551 Repositories
Python aws-security Libraries
Discord-Protect is a simple discord bot allowing you to have some security on your discord server by ordering a captcha to the user who joins your server.
Discord-Protect Discord-Protect is a simple discord bot allowing you to have some security on your discord server by ordering a captcha to the user wh
AWS Enumeration and Footprinting Tool
Quiet Riot 🎶 C'mon, Feel The Noise 🎶 An enumeration tool for scalable, unauthenticated validation of AWS principals; including AWS Acccount IDs, roo
aws ec2.py companion script to generate sshconfigs with auto bastion host discovery
ec2-bastion-sshconfig This script will interate over instances found by ec2.py and if those instances are not publically accessible it will search the
This Lambda will Pull propagated routes from TGW and update VPC route table
AWS-Transitgateway-Route-Propagation This Lambda will Pull propagated routes from TGW and update VPC route table. Tested on python 3.8 Lambda AWS INST

AutoExploitSwagger is an automated API security testing exploit tool that can be combined with xray, BurpSuite and other scanners.
AutoExploitSwagger is an automated API security testing exploit tool that can be combined with xray, BurpSuite and other scanners.
Demo to explain how to use AWS Chalice to connect to twitter API and change profile picture at scheduled times.
chalice-twitter-demo Demo to explain how to use AWS Chalice to connect to twitter API and change profile picture at scheduled times. Video Demo Click

Security tool to test different bypass of forbidden
notForbidden Security tool to test different bypass of forbidden Usage python3 notForbidden.py URL Features Bypass with different methods (POST, OPT
Building and deploying AWS Lambda Shared Layers
AWS Lambda Shared Layers This repository is hosting the code from the following blog post: AWS Lambda & Shared layers for Python. The goal of this rep
Dumps to CSV all the resources in an organization's member accounts
AWS Org Inventory Dumps to CSV all the resources in an organization's member accounts. Set your environment's AWS_PROFILE and AWS_DEFAULT_REGION varia
AWS Workmail Migration Tool
WMigrate A tool for migrating AWS Workmail Users and Groups cross region and cross accounts. It also creates user and group aliases and adds the users

The Research PACS on AWS solution facilitates researchers' access medical images stored in the clinical PACS in a secure and seamless manner
Research PACS on AWS Challenge to solve Solution presentation Deploy the solution Further reading Releases License Challenge to solve The rise of new

Django e-commerce website with Advanced Features and SEO Friendly
MyTech® - Your Technology Django e-commerce website with Advanced Features and SEO Friendly Images and Prices are only used for Demo purpose and does
Set the draft security HTTP header Permissions-Policy (previously Feature-Policy) on your Django app.
django-permissions-policy Set the draft security HTTP header Permissions-Policy (previously Feature-Policy) on your Django app. Requirements Python 3.
AWS provides a Python SDK, "Boto3" ,which can be used to access the AWS-account from the local.
Boto3 - The AWS SDK for Python Boto3 is the Amazon Web Services (AWS) Software Development Kit (SDK) for Python, which allows Python developers to wri
Enrich IP addresses with metadata and security IoC
Stratosphere IP enrich Get an IP address and enrich it with metadata and IoC You need API keys for VirusTotal and PassiveTotal (RiskIQ) How to use fro
Unit testing AWS interactions with pytest and moto. These examples demonstrate how to structure, setup, teardown, mock, and conduct unit testing. The source code is only intended to demonstrate unit testing.
Unit Testing Interactions with Amazon Web Services (AWS) Unit testing AWS interactions with pytest and moto. These examples demonstrate how to structu
BinCat is an innovative login system, with which the account you register will be more secure.
BinCat is an innovative login system, with which the account you register will be more secure. This project is inspired by a conventional token system.
External Network Pentest Automation using Shodan API and other tools.
Chopin External Network Pentest Automation using Shodan API and other tools. Workflow Input a file containing CIDR ranges. Converts CIDR ranges to ind
D(HE)ater is a security tool can perform DoS attack by enforcing the DHE key exchange.
D(HE)ater D(HE)ater is an attacking tool based on CPU heating in that it forces the ephemeral variant of Diffie-Hellman key exchange (DHE) in given cr

