58 Repositories
Python cybersecurity Libraries
Ridogram is an advanced multi-featured Telegram UserBot.
Ridogram Ridogram is an advanced multi-featured Telegram UserBot. String Session Collect String Session by running python3 stringsession.py locally or
Implementation of RITA (Real Intelligence Threat Analytics) in Jupyter Notebook with improved scoring algorithm.
RITA (Real Intelligence Threat Analytics) in Jupyter Notebook RITA is an open source framework for network traffic analysis sponsored by Active Counte

NIVOS is a hacking tool that allows you to scan deeply , crack wifi, see people on your network
NIVOS is a hacking tool that allows you to scan deeply , crack wifi, see people on your network. It applies to all linux operating systems. And it is improving every day, new packages are added. Thank You For Using NIVOS : [NIVOS Created By NIVO Team]
Ridogram is an advanced multi-featured Telegram UserBot.
Ridogram Ridogram is an advanced multi-featured Telegram UserBot. String Session Collect String Session by running python3 stringsession.py locally or

Uses Sharphound, Bloodhound and Neo4j to produce an actionable list of attack paths for targeted remediation.
GoodHound ______ ____ __ __ / ____/___ ____ ____/ / / / /___ __ ______ ____/ / / / __/ __ \/ __ \/ __

A wordlist generator tool, that allows you to supply a set of words, giving you the possibility to craft multiple variations from the given words, creating a unique and ideal wordlist to use regarding a specific target.
A wordlist generator tool, that allows you to supply a set of words, giving you the possibility to craft multiple variations from the given words, creating a unique and ideal wordlist to use regarding a specific target.

Seamless deployment and management of cybersecurity solutions 🏗️
Description 🖼️ Background 👴🏼 Vision 📜 Concepts 💬 Solutions' Lifecycle. Operations ⭕ Functionalities 🚀 Supported Cybersecurity Solutions 📦 Insta

An automated scanning, enumeration, and note taking tool for pentesters
EV1L J3ST3R An automated scanning, enumeration, and note taking tool Created by S1n1st3r Meant to help easily go through Hack The Box machine and TryH

OSINT Cybersecurity Tools
OSINT Cybersecurity Tools Welcome to the World of OSINT: An ongoing collection of awesome tools and frameworks, best security software practices, libr

An curated collection of awesome resources about networking in cybersecurity
An ongoing curated collection of awesome software, libraries, frameworks, talks & videos, best practices, learning tutorials and important practical resources about networking in cybersecurity

⛤Keylogger Generator for Windows written in Python⛤
⛤Keylogger Generator for Windows written in Python⛤
Spy Ad Network - Spy Ad Network Detection With Python
Spy Ad Network Spy Ad Network Detection Jumps from link to link to access a site
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries
A Python Bytecode Disassembler helping reverse engineers in dissecting Python binaries by disassembling and analyzing the compiled python byte-code(.pyc) files across all python versions (including Python 3.10.*)

Cloud-native SIEM for intelligent security analytics for your entire enterprise.
Microsoft Sentinel Welcome to the Microsoft Sentinel repository! This repository contains out of the box detections, exploration queries, hunting quer
Anti Supercookie - Confusing the ISP & Escaping the Supercookie
Confusing the ISP & Escaping the Supercookie
Threat Intel Platform for T-POTs
GreedyBear The project goal is to extract data of the attacks detected by a TPOT or a cluster of them and to generate some feeds that can be used to p
Denial Attacks by Various Methods
Denial Service Attack Denial Attacks by Various Methods IIIIIIIIIIIIIIIIIIII PPPPPPPPPPPPPPPPP VVVVVVVV VVVVVVVV I::

PassLock is a medium-security password manager that encrypts passwords using Advanced Encryption Standards (AES)
A medium security python password manager that encrypt passwords using Advanced Encryption Standard (AES) PassLock is a password manager and password
PcapXray - A Network Forensics Tool - To visualize a Packet Capture offline as a Network Diagram
PcapXray - A Network Forensics Tool - To visualize a Packet Capture offline as a Network Diagram including device identification, highlight important communication and file extraction
A collection of intelligence about Log4Shell and its exploitation activity
Log4Shell-IOCs Members of the Curated Intelligence Trust Group have compiled a list of IOC feeds and threat reports focused on the recent Log4Shell ex
MITMSDR for INDIAN ARMY cybersecurity hackthon
There mainly three things here: MITMSDR spectrum Manual reverse shell MITMSDR Installation Clone the project and run the setup file: ./setup One of th

