776 Repositories
Python ddos-attack-tools Libraries
Lightweight utility tools for the detection of multiple spellings, meanings, and language-specific terminology in British and American English
Breame ( British English and American English) Breame is a lightweight Python package with a number of utility tools to aid in the detection of words

GraphiQL & the GraphQL LSP Reference Ecosystem for building browser & IDE tools.
Black Lives Matter 🖤 GraphQL IDE Monorepo Security Notice: All versions of graphiql 1.4.7 are vulnerable to an XSS attack in cases where the GraphQ
This python script can change the mac address after some attack
MAC-changer Hello people, this python script was written for people who want to change the mac address after some attack, I know there are many ways t

Text modding tools for FF7R (Final Fantasy VII Remake)
FF7R_text_mod_tools Subtitle modding tools for FF7R (Final Fantasy VII Remake) There are 3 tools I made. make_dualsub_mod.exe: Merges (or swaps) subti
![AMC- Automatic Media Access Control [MAC] Address Spoofing Tool](https://github.com/hexdee606/AMC2.0/raw/main/User/Banner.png)
AMC- Automatic Media Access Control [MAC] Address Spoofing Tool
AMC (Automatic Media Access Control [MAC] Address Spoofing tool), helps you to protect your real network hardware identity. Each entered time interval your hardware address was changed automatically. without interrupting your internet connection.

Dynamics-aware Adversarial Attack of 3D Sparse Convolution Network
Leaded Gradient Method (LGM) This repository contains the PyTorch implementation for paper Dynamics-aware Adversarial Attack of 3D Sparse Convolution
Exports the local variables into a global dictionary for later debugging.
PyExfiltrator Julia’s @exfiltrate for Python; Exports the local variables into a global dictionary for later debugging. Installation pip install pyexf
Tools for the Cleveland State Human Motion and Control Lab
Introduction This is a collection of tools that are helpful for gait analysis. Some are specific to the needs of the Human Motion and Control Lab at C

Computer vision - fun segmentation experience using classic and deep tools :)
Computer_Vision_Segmentation_Fun Segmentation of Images and Video. Tools: pytorch Models: Classic model - GrabCut Deep model - Deeplabv3_resnet101 Flo