The ibet-Prime security token management system for ibet network.
ibet-Prime The ibet-Prime security token management system for ibet network. Features ibet-Prime is an API service that enables the issuance and manag

Nixtla is an open-source time series forecasting library.
Nixtla Nixtla is an open-source time series forecasting library. We are helping data scientists and developers to have access to open source state-of-
Security offerings for AWS Control Tower
Caylent Security Catalyst Reference Architecture Examples This repository contains solutions for Caylent's Security Catalyst. The Security Catalyst is
AWS SQS event redrive Lambda
This repository contains the Lambda function to redrive sqs events from source to destination queue while controlling maxRetry per event.
AWS SQS event redrive Lambda With Python
AWS SQS event redrive Lambda This repository contains one simple AWS Lambda function in Python to redrive AWS SQS events from source queue to destinat

POC de uma AWS lambda que executa a consulta de preços de criptomoedas, e é implantada na AWS usando Github actions.
Cryptocurrency Prices Overview Instalação Repositório Configuração CI/CD Roadmap Testes Overview A ideia deste projeto é aplicar o conteúdo estudado s
A CLI tool to disable and enable security standards controls in AWS Security Hub
Security Hub Controls CLI A CLI tool to disable and enable security standards controls in AWS Security Hub. It is designed to work together with AWS S
Audio Steganography is a technique used to transmit hidden information by modifying an audio signal in an imperceptible manner.
Audio Steganography Audio Steganography is a technique used to transmit hidden information by modifying an audio signal in an imperceptible manner. Ab
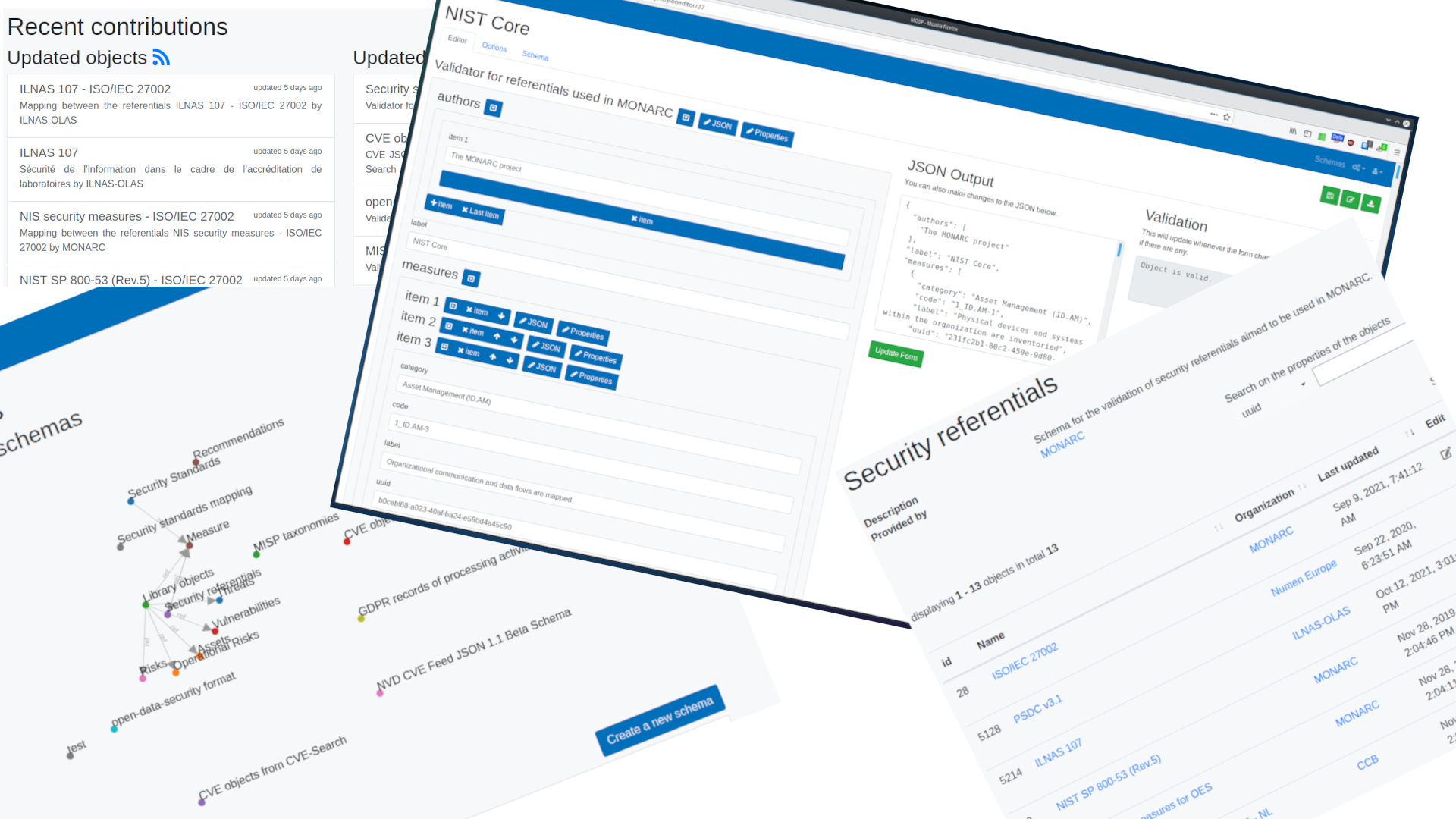
MOSP is a platform for creating, editing and sharing validated JSON objects of any type.
MONARC Objects Sharing Platform Presentation MOSP is a platform for creating, editing and sharing validated JSON objects of any type. You can use any

