500 Repositories
Python content-security-policy Libraries

Lazarus analysis tools and research report
Lazarus Research This repository publishes analysis reports and analysis tools for Operation Dream Job and Operation JTrack for Lazarus. Tools Python
Natas teaches the basics of serverside web-security.
over-the-wire-natas Natas teaches the basics of serverside web-security. Each level of natas consists of its own website located at http://natasX.nata

About Hive Burp Suite Extension
Hive Burp Suite Extension Description Hive extension for Burp Suite. This extension allows you to send data from Burp to Hive in one click. Create iss
GitHub action for AppSweep Mobile Application Security Testing
GitHub action for AppSweep can be used to continuously integrate app scanning using AppSweep into your Android app build process
Automated Content Feed Curator
Gathers posts from content feeds, filters, formats, delivers to you.

Training code and evaluation benchmarks for the "Self-Supervised Policy Adaptation during Deployment" paper.
Self-Supervised Policy Adaptation during Deployment PyTorch implementation of PAD and evaluation benchmarks from Self-Supervised Policy Adaptation dur

Blinder is a tool that will help you simplify the exploitation of blind SQL injection
Blinder Have you found a blind SQL injection? Great! Now you need to export it, but are you too lazy to sort through the values? Most likely,

An encryption format offering better security, performance and ease of use than PGP.
An encryption format offering better security, performance and ease of use than PGP. File a bug if you found anything where we are worse than our competition, and we will fix it.

Moodle community-based vulnerability scanner
badmoodle Moodle community-based vulnerability scanner Description badmoodle is an unofficial community-based vulnerability scanner for moodle that sc

A Python package for causal inference using Synthetic Controls
Synthetic Control Methods A Python package for causal inference using synthetic controls This Python package implements a class of approaches to estim
A Simple Python CLI Lockpicking Tool
Cryptex a simple CLI lockpicking tool What can it do: Encode / Decode Hex Encode / Decode Base64 Break Randomly :D Requirements: Python3 Linux as your

🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.
🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.
Unsupervised clustering of high content screen samples
Microscopium Unsupervised clustering and dataset exploration for high content screens. See microscopium in action Public dataset BBBC021 from the Broa

This script runs neural style transfer against the provided content image.
Neural Style Transfer Content Style Output Description: This script runs neural style transfer against the provided content image. The content image m
Multiple implementations for abstractive text summurization , using google colab
Text Summarization models if you are able to endorse me on Arxiv, i would be more than glad https://arxiv.org/auth/endorse?x=FRBB89 thanks This repo i
A Python module for clustering creators of social media content into networks
sm_content_clustering A Python module for clustering creators of social media content into networks. Currently supports identifying potential networks

Spray365 is a password spraying tool that identifies valid credentials for Microsoft accounts (Office 365 / Azure AD).
What is Spray365? Spray365 is a password spraying tool that identifies valid credentials for Microsoft accounts (Office 365 / Azure AD). How is Spray3
Multi-modal Content Creation Model Training Infrastructure including the FACT model (AI Choreographer) implementation.
AI Choreographer: Music Conditioned 3D Dance Generation with AIST++ [ICCV-2021]. Overview This package contains the model implementation and training

Editor and Presenter for Manim Generated Content.
Editor and Presenter for Manim Generated Content. Take a look at the Working Example. More information can be found on the documentation. These Browse

Implementation of Sequence Generative Adversarial Nets with Policy Gradient
SeqGAN Requirements: Tensorflow r1.0.1 Python 2.7 CUDA 7.5+ (For GPU) Introduction Apply Generative Adversarial Nets to generating sequences of discre

MoCoGAN: Decomposing Motion and Content for Video Generation
MoCoGAN: Decomposing Motion and Content for Video Generation This repository contains an implementation and further details of MoCoGAN: Decomposing Mo
Multi-Content GAN for Few-Shot Font Style Transfer at CVPR 2018
MC-GAN in PyTorch This is the implementation of the Multi-Content GAN for Few-Shot Font Style Transfer. The code was written by Samaneh Azadi. If you
Encrypted Python Password Manager
PyPassKeep Encrypted Python Password Manager About PyPassKeep (PPK for short) is an encrypted python password manager used to secure your passwords fr