DaProfiler allows you to get emails, social medias, adresses, works and more on your target using web scraping and google dorking techniques
DaProfiler allows you to get emails, social medias, adresses, works and more on your target using web scraping and google dorking techniques, based in France Only. The particularity of this program is its ability to find your target's e-mail adresses.
I hacked my own webcam from a Kali Linux VM in my local network, using Ettercap to do the MiTM ARP poisoning attack, sniffing with Wireshark, and using metasploit
plan I - Linux Fundamentals Les utilisateurs et les droits Installer des programmes avec apt-get Surveiller l'activité du système Exécuter des program
labsecurity is a framework and its use is for ethical hacking and computer security
labsecurity labsecurity is a framework and its use is for ethical hacking and computer security. Warning This tool is only for educational purpose. If
Tools to download and cleanup Common Crawl data
cc_net Tools to download and clean Common Crawl as introduced in our paper CCNet. If you found these resources useful, please consider citing: @inproc
Dense Passage Retriever - is a set of tools and models for open domain Q&A task.
Dense Passage Retrieval Dense Passage Retrieval (DPR) - is a set of tools and models for state-of-the-art open-domain Q&A research. It is based on the
Tools hacking termux in the name ant-attack
Hello friends, I am ama.player0000. Web developer, software, Android command line (termux). (1)=Well, ant-attack tool is a tool to attack sites and disable them. (2)=You can use those CCTV servers, switch controls, slow down WI-FI, send packets around by dongle or hotspot. [*[*[*=I said a very important point at the bottom of the page, be sure to read it !! *]*]*]
log4j-tools: CVE-2021-44228 poses a serious threat to a wide range of Java-based applications
log4j-tools Quick links Click to find: Inclusions of log4j2 in compiled code Calls to log4j2 in compiled code Calls to log4j2 in source code Overview
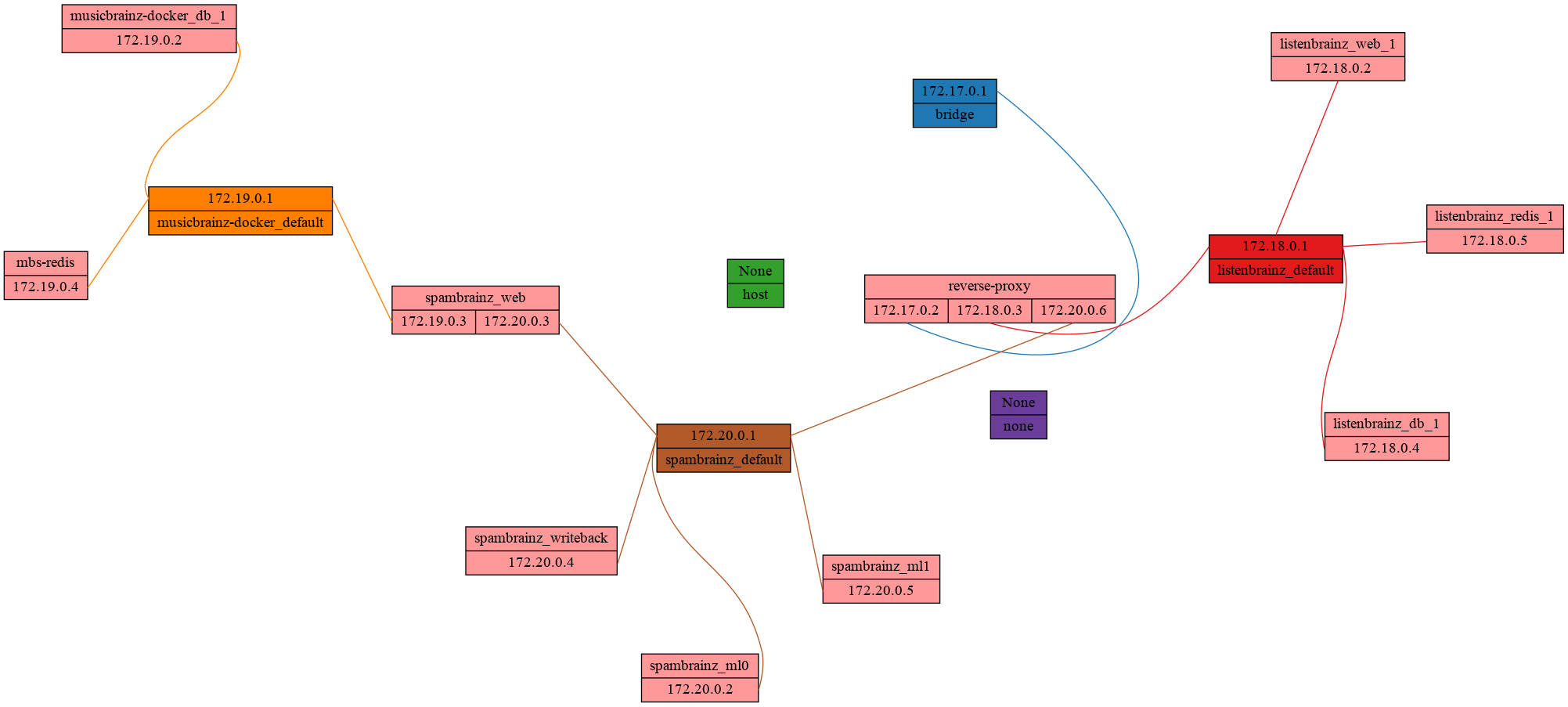
Quickly visualize docker networks with graphviz.
Docker Network Graph Visualize the relationship between Docker networks and containers as a neat graphviz graph. Example Usage usage: docker-net-graph

Tools for calculating and visualizing Elo-like ratings of MLB teams using Retosheet data
Overview This project uses historical baseball games data to calculate an Elo-like rating for MLB teams based on regular season match ups. The Elo rat
Pure Python tools for reading and writing all TIFF IFDs, sub-IFDs, and tags.
Tiff Tools Pure Python tools for reading and writing all TIFF IFDs, sub-IFDs, and tags. Developed by Kitware, Inc. with funding from The National Canc
Tools for investigating Log4j CVE-2021-44228
Log4jTools Tools for investigating Log4j CVE-2021-44228 FetchPayload.py (Get java payload from ldap path provided in JNDI lookup). Example command: Re
Convenient tools for using Swagger to define and validate your interfaces in a Pyramid webapp.
Convenient tools for using Swagger to define and validate your interfaces in a Pyramid webapp.
Trustme: #1 quality TLS certs while you wait
trustme: #1 quality TLS certs while you wait You wrote a cool network client or server. It encrypts connections using TLS. Your test suite needs to ma

