175 Repositories
Python vulnerability-exploit Libraries

Dockerized Spring4Shell (CVE-2022-22965) PoC application and exploit
Spring4Shell PoC Application This is a dockerized application that is vulnerable to the Spring4Shell vulnerability (CVE-2022-22965). Full Java source

DLLirant is a tool to automatize the DLL Hijacking researches on a specified binary.
DLLirant DLLirant is a tool to automatize the DLL Hijacking researches on a specified binary. Live Demo How to install You need to install Visual Stud
Everything I needed to understand what was going on with "Spring4Shell" - translated source materials, exploit, links to demo apps, and more.
springcore-0day-en These are all my notes from the alleged confirmed! 0day dropped on 2022-03-29. This vulnerability is commonly referred to as "Sprin
Exploit and Check Script for CVE 2022-1388
F5-CVE-2022-1388-Exploit Exploit and Check Script for CVE 2022-1388 Usage Check against single host python3 CVE-2022-1388.py -v true -u target_url At

😭 WSOB is a python tool created to exploit the new vulnerability on WSO2 assigned as CVE-2022-29464.
😭 WSOB (CVE-2022-29464) 😭 WSOB is a python tool created to exploit the new vulnerability on WSO2 assigned as CVE-2022-29464. CVE-2022-29464 details:

A simple tool to audit Unix/*BSD/Linux system libraries to find public security vulnerabilities
master_librarian A simple tool to audit Unix/*BSD/Linux system libraries to find public security vulnerabilities. To install requirements: $ sudo pyth
HTTP Protocol Stack Remote Code Execution Vulnerability CVE-2022-21907
CVE-2022-21907 Description POC for CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability. create by antx at 2022-01-17. Detail HTTP

Red Team Toolkit is an Open-Source Django Offensive Web-App which is keeping the useful offensive tools used in the red-teaming together.
RedTeam Toolkit Note: Only legal activities should be conducted with this project. Red Team Toolkit is an Open-Source Django Offensive Web-App contain

automatically crawl every URL and find cross site scripting (XSS)
scancss Fastest tool to find XSS. scancss is a fastest tool to detect Cross Site scripting (XSS) automatically and it's also an intelligent payload ge
Discord Region Swapping Exploit (VC Overload)
Discord-VC-Exploit Discord Region Swapping Exploit (VC Overload) aka VC Crasher How does this work? Discord has multiple servers that lets people arou
wsvuls - website vulnerability scanner detect issues [ outdated server software and insecure HTTP headers.]
WSVuls Website vulnerability scanner detect issues [ outdated server software and insecure HTTP headers.] What's WSVuls? WSVuls is a simple and powerf

Dark Finix: All in one hacking framework with almost 100 tools
Dark Finix - Hacking Framework. Dark Finix is a all in one hacking framework wit
CVE-2022-22536 - SAP memory pipes(MPI) desynchronization vulnerability CVE-2022-22536
CVE-2022-22536 SAP memory pipes desynchronization vulnerability(MPI) CVE-2022-22

CVE-2022-23046 - SQL Injection Vulnerability on PhpIPAM v1.4.4
CVE-2022-23046 PhpIPAM v1.4.4 allows an authenticated admin user to inject SQL s
VHub - An API that permits uploading of vulnerability datasets and return of the serialized data
VHub - An API that permits uploading of vulnerability datasets and return of the serialized data
FAVD: Featherweight Assisted Vulnerability Discovery
FAVD: Featherweight Assisted Vulnerability Discovery This repository contains the replication package for the paper "Featherweight Assisted Vulnerabil
AnonStress-Stored-XSS-Exploit - An exploit and demonstration on how to exploit a Stored XSS vulnerability in anonstress
AnonStress Stored XSS Exploit An exploit and demonstration on how to exploit a S
JstDoS - HTTP Protocol Stack Remote Code Execution Vulnerability
jstDoS If you are going to skid that, please give credits ! ^^ ¿How works? This

