505 Repositories
Python CVE-2020-14871-Exploit Libraries

Spring4Shell Proof Of Concept/And vulnerable application CVE-2022-22965
Spring4Shell-POC (CVE-2022-22965) Spring4Shell (CVE-2022-22965) Proof Of Concept/Information + A vulnerable Tomcat server with a vulnerable spring4she

Dockerized Spring4Shell (CVE-2022-22965) PoC application and exploit
Spring4Shell PoC Application This is a dockerized application that is vulnerable to the Spring4Shell vulnerability (CVE-2022-22965). Full Java source
Everything I needed to understand what was going on with "Spring4Shell" - translated source materials, exploit, links to demo apps, and more.
springcore-0day-en These are all my notes from the alleged confirmed! 0day dropped on 2022-03-29. This vulnerability is commonly referred to as "Sprin
CVE-2022-22963 PoC
CVE-2022-22963 CVE-2022-22963 PoC Slight modified for English translation and detection of https://github.com/chaosec2021/Spring-cloud-function-SpEL-R

Spring4Shell - Spring Core RCE - CVE-2022-22965
Spring Core RCE - CVE-2022-22965 After Spring Cloud, on March 29, another heavyweight vulnerability of Spring broke out on the Internet: Spring Core R
A Safer PoC for CVE-2022-22965 (Spring4Shell)
Safer_PoC_CVE-2022-22965 A Safer PoC for CVE-2022-22965 (Spring4Shell) Functionality Creates a file called CVE_2022-22965_exploited.txt in the tomcat
Exploit and Check Script for CVE 2022-1388
F5-CVE-2022-1388-Exploit Exploit and Check Script for CVE 2022-1388 Usage Check against single host python3 CVE-2022-1388.py -v true -u target_url At

😭 WSOB is a python tool created to exploit the new vulnerability on WSO2 assigned as CVE-2022-29464.
😭 WSOB (CVE-2022-29464) 😭 WSOB is a python tool created to exploit the new vulnerability on WSO2 assigned as CVE-2022-29464. CVE-2022-29464 details:
POC for CVE-2022-1388
CVE-2022-1388 POC for CVE-2022-1388 affecting multiple F5 products. Follow the Horizon3.ai Attack Team on Twitter for the latest security research: Ho

CVE-2022-1388 F5 BIG-IP iControl REST Auth Bypass RCE
CVE-2022-1388 CVE-2022-1388 F5 BIG-IP iControl REST Auth Bypass RCE. POST /mgmt/tm/util/bash HTTP/1.1 Host: Accept-Encoding: gzip, deflate Accept: */
HTTP Protocol Stack Remote Code Execution Vulnerability CVE-2022-21907
CVE-2022-21907 Description POC for CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability. create by antx at 2022-01-17. Detail HTTP

Red Team Toolkit is an Open-Source Django Offensive Web-App which is keeping the useful offensive tools used in the red-teaming together.
RedTeam Toolkit Note: Only legal activities should be conducted with this project. Red Team Toolkit is an Open-Source Django Offensive Web-App contain

CVE-2022-22965 : about spring core rce
CVE-2022-22965: Spring-Core-Rce EXP 特性: 漏洞探测(不写入 webshell,简单字符串输出) 自定义写入 webshell 文件名称及路径 不会追加写入到同一文件中,每次检测写入到不同名称 webshell 文件 支持写入 冰蝎 webshell 代理支持,可
CVE-2022-22965 - CVE-2010-1622 redux
CVE-2022-22965 - vulnerable app and PoC Trial & error $ docker rm -f rce; docker build -t rce:latest . && docker run -d -p 8080:8080 --name rce rce:la

S2-062 (CVE-2021-31805) / S2-061 / S2-059 RCE
CVE-2021-31805 Remote code execution S2-062 (CVE-2021-31805) Due to Apache Struts2's incomplete fix for S2-061 (CVE-2020-17530), some tag attributes c
Laravel RCE (CVE-2021-3129)
CVE-2021-3129 - Laravel RCE About The script has been made for exploiting the Laravel RCE (CVE-2021-3129) vulnerability. This script allows you to wri
Discord Region Swapping Exploit (VC Overload)
Discord-VC-Exploit Discord Region Swapping Exploit (VC Overload) aka VC Crasher How does this work? Discord has multiple servers that lets people arou