A curated list of resources dedicated to reinforcement learning applied to cyber security.
Awesome Reinforcement Learning for Cyber Security A curated list of resources dedicated to reinforcement learning applied to cyber security. Note that
Robot Hacking Manual (RHM). From robotics to cybersecurity. Papers, notes and writeups from a journey into robot cybersecurity.
RHM: Robot Hacking Manual Download in PDF RHM v0.4 ┃ Read online The Robot Hacking Manual (RHM) is an introductory series about cybersecurity for robo
Anonymous Dark Web Tool
Anonymous Dark Web Tool v1.0 Features Anonymous Mode Darkweb Search Engines Check Onion Url/s Scanning Host/IP Keep eyes on v2.0 soon. Requirement Deb
Search ports in multiples hosts
Search Port ✨ Multiples Searchs ✨ Create list hosts Create list targets Start Require Python 3.10.0+. python main.py Struture Function Directory load_
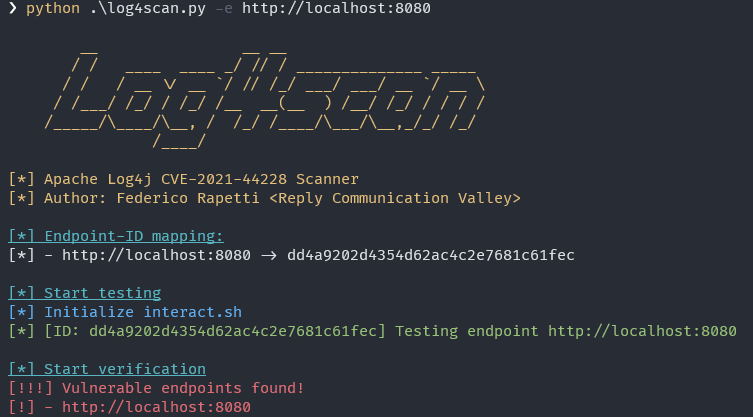
A simple automatic tool for finding vulnerable log4j hosts
Log4Scan A simple automatic tool for finding vulnerable log4j hosts Installation pip3 install -r requirements.txt Usage usage: log4scan.py [-h] (-f FI

A way to analyse how malware and/or goodware samples vary from each other using Shannon Entropy, Hausdorff Distance and Jaro-Winkler Distance
A way to analyse how malware and/or goodware samples vary from each other using Shannon Entropy, Hausdorff Distance and Jaro-Winkler Distance
NotesToCommands - a fully customizable notes / command template program, allowing users to instantly execute terminal commands
NotesToCommands is a fully customizable notes / command template program, allowing users to instantly execute terminal commands with dynamic arguments grouped into sections in their notes/files. It was originally created for pentesting uses, to avoid the needed remembrance and retyping of sets of commands for various attacks.

Fast subdomain scanner, Takes arguments from a Json file ("args.json") and outputs the subdomains.
Fast subdomain scanner, Takes arguments from a Json file ("args.json") and outputs the subdomains. File Structure core/ colors.py db/ wordlist.txt REA

🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.
🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.