Buff A simple BOF library I wrote under an hour to help me automate with BOF attack
What is Buff? A simple BOF library I wrote under an hour to help me automate with BOF attack. It comes with fuzzer and a generic method to generate ex

A simple file transfer tools, similar to rz / sz but compatible with tmux (control mode), which works with iTerm2 and has a nice progress bar
trzsz A simple file transfer tools, similar to rz/sz but compatible with tmux (control mode), which works with iTerm2 and has a nice progress bar. Why
Tools untuk cek nomor rekening, terhadap penipuan yang sudah terjadi!
No Rekening Checker Selalu waspada terhadap penipuan! Sebelum anda transfer sejumlah uang alangkah baiknya untuk cek terlebih dahulu, apakah norek itu
Python-dotenv reads key-value pairs from a .env file and can set them as environment variables.
python-dotenv Python-dotenv reads key-value pairs from a .env file and can set them as environment variables. It helps in the development of applicati
Tools for teachers and students using nng (Natural Number Game)
nngtools Usage Place your nngsave.json to the directory in which you want to extract the level files. Place nngmap.json on the same directory. Run nng
Tools ini hanya bisa digunakan untuk menyerang website atau http/s
☢️ Tawkun DoS ☢️ Tools ini hanya bisa digunakan untuk menyerang website atau http/s FITUR: [ ☯️ ] Proxy Mode [ 🔥 ] SOCKS Mode | Kadang Eror [ ☢️ ] Ht

𝗖𝝠𝝦𝝩𝝠𝝞𝝥 𝝦𝗥𝝞𝗖𝝽°™️ 🇱🇰 Is An All In One Media Inline Bot Made For Inline Your Media Effectively With Some Advance Security Tools♥️
𝗖𝝠𝝦𝝩𝝠𝝞𝝥 𝝦𝗥𝝞𝗖𝝽° ™️ 🇱🇰 𝗙𝗘𝝠𝝩𝗨𝗥𝗘𝗦 Auto Filter IMDB Admin Commands Broadcast Index IMDB Search Inline Search Random Pics Ids & User I
Flexible HDF5 saving/loading and other data science tools from the University of Chicago
deepdish Flexible HDF5 saving/loading and other data science tools from the University of Chicago. This repository also host a Deep Learning blog: htt
Tools for test driven data-wrangling and data validation.
datatest: Test driven data-wrangling and data validation Datatest helps to speed up and formalize data-wrangling and data validation tasks. It impleme
Tools for parsing messy tabular data.
Parsing for messy tables A library for dealing with messy tabular data in several formats, guessing types and detecting headers. See the documentation

Python supercharged for the fastai library
Welcome to fastcore Python goodies to make your coding faster, easier, and more maintainable Python is a powerful, dynamic language. Rather than bake
Detect secret in source code, scan your repo for leaks. Find secrets with GitGuardian and prevent leaked credentials. GitGuardian is an automated secrets detection & remediation service.
GitGuardian Shield: protect your secrets with GitGuardian GitGuardian shield (ggshield) is a CLI application that runs in your local environment or in

Goal: Enable awesome tooling for Bazel users of the C language family.
Hedron's Compile Commands Extractor for Bazel — User Interface What is this project trying to do for me? First, provide Bazel users cross-platform aut
Tools ini digunakan untuk krekk pacebuk:v
E-Crack By Aang-XD Fitur Login • Login via token facebook • Login via cookie facebook Install On Termux $ pkg update && pkg upgrade $ pkg install pyth
Models, datasets and tools for Facial keypoints detection
Template for Data Science Project This repo aims to give a robust starting point to any Data Science related project. It contains readymade tools setu
Collection of awesome Python types, stubs, plugins, and tools to work with them.
Awesome Python Typing Collection of awesome Python types, stubs, plugins, and tools to work with them. Contents Static type checkers Dynamic type chec

Tools crack instagram + fb ayok dicoba keburu premium 😁
FITUR INSTALLASI [1] pkg update && pkg upgrade [2] pkg install git [3] pkg install python [4] pkg install python2 [5] pkg install nano [6]

