114 Repositories
Python xss-exploit Libraries

Dockerized Spring4Shell (CVE-2022-22965) PoC application and exploit
Spring4Shell PoC Application This is a dockerized application that is vulnerable to the Spring4Shell vulnerability (CVE-2022-22965). Full Java source
Everything I needed to understand what was going on with "Spring4Shell" - translated source materials, exploit, links to demo apps, and more.
springcore-0day-en These are all my notes from the alleged confirmed! 0day dropped on 2022-03-29. This vulnerability is commonly referred to as "Sprin
Exploit and Check Script for CVE 2022-1388
F5-CVE-2022-1388-Exploit Exploit and Check Script for CVE 2022-1388 Usage Check against single host python3 CVE-2022-1388.py -v true -u target_url At

😭 WSOB is a python tool created to exploit the new vulnerability on WSO2 assigned as CVE-2022-29464.
😭 WSOB (CVE-2022-29464) 😭 WSOB is a python tool created to exploit the new vulnerability on WSO2 assigned as CVE-2022-29464. CVE-2022-29464 details:

automatically crawl every URL and find cross site scripting (XSS)
scancss Fastest tool to find XSS. scancss is a fastest tool to detect Cross Site scripting (XSS) automatically and it's also an intelligent payload ge
Discord Region Swapping Exploit (VC Overload)
Discord-VC-Exploit Discord Region Swapping Exploit (VC Overload) aka VC Crasher How does this work? Discord has multiple servers that lets people arou
AnonStress-Stored-XSS-Exploit - An exploit and demonstration on how to exploit a Stored XSS vulnerability in anonstress
AnonStress Stored XSS Exploit An exploit and demonstration on how to exploit a S

XSSearch - A comprehensive reflected XSS tool built on selenium framework in python
XSSearch A Comprehensive Reflected XSS Scanner XSSearch is a comprehensive refle
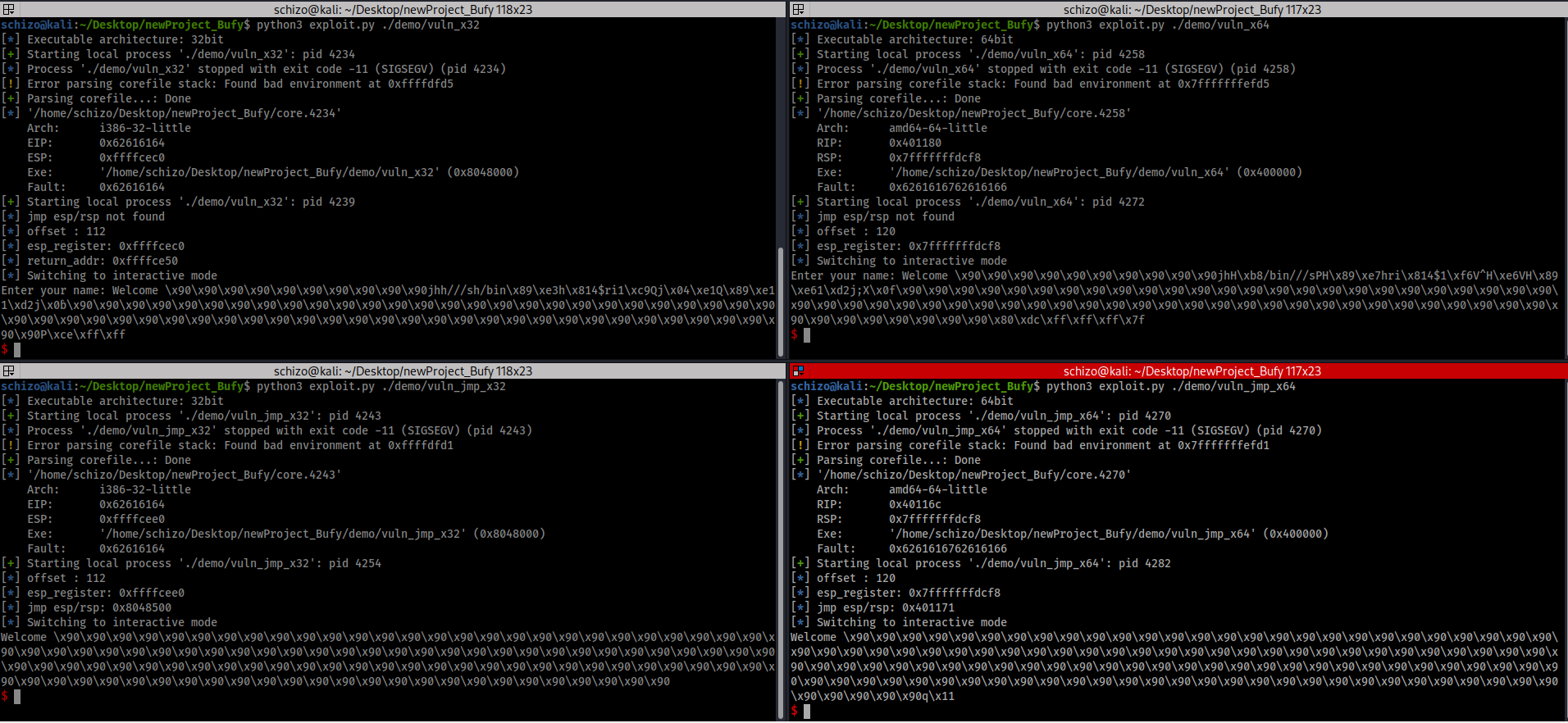
Automated tool to exploit basic buffer overflow remotely and locally & x32 and x64
Automated tool to exploit basic buffer overflow (remotely or locally) & (x32 or x64)
Python exploit code for CVE-2021-4034 (pwnkit)
Python3 code to exploit CVE-2021-4034 (PWNKIT). This was an exercise in "can I make this work in Python?", and not meant as a robust exploit. It Works
TheTimeMachine - Weaponizing WaybackUrls for Recon, BugBounties , OSINT, Sensitive Endpoints and what not
The Time Machine - Weaponizing WaybackUrls for Recon, BugBounties , OSINT, Sensi
SonicWall SMA-100 Unauth RCE Exploit (CVE-2021-20038)
Bad Blood Bad Blood is an exploit for CVE-2021-20038, a stack-based buffer overflow in the httpd binary of SMA-100 series systems using firmware versi