A Python Tool to encrypt all types of files using AES and XOR Algorithm.
DataShield This project intends to protect user’s data, it stores files in encrypted format in device provided the passcode and path of the file. AES
Uma ferramenta de segurança da informação escrita em python3,capaz de dar acesso total ao computador de alguém!
shell-reverse Uma ferramenta de segurança da informação escrita em python3, capaz de dar acesso total ao computador de alguém! A cybersecurity tool wr
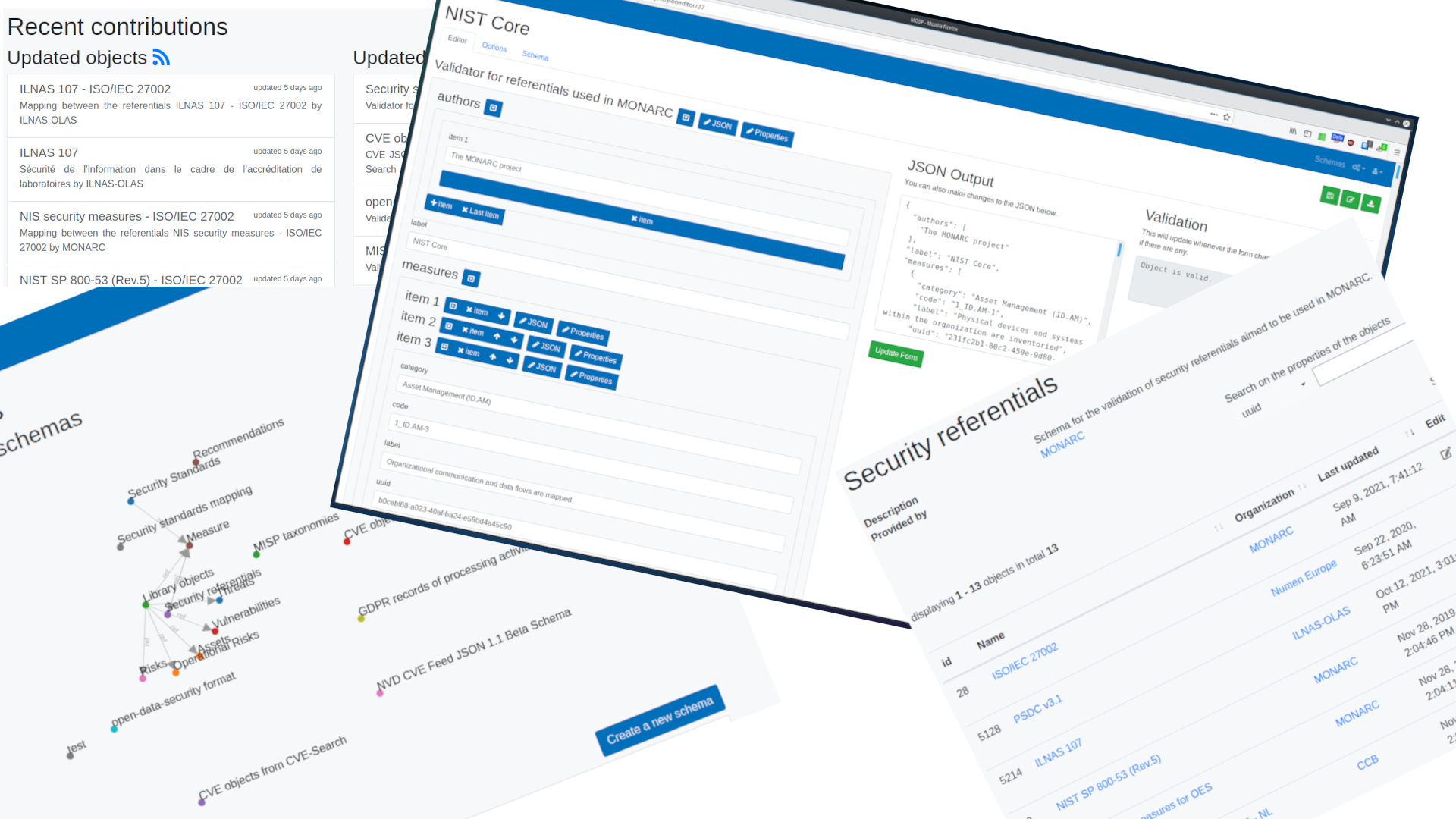
MOSP is a platform for creating, editing and sharing validated JSON objects of any type.
MONARC Objects Sharing Platform Presentation MOSP is a platform for creating, editing and sharing validated JSON objects of any type. You can use any

Passhunt is a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords.
Passhunt is a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords.

Aim of the project is to reduce phishing victims. 😇
Sites: For more details visit our Blog. How to use 😀 : You just have to paste the url in the ENTER THE SUSPECTED URL section and SELECT THE RESEMBELI

ThePhish: an automated phishing email analysis tool
ThePhish ThePhish is an automated phishing email analysis tool based on TheHive, Cortex and MISP. It is a web application written in Python 3 and base

KeyKatcher is a keylogger that records keystrokes made on a computer and sends to the E-Mail.
What is a keylogger? A keylogger is a software application or piece of hardware that monitors and records keystrokes made on a computer keyboard. The
Open Source Tool - Cybersecurity Graph Database in Neo4j
GraphKer Open Source Tool - Cybersecurity Graph Database in Neo4j |G|r|a|p|h|K|e|r| { open source tool for a cybersecurity graph database in neo4j } W