Terraform module to ship CloudTrail logs stored in a S3 bucket into a Kinesis stream for further processing and real-time analysis.
AWS infrastructure to ship CloudTrail logs from S3 to Kinesis This repository contains a Terraform module to ship CloudTrail logs stored in a S3 bucke
Project template for using aws-cdk, Chalice and React in concert, including RDS Postgresql and AWS Cognito
What is This? This repository is an opinonated project template for using aws-cdk, Chalice and React in concert. Where aws-cdk and Chalice are in Pyth

Brute force a JWT token. Script uses multithreading.
JWT BF Brute force a JWT token. Script uses multithreading. Tested on Kali Linux v2021.4 (64-bit). Made for educational purposes. I hope it will help!
sysctl/sysfs settings on a fly for Kubernetes Cluster. No restarts are required for clusters and nodes.
SysBindings Daemon Little toolkit for control the sysctl/sysfs bindings on Kubernetes Cluster on the fly and without unnecessary restarts of cluster o
A small script to migrate or synchronize users & groups from Okta to AWS SSO
aws-sso-sync-okta A small script to migrate or synchronize users & groups from Okta to AWS SSO Changelog Version Remove hardcoded values on variables

boofuzz: Network Protocol Fuzzing for Humans
boofuzz: Network Protocol Fuzzing for Humans Boofuzz is a fork of and the successor to the venerable Sulley fuzzing framework. Besides numerous bug fi

Passhunt is a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords.
Passhunt is a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords.

The core packages of security analyzer web crawler
Security Analyzer 🐍 A large scale web crawler (considered also as vulnerability scanner tool) to take an overview about security of Moroccan sites Cu
Python codes for the server and client end that facilitates file transfers. (Using AWS EC2 instance as the server)
Server-and-Client-File-Transfer Python codes for the server and client end that facilitates file transfers. I will be using an AWS EC2 instance as the
code release for USENIX'22 paper `On the Security Risks of AutoML`
This project is a minimized runnable project cut from trojanzoo, which contains more datasets, models, attacks and defenses. This repo will not be mai

Bypass 4xx HTTP response status codes.
Forbidden Bypass 4xx HTTP response status codes. To see all the test cases, check the source code - follow the NOTE comments. Script uses multithreadi
A GitHub action for organizations that enables advanced security code scanning on all new repos
Advanced-Security-Enforcer What this repository does This code is for an active GitHub Action written in Python to check (on a schedule) for new repos

Simulation artifacts, core components and configuration files to integrate AWS DeepRacer device with ROS Navigation stack.
AWS DeepRacer Overview The AWS DeepRacer Evo vehicle is a 1/18th scale Wi-Fi enabled 4-wheel ackermann steering platform that features two RGB cameras
Github dorking tool
gh-dork Supply a list of dorks and, optionally, one of the following: a user (-u) a file with a list of users (-uf) an organization (-org) a file with
AWS Interactive CLI - Allows you to execute a complex AWS commands by chaining one or more other AWS CLI dependency
AWS Interactive CLI - Allows you to execute a complex AWS commands by chaining one or more other AWS CLI dependency
A python library for creating Slack slash commands using AWS Lambda Functions
slashbot Slashbot makes it easy to create slash commands using AWS Lambda functions. These can be handy for creating a secure way to execute automated