Python Toolkit containing different Cyber Attacks Tools
Helikopter Python Toolkit containing different Cyber Attacks Tools. Tools in Helikopter Toolkit 1. FattyNigger (PYTHON WORM) 2. Taxes (PYTHON PASS EXT

An ongoing curated list of OS X best applications, libraries, frameworks and tools to help developers set up their macOS Laptop.
macOS Development Setup Welcome to MacOS Local Development & Setup. An ongoing curated list of OS X best applications, libraries, frameworks and tools
ZenML 🙏: MLOps framework to create reproducible ML pipelines for production machine learning.
ZenML is an extensible, open-source MLOps framework to create production-ready machine learning pipelines. It has a simple, flexible syntax, is cloud and tool agnostic, and has interfaces/abstractions that are catered towards ML workflows.

Tools for computational pathology
A toolkit for computational pathology and machine learning. View documentation Please cite our paper Installation There are several ways to install Pa
Simple Dos-Attacker.
dos-attacker ❕ Atenção Não ataque sites privados. isto é illegal. 🖥️ Pré-requisitos Ultima versão do Python3. para verificar isto, é bem simples. Bas
Model Validation Toolkit is a collection of tools to assist with validating machine learning models prior to deploying them to production and monitoring them after deployment to production.
Model Validation Toolkit is a collection of tools to assist with validating machine learning models prior to deploying them to production and monitoring them after deployment to production.

Implementation of paper "Decision-based Black-box Attack Against Vision Transformers via Patch-wise Adversarial Removal"
Patch-wise Adversarial Removal Implementation of paper "Decision-based Black-box Attack Against Vision Transformers via Patch-wise Adversarial Removal

S-attack library. Official implementation of two papers "Are socially-aware trajectory prediction models really socially-aware?" and "Vehicle trajectory prediction works, but not everywhere".
S-attack library: A library for evaluating trajectory prediction models This library contains two research projects to assess the trajectory predictio
Code for a db backend that relies on bash tools (grep, cat, echo, etc)
Simple-nosql-db is a python backend for a database that relies on unix tools such as cat, echo and grep. Funny enough I got the idea from this discuss
Simples brute forcer de diretorios para web pentest.
🦑 dirbruter Simples brute forcer de diretorios para web pentest. ❕ Atenção Não ataque sites privados. Isto é illegal. 🖥️ Pré-requisitos Ultima versã

An ongoing curated list of frameworks, libraries, learning tutorials, software and resources in Python Language.
Python Development Welcome to the world of Python. An ongoing curated list of frameworks, libraries, learning tutorials, software and resources in Pyt
A begginer reverse shell tool python.
A begginer tools for hacking. The theme of this repository is to bring some ready-made open-source tools for anyone new to the world of hacking. This

Template for new OSINT command-line tools
OSINT cli tool skeleton Template for new OSINT command-line tools. Press button "Use this template" to generate your own tool repository. See INSTALL.
Modular analysis tools for neurophysiology data
Neuroanalysis Modular and interactive tools for analysis of neurophysiology data, with emphasis on patch-clamp electrophysiology. Functions for runnin
Collection of sports betting AI tools.
sports-betting sports-betting is a collection of tools that makes it easy to create machine learning models for sports betting and evaluate their perf
This project was created using Python technology and flask tools to scrape a music site
python-scrapping This project was created using Python technology and flask tools to scrape a music site You need to install the following packages to
A begginer reverse shell tool python.
A begginer reverse shell tool python. Este programa é para apenas estudo e conhecimento. Não use isso em outra pessoas. Não me responsabilizo por uso
Code for "My(o) Armband Leaks Passwords: An EMG and IMU Based Keylogging Side-Channel Attack" paper
Myo Keylogging This is the source code for our paper My(o) Armband Leaks Passwords: An EMG and IMU Based Keylogging Side-Channel Attack by Matthias Ga
A working cloudflare uam bypass !!
Dark Utilities - Cloudflare Uam Bypass Our Website https://over-spam.space/ ! Additional Informations The proxies type are http,https ... You need fas

This collection of tools that makes it easy to secure and/or obfuscate messages, files, and data.
Scrambler App This collection of tools that makes it easy to secure and/or obfuscate messages, files, and data. It leverages encryption tools such as
Brute force attack tool for Azure AD Autologon/Seamless SSO
Brute force attack tool for Azure AD Autologon
NotesToCommands - a fully customizable notes / command template program, allowing users to instantly execute terminal commands
NotesToCommands is a fully customizable notes / command template program, allowing users to instantly execute terminal commands with dynamic arguments grouped into sections in their notes/files. It was originally created for pentesting uses, to avoid the needed remembrance and retyping of sets of commands for various attacks.

