248 Repositories
Python dictionary-attack-facebook Libraries

Implementation of paper "Decision-based Black-box Attack Against Vision Transformers via Patch-wise Adversarial Removal"
Patch-wise Adversarial Removal Implementation of paper "Decision-based Black-box Attack Against Vision Transformers via Patch-wise Adversarial Removal

S-attack library. Official implementation of two papers "Are socially-aware trajectory prediction models really socially-aware?" and "Vehicle trajectory prediction works, but not everywhere".
S-attack library: A library for evaluating trajectory prediction models This library contains two research projects to assess the trajectory predictio
The 1st Place Solution of the Facebook AI Image Similarity Challenge (ISC21) : Descriptor Track.
ISC21-Descriptor-Track-1st The 1st Place Solution of the Facebook AI Image Similarity Challenge (ISC21) : Descriptor Track. You can check our solution
Correcting typos in a word based on the frequency dictionary
Auto-correct text Correcting typos in a word based on the frequency dictionary. This algorithm is based on the distance between words according to the
A python base script from which you can hack or clone any person's facebook friendlist or followers accounts which have simple password
Hcoder This is a python base script from which you can hack or clone any person's facebook friendlist or followers accounts which have simple password
Code for "My(o) Armband Leaks Passwords: An EMG and IMU Based Keylogging Side-Channel Attack" paper
Myo Keylogging This is the source code for our paper My(o) Armband Leaks Passwords: An EMG and IMU Based Keylogging Side-Channel Attack by Matthias Ga
Brute force attack tool for Azure AD Autologon/Seamless SSO
Brute force attack tool for Azure AD Autologon
Script Crack Facebook Premium 🚶♂
premium Script Crack Facebook Premium 🚶♂ In Script Install Script $ pkg update && pkg upgrade $ termux-setup-storage $ pkg install python $ pkg inst
English dictionary using Django based on freecodecamp
English Dictionary Hi there, i made this english dictionary using Django based on freecodecamp.org tutorial :) Table of Contents Preview Technologies
Script Crack Facebook Elite 🚶♂
elite Script Crack Facebook Elite 🚶♂ Install Script $ pkg update && pkg upgrade $ termux-setup-storage $ pkg install git $ pkg install python $ pip

Google, Facebook, Amazon, Microsoft, Netflix tech interview questions
Algorithm and Data Structures Interview Questions HackerRank | Practice, Tutorials & Interview Preparation Solutions This repository consists of solut
A protocol or procedure that connects an ever-changing IP address to a fixed physical machine address
p0znMITM ARP Poisoning Tool What is ARP? Address Resolution Protocol (ARP) is a protocol or procedure that connects an ever-changing IP address to a f

A simple Python +3.x script to download videos from Facebook.
Facebook Video Downloader A simple Python +3.x script to download videos from Facebook posts
Script Crack Facebook Premium 🚶♂
prem Script Crack Facebook Premium 🚶♂ Install Script $ pkg update && pkg update $ termux-setup-storage $ pkg install git $ pkg install python $ pip

Simulate Attacks With Mininet And Hping3
Miniattack Simulate Attacks With Mininet And Hping3 It measures network load with bwm-ng when the net is under attack and plots the result. This demo
Code for EMNLP2020 long paper: BERT-Attack: Adversarial Attack Against BERT Using BERT
BERT-ATTACK Code for our EMNLP2020 long paper: BERT-ATTACK: Adversarial Attack Against BERT Using BERT Dependencies Python 3.7 PyTorch 1.4.0 transform
A Model for Natural Language Attack on Text Classification and Inference
TextFooler A Model for Natural Language Attack on Text Classification and Inference This is the source code for the paper: Jin, Di, et al. "Is BERT Re
TOOLS CRACK FACEBOOK
Installation $ pkg update && pkg upgrade $ pkg install python2 $ pkg install git $ git clone https://github.com/Mark-Zuck/zafi $ cd zafi $ pip2 instal
This is a simple tool to create ZIP payloads using a provided wordlist for the symlink attack (present in some file upload vulnerabilities)
zip-symlink-payload-creator This is a simple tool to create ZIP payloads using a provided wordlist for the symlink attack (present in some file upload
A dictionary that can be flattened and re-inflated
deflatable-dict A dictionary that can be flattened and re-inflated. Particularly useful if you're interacting with yaml, for example. Installation wit