A simple python script to dump remote files through a local file read or local file inclusion web vulnerability.
A simple python script to dump remote files through a local file read or local file inclusion web vulnerability. Features Dump a single file w
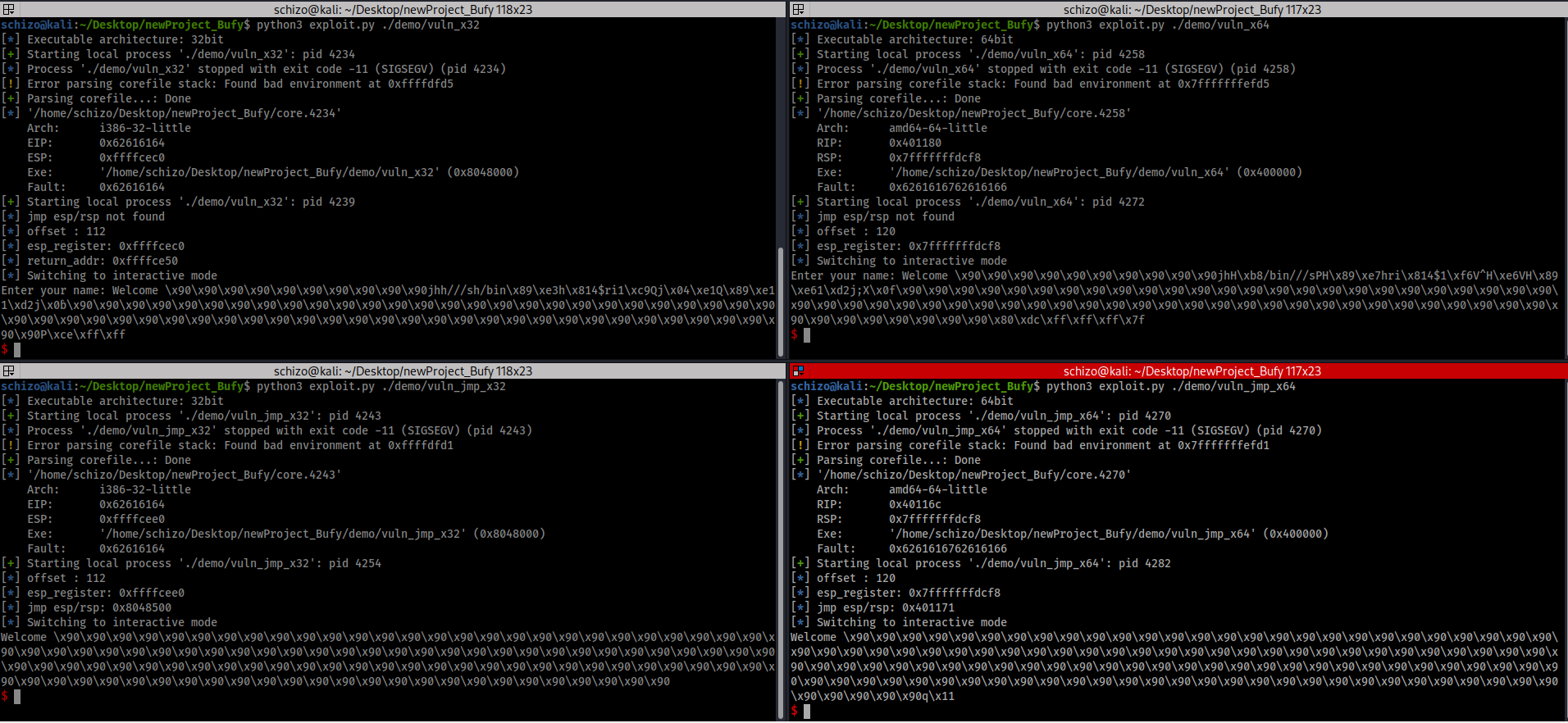
Automated tool to exploit basic buffer overflow remotely and locally & x32 and x64
Automated tool to exploit basic buffer overflow (remotely or locally) & (x32 or x64)
Robust and blazing fast open-redirect vulnerability scanner with ability of recursevely crawling all of web-forms, entry points, or links with data.
After Golismero project got dead there is no more any up to date open-source tool that can collect links with parametrs and web-forms and then test th
TightVNC Vulnerability.
CVE-2022-23967 In TightVNC 1.3.10, there is an integer signedness error and resultant heap-based buffer overflow in InitialiseRFBConnection in rfbprot
Python exploit code for CVE-2021-4034 (pwnkit)
Python3 code to exploit CVE-2021-4034 (PWNKIT). This was an exercise in "can I make this work in Python?", and not meant as a robust exploit. It Works