Automated tool to find & created Exploit Poc for Clickjacking Vulnerability
ClickJackPoc This tool will help you automate finding Clickjacking Vulnerability by just passing a file containing list of Targets . Once the Target i
Validate arbitrary image uploads from incoming data urls while preserving file integrity but removing EXIF and unwanted artifacts and RCE exploit potential
Validate arbitrary base64-encoded image uploads as incoming data urls while preserving image integrity but removing EXIF and unwanted artifacts and mitigating RCE-exploit potential.
labsecurity is a tool that brings together python scripts made for ethical hacking, in a single tool, through a console interface
labsecurity labsecurity is a tool that brings together python scripts made for ethical hacking, in a single tool, through a console interface. Warning
Find-Xss - Termux Kurulum Dosyası Eklendi Eğer Hata Alıyorsanız Lütfen Resmini Çekip İnstagramdan Bildiriniz
FindXss Waf Bypass Eklendi !!! PRODUCER: Saep UPDATER: Aser-Vant Download: git c

NS-Defacer: a auto html injecter, In other words It's a auto defacer to deface a lot of websites in less time
Overview NS-Defacer is a auto html injecter, In other words It's a auto defacer
An interactive python script that enables root access on the T-Mobile (Wingtech) TMOHS1, as well as providing several useful utilites to change the configuration of the device.
TMOHS1 Root Utility Description An interactive python script that enables root access on the T-Mobile (Wingtech) TMOHS1, as well as providing several
Discord-email-spammer-exploit - A discord email spammer exploit with python
Discord-email-spammer-exploit was made by Love ❌ code ✅ 🎈 ・Description First it
Python library to prevent XSS(cross site scripting attach) by removing harmful content from data.
A tool for removing malicious content from input data before saving data into database. It takes input containing HTML with XSS scripts and returns va

Tinyman exploit finder - Tinyman exploit finder for python
tinyman_exploit_finder There was a big tinyman exploit. You can read about it he
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging features for exploit developers & reverse engineers ☢
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging features for exploit developers & reverse engineers ☢