Subnet Replacement Attack: Towards Practical Deployment-Stage Backdoor Attack on Deep Neural Networks
Subnet Replacement Attack: Towards Practical Deployment-Stage Backdoor Attack on Deep Neural Networks Official implementation of paper Towards Practic
GMailBomber is a form of Internet abuse which is perpetrated through the sending of massive volumes of email to a specific email address with the goal of overflowing the mailbox and overwhelming the mail server hosting the address, making it into some form of denial of service attack.
GMailBomber is a form of Internet abuse which is perpetrated through the sending of massive volumes of email to a specific email address with the goal of overflowing the mailbox and overwhelming the mail server hosting the address, making it into some form of denial of service attack.
Forecasting prices using Facebook/Meta's Prophet model
CryptoForecasting using Machine and Deep learning (Part 1) CryptoForecasting using Machine Learning The main aspect of predicting the stock-related da

A Facebook Messenger Chatbot using NLP
A Facebook Messenger Chatbot using NLP This project is about creating a messenger chatbot using basic NLP techniques and models like Logistic Regressi
GoldenSAML Attack Libraries and Framework
WhiskeySAML and Friends TicketsPlease TicketsPlease: Python library to assist with the generation of Kerberos tickets, remote retrieval of ADFS config
MITRE ATT&CK Lookup Tool
MITRE ATT&CK Lookup Tool attack-lookup is a tool that lets you easily check what Tactic, Technique, or Sub-technique ID maps to what name, and vice ve
Backdoor Attack through Frequency Domain
Backdoor Attack through Frequency Domain DEPENDENCIES python==3.8.3 numpy==1.19.4 tensorflow==2.4.0 opencv==4.5.1 idx2numpy==1.2.3 pytorch==1.7.0 Data
Pytorch implementation of "Geometrically Adaptive Dictionary Attack on Face Recognition" (WACV 2022)
Geometrically Adaptive Dictionary Attack on Face Recognition This is the Pytorch code of our paper "Geometrically Adaptive Dictionary Attack on Face R
Use Flask API to wrap Facebook data. Grab the wapper of Facebook public pages without an API key.
Facebook Scraper Use Flask API to wrap Facebook data. Grab the wapper of Facebook public pages without an API key. (Currently working 2021) Setup Befo

💬 Python scripts to parse Messenger, Hangouts, WhatsApp and Telegram chat logs into DataFrames.
Chatistics Python 3 scripts to convert chat logs from various messaging platforms into Pandas DataFrames. Can also generate histograms and word clouds

Pytorch implementation of 'Fingerprint Presentation Attack Detector Using Global-Local Model'
RTK-PAD This is an official pytorch implementation of 'Fingerprint Presentation Attack Detector Using Global-Local Model', which is accepted by IEEE T
🔪 Facebook Messenger to email bridge based on reverse engineered auth and GraphQL APIs.
Unzuckify This repository has a small Python application which allows me to receive an email notification when somebody sends me a Facebook message. W

TraSw for FairMOT - A Single-Target Attack example (Attack ID: 19; Screener ID: 24):
TraSw for FairMOT A Single-Target Attack example (Attack ID: 19; Screener ID: 24): Fig.1 Original Fig.2 Attacked By perturbing only two frames in this

The lastest all in one bombing tool coded in python uses tbomb api
BaapG-Attack is a python3 based script which is officially made for linux based distro . It is inbuit mass bomber with sms, mail, calls and many more bombing