Great script for sending and spaming emails! gmail, yahoo, outlook, hotmail.
• License • Issues • Project • Wikipedia • Я не несу ответственности за ваши действия. Скачивая программное обеспечение из этого репозитория, вы согла
This directory gathers the tools developed by the Data Sourcing Working Group
BigScience Data Sourcing Code This directory gathers the tools developed by the Data Sourcing Working Group First Sourcing Sprint: October 2021 The co
Tsunami-Fi is simple multi-tool bash application for Wi-Fi attacks
🪴 Tsunami-Fi 🪴 Русская версия README 🌿 Description 🌿 Tsunami-Fi is simple multi-tool bash application for Wi-Fi WPS PixieDust and NullPIN attack,
Utility.py - a utility that offerres cool cli tools and games.
Utilty.py Utility.py is a utility that offerres cool cli tools and games. Currently the offerd games/items are: get the number, countdown, random name
A cookiecutter to start a Python package with flawless practices and a magical workflow 🧙🏼♂️
PyPackage Cookiecutter This repository is a cookiecutter to quickly start a Python package. It contains a ton of very useful features 🐳 : Package man
FIVE, Vulnerability Scanner And Mass Exploiter, made for pentesting.
$ FIVE - FIVE is a Pentesting Framework to Test the Security & Integrity of a Website, or Multiple Websites. $ Info FIVE Was Made After Vulnnr to Prod
Dense Passage Retriever - is a set of tools and models for open domain Q&A task.
Dense Passage Retrieval Dense Passage Retrieval (DPR) - is a set of tools and models for state-of-the-art open-domain Q&A research. It is based on the
FPE - Format Preserving Encryption with FF3 in Python
ff3 - Format Preserving Encryption in Python An implementation of the NIST approved FF3 and FF3-1 Format Preserving Encryption (FPE) algorithms in Pyt
A protocol or procedure that connects an ever-changing IP address to a fixed physical machine address
p0znMITM ARP Poisoning Tool What is ARP? Address Resolution Protocol (ARP) is a protocol or procedure that connects an ever-changing IP address to a f

Simulate Attacks With Mininet And Hping3
Miniattack Simulate Attacks With Mininet And Hping3 It measures network load with bwm-ng when the net is under attack and plots the result. This demo
Core ML tools contain supporting tools for Core ML model conversion, editing, and validation.
Core ML Tools Use coremltools to convert machine learning models from third-party libraries to the Core ML format. The Python package contains the sup
Tools for curating biomedical training data for large-scale language modeling
Tools for curating biomedical training data for large-scale language modeling
Code for EMNLP2020 long paper: BERT-Attack: Adversarial Attack Against BERT Using BERT
BERT-ATTACK Code for our EMNLP2020 long paper: BERT-ATTACK: Adversarial Attack Against BERT Using BERT Dependencies Python 3.7 PyTorch 1.4.0 transform
A Model for Natural Language Attack on Text Classification and Inference
TextFooler A Model for Natural Language Attack on Text Classification and Inference This is the source code for the paper: Jin, Di, et al. "Is BERT Re

PyTorch Live is an easy to use library of tools for creating on-device ML demos on Android and iOS.
PyTorch Live is an easy to use library of tools for creating on-device ML demos on Android and iOS. With Live, you can build a working mobile app ML demo in minutes.
A collection of tools for managing Jira issues for the RHODS project
RHODS-Jira-Tools A collection of tools for managing Jira issues for the RHODS project move_to_qa.py This script handles transitioning a given Jira iss
Dark Utilities - Cloudflare Uam Bypass
Dark Utilities - Cloudflare Uam Bypass
Um keylogger que se disfarça de um app que tira print da tela.
Keylogger_ Um keylogger que se disfarça de um app que tira print da tela. Este programa captura o print da tela e salva ,normalmente, na pasta Picture
A collection of simple tools that proved to be needed for hadling large periodic calculations with the VASP software package.
VESTA-tools A collection of simple tools that proved to be needed for handling large periodic calculations with the VASP software package. distTotCalc
A set of simple scripts to process the Imagenet-1K dataset as TFRecords and make index files for NVIDIA DALI.
Overview This is a set of simple scripts to process the Imagenet-1K dataset as TFRecords and make index files for NVIDIA DALI. Make TFRecords To run t

