44 Repositories
Python BF-Hash Libraries
An excellent hash algorithm combining classical sponge structure and RNN.
SHA-RNN Recurrent Neural Network with Chaotic System for Hash Functions Anonymous Authors [摘要] 在这次作业中我们提出了一种新的 Hash Function —— SHA-RNN。其以海绵结构为基础,融合了混
A simple hash system.
PBH-Hash-System A simple hash system. Usage You could use it like this: from pbh import pbh print(pbh("Hey", True)) Output: 2feae2471698cfcdcbd6b98ca

PassAPI is a password generator in hash format and fully developed in Python, with the aim of teaching how to handle and build
simple, elegant and safe Introduction PassAPI is a password generator in hash format and fully developed in Python, with the aim of teaching how to ha

Hashcrack: Hash Bruteforse tool using python
HashCrack Hash Bruteforse tool Usage hashcrack.py -n 6 -c lower -l 5 -a md5 -t 3
Searches a document for hash tags. Support multiple natural languages. Works in various contexts.
ht-getter Searches a document for hash tags. Supports multiple natural languages. Works in various contexts. This package uses a non-regex approach an
md5 hash cracking with python.
Python-Md5-Cracker- md5 hash cracking with python. Original files added First create a file called word.txt then run the wordCreate.py script The task
A simple and secure password-based encryption & decryption algorithm based on hash functions, implemented solely based on python.
pyhcrypt A simple and secure password-based encryption & decryption algorithm based on hash functions, implemented solely based on python. Usage Pytho

Hashpic - Hashpic creates an image from a MD5 or SHA512 hash
Hashpic Hashpic creates an image from the MD5 hash of your input. Since v0.2.0 i
BF-Hash - A Python Tool to decrypt hashes by brute force
BF-Hash Herramienta para descifrar hashes por fuerza bruta Instalación git clone

A module for CME that spiders hashes across the domain with a given hash.
hash_spider A module for CME that spiders hashes across the domain with a given hash. Installation Simply copy hash_spider.py to your CME module folde

Torch-ngp - A pytorch implementation of the hash encoder proposed in instant-ngp
HashGrid Encoder (WIP) A pytorch implementation of the HashGrid Encoder from ins

Semi-hash-based Image Generator
pixel-planet Semi-hash-based Image Generator Utilizable for NFTs Generation Process Input is salted and hashed Colors (background, planet, stars) are
Python package for Near Duplicate Video Detection (Perceptual Video Hashing) - Get a 64-bit comparable hash-value for any video.
The Python package for near duplicate video detection ⭐️ Introduction Videohash is a Python package for detecting near-duplicate videos (Perceptual Vi

Faza - Faza terminal, Faza help to beginners for pen testing
Faza terminal simple tool for pen testers Use small letter only for commands Don't use space after command 'help' for more information Installation gi

Encode and decode text application
Text Encoder and Decoder Encode and decode text in many ways using this application! Encode in: ASCII85 Base85 Base64 Base32 Base16 Url MD5 Hash SHA-1
Python implementation of EIP 1577 content hash
ContentHash for Python Python implementation of EIP 1577 content hash. Description This is a simple package made for encoding and decoding content has

A basic duplicate image detection service using perceptual image hash functions and nearest neighbor search, implemented using faiss, fastapi, and imagehash
Duplicate Image Detection Getting Started Install dependencies pip install -r requirements.txt Run service python main.py Testing Test with pytest How

That Hash will name that hash type! Identify MD5, SHA256 and 300+ other hashes Comes with
Call for translators! We're looking for translators to help translate this spec for everyone! Read this documentation in the following languages 한국어 中
Impacket is a collection of Python classes for working with network protocols.
What is Impacket? Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmat
Sign data using symmetric-key algorithm encryption.
Sign data using symmetric-key algorithm encryption. Validate signed data and identify possible validation errors. Uses sha-(1, 224, 256, 385 and 512)/hmac for signature encryption. Custom hash algorithms are allowed. Useful shortcut functions for signing (and validating) dictionaries and URLs.
This program generate hashes from random salts
Hash Generator This program generate hashes from random salts. How to install Install this program using python 3 and pip: pip install . In the future
Some Python scripts that fx(hash) users might find useful.
fx_hash_utils Some Python scripts that fx(hash) users might find useful. get_images This script downloads all the static images of the tokens generate
Team Hash Brown Science4Cast Submission
Team Hash Brown Science4Cast Submission This code reproduces Team Hash Brown's (@princengoc, @Xieyangxinyu) best submission (ee5a) for the competition
Decrypting winrm traffic using password/ntlm hash
Decrypting winrm traffic using password/ntlm hash