Bot facebook
botfb Bot facebook Login via cookies cara install $pkg update && pkg upgrade $pkg install git python $git clone https://github.com/Ainx-BOT/botfb $cd

Abusing Microsoft 365 OAuth Authorization Flow for Phishing Attack
O365DevicePhish Microsoft365_devicePhish Abusing Microsoft 365 OAuth Authorization Flow for Phishing Attack This is a simple proof-of-concept script t

GAM timeseries modeling with auto-changepoint detection. Inspired by Facebook Prophet and implemented in PyMC3
pm-prophet Pymc3-based universal time series prediction and decomposition library (inspired by Facebook Prophet). However, while Faceook prophet is a

ChainJacking is a tool to find which of your Go lang direct GitHub dependencies is susceptible to ChainJacking attack.
ChainJacking is a tool to find which of your Go lang direct GitHub dependencies is susceptible to ChainJacking attack.

NEW FACEBOOK CLONER WITH NEW PASSWORD, TERMUX FB CLONE, FB CLONING COMMAND. M
NEW FACEBOOK CLONER WITH NEW PASSWORD, TERMUX FB CLONE, FB CLONING COMMAND. M
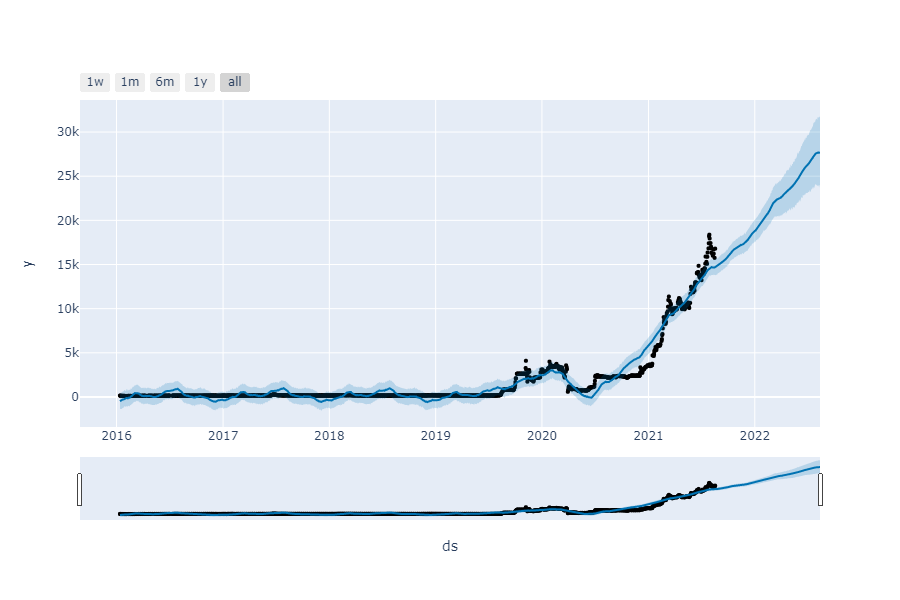
Stock Price Prediction Bank Jago Using Facebook Prophet Machine Learning & Python
Stock Price Prediction Bank Jago Using Facebook Prophet Machine Learning & Python Overview Bank Jago has attracted investors' attention since the end
Tool cek opsi checkpoint facebook!
tool apa ini? cek_opsi_facebook adalah sebuah tool yang mengecek opsi checkpoint akun facebook yang terkena checkpoint! tujuan dibuatnya tool ini? too

FCA: Learning a 3D Full-coverage Vehicle Camouflage for Multi-view Physical Adversarial Attack
FCA: Learning a 3D Full-coverage Vehicle Camouflage for Multi-view Physical Adversarial Attack Case study of the FCA. The code can be find in FCA. Cas