ClearML - Auto-Magical Suite of tools to streamline your ML workflow. Experiment Manager, MLOps and Data-Management
ClearML - Auto-Magical Suite of tools to streamline your ML workflow Experiment Manager, MLOps and Data-Management ClearML Formerly known as Allegro T

Fast subdomain scanner, Takes arguments from a Json file ("args.json") and outputs the subdomains.
Fast subdomain scanner, Takes arguments from a Json file ("args.json") and outputs the subdomains. File Structure core/ colors.py db/ wordlist.txt REA
Table (Finnish Taulukko) glued together to transform into hands-free living.
taulukko Table (Finnish Taulukko) glued together to transform into hands-free living. Installation Preferred way to install is as usual (for testing o

DALLE-tools provided useful dataset utilities to improve you workflow with WebDatasets.
DALLE tools DALLE-tools is a github repository with useful tools to categorize, annotate or check the sanity of your datasets. Installation Just clone

Algorithm for Cutting Stock Problem using Google OR-Tools. Link to the tool:
Cutting Stock Problem Cutting Stock Problem (CSP) deals with planning the cutting of items (rods / sheets) from given stock items (which are usually o
TOOLS CRACK FACEBOOK
Installation $ pkg update && pkg upgrade $ pkg install python2 $ pkg install git $ git clone https://github.com/Mark-Zuck/zafi $ cd zafi $ pip2 instal
This is a simple tool to create ZIP payloads using a provided wordlist for the symlink attack (present in some file upload vulnerabilities)
zip-symlink-payload-creator This is a simple tool to create ZIP payloads using a provided wordlist for the symlink attack (present in some file upload

A multi-platform HTTP(S) Reverse Shell Server and Client in Python 3
Phantom - A multi-platform HTTP(S) Reverse Shell Server and Client Phantom is a multi-platform HTTP(S) Reverse Shell server and client in Python 3. Bi
Tools for improving Python imports
imptools Tools for improving Python imports. Installation pip3 install imptools Overview Detailed docs import_path Import a module from any path on th

A discord account nuker with lots of tools that will destroy a discord account
A discord account nuker with lots of tools that will destroy a discord account (token destroyer... and much more).
A patch and keygen tools for typora.
A patch and keygen tools for typora.

Python tools for 3D face: 3DMM, Mesh processing(transform, camera, light, render), 3D face representations.
face3d: Python tools for processing 3D face Introduction This project implements some basic functions related to 3D faces. You can use this to process
The best way to send tokens into a specific server, which can be used for discord bots, and some tools..
XTRA420 The simplified version of sending tokens into a server, the basic and fastest way.. When using this, you have the option to use proxies (http)

Subnet Replacement Attack: Towards Practical Deployment-Stage Backdoor Attack on Deep Neural Networks
Subnet Replacement Attack: Towards Practical Deployment-Stage Backdoor Attack on Deep Neural Networks Official implementation of paper Towards Practic
Python tools for experimenting with differentiable intonation cost measures
Differentiable Intonation Tools The Differentiable Intonation Tools (dit) are a collection of Python functions to analyze the intonation in multitrack

Tools to create pixel-wise object masks, bounding box labels (2D and 3D) and 3D object model (PLY triangle mesh) for object sequences filmed with an RGB-D camera.
Tools to create pixel-wise object masks, bounding box labels (2D and 3D) and 3D object model (PLY triangle mesh) for object sequences filmed with an RGB-D camera. This project prepares training and testing data for various deep learning projects such as 6D object pose estimation projects singleshotpose, as well as object detection and instance segmentation projects.

This is tools hacking for scan vuln in port web, happy using
Xnuvers007 PortInjection this is tools hacking for scan vuln in port web, happy using view/show python 3.9 solo coder (tangerang) 19 y/o installation
GMailBomber is a form of Internet abuse which is perpetrated through the sending of massive volumes of email to a specific email address with the goal of overflowing the mailbox and overwhelming the mail server hosting the address, making it into some form of denial of service attack.
GMailBomber is a form of Internet abuse which is perpetrated through the sending of massive volumes of email to a specific email address with the goal of overflowing the mailbox and overwhelming the mail server hosting the address, making it into some form of denial of service attack.