Python based tool to extract forensic info from EventTranscript.db (Windows Diagnostic Data)
EventTranscriptParser EventTranscriptParser is python based tool to extract forensically useful details from EventTranscript.db (Windows Diagnostic Da

Goblyn is a Python tool focused to enumeration and capture of website files metadata.
Goblyn Metadata Enumeration What's Goblyn? Goblyn is a tool focused to enumeration and capture of website files metadata. How it works? Goblyn will se
AIL LeakFeeder: A Module for AIL Framework that automate the process to feed leaked files automatically to AIL
AIL LeakFeeder: A Module for AIL Framework that automates the process to feed leaked files automatically to AIL, So basically this feeder will help you ingest AIL with your leaked files automatically.
Access hacksec.in from your command-line
Access hacksec.in from your command-line

Phomber is infomation grathering tool that reverse search phone numbers and get their details, written in python3.
A Infomation Grathering tool that reverse search phone numbers and get their details ! What is phomber? Phomber is one of the best tools available fo
The official command-line client for spyse.com
Spyse CLI The official command-line client for spyse.com. NOTE: This tool is currently in the early stage beta and shouldn't be used in production. Yo
The official wrapper for spyse.com API, written in Python, aimed to help developers build their integrations with Spyse.
Python wrapper for Spyse API The official wrapper for spyse.com API, written in Python, aimed to help developers build their integrations with Spyse.
A curated list of amazingly awesome Cybersecurity datasets
A curated list of amazingly awesome Cybersecurity datasets

Visius Heimdall is a tool that checks for risks on your cloud infrastructure
Heimdall Cloud Checker 🇧🇷 About Visius is a Brazilian cybersecurity startup that follows the signs of the crimson thunder ;) 🎸 ! As we value open s

Omega - From Wordpress admin to pty
The Linux tool to automate the process of getting a pty once you got admin credentials in a Wordpress site. Keep in mind that right now Omega only can attack Linux hosts.
[CVPR 2021] Pytorch implementation of Hijack-GAN: Unintended-Use of Pretrained, Black-Box GANs
Hijack-GAN: Unintended-Use of Pretrained, Black-Box GANs In this work, we propose a framework HijackGAN, which enables non-linear latent space travers
Incident Response Process and Playbooks | Goal: Playbooks to be Mapped to MITRE Attack Techniques
PURPOSE OF PROJECT That this project will be created by the SOC/Incident Response Community Develop a Catalog of Incident Response Playbook for every

🐸 Identify anything. pyWhat easily lets you identify emails, IP addresses, and more. Feed it a .pcap file or some text and it'll tell you what it is! 🧙♀️
🐸 Identify anything. pyWhat easily lets you identify emails, IP addresses, and more. Feed it a .pcap file or some text and it'll tell you what it is! 🧙♀️

This little tool is to calculate a MurmurHash value of a favicon to hunt phishing websites on the Shodan platform.
MurMurHash This little tool is to calculate a MurmurHash value of a favicon to hunt phishing websites on the Shodan platform. What is MurMurHash? Murm
NExfil is an OSINT tool written in python for finding profiles by username.
NExfil is an OSINT tool written in python for finding profiles by username. The provided usernames are checked on over 350 websites within few seconds.

Domain Connectivity Analysis Tools to analyze aggregate connectivity patterns across a set of domains during security investigations
DomainCAT (Domain Connectivity Analysis Tool) Domain Connectivity Analysis Tool is used to analyze aggregate connectivity patterns across a set of dom

GNU Radio – the Free and Open Software Radio Ecosystem
GNU Radio is a free & open-source software development toolkit that provides signal processing blocks to implement software radios. It can be used wit

RAT-el is an open source penetration test tool that allows you to take control of a windows machine.
To prevent RATel from being detected by antivirus, please do not upload the payload to TOTAL VIRUS. Each month I will test myself if the payload gets detected by antivirus. So you’ll have a photo every month to prove RAtel’s discretion.
tg-nearby Trilateration of nearby Telegram users as described in my corresponding article.
tg-nearby Trilateration of nearby Telegram users as described in my corresponding article. Setup If you want to toy with the code in this repository

A collection of over 5.1 million sub-domains and assets belonging to public bug bounty programs, compiled into a repo, for performing bulk operations.
📂 Public Bug Bounty Targets Data By BugBountyResources A collection of over 5.1M sub-domains and assets belonging to bug bounty targets, all put in a