Adversarial vulnerability of powerful near out-of-distribution detection
Adversarial vulnerability of powerful near out-of-distribution detection by Stanislav Fort In this repository we're collecting replications for the ke
CVE-2022-21907 Vulnerability PoC
CVE-2022-21907 Description POC for CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability. create by antx at 2022-01-17, just some sm
This repository detects a system vulnerable to CVE-2022-21907 and protects against this vulnerability if desired
This repository detects a system vulnerable to CVE-2022-21907 and protects against this vulnerability if desired
SonicWall SMA-100 Unauth RCE Exploit (CVE-2021-20038)
Bad Blood Bad Blood is an exploit for CVE-2021-20038, a stack-based buffer overflow in the httpd binary of SMA-100 series systems using firmware versi

Automated tool to find & created Exploit Poc for Clickjacking Vulnerability
ClickJackPoc This tool will help you automate finding Clickjacking Vulnerability by just passing a file containing list of Targets . Once the Target i
Security audit Python project dependencies against security advisory databases.
Security audit Python project dependencies against security advisory databases.
Validate arbitrary image uploads from incoming data urls while preserving file integrity but removing EXIF and unwanted artifacts and RCE exploit potential
Validate arbitrary base64-encoded image uploads as incoming data urls while preserving image integrity but removing EXIF and unwanted artifacts and mitigating RCE-exploit potential.

Click-Jack - Automatic tool to find Clickjacking Vulnerability in various Web applications
CLICK-Jack It is a automatic tool to find Clickjacking Vulnerability in various
labsecurity is a tool that brings together python scripts made for ethical hacking, in a single tool, through a console interface
labsecurity labsecurity is a tool that brings together python scripts made for ethical hacking, in a single tool, through a console interface. Warning
Find-Xss - Termux Kurulum Dosyası Eklendi Eğer Hata Alıyorsanız Lütfen Resmini Çekip İnstagramdan Bildiriniz
FindXss Waf Bypass Eklendi !!! PRODUCER: Saep UPDATER: Aser-Vant Download: git c

NS-Defacer: a auto html injecter, In other words It's a auto defacer to deface a lot of websites in less time
Overview NS-Defacer is a auto html injecter, In other words It's a auto defacer
An interactive python script that enables root access on the T-Mobile (Wingtech) TMOHS1, as well as providing several useful utilites to change the configuration of the device.
TMOHS1 Root Utility Description An interactive python script that enables root access on the T-Mobile (Wingtech) TMOHS1, as well as providing several
Discord-email-spammer-exploit - A discord email spammer exploit with python
Discord-email-spammer-exploit was made by Love ❌ code ✅ 🎈 ・Description First it

Tinyman exploit finder - Tinyman exploit finder for python
tinyman_exploit_finder There was a big tinyman exploit. You can read about it he
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging features for exploit developers & reverse engineers ☢
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging features for exploit developers & reverse engineers ☢

Faza - Faza terminal, Faza help to beginners for pen testing
Faza terminal simple tool for pen testers Use small letter only for commands Don't use space after command 'help' for more information Installation gi

Raphael is a vulnerability scanning tool based on Python3.
Raphael Raphael是一款基于Python3开发的插件式漏洞扫描工具。 Raphael is a vulnerability scanning too
Auerswald COMpact 8.0B Backdoors exploit
CVE-2021-40859 Auerswald COMpact 8.0B Backdoors exploit About Backdoors were discovered in Auerswald COMpact 5500R 7.8A and 8.0B devices, that allow a
CVE-2021-43936 is a critical vulnerability (CVSS3 10.0) leading to Remote Code Execution (RCE) in WebHMI Firmware.
CVE-2021-43936 CVE-2021-43936 is a critical vulnerability (CVSS3 10.0) leading to Remote Code Execution (RCE) in WebHMI Firmware. This vulnerability w
Auerswald COMpact 8.0B Backdoors exploit
CVE-2021-40859 Auerswald COMpact 8.0B Backdoors exploit About Backdoors were discovered in Auerswald COMpact 5500R 7.8A and 8.0B devices, that allow a
The Multi-Tool Web Vulnerability Scanner.
🟥 RapidScan v1.2 - The Multi-Tool Web Vulnerability Scanner RapidScan has been ported to Python3 i.e. v1.2. The Python2.7 codebase is available on v1
CVE 2020-14871 Solaris exploit
CVE 2020-14871 Solaris exploit This is a basic ROP based exploit for CVE 2020-14871. CVE 2020-14871 is a vulnerability in Sun Solaris systems. The act
Exploit ILP to learn symmetry breaking constraints of ASP programs.
ILP Symmetry Breaking Overview This project aims to exploit inductive logic programming to lift symmetry breaking constraints of ASP programs. Given a

