorn app:app And th

Gym Threat Defense
Gym Threat Defense The Threat Defense environment is an OpenAI Gym implementation of the environment defined as the toy example in Optimal Defense Pol

DaProfiler allows you to get emails, social medias, adresses, works and more on your target using web scraping and google dorking techniques
DaProfiler allows you to get emails, social medias, adresses, works and more on your target using web scraping and google dorking techniques, based in France Only. The particularity of this program is its ability to find your target's e-mail adresses.
log4j-tools: CVE-2021-44228 poses a serious threat to a wide range of Java-based applications
log4j-tools Quick links Click to find: Inclusions of log4j2 in compiled code Calls to log4j2 in compiled code Calls to log4j2 in source code Overview
Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228
log4j-honeypot-flask Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228 This can be
A small Django app to easily broadcast an announcement across a website.
django-site-broadcasts The site broadcast application allows users to define short messages and announcements that should be displayed across a site.

Open-CyKG: An Open Cyber Threat Intelligence Knowledge Graph
Open-CyKG: An Open Cyber Threat Intelligence Knowledge Graph Model Description Open-CyKG is a framework that is constructed using an attenti
The Malware Open-source Threat Intelligence Family dataset contains 3,095 disarmed PE malware samples from 454 families
MOTIF Dataset The Malware Open-source Threat Intelligence Family (MOTIF) dataset contains 3,095 disarmed PE malware samples from 454 families, labeled

This Tool can help enginners and biggener in network, the tool help you to find of any ip with subnet mask that can calucate them and show you ( Availble IP's , Subnet Mask, Network-ID, Broadcast-ID )
This Tool can help enginners and biggener in network, the tool help you to find of any ip with subnet mask that can calucate them and show you ( Availble IP's , Subnet Mask, Network-ID, Broadcast-ID )
Una herramienta para transmitir mensajes automáticamente a múltiples grupos de chat
chat-broadcast Una herramienta para transmitir mensajes automáticamente a múltiples grupos de chat Setup Librerías Necesitas Python 3 con la librería
Agile Threat Modeling Toolkit
Threagile is an open-source toolkit for agile threat modeling:

A Pythonic framework for threat modeling
pytm: A Pythonic framework for threat modeling Introduction Traditional threat modeling too often comes late to the party, or sometimes not at all. In
Listen to the radio station from your favorite broadcast
Latest news Listen to the radio station from your favorite broadcast MyCroft Radio Skill for testing and copy at docker skill About Play regional radi
It's an extra broadcast driver for masonite. It adds support for socketio.
It's an extra broadcast driver for masonite. It adds support for socketio.
A lightweight Python module to interact with the Mitre Att&ck Enterprise dataset.
enterpriseattack - Mitre's Enterprise Att&ck A lightweight Python module to interact with the Mitre Att&ck Enterprise dataset. Built to be used in pro