Faza - Faza terminal, Faza help to beginners for pen testing
Faza terminal simple tool for pen testers Use small letter only for commands Don't use space after command 'help' for more information Installation gi
Auerswald COMpact 8.0B Backdoors exploit
CVE-2021-40859 Auerswald COMpact 8.0B Backdoors exploit About Backdoors were discovered in Auerswald COMpact 5500R 7.8A and 8.0B devices, that allow a
Auerswald COMpact 8.0B Backdoors exploit
CVE-2021-40859 Auerswald COMpact 8.0B Backdoors exploit About Backdoors were discovered in Auerswald COMpact 5500R 7.8A and 8.0B devices, that allow a
CVE 2020-14871 Solaris exploit
CVE 2020-14871 Solaris exploit This is a basic ROP based exploit for CVE 2020-14871. CVE 2020-14871 is a vulnerability in Sun Solaris systems. The act

The AWS Lambda Serverless Blind XSS App
Ass The AWS Lambda Serverless Blind XSS App 利用VPS配置XSS平台太麻烦了,如果利用AWS的Lambda那不就是一个域名的事情么?剩下的环境配置、HTTPS证书、隐私性、VPS续费都不用管了, 所以根据xless重写了Lambda平台的XSS,利用sla
Exploit ILP to learn symmetry breaking constraints of ASP programs.
ILP Symmetry Breaking Overview This project aims to exploit inductive logic programming to lift symmetry breaking constraints of ASP programs. Given a
telegram bug that discloses user's hidden phone number (still unpatched) (exploit included)
CVE-2019-15514 Type: Information Disclosure Affected Users, Versions, Devices: All Telegram Users Still not fixed/unpatched. brute.py is available exp
log4j2 dos exploit,CVE-2021-45105 exploit,Denial of Service poc
说明 about author: 我超怕的 blog: https://www.cnblogs.com/iAmSoScArEd/ github: https://github.com/iAmSOScArEd/ date: 2021-12-20 log4j2 dos exploit log4j2 do
A scanner and a proof of sample exploit for log4j RCE CVE-2021-44228
1.Create a Sample Vulnerable Application . 2.Start a netcat listner . 3.Run the exploit . 5.Use jdk1.8.0_20 for better results . Exploit-db - https://
Simulating Log4j Remote Code Execution (RCE) vulnerability in a flask web server using python's logging library with custom formatter that simulates lookup substitution by executing remote exploit code.
py4jshell Simulating Log4j Remote Code Execution (RCE) CVE-2021-44228 vulnerability in a flask web server using python's logging library with custom f
This exploit allows to connect to the remote RemoteMouse 3.008 service to virtually press arbitrary keys and execute code on the machine.
RemoteMouse-3.008-Exploit The RemoteMouse application is a program for remotely controlling a computer from a phone or tablet. This exploit allows to
labsecurity is a framework and its use is for ethical hacking and computer security
labsecurity labsecurity is a framework and its use is for ethical hacking and computer security. Warning This tool is only for educational purpose. If
Provides script to download and format public IP lists related to the Log4j exploit.
Provides script to download and format public IP lists related to the Log4j exploit. Current format includes: plain list, Cisco ASA Network Group.
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability
Python3 script for scanning CVE-2021-44228 (Log4shell) vulnerable machines.
Log4j_checker.py (CVE-2021-44228) Description This Python3 script tries to look for servers vulnerable to CVE-2021-44228, also known as Log4Shell, a v

CTF framework and exploit development library
pwntools - CTF toolkit Pwntools is a CTF framework and exploit development library. Written in Python, it is designed for rapid prototyping and develo
Log4Shell RCE Exploit - fully independent exploit does not require any 3rd party binaries.
Log4Shell RCE Exploit fully independent exploit does not require any 3rd party binaries. The exploit spraying the payload to all possible logged HTTP