Suplantar mails de empresas como google, facebook, github, etc...
Suplantar mails de empresas como google, facebook, github, etc...
JSON and CSV data for Swahili dictionary with over 16600+ words
kamusi JSON and CSV data for swahili dictionary with over 16600+ words. This repo consists of data from swahili dictionary with about 16683 words toge
Multi-Modal Fingerprint Presentation Attack Detection: Evaluation On A New Dataset
PADISI USC Dataset This repository analyzes the PADISI-Finger dataset introduced in Multi-Modal Fingerprint Presentation Attack Detection: Evaluation
This reposityory contains the PyTorch implementation of our paper "Generative Dynamic Patch Attack".
Generative Dynamic Patch Attack This reposityory contains the PyTorch implementation of our paper "Generative Dynamic Patch Attack". Requirements PyTo

An open-source online reverse dictionary.
An open-source online reverse dictionary.
Cack facebook tidak login
Cack facebook tidak login

Code for "Adversarial attack by dropping information." (ICCV 2021)
AdvDrop Code for "AdvDrop: Adversarial Attack to DNNs by Dropping Information(ICCV 2021)." Human can easily recognize visual objects with lost informa
Dapunta Multi Brute Force Facebook - Crack Facebook With Login - Free
✭ DMBF CRACK Dibuat Dengan ❤️ Oleh Dapunta Author: - Dapunta Khurayra X ⇨ Fitur Login [✯] Login Token ⇨ Fitur Crack [✯] Crack Dari Teman, Public,
nocasedict - A case-insensitive ordered dictionary for Python
nocasedict - A case-insensitive ordered dictionary for Python Overview Class NocaseDict is a case-insensitive ordered dictionary that preserves the or

Facebook account cloning/hacking advanced tool + dictionary attack added | Facebook automation tool
loggef Facebook automation tool, Facebook account hacking and cloning advanced tool + dictionary attack added Warning Use this tool for educational pu
Facebook Group Scraping Using Beautiful Soup & Selenium
Extract Facebook group posts that are related to a specific topic and write them to a .json file.

Tools convert cookies facebook menjadi token facebook.
Tools convert cookies facebook menjadi token facebook.
python's memory-saving dictionary data structure
ConstDict python代替的Dict数据结构 若字典不会增加字段,只读/原字段修改 使用ConstDict可节省内存 Dict()内存主要消耗的地方: 1、Dict扩容机制,预留内存空间 2、Dict也是一个对象,内部会动态维护__dict__,增加slot类属性可以节省内容 节省内存大小

python script for hack gmail account using brute force attack
#Creator: johnry #coded by john ry GBrute python script for hack gmail account using brute force attack Commands apt update && apt upgrade git clone h

Generate malicious files using recently published bidi-attack (CVE-2021-42574)
CVE-2021-42574 - Code generator Generate malicious files using recently published bidi-attack vulnerability, which was discovered in Unicode Specifica
A lightweight Python module to interact with the Mitre Att&ck Enterprise dataset.
enterpriseattack - Mitre's Enterprise Att&ck A lightweight Python module to interact with the Mitre Att&ck Enterprise dataset. Built to be used in pro
A (completely native) python3 wifi brute-force attack using the 100k most common passwords (2021)
wifi-bf [LINUX ONLY] A (completely native) python3 wifi brute-force attack using the 100k most common passwords (2021) This script is purely for educa
A python tool capable of creating HUGE wordlists. Has the ability to add custom words for concatenation in any way you see fit.
A python tool capable of creating HUGE wordlists. Has the ability to add custom words for concatenation in any way you see fit.
This is python script that will extract the functions call in all used DLL in an executable and then provide a mapping of those functions to the attack classes defined and curated malapi.io.
F2Amapper This is python script that will extract the functions call in all used DLL in an executable and then provide a mapping of those functions to
Generate malicious files using recently published homoglyphic-attack (CVE-2021-42694)
CVE-2021-42694 Generate malicious files using recently published homoglyph-attack vulnerability, which was discovered at least in C, C++, C#, Go, Pyth