KonomiTV: Kind and Optimized Next brOadcast watching systeM Infrastructure for TV
備考・注意事項 現在 α 版で、まだ実験的なプロダクトです。通常利用には耐えないでしょうし、サポートもできません。 安定しているとは到底言いがたい品質ですが、それでも構わない方のみ導入してください。 使い方などの説明も用意できていないため、自力でトラブルに対処できるエンジニアの方以外には現状おすすめ
Signatures and IoCs from public Volexity blog posts.
threat-intel This repository contains IoCs related to Volexity public threat intelligence blog posts. They are organised by year, and within each year
A simple Telegram bot that can broadcast messages and media to the bot subscribers. with mongo DB support
𝘽𝙧𝙤𝙖𝙙𝙘𝙖𝙨𝙩 𝘽𝙤𝙩 A simple Telegram bot that can broadcast messages and media to the bot subscribers using MongoDB. Features Support mongodb.c
A bot can be used to broadcast your messages ( Text & Media ) to the Subscribers
Broadcast Bot A Telegram bot to send messages and medias to the subscribers directly through bot. Authorized users of the bot can send messages (Texts
AIL LeakFeeder: A Module for AIL Framework that automate the process to feed leaked files automatically to AIL
AIL LeakFeeder: A Module for AIL Framework that automates the process to feed leaked files automatically to AIL, So basically this feeder will help you ingest AIL with your leaked files automatically.
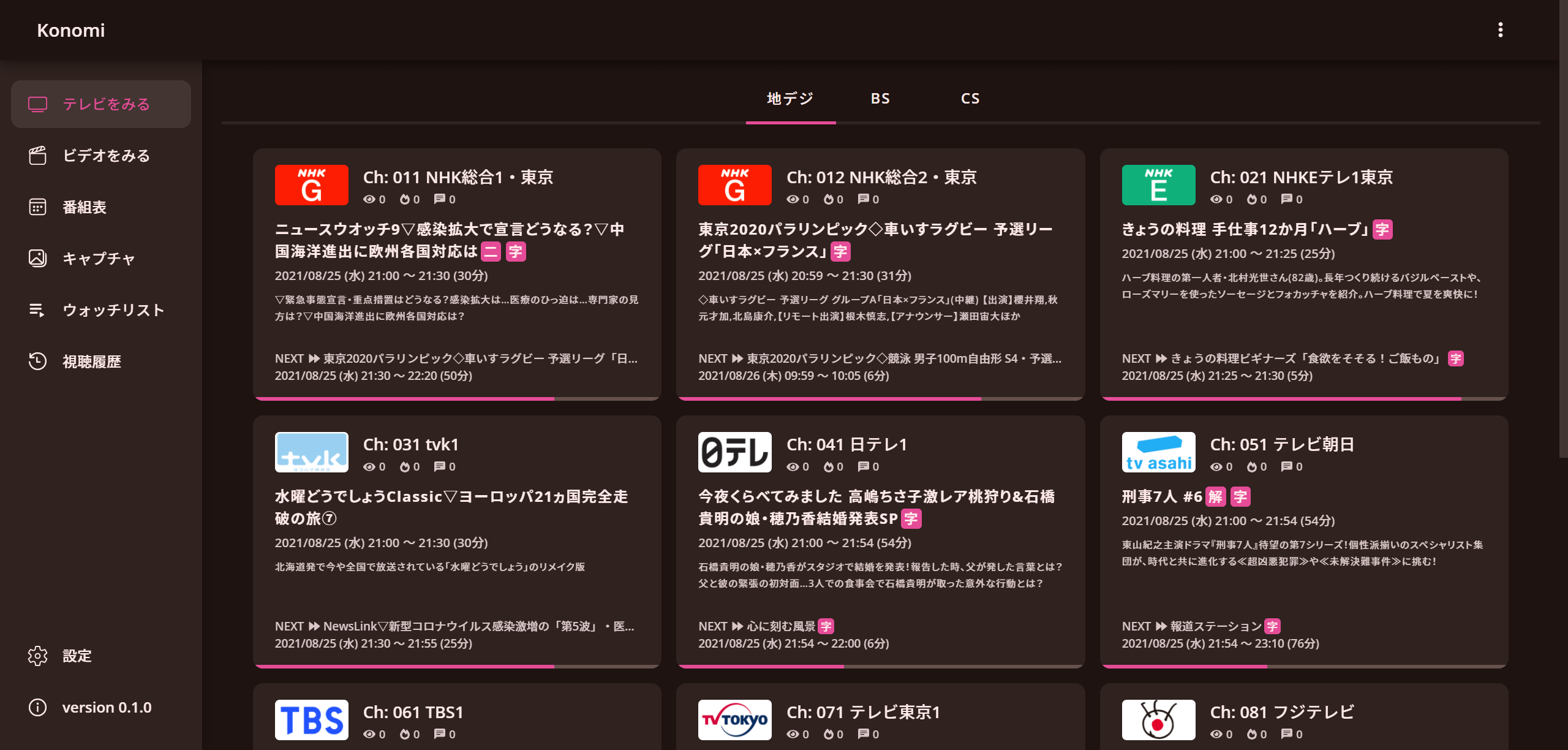
Konomi: Kind and Optimized Next brOadcast watching systeM Infrastructure
Konomi 備考・注意事項 現在 α 版で、まだ実験的なプロダクトです。通常利用には耐えないでしょうし、サポートもできません。 安定しているとは到底言いがたい品質ですが、それでも構わない方のみ導入してください。 使い方などの説明も用意できていないため、自力でトラブルに対処できるエンジニアの方以外に
evtx-hunter helps to quickly spot interesting security-related activity in Windows Event Viewer (EVTX) files.
Introduction evtx-hunter helps to quickly spot interesting security-related activity in Windows Event Viewer (EVTX) files. It can process a high numbe