Exploit tool for Adminer 1.0 up to 4.6.2 Arbitrary File Read vulnerability
AdminerRead Exploit tool for Adminer 1.0 up to 4.6.2 Arbitrary File Read vulnerability Installation git clone https://github.com/p0dalirius/AdminerRea
A Docker based LDAP RCE exploit demo for CVE-2021-44228 Log4Shell
log4j-poc An LDAP RCE exploit for CVE-2021-44228 Log4Shell Description This demo Tomcat 8 server has a vulnerable app deployed on it and is also vulne
A small Minecraft server to help players detect vulnerability to the Log4Shell exploit 🐚
log4check A small Minecraft server to help players detect vulnerability to the Log4Shell exploit 🐚 Tested to work between Minecraft versions 1.12.2 a

A proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228)
CVE-2021-44228 – Log4j RCE Unauthenticated About This is a proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228). This vulnerability

This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798).
CVE-2021-43798 – Grafana Exploit About This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798
Log4j exploit catcher, detect Log4Shell exploits and try to get payloads.
log4j_catcher Log4j exploit catcher, detect Log4Shell exploits and try to get payloads. This is a basic python server that listen on a port and logs i

Proof of Concept Exploit for ManageEngine ServiceDesk Plus CVE-2021-44077
CVE-2021-44077 Proof of Concept Exploit for CVE-2021-44077: PreAuth RCE in ManageEngine ServiceDesk Plus 11306 Based on: https://xz.aliyun.com/t/106
Exploit grafana Pre-Auth LFI
Grafana-LFI-8.x Exploit grafana Pre-Auth LFI How to use python3
This repo explains in details about buffer overflow exploit development for windows executable.
Buffer Overflow Exploit Development For Beginner Introduction I am beginner in security community and as my fellow beginner, I spend some of my time a
FIVE, Vulnerability Scanner And Mass Exploiter, made for pentesting.
$ FIVE - FIVE is a Pentesting Framework to Test the Security & Integrity of a Website, or Multiple Websites. $ Info FIVE Was Made After Vulnnr to Prod
Exploit-CVE-2021-21086
CVE-2021-21086 Exploit This exploit allows to execute a shellcode in the context of the rendering process of Adobe Acrobat Reader DC 2020.013.20074 an
Buffer Overflow para SLmail5.5 32 bits
SLmail5.5-Exploit-BoF Buffer Overflow para SLmail5.5 32 bits con un par de utilidades para que puedas hacer el tuyo REQUISITOS PARA QUE FUNCIONE: Desa
Chrome Post-Exploitation is a client-server Chrome exploit to remotely allow an attacker access to Chrome passwords, downloads, history, and more.
ChromePE [Linux/Windows] Chrome Post-Exploitation is a client-server Chrome exploit to remotely allow an attacker access to Chrome passwords, download
BOF-Roaster is an automated buffer overflow exploit machine which is begin written with Python 3.
BOF-Roaster is an automated buffer overflow exploit machine which is begin written with Python 3. On first release it was able to successfully break many of the most well-known buffer overflow example executables.

This a simple tool XSS Detection Suite for CTFs games
This a simple tool XSS Detection Suite for CTFs games
neo Tool is great one in binary exploitation topic
neo Tool is great one in binary exploitation topic. instead of doing several missions by many tools and windows, you can now automate this in one tool in one session.. Enjoy it
Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamically linked.
GoAhead RCE Exploit Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamic
Vulnerability Exploitation Code Collection Repository
Introduction expbox is an exploit code collection repository List CVE-2021-41349 Exchange XSS PoC = Exchange 2013 update 23 = Exchange 2016 update 2
XSS scanner in python
DeadXSS XSS scanner in python How to Download: Step 1: git clone https://github.com/Deadeye0x/DeadXSS.git Step 2: cd DeadXSS Step 3: python3 DeadXSS.p
Exploit for GitLab CVE-2021-22205 Unauthenticated Remote Code Execution
Vuln Impact An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not properly validating image files tha
Collection Of Discord Hacking Tools / Fun Stuff / Exploits That Is Completely Made Using Python.
Venom Collection Of Discord Hacking Tools / Fun Stuff / Exploits That Is Completely Made Using Python. Report Bug · Request Feature Contributing Well,
On the 11/11/21 the apache 2.4.49-2.4.50 remote command execution POC has been published online and this is a loader so that you can mass exploit servers using this.
ApacheRCE ApacheRCE is a small little python script that will allow you to input the apache version 2.4.49-2.4.50 and then input a list of ip addresse
It is a very simple XSS simulator based on flask, python.
It is a very simple XSS simulator based on flask, python. The purpose of making this is for teaching the concept of XSS.