Spring-0day/CVE-2022-22965
CVE-2022-22965 Spring Framework/CVE-2022-22965 Vulnerability ID: CVE-2022-22965/CNVD-2022-23942/QVD-2022-1691 Reproduce the vulnerability docker pull

spring-cloud-gateway-rce CVE-2022-22947
Spring Cloud Gateway Actuator API SpEL表达式注入命令执行(CVE-2022-22947) 1.installation pip3 install -r requirements.txt 2.Usage $ python3 spring-cloud-gateway
Spring Cloud Gateway 3.0.7 & 3.1.1 Code Injection (RCE)
Spring Cloud Gateway 3.0.7 & 3.1.1 Code Injection (RCE) CVE: CVE-2022-22947 CVSS: 10.0 (Vmware - https://tanzu.vmware.com/security/cve-2022-22947)
PyTorch implementation of SCAFFOLD (Stochastic Controlled Averaging for Federated Learning, ICML 2020).
Scaffold-Federated-Learning PyTorch implementation of SCAFFOLD (Stochastic Controlled Averaging for Federated Learning, ICML 2020). Environment numpy=

Cve-2022-23131 - Cve-2022-23131 zabbix-saml-bypass-exp
cve-2022-23131 cve-2022-23131 zabbix-saml-bypass-exp replace [zbx_signed_session
CVE-2022-22536 - SAP memory pipes(MPI) desynchronization vulnerability CVE-2022-22536
CVE-2022-22536 SAP memory pipes desynchronization vulnerability(MPI) CVE-2022-22

CVE-2022-23046 - SQL Injection Vulnerability on PhpIPAM v1.4.4
CVE-2022-23046 PhpIPAM v1.4.4 allows an authenticated admin user to inject SQL s
pwncat module that automatically exploits CVE-2021-4034 (pwnkit)
pwncat_pwnkit Introduction The purpose of this module is to attempt to exploit CVE-2021-4034 (pwnkit) on a target when using pwncat. There is no need
A Python script that can be used to check if a SAP system is affected by CVE-2022-22536
Vulnerability assessment for CVE-2022-22536 This repository contains a Python script that can be used to check if a SAP system is affected by CVE-2022

Pytorch Implementation of "Desigining Network Design Spaces", Radosavovic et al. CVPR 2020.
RegNet Pytorch Implementation of "Desigining Network Design Spaces", Radosavovic et al. CVPR 2020. Paper | Official Implementation RegNet offer a very
A Bayesian cognition approach for belief updating of correlation judgement through uncertainty visualizations
Overview Code and supplemental materials for Karduni et al., 2020 IEEE Vis. "A Bayesian cognition approach for belief updating of correlation judgemen
AnonStress-Stored-XSS-Exploit - An exploit and demonstration on how to exploit a Stored XSS vulnerability in anonstress
AnonStress Stored XSS Exploit An exploit and demonstration on how to exploit a S

PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1
CVE-2021-45897 PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1 This vulnerability was repor
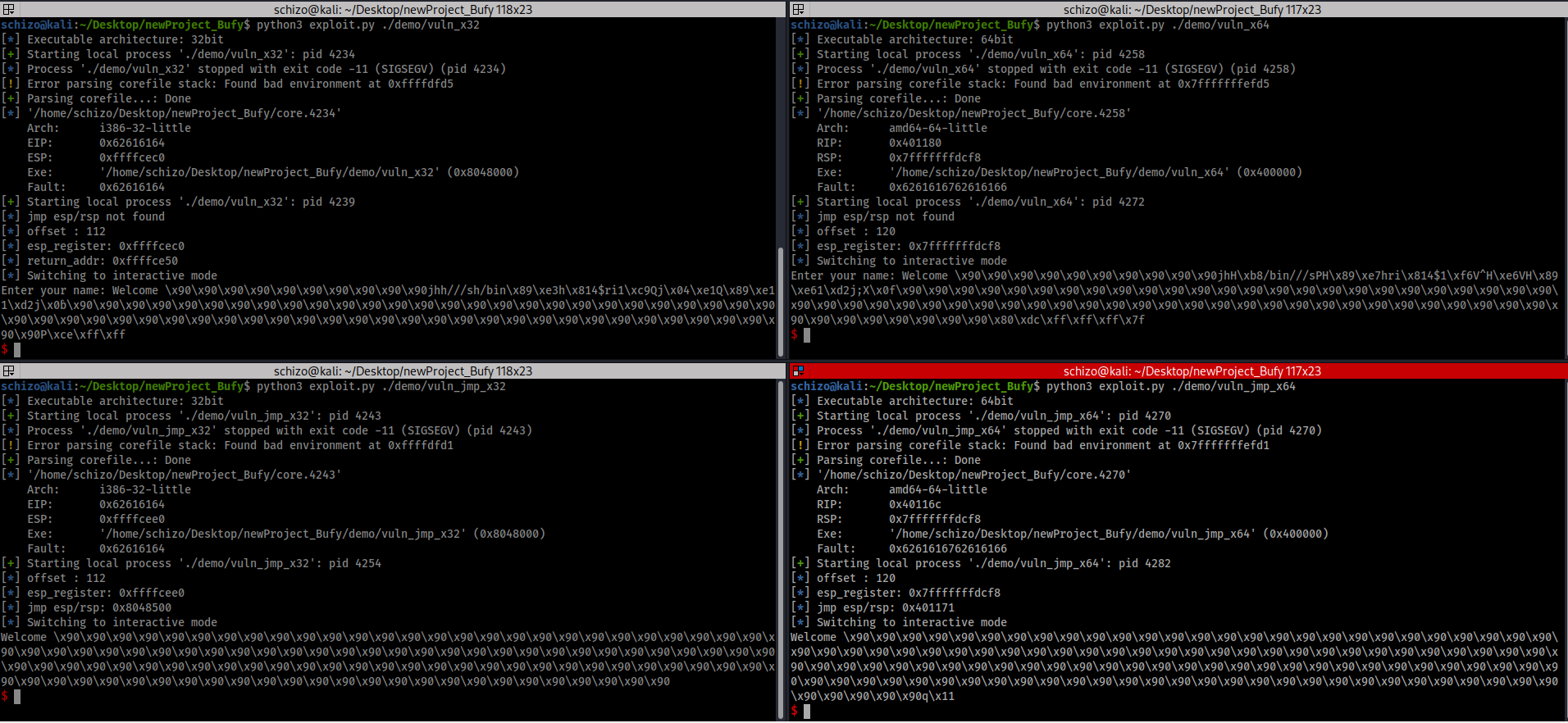
Automated tool to exploit basic buffer overflow remotely and locally & x32 and x64
Automated tool to exploit basic buffer overflow (remotely or locally) & (x32 or x64)
PortSwigger Burp Plugin for the Log4j (CVE-2021-44228)
yLog4j This is Y-Sec's @PortSwigger Burp Plugin for the Log4j CVE-2021-44228 vulnerability. The focus of yLog4j is to support mass-scanning of the Log
![[ECE NTUA] 👁 Computer Vision - Lab Projects & Theoretical Problem Sets (2020-2021)](https://github.com/d-dimos/computer_vision_ntua/raw/master/labs/lab1/README_imgs/edge_in.jpg?raw=true)
[ECE NTUA] 👁 Computer Vision - Lab Projects & Theoretical Problem Sets (2020-2021)
Computer Vision - NTUA (2020-2021) This repository hosts the lab projects and theoretical problem sets of the Computer Vision course held by ECE NTUA
Retrieval.pytorch - The code we used in [2020 DIGIX]
Retrieval.pytorch - The code we used in [2020 DIGIX]
TightVNC Vulnerability.
CVE-2022-23967 In TightVNC 1.3.10, there is an integer signedness error and resultant heap-based buffer overflow in InitialiseRFBConnection in rfbprot