An advanced real time threat intelligence framework to identify threats and malicious web traffic on the basis of IP reputation and historical data.
ARTIF is a new advanced real time threat intelligence framework built that adds another abstraction layer on the top of MISP to identify threats and malicious web traffic on the basis of IP reputation and historical data. It also performs automatic enrichment and threat scoring by collecting, processing and correlating observables based on different factors.

This little tool is to calculate a MurmurHash value of a favicon to hunt phishing websites on the Shodan platform.
MurMurHash This little tool is to calculate a MurmurHash value of a favicon to hunt phishing websites on the Shodan platform. What is MurMurHash? Murm

Kestrel Threat Hunting Language
Kestrel Threat Hunting Language What is Kestrel? Why we need it? How to hunt with XDR support? What is the science behind it? You can find all the ans

Domain Connectivity Analysis Tools to analyze aggregate connectivity patterns across a set of domains during security investigations
DomainCAT (Domain Connectivity Analysis Tool) Domain Connectivity Analysis Tool is used to analyze aggregate connectivity patterns across a set of dom
A fast and durable Pub/Sub channel over Websockets. FastAPI + WebSockets + PubSub == ⚡ 💪 ❤️
⚡ 🗞️ FastAPI Websocket Pub/Sub A fast and durable Pub/Sub channel over Websockets. The easiest way to create a live publish / subscribe multi-cast ov
Cowrie SSH/Telnet Honeypot https://cowrie.readthedocs.io
Cowrie Welcome to the Cowrie GitHub repository This is the official repository for the Cowrie SSH and Telnet Honeypot effort. What is Cowrie Cowrie is
Threat Intelligence Gathering 威胁情报收集,旨在提高蓝队拿到攻击 IP 后对其进行威胁情报信息收集的效率。
0x00 介绍 tig Threat Intelligence Gathering 威胁情报收集,旨在提高蓝队拿到攻击 IP 后对其进行威胁情报信息收集的效率,目前已集成微步、IP 域名反查、Fofa 信息收集、ICP 备案查询、IP 存活检测五个模块,现已支持以下信息的查询: ✅ 微步标签 ✅ I

威胁情报播报
Threat-Broadcast 威胁情报播报 运行环境 项目介绍 从以下公开的威胁情报来源爬取并整合最新信息: 360:https://cert.360.cn/warning 奇安信:https://ti.qianxin.com/advisory/ 红后:https://redqueen.tj-u
APT-Hunter is Threat Hunting tool for windows event logs
APT-Hunter is Threat Hunting tool for windows event logs which made by purple team mindset to provide detect APT movements hidden in the sea of windows event logs to decrease the time to uncover suspicious activity
DaProfiler vous permet d'automatiser vos recherches sur des particuliers basés en France uniquement et d'afficher vos résultats sous forme d'arbre.
A but educatif seulement. DaProfiler DaProfiler vous permet de créer un profil sur votre target basé en France uniquement. La particularité de ce prog