A python tool one can extract the "hash" from a WINDOWS HELLO PIN
WINHELLO2hashcat About With this tool one can extract the "hash" from a WINDOWS HELLO PIN. This hash can be cracked with Hashcat, more precisely with
Get the SHA256 hash of any file with this Python Script
Hashfile-SHA256 A SHA256 hash verifying script, written in python. Report Bug Table of Contents About The Project Built With Getting Started Prerequis
Shazam is a Command Line Application that checks the integrity of the file by comparing it with a given hash.
SHAZAM - Check the file's integrity Shazam is a Command Line Application that checks the integrity of the file by comparing it with a given hash. Crea

Verify file hashes of downloaded files easily in a GUI
HASH-verify Verify file hashes of downloaded files easily in a GUI What it does... This gui based Python3 app calculates 3 types of file hashes and ca

📊 Python Flask game that consolidates data from Nasdaq, allowing the user to practice buying and selling stocks.
Web Trader Web Trader is a trading website that consolidates data from Nasdaq, allowing the user to search up the ticker symbol and price of any stock
This app finds duplicate to near duplicate images by generating a hash value for each image stored with a specialized data structure called VP-Tree which makes searching an image on a dataset of 100Ks almost instantanious
Offline Reverse Image Search Overview This app finds duplicate to near duplicate images by generating a hash value for each image stored with a specia