ChainJacking is a tool to find which of your Go lang direct GitHub dependencies is susceptible to ChainJacking attack.
ChainJacking is a tool to find which of your Go lang direct GitHub dependencies is susceptible to ChainJacking attack.
A tool that updates all your project's Python dependency files through Pull Requests on GitHub/GitLab.
A tool that updates all your project's Python dependency files through Pull Requests on GitHub/GitLab. About This repo contains the bot that is runnin

Fast and customizable vulnerability scanner For JIRA written in Python
Fast and customizable vulnerability scanner For JIRA. 🤔 What is this? Jira-Lens 🔍 is a Python Based vulnerability Scanner for JIRA. Jira is a propri
Python script for changing the SSH banner content with other content
Banner-changer-py Python script for changing the SSH banner content with other content. The Script will take the content of a specified file range and

A Python Tool to encrypt all types of files using AES and XOR Algorithm.
DataShield This project intends to protect user’s data, it stores files in encrypted format in device provided the passcode and path of the file. AES

MagTape is a Policy-as-Code tool for Kubernetes that allows for evaluating Kubernetes resources against a set of defined policies to inform and enforce best practice configurations.
MagTape is a Policy-as-Code tool for Kubernetes that allows for evaluating Kubernetes resources against a set of defined policies to inform and enforce best practice configurations. MagTape includes variable policy enforcement, notifications, and targeted metrics.

Self-Supervised Learning with Data Augmentations Provably Isolates Content from Style
Self-Supervised Learning with Data Augmentations Provably Isolates Content from Style [NeurIPS 2021] Official code to reproduce the results and data p
Course: Information Security with Python
Curso: Segurança da Informação com Python Curso realizado atravès da Plataforma da Digital Innovation One Prof: Bruno Dias Conteúdo: Introdução aos co

A Security Tool for Enumerating WebSockets
STEWS: Security Testing and Enumeration of WebSockets STEWS is a tool suite for security testing of WebSockets This research was first presented at OW
Distinguishing Commercial from Editorial Content in News
Distinguishing Commercial from Editorial Content in News In this repository you can find the following: An anonymized version of the data used for my

Gym environments used in the paper: "Developmental Reinforcement Learning of Control Policy of a Quadcopter UAV with Thrust Vectoring Rotors"
gym_multirotor Gym to train reinforcement learning agents on UAV platforms Quadrotor Tiltrotor Requirements This package has been tested on Ubuntu 18.

Safe Policy Optimization with Local Features
Safe Policy Optimization with Local Feature (SPO-LF) This is the source-code for implementing the algorithms in the paper "Safe Policy Optimization wi
6D Grasping Policy for Point Clouds
GA-DDPG [website, paper] Installation git clone https://github.com/liruiw/GA-DDPG.git --recursive Setup: Ubuntu 16.04 or above, CUDA 10.0 or above, py

Safe Policy Optimization with Local Features
Safe Policy Optimization with Local Feature (SPO-LF) This is the source-code for implementing the algorithms in the paper "Safe Policy Optimization wi

Code for "Adversarial attack by dropping information." (ICCV 2021)
AdvDrop Code for "AdvDrop: Adversarial Attack to DNNs by Dropping Information(ICCV 2021)." Human can easily recognize visual objects with lost informa

Members: Thomas Longuevergne Program: Network Security Course: 1DV501 Date of submission: 2021-11-02
Mini-project report Members: Thomas Longuevergne Program: Network Security Course: 1DV501 Date of submission: 2021-11-02 Introduction This project was
VaporCMS - The greatest content management system that will never exist
The greatest content management system that will never exist Overview WordPress is a huge success but could it be done better? Maybe being mo
Security System using OpenCV
Security-System Security System using OpenCV Files in this Repository: email_send.py - This file contains python code to send an email when something