This is a simple PoC for the newly found Polkit error names PwnKit
A Python3 and a BASH PoC for CVE-2021-4034 by Kim Schulz
Python exploit code for CVE-2021-4034 (pwnkit)
Python3 code to exploit CVE-2021-4034 (PWNKIT). This was an exercise in "can I make this work in Python?", and not meant as a robust exploit. It Works
CVE-2022-21907 Vulnerability PoC
CVE-2022-21907 Description POC for CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability. create by antx at 2022-01-17, just some sm
(ICONIP 2020) MobileHand: Real-time 3D Hand Shape and Pose Estimation from Color Image
MobileHand: Real-time 3D Hand Shape and Pose Estimation from Color Image This repo contains the source code for MobileHand, real-time estimation of 3D
This repository detects a system vulnerable to CVE-2022-21907 and protects against this vulnerability if desired
This repository detects a system vulnerable to CVE-2022-21907 and protects against this vulnerability if desired
To model the probability of a soccer coach leave his/her team during Campeonato Brasileiro for 10 chosen teams and considering years 2018, 2019 and 2020.
To model the probability of a soccer coach leave his/her team during Campeonato Brasileiro for 10 chosen teams and considering years 2018, 2019 and 2020.

Proof of concept of CVE-2022-21907 Double Free in http.sys driver, triggering a kernel crash on IIS servers
CVE-2022-21907 - Double Free in http.sys driver Summary An unauthenticated attacker can send an HTTP request with an "Accept-Encoding" HTTP request he
Custom IMDB Dataset is extracted between 2020-2021 and custom distilBERT model is trained for movie success probability prediction
IMDB Success Predictor Project involves Web Scraping custom IMDB data between 2020 and 2021 of 10000 movies and shows sorted by number of votes ,fine
CVE-2022-21907 - Windows HTTP协议栈远程代码执行漏洞 CVE-2022-21907
CVE-2022-21907 Description POC for CVE-2022-21907: Windows HTTP协议栈远程代码执行漏洞 creat

Official PyTorch implementation of Time-aware Large Kernel (TaLK) Convolutions (ICML 2020)
Time-aware Large Kernel (TaLK) Convolutions (Lioutas et al., 2020) This repository contains the source code, pre-trained models, as well as instructio
![[NeurIPS 2020] Official Implementation:](https://github.com/giannisdaras/smyrf/raw/master/visuals/quality_degradation.png)
[NeurIPS 2020] Official Implementation: "SMYRF: Efficient Attention using Asymmetric Clustering".
SMYRF: Efficient attention using asymmetric clustering Get started: Abstract We propose a novel type of balanced clustering algorithm to approximate a
Code and data (Incidents Dataset) for ECCV 2020 Paper "Detecting natural disasters, damage, and incidents in the wild".
Incidents Dataset See the following pages for more details: Project page: IncidentsDataset.csail.mit.edu. ECCV 2020 Paper "Detecting natural disasters
Source codes for Improved Few-Shot Visual Classification (CVPR 2020), Enhancing Few-Shot Image Classification with Unlabelled Examples
Source codes for Improved Few-Shot Visual Classification (CVPR 2020), Enhancing Few-Shot Image Classification with Unlabelled Examples (WACV 2022) and Beyond Simple Meta-Learning: Multi-Purpose Models for Multi-Domain, Active and Continual Few-Shot Learning (TPAMI 2022 - in submission)
![[PAMI 2020] Show, Match and Segment: Joint Weakly Supervised Learning of Semantic Matching and Object Co-segmentation](https://github.com/YunChunChen/MaCoSNet-pytorch/raw/master/img/teaser.png)
[PAMI 2020] Show, Match and Segment: Joint Weakly Supervised Learning of Semantic Matching and Object Co-segmentation
Show, Match and Segment: Joint Weakly Supervised Learning of Semantic Matching and Object Co-segmentation This repository contains the source code for
POC of CVE-2021-26084, which is Atlassian Confluence Server OGNL Pre-Auth RCE Injection Vulneralibity.
CVE-2021-26084 Description POC of CVE-2021-26084, which is Atlassian Confluence Server OGNL(Object-Graph Navigation Language) Pre-Auth RCE Injection V

UDP++ (ECCVW 2020 Oral), (Winner of COCO 2020 Keypoint Challenge).
UDP-Pose This is the pytorch implementation for UDP++, which won the Fisrt place in COCO Keypoint Challenge at ECCV 2020 Workshop. Top-Down Results on