If you only have hash, you can still operate exchange
PTH Exchange If you only have hash, you can still operate exchange This project module is the same as my other project Exchange_SSRF, This project use
Quick and dirty script to fix MD5 hashes in poetry.lock file
fix-poetry-md5-hash Quick and dirty script to fix MD5 hashes in poetry.lock file. Usage: poetry run fix-poetry-md5-hash
telegram bot that calculates file hash / Dosya toplamı hesaplayan telegram botu
Telegram File Hash Bot FileHashBot: 🇬🇧 Bot that calculates file hashes. 🇹🇷 Dosya toplamları hesaplayan bot. Demo in Telegram: @FileHashBot 🇬🇧 Se
compact and speedy hash cracker for md5, sha1, and sha256 hashes
hash-cracker hash cracker is a multi-functional and compact...hash cracking tool...that supports dictionary attacks against three kinds of hashes: md5
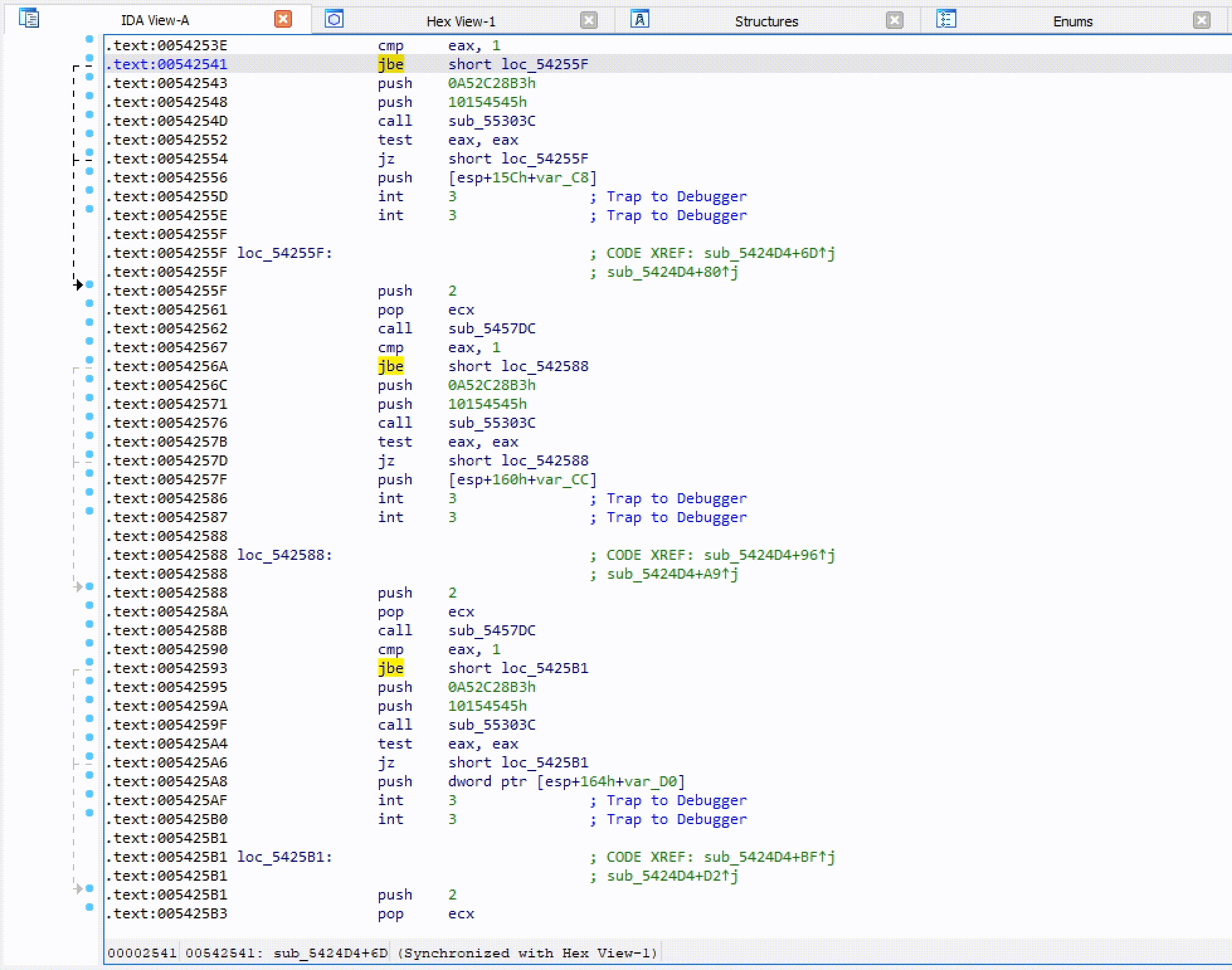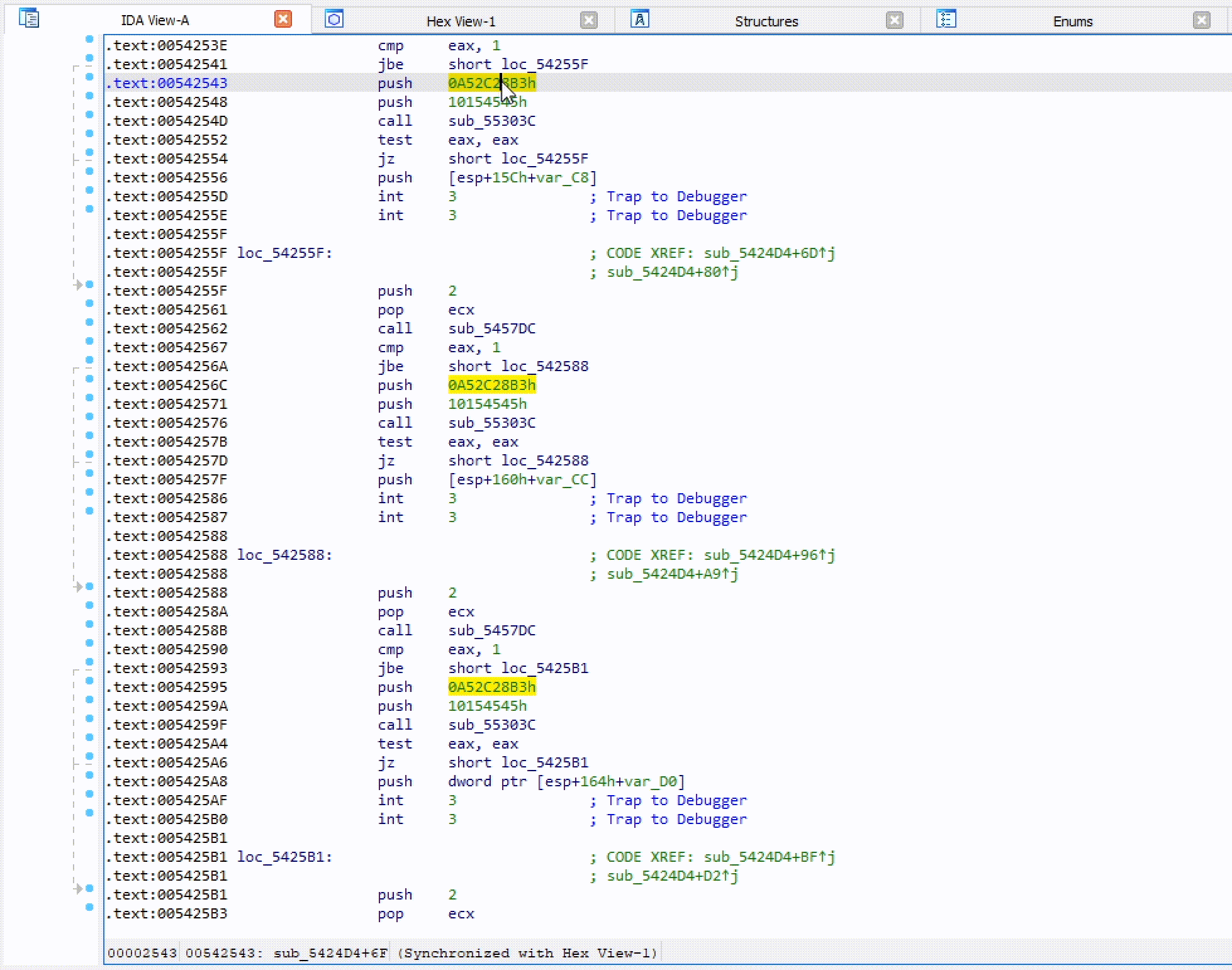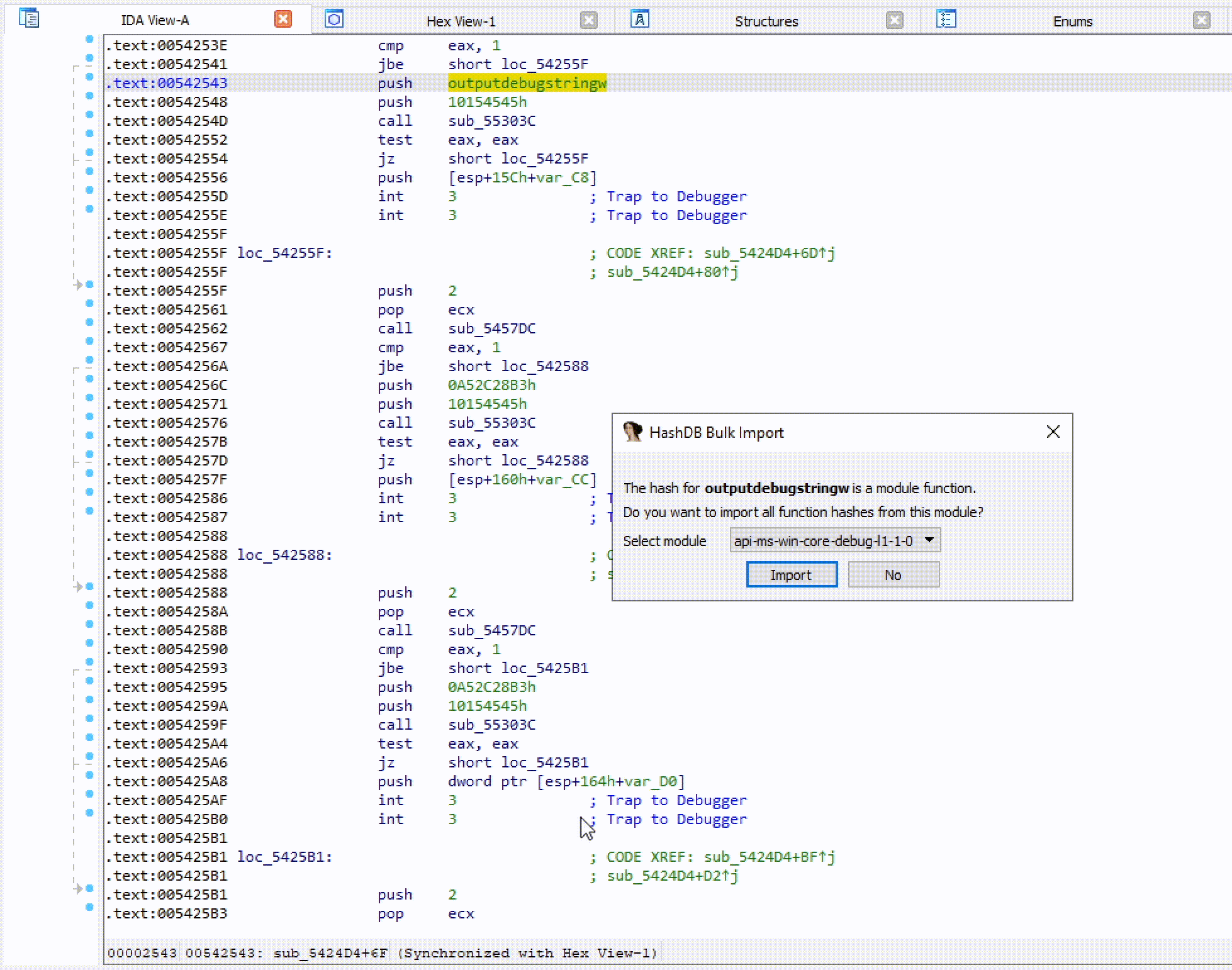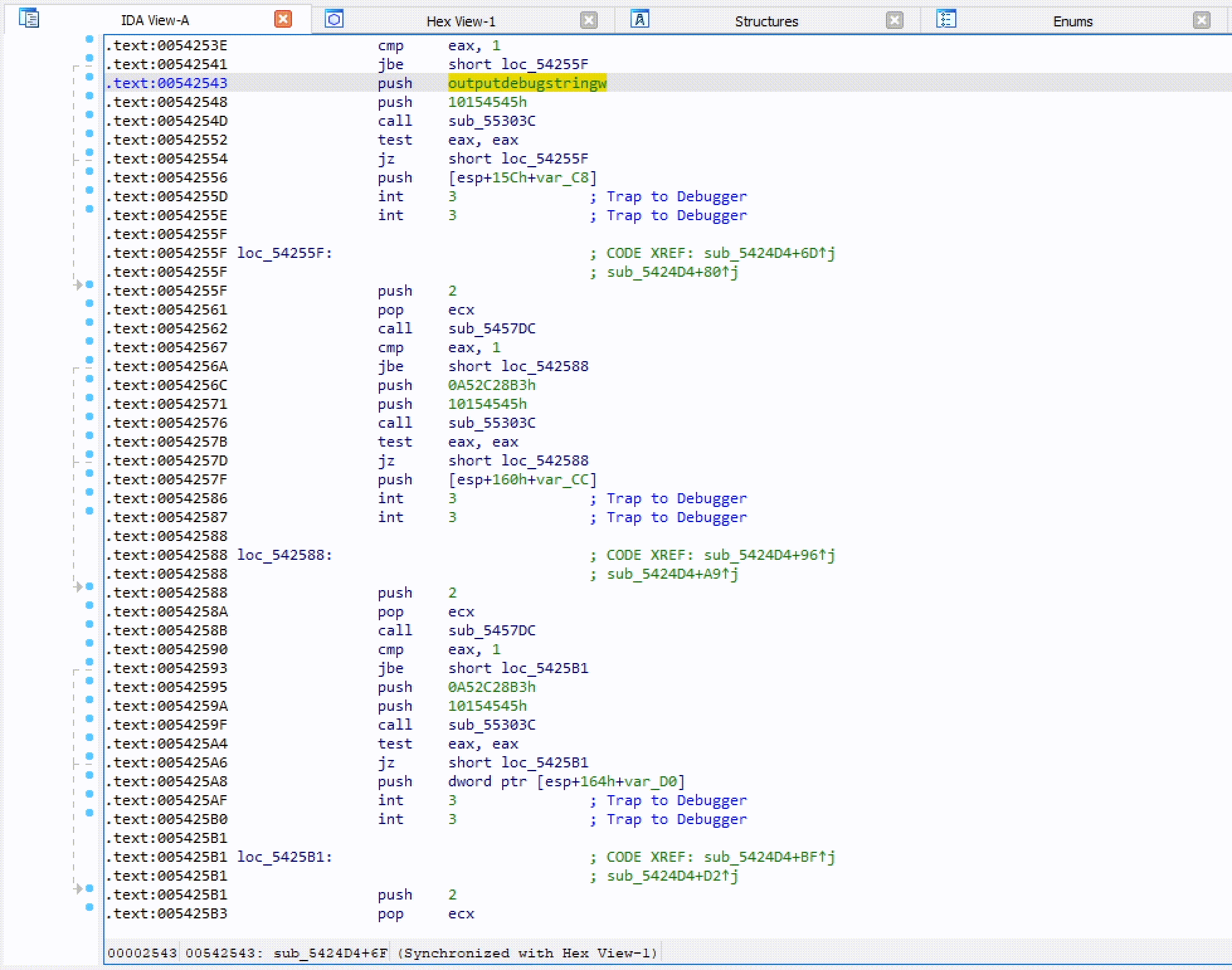
HashDB API hash lookup plugin for IDA Pro
HashDB IDA Plugin Malware string hash lookup plugin for IDA Pro. This plugin connects to the OALABS HashDB Lookup Service. Adding New Hash Algorithms