Using AWS Batch jobs to bulk copy/sync files in S3
Using AWS Batch jobs to bulk copy/sync files in S3

AutomaTik is an automation system for MikroTik devices with simplicity and security in mind.
AutomaTik Installation AutomaTik is an automation system for MikroTik devices with simplicity and security in mind. Winbox is the main tool for MikroT

Multi-Branch CI/CD Pipeline using CDK Pipelines.
Using AWS CDK Pipelines and AWS Lambda for multi-branch pipeline management and infrastructure deployment. This project shows how to use the AWS CDK P
Manage AWS Secrets the easy way
AWStanding Easily load variables from AWS Parameter store into environment variables. Why to AWStanding? Because it handles AWS pagination so the amou
Zappa makes it super easy to build and deploy server-less, event-driven Python applications on AWS Lambda + API Gateway.
Zappa makes it super easy to build and deploy server-less, event-driven Python applications (including, but not limited to, WSGI web apps) on AWS Lambda + API Gateway. Think of it as "serverless" web hosting for your Python apps. That means infinite scaling, zero downtime, zero maintenance - and at a fraction of the cost of your current deployments!
Angora is a mutation-based fuzzer. The main goal of Angora is to increase branch coverage by solving path constraints without symbolic execution.
Angora Angora is a mutation-based coverage guided fuzzer. The main goal of Angora is to increase branch coverage by solving path constraints without s

ProFuzzBench - A Benchmark for Stateful Protocol Fuzzing
ProFuzzBench - A Benchmark for Stateful Protocol Fuzzing ProFuzzBench is a benchmark for stateful fuzzing of network protocols. It includes a suite of
Work with the AWS IP address ranges in native Python.
Amazon Web Services (AWS) publishes its current IP address ranges in JSON format. Python v3 provides an ipaddress module in the standard library that allows you to create, manipulate, and perform operations on IPv4 and IPv6 addresses and networks. Wouldn't it be nice if you could work with the AWS IP address ranges like native Python objects?
This repository contains ready to deploy automations on AWS
aws-automation-plugins This repository contains ready to deploy automations on AWS. How-To All projects in this repository contain a deploy.sh file wh
Huggingface inference with GPU Docker on AWS
This repository contains code to containerize and deploy a GPU docker on AWS for summarization task. Find a detailed blogpost here Youtube Video Versi
2021 Machine Learning Security Evasion Competition
2021 Machine Learning Security Evasion Competition This repository contains code samples for the 2021 Machine Learning Security Evasion Competition. P
Criando Lambda Functions para Ingerir Dados de APIs com AWS CDK
LIVE001 - AWS Lambda para Ingerir Dados de APIs Fazer o deploy de uma função lambda com infraestrutura como código Lambda vai numa API externa e extra

Flutter Reverse Engineering Framework
This framework helps reverse engineer Flutter apps using patched version of Flutter library which is already compiled and ready for app repacking. There are changes made to snapshot deserialization process that allow you perform dynamic analysis in a convenient way.
Easy and secure implementation of Azure AD for your FastAPI APIs 🔒 Single- and multi-tenant support.
Easy and secure implementation of Azure AD for your FastAPI APIs 🔒 Single- and multi-tenant support.
troposphere - Python library to create AWS CloudFormation descriptions
troposphere - Python library to create AWS CloudFormation descriptions
Research Artifact of USENIX Security 2022 Paper: Automated Side Channel Analysis of Media Software with Manifold Learning
Manifold-SCA Research Artifact of USENIX Security 2022 Paper: Automated Side Channel Analysis of Media Software with Manifold Learning The repo is org
Wonk is a tool for combining a set of AWS policy files into smaller compiled policy sets.
Wonk is a tool for combining a set of AWS policy files into smaller compiled policy sets.
Early days of an Asset Discovery tool.
Please star this project! Written in Python Report Bug . Request Feature DISCLAIMER This project is in its early days, everything you see here is almo

GitGoat enables DevOps and Engineering teams to test security products intending to integrate with GitHub
GitGoat is an open source tool that was built to enable DevOps and Engineering teams to design and implement a sustainable misconfiguration prevention strategy. It can be used to test with products with access to GitHub repositories without a risk to your production environment.