Code for "Adversarial Attack Generation Empowered by Min-Max Optimization", NeurIPS 2021
Min-Max Adversarial Attacks [Paper] [arXiv] [Video] [Slide] Adversarial Attack Generation Empowered by Min-Max Optimization Jingkang Wang, Tianyun Zha
This program do translate english words to portuguese
Python-Dictionary This program is used to translate english words to portuguese. Web-Scraping This program use BeautifulSoap to make web scraping, so
🤕 spelling exceptions builder for lazy people
🤕 spelling exceptions builder for lazy people
json|dict to python object
Pyonize convert json|dict to python object Setup pip install pyonize Examples from pyonize import pyonize
Read API docs offline, CLI, supports DevDocs.io compatible JSON files
Read API docs offline, CLI, supports DevDocs.io compatible JSON files
D-dos attack GUI tool written in python using tkinter module
ddos D-dos attack GUI tool written in python using tkinter module #to use this tool on android, do the following on termux. *. apt update *. apt upgra

Brute Force Attack On Facebook Accounts
Brute Force Attack On Facebook Accounts For Install: pkg install update && pkg upgrade -y pkg install python pip install requests pip install mechani
A repository to spoof ARP table of any devices and successfully establish Man in the Middle(MITM) attack using Python3 in Linux
arp_spoofer A repository to spoof ARP table of any devices and successfully establish Man in the Middle(MITM) attack using Python3 in Linux Usage: git
A repository to detect the ARP spoofing in any devices and prevent Man in the Middle(MITM) attack using Python3
arp_spoof_detector A repository to detect the ARP spoofing in any devices and prevent Man in the Middle(MITM) attack using Python3 Usage: git clone ht
All in One CRACKER911181's Tool. This Tool For Hacking and Pentesting. 🎭
All in One CRACKER911181's Tool. This Tool For Hacking and Pentesting. 🎭
Dirty, ugly, and hopefully useful OCR of Facebook Papers docs released by Gizmodo
Quick and Dirty OCR of Facebook Papers Gizmodo has been working through the Facebook Papers and releasing the docs that they process and review. As lu

Attack on Confidence Estimation algorithm from the paper "Disrupting Deep Uncertainty Estimation Without Harming Accuracy"
Attack on Confidence Estimation (ACE) This repository is the official implementation of "Disrupting Deep Uncertainty Estimation Without Harming Accura
command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validation, attacker can exploit the vulnerability to launch a command injection attack by sending some messages with malicious commands.
CVE-2021-36260 CVE-2021-36260 POC command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validatio
This is a telegram bot built using the Oxford Dictionary API
Oxford Dictionaries Telegram Bot This is a telegram bot built using the Oxford Dictionary API Source: Oxford Dictionaries API Documentation Install En

A Proof-of-Concept Layer 2 Denial of Service Attack that disrupts low level operations of Programmable Logic Controllers within industrial environments. Utilizing multithreaded processing, Automator-Terminator delivers a powerful wave of spoofed ethernet packets to a null MAC address.
Automator-Terminator A Proof-of-Concept Layer 2 Denial of Service Attack that disrupts low level operations of Programmable Logic Controllers (PLCs) w
D(HE)ater is a security tool can perform DoS attack by enforcing the DHE key exchange.
D(HE)ater D(HE)ater is an attacking tool based on CPU heating in that it forces the ephemeral variant of Diffie-Hellman key exchange (DHE) in given cr

Bark Toolkit is a toolkit wich provides Denial-of-service attacks, SMS attacks and more.
Bark Toolkit About Bark Toolkit Bark Toolkit is a set of tools that provides denial of service attacks. Bark Toolkit includes SMS attack tool, HTTP
Dos attack a Bluetooth connection!
Bluetooth Denial of service Script made for attacking Bluetooth Devices By Samrat Katwal. Warning This project was created only for fun purposes and p
![Moiré Attack (MA): A New Potential Risk of Screen Photos [NeurIPS 2021]](https://github.com/Dantong88/Moire_Attack/raw/main/Images/Pipeline.png)
Moiré Attack (MA): A New Potential Risk of Screen Photos [NeurIPS 2021]
Moiré Attack (MA): A New Potential Risk of Screen Photos [NeurIPS 2021] This repository is the official implementation of Moiré Attack (MA): A New Pot
A modular framework for vision & language multimodal research from Facebook AI Research (FAIR)
MMF is a modular framework for vision and language multimodal research from Facebook AI Research. MMF contains reference implementations of state-of-t