Python exploit for vsftpd 2.3.4 - Backdoor Command Execution
CVE-2011-2523 - vsftpd 2.3.4 Exploit Discription vsftpd, which stands for Very Secure FTP Daemon,is an FTP server for Unix-like systems, including Lin
This is a repository filled with scripts that were made with Python, and designed to exploit computer systems.
PYTHON-EXPLOITATION This is a repository filled with scripts that were made with Python, and designed to exploit computer systems. Networking tcp_clin

AutoExploitSwagger is an automated API security testing exploit tool that can be combined with xray, BurpSuite and other scanners.
AutoExploitSwagger is an automated API security testing exploit tool that can be combined with xray, BurpSuite and other scanners.
command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validation, attacker can exploit the vulnerability to launch a command injection attack by sending some messages with malicious commands.
CVE-2021-36260 CVE-2021-36260 POC command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validatio
Wanli Li and Tieyun Qian: Exploit a Multi-head Reference Graph for Semi-supervised Relation Extraction, IJCNN 2021
MRefG Wanli Li and Tieyun Qian: "Exploit a Multi-head Reference Graph for Semi-supervised Relation Extraction", IJCNN 2021 1. Requirements To reproduc

How to exploit a double free vulnerability in 2021. 'Use-After-Free for Dummies'
This bug doesn’t exist on x86: Exploiting an ARM-only race condition How to exploit a double free and get a shell. "Use-After-Free for dummies" In thi
Dahua IPC/VTH/VTO devices auth bypass exploit
CVE-2021-33044 Dahua IPC/VTH/VTO devices auth bypass exploit About: The identity authentication bypass vulnerability found in some Dahua products duri
Multiple hacks that breaks the game
Blooket-Hack All of the cheats are based on a game mode.

👁️ Tool for Data Extraction and Web Requests.
httpmapper 👁️ Project • Technologies • Installation • How it works • License Project 🚧 For educational purposes. This is a project that I developed,
Simple PoC script that allows you to exploit telegram's "send with timer" feature by saving any media sent with this functionality.
Simple PoC script that allows you to exploit telegram's "send with timer" feature by saving any media sent with this functionality.
A multi exploit instagram exploitation framework
Instagram Exploitation Framework About IEF Is an open source Instagram Exploitation Framework with various Exploits that could be used to mod your pro
Phoenix Framework is an environment for writing, testing and using exploit code.
Phoenix-Framework Phoenix Framework is an environment for writing, testing and using exploit code. 🖼 Screenshots 🎪 Community PwnWiki Forums 🔑 Licen
BlueBorne Dockerized
BlueBorne Dockerized This is the repo to reproduce the BlueBorne kill-chain on Dockerized Android as described here, to fully understand the code you

discord vc exploit to lightly lag vcs
discord-vc-reconnector discord vc exploit to lag vcs how to use open the py file, then open devtools on discord, go to network and join a vc, dont sta

🎻 Modularized exploit generation framework
Modularized exploit generation framework for x86_64 binaries Overview This project is still at early stage of development, so you might want to come b

Proof on Concept Exploit for CVE-2021-38647 (OMIGOD)
OMIGOD Proof on Concept Exploit for CVE-2021-38647 (OMIGOD) For background information and context, read the our blog post detailing this vulnerabilit
Discord exploit allowing you to be unbannable.
Discord-Ban-Immunity Discord exploit allowing you to be unbannable. 9/3/2021 Found in late August. Found by Passive and Me. Explanation If a user gets

This repo contain builders of cab file, html file, and docx file for CVE-2021-40444 exploit
CVE-2021-40444 builders This repo contain builders of cab file, html file, and docx file for CVE-2021-40444 exploit. This repo is just for testing, re
A Python replicated exploit for Webmin 1.580 /file/show.cgi Remote Code Execution
CVE-2012-2982 John Hammond | September 4th, 2021 Checking searchsploit for Webmin 1.580 I only saw a Metasploit module for the /file/show.cgi Remote C