KeyKatcher is a keylogger that records keystrokes made on a computer and sends to the E-Mail.
What is a keylogger? A keylogger is a software application or piece of hardware that monitors and records keystrokes made on a computer keyboard. The
Bleeding edge django template focused on code quality and security.
wemake-django-template Bleeding edge django2.2 template focused on code quality and security. Purpose This project is used to scaffold a django projec

This application demonstrates IoTVAS device discovery and security assessment API integration with the Rapid7 InsightVM.
Introduction This repository hosts a sample application that demonstrates integrating Firmalyzer's IoTVAS API with the Rapid7 InsightVM platform. This

TextAttack 🐙 is a Python framework for adversarial attacks, data augmentation, and model training in NLP
TextAttack 🐙 Generating adversarial examples for NLP models [TextAttack Documentation on ReadTheDocs] About • Setup • Usage • Design About TextAttack

Web authentication testing framework
What is this This is a framework designed to test authentication for web applications. While web proxies like ZAProxy and Burpsuite allow authenticate

Automated AWS account hardening with AWS Control Tower and AWS Step Functions
Automate activities in Control Tower provisioned AWS accounts Table of contents Introduction Architecture Prerequisites Tools and services Usage Clean
Simple DDL Parser to parse SQL (HQL, TSQL, AWS Redshift, Snowflake and other dialects) ddl files to json/python dict with full information about columns: types, defaults, primary keys, etc.
Simple DDL Parser Build with ply (lex & yacc in python). A lot of samples in 'tests/. Is it Stable? Yes, library already has about 5000+ usage per day
Audits Python environments and dependency trees for known vulnerabilities
pip-audit pip-audit is a prototype tool for scanning Python environments for packages with known vulnerabilities. It uses the Python Packaging Advisor

Demonstration that AWS IAM policy evaluation docs are incorrect
The flowchart from the AWS IAM policy evaluation documentation page, as of 2021-09-12, and dating back to at least 2018-12-27, is the following: The f
Bleeding edge django template focused on code quality and security.
wemake-django-template Bleeding edge django2.2 template focused on code quality and security. Purpose This project is used to scaffold a django projec
A zero-dependency Python library for getting the Kubernetes token of a AWS EKS cluster
tokeks A zero-dependency Python library for getting the Kubernetes token of a AWS EKS cluster. No AWS CLI, third-party client or library (boto3, botoc

Linux, Jenkins, AWS, SRE, Prometheus, Docker, Python, Ansible, Git, Kubernetes, Terraform, OpenStack, SQL, NoSQL, Azure, GCP, DNS, Elastic, Network, Virtualization. DevOps Interview Questions
Linux, Jenkins, AWS, SRE, Prometheus, Docker, Python, Ansible, Git, Kubernetes, Terraform, OpenStack, SQL, NoSQL, Azure, GCP, DNS, Elastic, Network, Virtualization. DevOps Interview Questions

Recommended AWS CDK project structure for Python applications
Recommended AWS CDK project structure for Python applications The project implements a user management backend component that uses Amazon API Gateway,

Small python script to look for common vulnerabilities on SMTP server.
BrokenSMTP BrokenSMTP is a python3 BugBounty/Pentesting tool to look for common vulnerabilities on SMTP server. Supported Vulnerability : Spoofing - T

Pokemon catch events project to demonstrate data pipeline on AWS
Pokemon Catches Data Pipeline This is a sample project to practice end-to-end data project; Terraform is used to deploy infrastructure; Kafka is the t
Deploy a STAC API and a dynamic mosaic tiler API using AWS CDK.
Earth Observation API Deploy a STAC API and a dynamic mosaic tiler API using AWS CDK.
We protect the privacy of the data on your computer by using the camera of your Debian based Pardus operating system. 🕵️
Pardus Lookout We protect the privacy of the data on your computer by using the camera of your Debian based Pardus operating system. The application i
Programming labs for 6.S060 (Foundations of Computer Security).
6.S060 Labs This git repository contains the code for the labs in 6.S060. In these labs, you will add a series of security features to a photo-sharing
PySETO is a PASETO (Platform-Agnostic SEcurity TOkens) implementation written in Python
A Python implementation of PASETO.
🔑 Password manager and password generator
Password-Manager Create Account Quick Login Generate Password Save Password Offline App Passwords are stored on your system and no one has access to t