open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability
CVE-2021-44228-log4jVulnScanner-metasploit open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability pre
Python script who crawl first shodan page and check DBLTEK vulnerability
🐛 MASS DBLTEK EXPLOIT CHECKER USING SHODAN 🕸 Python script who crawl first shodan page and check DBLTEK vulnerability
telegram bug that discloses user's hidden phone number (still unpatched) (exploit included)
CVE-2019-15514 Type: Information Disclosure Affected Users, Versions, Devices: All Telegram Users Still not fixed/unpatched. brute.py is available exp
log4j2 dos exploit,CVE-2021-45105 exploit,Denial of Service poc
说明 about author: 我超怕的 blog: https://www.cnblogs.com/iAmSoScArEd/ github: https://github.com/iAmSOScArEd/ date: 2021-12-20 log4j2 dos exploit log4j2 do

Execution After Redirect (EAR) / Long Response Redirection Vulnerability Scanner written in python3
Execution After Redirect (EAR) / Long Response Redirection Vulnerability Scanner written in python3, It Fuzzes All URLs of target website & then scan them for EAR
Multi-Process Vulnerability Tool
Multi-Process Vulnerability Tool

A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability
log4j-shell-poc A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability. Recently there was a new vulnerability in log4j, a java loggin
A scanner and a proof of sample exploit for log4j RCE CVE-2021-44228
1.Create a Sample Vulnerable Application . 2.Start a netcat listner . 3.Run the exploit . 5.Use jdk1.8.0_20 for better results . Exploit-db - https://
Simulating Log4j Remote Code Execution (RCE) vulnerability in a flask web server using python's logging library with custom formatter that simulates lookup substitution by executing remote exploit code.
py4jshell Simulating Log4j Remote Code Execution (RCE) CVE-2021-44228 vulnerability in a flask web server using python's logging library with custom f
This exploit allows to connect to the remote RemoteMouse 3.008 service to virtually press arbitrary keys and execute code on the machine.
RemoteMouse-3.008-Exploit The RemoteMouse application is a program for remotely controlling a computer from a phone or tablet. This exploit allows to
labsecurity is a framework and its use is for ethical hacking and computer security
labsecurity labsecurity is a framework and its use is for ethical hacking and computer security. Warning This tool is only for educational purpose. If

An automated, reliable scanner for the Log4Shell (CVE-2021-44228) vulnerability.
Log4JHunt An automated, reliable scanner for the Log4Shell CVE-2021-44228 vulnerability. Video demo: Usage Here the help usage: $ python3 log4jhunt.py
This python script will automate the testing for the Log4J vulnerability for HTTP and HTTPS connections.
Log4J-Huntress-Automate-Script This python script will automate the testing for the Log4J vulnerability for HTTP and HTTPS connections. Pre-Requisits
Operational information regarding the vulnerability in the Log4j logging library.
Log4j Vulnerability (CVE-2021-44228) This repo contains operational information regarding the vulnerability in the Log4j logging library (CVE-2021-442
A honeypot for the Log4Shell vulnerability (CVE-2021-44228)
Log4Pot A honeypot for the Log4Shell vulnerability (CVE-2021-44228). License: GPLv3.0 Features Listen on various ports for Log4Shell exploitation. Det
Python script to tamper with pages to test for Log4J Shell vulnerability.
log4jShell Scanner This shell script scans a vulnerable web application that is using a version of apache-log4j 2.15.0. This application is a static
Provides script to download and format public IP lists related to the Log4j exploit.
Provides script to download and format public IP lists related to the Log4j exploit. Current format includes: plain list, Cisco ASA Network Group.
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability

Providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account.
We are providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account. The script enables security teams to identify external-facing AWS assets by running the exploit on them, and thus be able to map them and quickly patch them
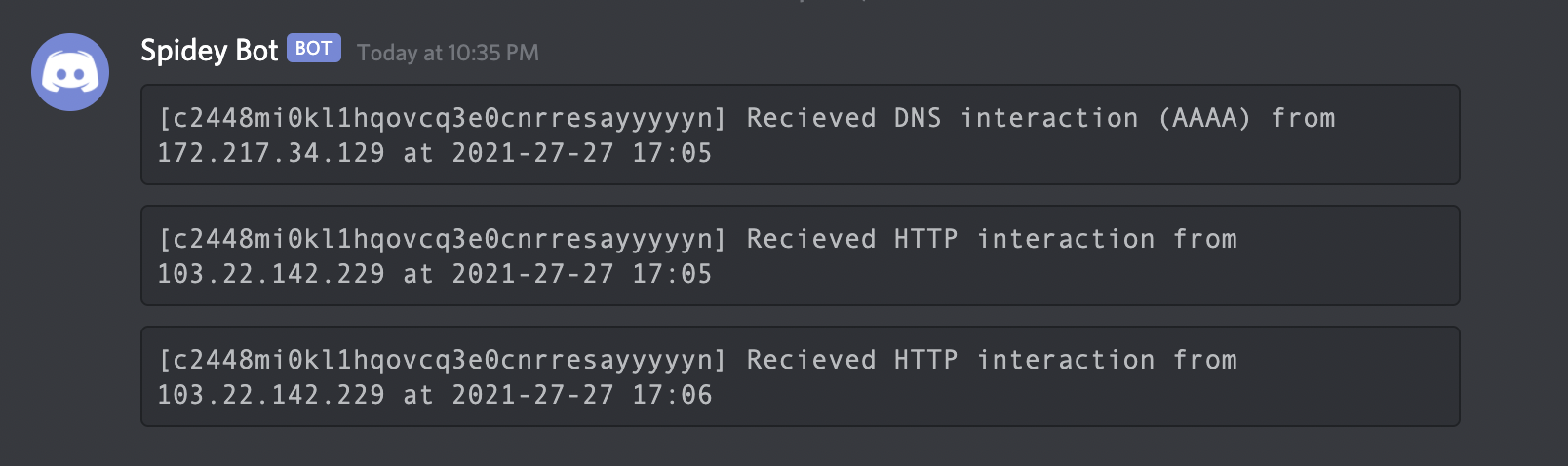
POC for detecting the Log4Shell (Log4J RCE) vulnerability
Interactsh An OOB interaction gathering server and client library Features • Usage • Interactsh Client • Interactsh Server • Interactsh Integration •
POC for detecting the Log4Shell (Log4J RCE) vulnerability.
log4shell-poc-py POC for detecting the Log4Shell (Log4J RCE) vulnerability. Run on a system with python3 python3 log4shell-poc.py pathToTargetFile
Python3 script for scanning CVE-2021-44228 (Log4shell) vulnerable machines.
Log4j_checker.py (CVE-2021-44228) Description This Python3 script tries to look for servers vulnerable to CVE-2021-44228, also known as Log4Shell, a v

Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading
log4j-detect Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading The script

CTF framework and exploit development library
pwntools - CTF toolkit Pwntools is a CTF framework and exploit development library. Written in Python, it is designed for rapid prototyping and develo
Log4Shell RCE Exploit - fully independent exploit does not require any 3rd party binaries.
Log4Shell RCE Exploit fully independent exploit does not require any 3rd party binaries. The exploit spraying the payload to all possible logged HTTP

Exploit tool for Adminer 1.0 up to 4.6.2 Arbitrary File Read vulnerability
AdminerRead Exploit tool for Adminer 1.0 up to 4.6.2 Arbitrary File Read vulnerability Installation git clone https://github.com/p0dalirius/AdminerRea
A Docker based LDAP RCE exploit demo for CVE-2021-44228 Log4Shell
log4j-poc An LDAP RCE exploit for CVE-2021-44228 Log4Shell Description This demo Tomcat 8 server has a vulnerable app deployed on it and is also vulne
A small Minecraft server to help players detect vulnerability to the Log4Shell exploit 🐚
log4check A small Minecraft server to help players detect vulnerability to the Log4Shell exploit 🐚 Tested to work between Minecraft versions 1.12.2 a

A proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228)
CVE-2021-44228 – Log4j RCE Unauthenticated About This is a proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228). This vulnerability
Script checks provided domains for log4j vulnerability
log4j Script checks provided domains for log4j vulnerability. A token is created with canarytokens.org and passed as header at request for a single do

This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798).
CVE-2021-43798 – Grafana Exploit About This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798

Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading
log4j-detect Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading The script
Log4j exploit catcher, detect Log4Shell exploits and try to get payloads.
log4j_catcher Log4j exploit catcher, detect Log4Shell exploits and try to get payloads. This is a basic python server that listen on a port and logs i