Security evaluation module with onnx, pytorch, and SecML.
🚀 🐼 🔥 PandaVision Integrate and automate security evaluations with onnx, pytorch, and SecML! Installation Starting the server without Docker If you
Use scrapli to retrieve security zone information from a Juniper SRX firewall
Get Security Zones with Scrapli Overview This example will show how to retrieve security zone information on Juniper's SRX firewalls. In addition to t
Arp Spoofer using Python 3.
ARP Spoofer / Wifi Killer By Auax Run: Run the application with the following command: python3 spoof.py -t target_ip_address -lh host_ip_address I
Arp Spoofer using Python 3.
ARP Spoofer / Wifi Killer By Auax Run: Run the application with the following command: python3 spoof.py -t target_ip_address -lh host_ip_address I
Filtering user-generated video content(SberZvukTechDays)Filtering user-generated video content(SberZvukTechDays)
Filtering user-generated video content(SberZvukTechDays) Table of contents General info Team members Technologies Setup Result General info This is a

A package for "Procedural Content Generation via Reinforcement Learning" OpenAI Gym interface.
Readme: Illuminating Diverse Neural Cellular Automata for Level Generation This is the codebase used to generate the results presented in the paper av

Automated GitHub profile content using the USGS API, Plotly and GitHub Actions.
Top 20 Largest Earthquakes in the Past 24 Hours Location Mag Date and Time (UTC) 92 km SW of Sechura, Peru 5.2 11-05-2021 23:19:50 113 km NNE of Lobuj
gwcheck is a tool to check .gnu.warning.* sections in ELF object files and display their content.
gwcheck Description gwcheck is a tool to check .gnu.warning.* sections in ELF object files and display their content. For an introduction to .gnu.warn
🍉一款基于Python-Django的多功能Web安全渗透测试工具,包含漏洞扫描,端口扫描,指纹识别,目录扫描,旁站扫描,域名扫描等功能。
Sec-Tools 项目介绍 系统简介 本项目命名为Sec-Tools,是一款基于 Python-Django 的在线多功能 Web 应用渗透测试系统,包含漏洞检测、目录识别、端口扫描、指纹识别、域名探测、旁站探测、信息泄露检测等功能。本系统通过旁站探测和域名探测功能对待检测网站进行资产收集,通过端
A simple python program to record security cam footage by detecting a face and body of a person in the frame.
SecurityCam A simple python program to record security cam footage by detecting a face and body of a person in the frame. This code was created by me,
Trains an agent with stochastic policy gradient ascent to solve the Lunar Lander challenge from OpenAI
Introduction This script trains an agent with stochastic policy gradient ascent to solve the Lunar Lander challenge from OpenAI. In order to run this
This tool parses log data and allows to define analysis pipelines for anomaly detection.
logdata-anomaly-miner This tool parses log data and allows to define analysis pipelines for anomaly detection. It was designed to run the analysis wit
GitGuardian Shield: protect your secrets with GitGuardian
Detect secret in source code, scan your repo for leaks. Find secrets with GitGuardian and prevent leaked credentials. GitGuardian is an automated secrets detection & remediation service.
Demo content - Automate your automation!
Automate-AAP2 Demo Content - Automate your automation! A fully automated Ansible Automation Platform. Context Installing and configuring Ansible Autom

This tool allows to automatically test for Content Security Policy bypass payloads.
CSPass This tool allows to automatically test for Content Security Policy bypass payloads. Usage [cspass]$ ./cspass.py -h usage: cspass.py [-h] [--no-
A lightweight Python module to interact with the Mitre Att&ck Enterprise dataset.
enterpriseattack - Mitre's Enterprise Att&ck A lightweight Python module to interact with the Mitre Att&ck Enterprise dataset. Built to be used in pro
A (completely native) python3 wifi brute-force attack using the 100k most common passwords (2021)
wifi-bf [LINUX ONLY] A (completely native) python3 wifi brute-force attack using the 100k most common passwords (2021) This script is purely for educa
Tools to assist with the configuration and maintenance of fapolicyd.
Tools to assist with the configuration and maintenance of fapolicyd.
Generalized Proximal Policy Optimization with Sample Reuse (GePPO)
Generalized Proximal Policy Optimization with Sample Reuse This repository is the official implementation of the reinforcement learning algorithm Gene
A facial recognition program that plays a alarm (mp3 file) when a person i seen in the room. A basic theif using Python and OpenCV
Home-Security-Demo A facial recognition program that plays a alarm (mp3 file) when a person is seen in the room. A basic theif using Python and OpenCV
ICMP Reverse Shell written in Python 3 and with Scapy (backdoor/rev shell)
icmpdoor - ICMP Reverse Shell icmpdoor is an ICMP rev shell written in Python3 and scapy. Tested on Ubuntu 20.04, Debian 10 (Kali Linux), and Windows
Scrapy-based cyber security news finder
Cyber-Security-News-Scraper Scrapy-based cyber security news finder Goal To keep up to date on the constant barrage of information within the field of
A python open source CMS scanner that automates the process of detecting security flaws of the most popular CMSs
CMSmap CMSmap is a python open source CMS scanner that automates the process of detecting security flaws of the most popular CMSs. The main purpose of