Using machine learning to predict and analyze high and low reader engagement for New York Times articles posted to Facebook.
How The New York Times can increase Engagement on Facebook Using machine learning to understand characteristics of news content that garners "high" Fa
A simple Facebook Account generator, written in python (needs different Email so Accounts do not get banned)
FacebookAccountGenerator FAB is a Facebook-Account generating script, written in python Installation Use the package manager pip to install selenium p
PyMultiDictionary is a Dictionary Module for Python 3+ to get meanings, translations, synonyms and antonyms of words in 20 different languages
PyMultiDictionary PyMultiDictionary is a Dictionary Module for Python 3+ to get meanings, translations, synonyms and antonyms of words in 20 different
Membership Inference Attack against Graph Neural Networks
MIA GNN Project Starter If you meet the version mismatch error for Lasagne library, please use following command to upgrade Lasagne library. pip insta

Facebook AI Research Sequence-to-Sequence Toolkit written in Python.
Fairseq(-py) is a sequence modeling toolkit that allows researchers and developers to train custom models for translation, summarization, language mod

kikuchipy is an open-source Python library for processing and analysis of electron backscatter diffraction (EBSD) patterns
kikuchipy is an open-source Python library for processing and analysis of electron backscatter diffraction (EBSD) patterns. The library builds on the
Mini Tool to lovers of debe from eksisozluk (one of the most famous website -reffered as collaborative dictionary like reddit- in Turkey) for pushing debe (Most Liked Entries of Yesterday) to kindle every day via Github Actions.
debe to kindle Mini Tool to lovers of debe from eksisozluk (one of the most famous website -refered as collaborative dictionary like reddit- in Turkey
Get the length of the Instagram encrypted password
instagram-weak-encryption Get the length of the Instagram encrypted password Introduction Instagram and Facebook encrypt the password submitted at log

Brute force a JWT token. Script uses multithreading.
JWT BF Brute force a JWT token. Script uses multithreading. Tested on Kali Linux v2021.4 (64-bit). Made for educational purposes. I hope it will help!
this is demo of tool dosploit for test and dos in network with python
this tool for dos and pentest vul SKILLS: syn flood udp flood $ git clone https://github.com/amicheh/demo_dosploit/ $ cd demo_dosploit $ python3 -m pi
This is the repository for paper NEEDLE: Towards Non-invertible Backdoor Attack to Deep Learning Models.
This is the repository for paper NEEDLE: Towards Non-invertible Backdoor Attack to Deep Learning Models.
python code used to download all images contained in a facebook uid , the uid can be profile,group,fanpage
python code used to download all images contained in a facebook uid , the uid can be profile,group,fanpage
compact and speedy hash cracker for md5, sha1, and sha256 hashes
hash-cracker hash cracker is a multi-functional and compact...hash cracking tool...that supports dictionary attacks against three kinds of hashes: md5

This is the official code for the paper "Ad2Attack: Adaptive Adversarial Attack for Real-Time UAV Tracking".
Ad^2Attack:Adaptive Adversarial Attack on Real-Time UAV Tracking Demo video 📹 Our video on bilibili demonstrates the test results of Ad^2Attack on se
Send email notification when receiving Facebook message.
Send email notification when receiving Facebook message.
Accurately generate all possible forms of an English word e.g "election" -- "elect", "electoral", "electorate" etc.
Accurately generate all possible forms of an English word Word forms can accurately generate all possible forms of an English word. It can conjugate v