JWT Key Confusion PoC (CVE-2015-9235) Written for the Hack the Box challenge - Under Construction
JWT Key Confusion PoC (CVE-2015-9235) Written for the Hack the Box challenge - Under Construction This script performs a Java Web Token Key Confusion
Unauthenticated Sqlinjection that leads to dump data base but this one impersonated Admin and drops a interactive shell
Unauthenticated Sqlinjection that leads to dump database but this one impersonated Admin and drops a interactive shell
Insights in greek football league 2020-2021 and bookmaker's accuracy
Greek_Football_League_Analysis_2020_2021 Aim of Project: This project aims in deriving useful insights from greek football league 2020-2021 by mean st
SonicWall SMA-100 Unauth RCE Exploit (CVE-2021-20038)
Bad Blood Bad Blood is an exploit for CVE-2021-20038, a stack-based buffer overflow in the httpd binary of SMA-100 series systems using firmware versi

Automated tool to find & created Exploit Poc for Clickjacking Vulnerability
ClickJackPoc This tool will help you automate finding Clickjacking Vulnerability by just passing a file containing list of Targets . Once the Target i
The dataset of tweets pulling from Twitters with keyword: Hydroxychloroquine, location: US, Time: 2020
HCQ_Tweet_Dataset: FREE to Download. Keywords: HCQ, hydroxychloroquine, tweet, twitter, COVID-19 This dataset is associated with the paper "Understand
This package implements the algorithms introduced in Smucler, Sapienza, and Rotnitzky (2020) to compute optimal adjustment sets in causal graphical models.
optimaladj: A library for computing optimal adjustment sets in causal graphical models This package implements the algorithms introduced in Smucler, S
Validate arbitrary image uploads from incoming data urls while preserving file integrity but removing EXIF and unwanted artifacts and RCE exploit potential
Validate arbitrary base64-encoded image uploads as incoming data urls while preserving image integrity but removing EXIF and unwanted artifacts and mitigating RCE-exploit potential.
Exploiting CVE-2021-44228 in VMWare Horizon for remote code execution and more.
Log4jHorizon Exploiting CVE-2021-44228 in VMWare Horizon for remote code execution and more. BLOG COMING SOON Code and README.md this time around are
[CVPR 2020] 3D Photography using Context-aware Layered Depth Inpainting
[CVPR 2020] 3D Photography using Context-aware Layered Depth Inpainting [Paper] [Project Website] [Google Colab] We propose a method for converting a

A Physics-based Noise Formation Model for Extreme Low-light Raw Denoising (CVPR 2020 Oral & TPAMI 2021)
ELD The implementation of CVPR 2020 (Oral) paper "A Physics-based Noise Formation Model for Extreme Low-light Raw Denoising" and its journal (TPAMI) v

PyTorch implementation of the REMIND method from our ECCV-2020 paper "REMIND Your Neural Network to Prevent Catastrophic Forgetting"
REMIND Your Neural Network to Prevent Catastrophic Forgetting This is a PyTorch implementation of the REMIND algorithm from our ECCV-2020 paper. An ar

Official Tensorflow implementation of U-GAT-IT: Unsupervised Generative Attentional Networks with Adaptive Layer-Instance Normalization for Image-to-Image Translation (ICLR 2020)
U-GAT-IT — Official TensorFlow Implementation (ICLR 2020) : Unsupervised Generative Attentional Networks with Adaptive Layer-Instance Normalization fo
labsecurity is a tool that brings together python scripts made for ethical hacking, in a single tool, through a console interface
labsecurity labsecurity is a tool that brings together python scripts made for ethical hacking, in a single tool, through a console interface. Warning

CVE-2021-45232-RCE-多线程批量漏洞检测
CVE-2021-45232-RCE CVE-2021-45232-RCE-多线程批量漏洞检测 FOFA 查询 title="Apache APISIX Das

Official Repsoitory for "Mish: A Self Regularized Non-Monotonic Neural Activation Function" [BMVC 2020]
Mish: Self Regularized Non-Monotonic Activation Function BMVC 2020 (Official Paper) Notes: (Click to expand) A considerably faster version based on CU
Details,PoC and patches for CVE-2021-45383 & CVE-2021-45384
CVE-2021-45383 & CVE-2021-45384 There are several network-layer vulnerabilities in the official server of Minecraft: Bedrock Edition (aka Bedrock Serv