AWSXenos will list all the trust relationships in all the IAM roles and S3 buckets
AWS External Account Scanner Xenos, is Greek for stranger. AWSXenos will list all the trust relationships in all the IAM roles, and S3 buckets, in an

Using AWS's API Gateway + Lambda + Python to run a simple websocket application. For learning/testing
Using AWS's API Gateway + Lambda + Python to run a simple websocket application. For learning/testing. The AWS Resources seemed overly complex and were missing some critical gotchas in setting up a system like this.
aws-lambda-scheduler lets you call any existing AWS Lambda Function you have in a future time.
aws-lambda-scheduler aws-lambda-scheduler lets you call any existing AWS Lambda Function you have in the future. This functionality is achieved by dyn

Goblyn is a Python tool focused to enumeration and capture of website files metadata.
Goblyn Metadata Enumeration What's Goblyn? Goblyn is a tool focused to enumeration and capture of website files metadata. How it works? Goblyn will se
Security-related flags and options for C compilers
Getting the maximum of your C compiler, for security

GitLab CI security tools runner
Common Security Pipeline Описание проекта: Данный проект является вариантом реализации DevSecOps практик, на базе: GitLab DefectDojo OpenSouce tools g
Docker is an open platform for developing, shipping, and running applications OS-level virtualization to deliver software in packages called containers However, 'security' is a top request on Docker's public roadmap This project aims at vulnerability check for such docker containers. New contributions are accepted
Docker-Vulnerability-Check Docker is an open platform for developing, shipping, and running applications OS-level virtualization to deliver software i
GraphQL security auditing script with a focus on performing batch GraphQL queries and mutations
BatchQL BatchQL is a GraphQL security auditing script with a focus on performing batch GraphQL queries and mutations. This script is not complex, and

graphw00f is Server Engine Fingerprinting utility for software security professionals looking to learn more about what technology is behind a given GraphQL endpoint.
graphw00f - GraphQL Server Fingerprinting graphw00f (inspired by wafw00f) is the GraphQL fingerprinting tool for GQL endpoints. Table of Contents How

Phomber is infomation grathering tool that reverse search phone numbers and get their details, written in python3.
A Infomation Grathering tool that reverse search phone numbers and get their details ! What is phomber? Phomber is one of the best tools available fo
This is the code repository for the USENIX Security 2021 paper, "Weaponizing Middleboxes for TCP Reflected Amplification".
weaponizing-censors Censors pose a threat to the entire Internet. In this work, we show that censoring middleboxes and firewalls can be weaponized by
Generate YARA rules for OOXML documents using ZIP local header metadata.
apooxml Generate YARA rules for OOXML documents using ZIP local header metadata. To learn more about this tool and the methodology behind it, check ou

Deploy an inference API on AWS (EC2) using FastAPI Docker and Github Actions
Deploy an inference API on AWS (EC2) using FastAPI Docker and Github Actions To learn more about this project: medium blog post The goal of this proje

Blockchain-Enabled IoT Sensor Framework that uses Augmented Reality and Artificial Intelligence.
Arduino + Raspberry Pi + Unity3D + Cloud + Hyperledger Our Mission: Keep it simple, leave no one behind. Blockchain-Enabled Smart Sensor Framework usi
EMBArk - The firmware security scanning environment
Embark is being developed to provide the firmware security analyzer emba as a containerized service and to ease accessibility to emba regardless of system and operating system.
A suite of utilities for AWS Lambda Functions that makes tracing with AWS X-Ray, structured logging and creating custom metrics asynchronously easier
A suite of utilities for AWS Lambda Functions that makes tracing with AWS X-Ray, structured logging and creating custom metrics asynchronously easier

This repository are used to give class about AWS
AWSTraining This repository are used to give class about AWS by Marco Antonio Pereira Linkedin: https://www.linkedin.com/in/marcoap To see the types o