This PR was automatically created by Snyk using the credentials of a real user.
Snyk has created this PR to fix one or more vulnerable packages in the `pip` dependencies of this project.
Changes included in this PR
- Changes to the following files to upgrade the vulnerable dependencies to a fixed version:
⚠️ Warning
tensorboard 2.1.0 requires protobuf, which is not installed.
tensorboard 2.1.0 requires grpcio, which is not installed.
tensorboard 2.1.0 has requirement setuptools>=41.0.0, but you have setuptools 39.0.1.
google-auth 1.35.0 has requirement setuptools>=40.3.0, but you have setuptools 39.0.1.
Vulnerabilities that will be fixed
By pinning:
Severity | Priority Score (*) | Issue | Upgrade | Breaking Change | Exploit Maturity
:-------------------------:|-------------------------|:-------------------------|:-------------------------|:-------------------------|:-------------------------
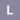 | 441/1000
| 441/1000
Why? Recently disclosed, Has a fix available, CVSS 3.1 | Regular Expression Denial of Service (ReDoS)
SNYK-PYTHON-SETUPTOOLS-3113904 | setuptools:
39.0.1 -> 65.5.1
| No | No Known Exploit
(*) Note that the real score may have changed since the PR was raised.
Some vulnerabilities couldn't be fully fixed and so Snyk will still find them when the project is tested again. This may be because the vulnerability existed within more than one direct dependency, but not all of the affected dependencies could be upgraded.
Check the changes in this PR to ensure they won't cause issues with your project.
Note: You are seeing this because you or someone else with access to this repository has authorized Snyk to open fix PRs.
For more information:  🧐 View latest project report
🧐 View latest project report
🛠 Adjust project settings
📚 Read more about Snyk's upgrade and patch logic
Learn how to fix vulnerabilities with free interactive lessons:
🦉 Regular Expression Denial of Service (ReDoS)