NS-Defacer: a auto html injecter, In other words It's a auto defacer to deface a lot of websites in less time
Overview NS-Defacer is a auto html injecter, In other words It's a auto defacer
An interactive python script that enables root access on the T-Mobile (Wingtech) TMOHS1, as well as providing several useful utilites to change the configuration of the device.
TMOHS1 Root Utility Description An interactive python script that enables root access on the T-Mobile (Wingtech) TMOHS1, as well as providing several
The dataset of tweets pulling from Twitters with keyword: Hydroxychloroquine, location: US, Time: 2020
HCQ_Tweet_Dataset: FREE to Download. Keywords: HCQ, hydroxychloroquine, tweet, twitter, COVID-19 This dataset is associated with the paper "Understand
Discord-email-spammer-exploit - A discord email spammer exploit with python
Discord-email-spammer-exploit was made by Love ❌ code ✅ 🎈 ・Description First it

Contrastive unpaired image-to-image translation, faster and lighter training than cyclegan (ECCV 2020, in PyTorch)
Contrastive Unpaired Translation (CUT) video (1m) | video (10m) | website | paper We provide our PyTorch implementation of unpaired image-to-image tra
![[ECCV 2020] XingGAN for Person Image Generation](https://github.com/Ha0Tang/XingGAN/raw/master/imgs/framework.jpg)
[ECCV 2020] XingGAN for Person Image Generation
Contents XingGAN or CrossingGAN Installation Dataset Preparation Generating Images Using Pretrained Model Train and Test New Models Evaluation Acknowl

PyTorch Implementation of ECCV 2020 Spotlight TuiGAN: Learning Versatile Image-to-Image Translation with Two Unpaired Images
TuiGAN-PyTorch Official PyTorch Implementation of "TuiGAN: Learning Versatile Image-to-Image Translation with Two Unpaired Images" (ECCV 2020 Spotligh

Council-GAN - Implementation for our paper Breaking the Cycle - Colleagues are all you need (CVPR 2020)
Council-GAN Implementation of our paper Breaking the Cycle - Colleagues are all you need (CVPR 2020) Paper Ori Nizan , Ayellet Tal, Breaking the Cycle

SMIS - Semantically Multi-modal Image Synthesis(CVPR 2020)
Semantically Multi-modal Image Synthesis Project page / Paper / Demo Semantically Multi-modal Image Synthesis(CVPR2020). Zhen Zhu, Zhiliang Xu, Anshen

SEAN: Image Synthesis with Semantic Region-Adaptive Normalization (CVPR 2020, Oral)
SEAN: Image Synthesis with Semantic Region-Adaptive Normalization (CVPR 2020 Oral) Figure: Face image editing controlled via style images and segmenta

StarGAN v2 - Official PyTorch Implementation (CVPR 2020)
StarGAN v2 - Official PyTorch Implementation StarGAN v2: Diverse Image Synthesis for Multiple Domains Yunjey Choi*, Youngjung Uh*, Jaejun Yoo*, Jung-W
![[CVPR 2020] GAN Compression: Efficient Architectures for Interactive Conditional GANs](https://github.com/mit-han-lab/gan-compression/raw/master/imgs/teaser.png)
[CVPR 2020] GAN Compression: Efficient Architectures for Interactive Conditional GANs
GAN Compression project | paper | videos | slides [NEW!] GAN Compression is accepted by T-PAMI! We released our T-PAMI version in the arXiv v4! [NEW!]

PyTorch code for ICPR 2020 paper Future Urban Scene Generation Through Vehicle Synthesis
Future urban scene generation through vehicle synthesis This repository contains Pytorch code for the ICPR2020 paper "Future Urban Scene Generation Th

Show, Edit and Tell: A Framework for Editing Image Captions, CVPR 2020
Show, Edit and Tell: A Framework for Editing Image Captions | arXiv This contains the source code for Show, Edit and Tell: A Framework for Editing Ima

Code accompanying the paper Say As You Wish: Fine-grained Control of Image Caption Generation with Abstract Scene Graphs (Chen et al., CVPR 2020, Oral).
Say As You Wish: Fine-grained Control of Image Caption Generation with Abstract Scene Graphs This repository contains PyTorch implementation of our pa