Proof of Concept Exploit for ManageEngine ServiceDesk Plus CVE-2021-44077
CVE-2021-44077 Proof of Concept Exploit for CVE-2021-44077: PreAuth RCE in ManageEngine ServiceDesk Plus 11306 Based on: https://xz.aliyun.com/t/106
Exploit grafana Pre-Auth LFI
Grafana-LFI-8.x Exploit grafana Pre-Auth LFI How to use python3
This repo explains in details about buffer overflow exploit development for windows executable.
Buffer Overflow Exploit Development For Beginner Introduction I am beginner in security community and as my fellow beginner, I spend some of my time a
FIVE, Vulnerability Scanner And Mass Exploiter, made for pentesting.
$ FIVE - FIVE is a Pentesting Framework to Test the Security & Integrity of a Website, or Multiple Websites. $ Info FIVE Was Made After Vulnnr to Prod
Exploit-CVE-2021-21086
CVE-2021-21086 Exploit This exploit allows to execute a shellcode in the context of the rendering process of Adobe Acrobat Reader DC 2020.013.20074 an
Buffer Overflow para SLmail5.5 32 bits
SLmail5.5-Exploit-BoF Buffer Overflow para SLmail5.5 32 bits con un par de utilidades para que puedas hacer el tuyo REQUISITOS PARA QUE FUNCIONE: Desa
Chrome Post-Exploitation is a client-server Chrome exploit to remotely allow an attacker access to Chrome passwords, downloads, history, and more.
ChromePE [Linux/Windows] Chrome Post-Exploitation is a client-server Chrome exploit to remotely allow an attacker access to Chrome passwords, download

IP Denial of Service Vulnerability ")A proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability ")
CVE-2021-24086 This is a proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability "), a NULL dereference in tcpip.sys patc
BOF-Roaster is an automated buffer overflow exploit machine which is begin written with Python 3.
BOF-Roaster is an automated buffer overflow exploit machine which is begin written with Python 3. On first release it was able to successfully break many of the most well-known buffer overflow example executables.

Moodle community-based vulnerability scanner
badmoodle Moodle community-based vulnerability scanner Description badmoodle is an unofficial community-based vulnerability scanner for moodle that sc
neo Tool is great one in binary exploitation topic
neo Tool is great one in binary exploitation topic. instead of doing several missions by many tools and windows, you can now automate this in one tool in one session.. Enjoy it
A tool that updates all your project's Python dependency files through Pull Requests on GitHub/GitLab.
A tool that updates all your project's Python dependency files through Pull Requests on GitHub/GitLab. About This repo contains the bot that is runnin
cve-search - a tool to perform local searches for known vulnerabilities
cve-search cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitat

Fast and customizable vulnerability scanner For JIRA written in Python
Fast and customizable vulnerability scanner For JIRA. 🤔 What is this? Jira-Lens 🔍 is a Python Based vulnerability Scanner for JIRA. Jira is a propri
Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamically linked.
GoAhead RCE Exploit Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamic
Vulnerability Exploitation Code Collection Repository
Introduction expbox is an exploit code collection repository List CVE-2021-41349 Exchange XSS PoC = Exchange 2013 update 23 = Exchange 2016 update 2
Remote control your Greenbone Vulnerability Manager (GVM)
Greenbone Vulnerability Management Tools The Greenbone Vulnerability Management Tools gvm-tools are a collection of tools that help with remote contro
Exploit for GitLab CVE-2021-22205 Unauthenticated Remote Code Execution
Vuln Impact An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not properly validating image files tha
Collection Of Discord Hacking Tools / Fun Stuff / Exploits That Is Completely Made Using Python.
Venom Collection Of Discord Hacking Tools / Fun Stuff / Exploits That Is Completely Made Using Python. Report Bug · Request Feature Contributing Well,
On the 11/11/21 the apache 2.4.49-2.4.50 remote command execution POC has been published online and this is a loader so that you can mass exploit servers using this.
ApacheRCE ApacheRCE is a small little python script that will allow you to input the apache version 2.4.49-2.4.50 and then input a list of ip addresse

Python exploit for vsftpd 2.3.4 - Backdoor Command Execution
CVE-2011-2523 - vsftpd 2.3.4 Exploit Discription vsftpd, which stands for Very Secure FTP Daemon,is an FTP server for Unix-like systems, including Lin