Pytorch Implementation of "Diagonal Attention and Style-based GAN for Content-Style disentanglement in image generation and translation" (ICCV 2021)
DiagonalGAN Official Pytorch Implementation of "Diagonal Attention and Style-based GAN for Content-Style Disentanglement in Image Generation and Trans

🔥 Real-time Super Resolution enhancement (4x) with content loss and relativistic adversarial optimization 🔥
🔥 Real-time Super Resolution enhancement (4x) with content loss and relativistic adversarial optimization 🔥
Short PhD seminar on Machine Learning Security (Adversarial Machine Learning)
Short PhD seminar on Machine Learning Security (Adversarial Machine Learning)
[NeurIPS 2021] Official implementation of paper "Learning to Simulate Self-driven Particles System with Coordinated Policy Optimization".
Code for Coordinated Policy Optimization Webpage | Code | Paper | Talk (English) | Talk (Chinese) Hi there! This is the source code of the paper “Lear
Structural Constraints on Information Content in Human Brain States
Structural Constraints on Information Content in Human Brain States Code accompanying the paper "The information content of brain states is explained
Discord-Protect is a simple discord bot allowing you to have some security on your discord server by ordering a captcha to the user who joins your server.
Discord-Protect Discord-Protect is a simple discord bot allowing you to have some security on your discord server by ordering a captcha to the user wh

AutoExploitSwagger is an automated API security testing exploit tool that can be combined with xray, BurpSuite and other scanners.
AutoExploitSwagger is an automated API security testing exploit tool that can be combined with xray, BurpSuite and other scanners.

Security tool to test different bypass of forbidden
notForbidden Security tool to test different bypass of forbidden Usage python3 notForbidden.py URL Features Bypass with different methods (POST, OPT

An implementation of the proximal policy optimization algorithm
PPO Pytorch C++ This is an implementation of the proximal policy optimization algorithm for the C++ API of Pytorch. It uses a simple TestEnvironment t

PyTorch implementation of Advantage Actor Critic (A2C), Proximal Policy Optimization (PPO), Scalable trust-region method for deep reinforcement learning using Kronecker-factored approximation (ACKTR) and Generative Adversarial Imitation Learning (GAIL).
PyTorch implementation of Advantage Actor Critic (A2C), Proximal Policy Optimization (PPO), Scalable trust-region method for deep reinforcement learning using Kronecker-factored approximation (ACKTR) and Generative Adversarial Imitation Learning (GAIL).

Off-policy continuous control in PyTorch, with RDPG, RTD3 & RSAC
arXiv technical report soon available. we are updating the readme to be as comprehensive as possible Please ask any questions in Issues, thanks. Intro
Set the draft security HTTP header Permissions-Policy (previously Feature-Policy) on your Django app.
django-permissions-policy Set the draft security HTTP header Permissions-Policy (previously Feature-Policy) on your Django app. Requirements Python 3.