Meshed-Memory Transformer for Image Captioning. CVPR 2020
M²: Meshed-Memory Transformer This repository contains the reference code for the paper Meshed-Memory Transformer for Image Captioning (CVPR 2020). Pl
![Implementation of 'X-Linear Attention Networks for Image Captioning' [CVPR 2020]](https://github.com/JDAI-CV/image-captioning/raw/master/images/framework.jpg)
Implementation of 'X-Linear Attention Networks for Image Captioning' [CVPR 2020]
Introduction This repository is for X-Linear Attention Networks for Image Captioning (CVPR 2020). The original paper can be found here. Please cite wi
![[CVPR 2020] Transform and Tell: Entity-Aware News Image Captioning](https://github.com/alasdairtran/transform-and-tell/raw/master/figures/teaser.png)
[CVPR 2020] Transform and Tell: Entity-Aware News Image Captioning
Transform and Tell: Entity-Aware News Image Captioning This repository contains the code to reproduce the results in our CVPR 2020 paper Transform and

CVE-log4j CheckMK plugin
CVE-2021-44228-log4j discovery (Download the MKP package) This plugin discovers vulnerable files for the CVE-2021-44228-log4j issue. To discover this

Tinyman exploit finder - Tinyman exploit finder for python
tinyman_exploit_finder There was a big tinyman exploit. You can read about it he

Snake - Code for "Deep Snake for Real-Time Instance Segmentation" CVPR 2020 oral
Good news! Snake algorithms exhibit state-of-the-art performances on COCO dataset: DANCE Deep Snake for Real-Time Instance Segmentation Deep Snake for

Adabelief-Optimizer - Repository for NeurIPS 2020 Spotlight "AdaBelief Optimizer: Adapting stepsizes by the belief in observed gradients"
AdaBelief Optimizer NeurIPS 2020 Spotlight, trains fast as Adam, generalizes well as SGD, and is stable to train GANs. Release of package We have rele
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging features for exploit developers & reverse engineers ☢
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging features for exploit developers & reverse engineers ☢
Self-supervised Equivariant Attention Mechanism for Weakly Supervised Semantic Segmentation, CVPR 2020 (Oral)
SEAM The implementation of Self-supervised Equivariant Attention Mechanism for Weakly Supervised Semantic Segmentaion. You can also download the repos
[CVPR'2020] DeepDeform: Learning Non-rigid RGB-D Reconstruction with Semi-supervised Data
DeepDeform (CVPR'2020) DeepDeform is an RGB-D video dataset containing over 390,000 RGB-D frames in 400 videos, with 5,533 optical and scene flow imag
Implementation of ICLR 2020 paper "Revisiting Self-Training for Neural Sequence Generation"
Self-Training for Neural Sequence Generation This repo includes instructions for running noisy self-training algorithms from the following paper: Revi

TensorFlow (v2.7.0) benchmark results on an M1 Macbook Air 2020 laptop (macOS Monterey v12.1).
M1-tensorflow-benchmark TensorFlow (v2.7.0) benchmark results on an M1 Macbook Air 2020 laptop (macOS Monterey v12.1). I was initially testing if Tens

GCC: Graph Contrastive Coding for Graph Neural Network Pre-Training @ KDD 2020
GCC: Graph Contrastive Coding for Graph Neural Network Pre-Training Original implementation for paper GCC: Graph Contrastive Coding for Graph Neural N
Unsupervised Attributed Multiplex Network Embedding (AAAI 2020)
Unsupervised Attributed Multiplex Network Embedding (DMGI) Overview Nodes in a multiplex network are connected by multiple types of relations. However
Exploiting CVE-2021-44228 in Unifi Network Application for remote code execution and more
Log4jUnifi Exploiting CVE-2021-44228 in Unifi Network Application for remote cod
Auerswald COMpact 8.0B Backdoors exploit
CVE-2021-40859 Auerswald COMpact 8.0B Backdoors exploit About Backdoors were discovered in Auerswald COMpact 5500R 7.8A and 8.0B devices, that allow a
CVE-2021-43936 is a critical vulnerability (CVSS3 10.0) leading to Remote Code Execution (RCE) in WebHMI Firmware.
CVE-2021-43936 CVE-2021-43936 is a critical vulnerability (CVSS3 10.0) leading to Remote Code Execution (RCE) in WebHMI Firmware. This vulnerability w