Hasher Hash, Compare and Verify your files Translations
Hasher Hash, Compare and Verify your files Translations In order to translate Hasher to a language you must add a folder with the language abbreviatio
Kyrie Eleison - The best and unique way to encrypt some data or a file safely
Encrypt your important data and files easily and safely with Kyrie Eleison.

theHasher Tool created for generate strong and unbreakable passwords by using Hash Functions.Generate Hashes and store them in txt files.Use the txt files as lists to execute Brute Force Attacks!
$theHasher theHasher is a Tool for generating hashes using some of the most Famous Hashes Functions ever created. You can save your hashes to correspo

Find target hash collisions for Apple's NeuralHash perceptual hash function.💣
neural-hash-collider Find target hash collisions for Apple's NeuralHash perceptual hash function. For example, starting from a picture of this cat, we

the swiss army knife in the hash field. fast, reliable and easy to use
hexxus Hexxus is a fast hash cracking tool which checks more than 30 thousand passwords in under 4 seconds and can crack the following types bcrypt sh
Craxk is a SINGLE AND NON-REPLICABLE Hash that uses data from the hardware where it is executed to form a hash that can only be reproduced by a single machine.
What is Craxk ? Craxk is a UNIQUE AND NON-REPLICABLE Hash that uses data from the hardware where it is executed to form a hash that can only be reprod

IMGUR5K handwriting set. It is a handwritten in-the-wild dataset, which contains challenging real world handwritten samples from different writers.The dataset is shared as a set of image urls with annotations. This code downloads the images and verifies the hash to the image to avoid data contamination.
IMGUR5K Handwriting Dataset To run the code for downloading the urls and generate corresponding annotations : Usage: python download_imgur5k.py --data
#crypto #cipher #encode #decode #hash
🌹 CYPHER TOOLS 🌹 Written by TMRSWRR Version 1.0.0 All in one tools for CRYPTOLOGY. Instagram: Capture the Root 🖼️ Screenshots 🖼️ 📹 How to use 📹

The Modern Hash Identification System
🔗 Don't know what type of hash it is? Name That Hash will name that hash type! 🤖 Identify MD5, SHA256 and 3000+ other hashes ☄ Comes with a neat web app 🔥