An extension to detect if the articles content match its title.
Clickbait Detector An extension to detect if the articles content match its title. This was developed in a period of 24-hours in a hackathon called 'H
Time Discretization-Invariant Safe Action Repetition for Policy Gradient Methods
Time Discretization-Invariant Safe Action Repetition for Policy Gradient Methods This repository is the official implementation of Seohong Park, Jaeky
Enrich IP addresses with metadata and security IoC
Stratosphere IP enrich Get an IP address and enrich it with metadata and IoC You need API keys for VirusTotal and PassiveTotal (RiskIQ) How to use fro
BinCat is an innovative login system, with which the account you register will be more secure.
BinCat is an innovative login system, with which the account you register will be more secure. This project is inspired by a conventional token system.
External Network Pentest Automation using Shodan API and other tools.
Chopin External Network Pentest Automation using Shodan API and other tools. Workflow Input a file containing CIDR ranges. Converts CIDR ranges to ind
D(HE)ater is a security tool can perform DoS attack by enforcing the DHE key exchange.
D(HE)ater D(HE)ater is an attacking tool based on CPU heating in that it forces the ephemeral variant of Diffie-Hellman key exchange (DHE) in given cr

The ibet-Prime security token management system for ibet network.
ibet-Prime The ibet-Prime security token management system for ibet network. Features ibet-Prime is an API service that enables the issuance and manag
Data for "Driving the Herd: Search Engines as Content Influencers" paper
herding_data Data for "Driving the Herd: Search Engines as Content Influencers" paper Dataset description The collection contains 2250 documents, 30 i
MBPO (paper: When to trust your model: Model-based policy optimization) in offline RL settings
offline-MBPO This repository contains the code of a version of model-based RL algorithm MBPO, which is modified to perform in offline RL settings Pape
Deep Reinforcement Learning by using an on-policy adaptation of Maximum a Posteriori Policy Optimization (MPO)
V-MPO Simple code to demonstrate Deep Reinforcement Learning by using an on-policy adaptation of Maximum a Posteriori Policy Optimization (MPO) in Pyt
Security offerings for AWS Control Tower
Caylent Security Catalyst Reference Architecture Examples This repository contains solutions for Caylent's Security Catalyst. The Security Catalyst is

Official PyTorch implementation of "Edge Rewiring Goes Neural: Boosting Network Resilience via Policy Gradient".
Edge Rewiring Goes Neural: Boosting Network Resilience via Policy Gradient This repository is the official PyTorch implementation of "Edge Rewiring Go