Übersicht remote command execution 0day exploit
Übersicht RCE 0day Unauthenticated remote command execution 0day exploit for Übersicht. Description Übersicht is a desktop widget application for m

WebScan is a web vulnerability Scanning tool, which scans sites for SQL injection and XSS vulnerabilities
WebScan is a web vulnerability Scanning tool, which scans sites for SQL injection and XSS vulnerabilities Which is a great tool for web pentesters. Coded in python3, CLI. WebScan is capable of scanning and detecting sql injection vulnerabilities across HTTP and HTTP sites.
adb - A tool that allows you to search for vulnerable android devices across the world and exploit them.
adb - An exploitation tool for android devices. A tool that allows you to search for vulnerable android devices across the world and exploit them. Fea
GraphQL security auditing script with a focus on performing batch GraphQL queries and mutations
BatchQL BatchQL is a GraphQL security auditing script with a focus on performing batch GraphQL queries and mutations. This script is not complex, and
Automatic ProxyShell Exploit
proxyshell-auto usage: proxyshell.py [-h] -t T Automatic Exploit ProxyShell optional arguments: -h, --help show this help message and exit -t T
ProxyShell POC Exploit : Exchange Server RCE (ACL Bypass + EoP + Arbitrary File Write)
ProxyShell Install git clone https://github.com/ktecv2000/ProxyShell cd ProxyShell virtualenv -p $(which python3) venv source venv/bin/activate pip3 i
Phoenix Framework is an environment for writing, testing and using exploit code.
Phoenix Framework is an environment for writing, testing and using exploit code. 🖼 Screenshots 🎪 Community PwnWiki Forums 🔑 Licen

Exploit Camera Raw Data for Video Super-Resolution via Hidden Markov Model Inference
RawVSR This repo contains the official codes for our paper: Exploit Camera Raw Data for Video Super-Resolution via Hidden Markov Model Inference Xiaoh

PwnWiki 数据库搜索命令行工具;该工具有点像 searchsploit 命令,只是搜索的不是 Exploit Database 而是 PwnWiki 条目
PWSearch PwnWiki 数据库搜索命令行工具。该工具有点像 searchsploit 命令,只是搜索的不是 Exploit Database 而是 PwnWiki 条目。

Privilege escalation with polkit - CVE-2021-3560
Polkit-exploit - CVE-2021-3560 Privilege escalation with polkit - CVE-2021-3560 Summary CVE-2021-3560 is an authentication bypass on polkit, which all
Used to build an XSS platform on the command line.
pyXSSPlatform Used to build an XSS platform on the command line. Usage: 1.generate the cert file You can use openssl like this: openssl req -new -x509
CamOver is a camera exploitation tool that allows to disclosure network camera admin password.
CamOver is a camera exploitation tool that allows to disclosure network camera admin password. Features Exploits vulnerabilities in most popul
✈️ HTML Template engine for python. Supports XSS preventation and many more!
Htmotor HTML Template Engine for Python! Installation: Open your terminal and type pip install htmotor.

Receive notifications/alerts on the most recent disclosed CVE's.
Receive notifications on the most recent disclosed CVE's.
RCE Exploit for Gitlab 13.9.4
GitLab-Wiki-RCE RCE Exploit for Gitlab 13.9.4 RCE via unsafe inline Kramdown options when rendering certain Wiki pages Allows any user with push acc
CamRaptor is a tool that exploits several vulnerabilities in popular DVR cameras to obtain device credentials.
CamRaptor is a tool that exploits several vulnerabilities in popular DVR cameras to obtain device credentials.

The official implementation of You Only Compress Once: Towards Effective and Elastic BERT Compression via Exploit-Explore Stochastic Nature Gradient.
You Only Compress Once: Towards Effective and Elastic BERT Compression via Exploit-Explore Stochastic Nature Gradient (paper) @misc{zhang2021compress,

cve-2021-21985 exploit
cve-2021-21985 exploit 0x01 漏洞点 分析可见: https://attackerkb.com/topics/X85GKjaVER/cve-2021-21985?referrer=home#rapid7-analysis 0x02 exploit 对beans对象进行重新构