PyTorch implementation of Constrained Policy Optimization
PyTorch implementation of Constrained Policy Optimization (CPO) This repository has a simple to understand and use implementation of CPO in PyTorch. A
A CLI tool to disable and enable security standards controls in AWS Security Hub
Security Hub Controls CLI A CLI tool to disable and enable security standards controls in AWS Security Hub. It is designed to work together with AWS S
Audio Steganography is a technique used to transmit hidden information by modifying an audio signal in an imperceptible manner.
Audio Steganography Audio Steganography is a technique used to transmit hidden information by modifying an audio signal in an imperceptible manner. Ab
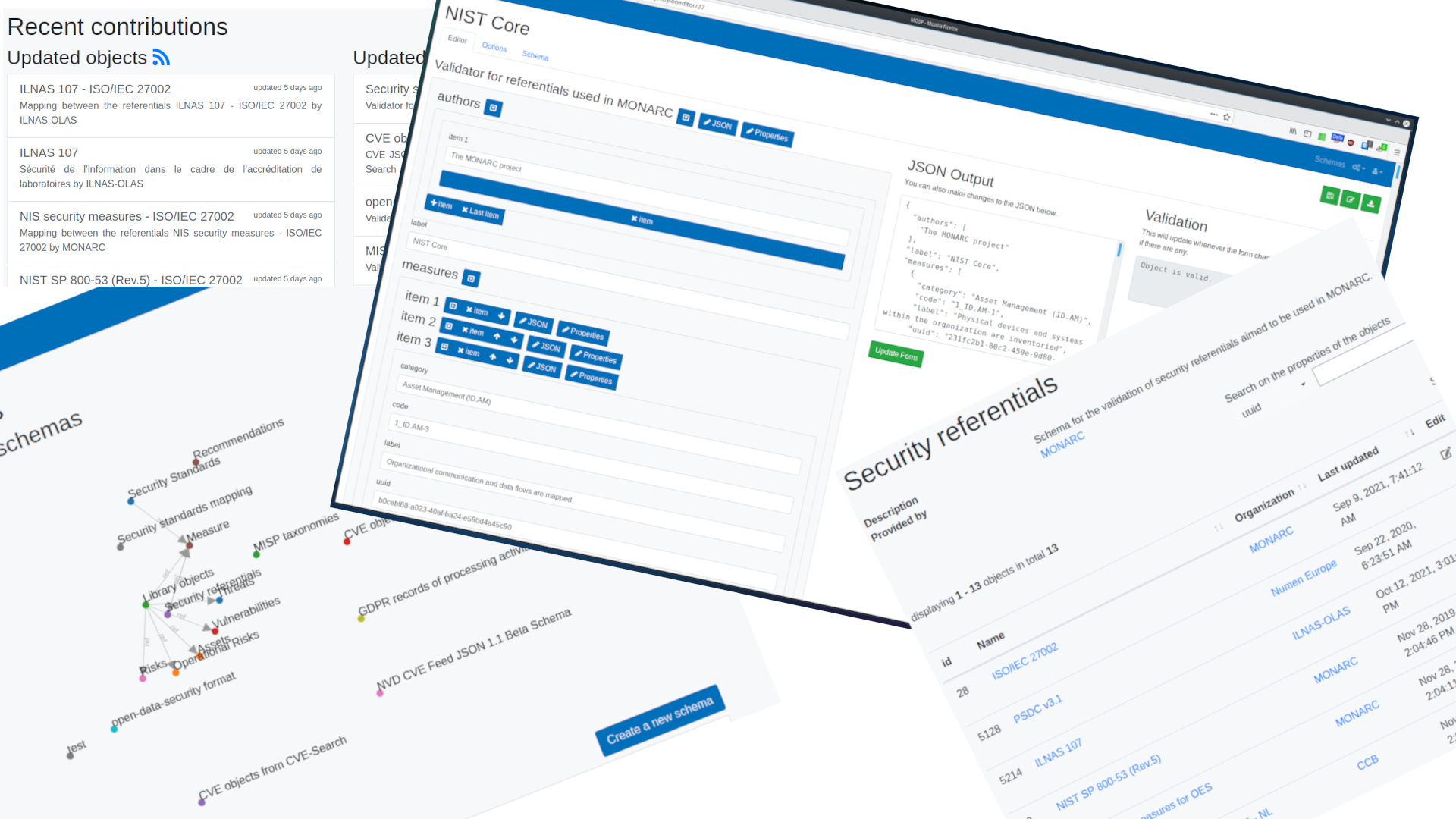
MOSP is a platform for creating, editing and sharing validated JSON objects of any type.
MONARC Objects Sharing Platform Presentation MOSP is a platform for creating, editing and sharing validated JSON objects of any type. You can use any

Brute force a JWT token. Script uses multithreading.
JWT BF Brute force a JWT token. Script uses multithreading. Tested on Kali Linux v2021.4 (64-bit). Made for educational purposes. I hope it will help!
ProMP: Proximal Meta-Policy Search
ProMP: Proximal Meta-Policy Search Implementations corresponding to ProMP (Rothfuss et al., 2018). Overall this repository consists of two branches: m

boofuzz: Network Protocol Fuzzing for Humans
boofuzz: Network Protocol Fuzzing for Humans Boofuzz is a fork of and the successor to the venerable Sulley fuzzing framework. Besides numerous bug fi

Passhunt is a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords.
Passhunt is a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords.
API to parse tibia.com content into python objects.
Tibia.py An API to parse Tibia.com content into object oriented data. No fetching is done by this module, you must provide the html content. Features:

The core packages of security analyzer web crawler
Security Analyzer 🐍 A large scale web crawler (considered also as vulnerability scanner tool) to take an overview about security of Moroccan sites Cu
CAPITAL: Optimal Subgroup Identification via Constrained Policy Tree Search
CAPITAL: Optimal Subgroup Identification via Constrained Policy Tree Search This repository is the official implementation of CAPITAL: Optimal Subgrou
