289 Repositories
Python cve-2019-17558 Libraries

Deep Anomaly Detection with Outlier Exposure (ICLR 2019)
Outlier Exposure This repository contains the essential code for the paper Deep Anomaly Detection with Outlier Exposure (ICLR 2019). Requires Python 3
Official PyTorch implementation of "Camera Distance-aware Top-down Approach for 3D Multi-person Pose Estimation from a Single RGB Image", ICCV 2019
PoseNet of "Camera Distance-aware Top-down Approach for 3D Multi-person Pose Estimation from a Single RGB Image" Introduction This repo is official Py

Using / reproducing ACD from the paper "Hierarchical interpretations for neural network predictions" 🧠 (ICLR 2019)
Hierarchical neural-net interpretations (ACD) 🧠 Produces hierarchical interpretations for a single prediction made by a pytorch neural network. Offic
A Fast and Accurate One-Stage Approach to Visual Grounding, ICCV 2019 (Oral)
One-Stage Visual Grounding ***** New: Our recent work on One-stage VG is available at ReSC.***** A Fast and Accurate One-Stage Approach to Visual Grou
Universal Adversarial Triggers for Attacking and Analyzing NLP (EMNLP 2019)
Universal Adversarial Triggers for Attacking and Analyzing NLP This is the official code for the EMNLP 2019 paper, Universal Adversarial Triggers for

A Pytorch implementation of "Splitter: Learning Node Representations that Capture Multiple Social Contexts" (WWW 2019).
Splitter ⠀⠀ A PyTorch implementation of Splitter: Learning Node Representations that Capture Multiple Social Contexts (WWW 2019). Abstract Recent inte
In this repository we have tested 3 VQA models on the ImageCLEF-2019 dataset.
Med-VQA In this repository we have tested 3 VQA models on the ImageCLEF-2019 dataset. Two of these are made on top of Facebook AI Reasearch's Multi-Mo

Proof on Concept Exploit for CVE-2021-38647 (OMIGOD)
OMIGOD Proof on Concept Exploit for CVE-2021-38647 (OMIGOD) For background information and context, read the our blog post detailing this vulnerabilit

CVE-2021-40346 integer overflow enables http smuggling
CVE-2021-40346-POC CVE-2021-40346 integer overflow enables http smuggling Reference: https://jfrog.com/blog/critical-vulnerability-in-haproxy-cve-2021
nuclei scanner for proxyshell ( CVE-2021-34473 )
Proxyshell-Scanner nuclei scanner for Proxyshell RCE (CVE-2021-34423,CVE-2021-34473,CVE-2021-31207) discovered by orange tsai in Pwn2Own, which affect

Dynamic Multi-scale Filters for Semantic Segmentation (DMNet ICCV'2019)
Dynamic Multi-scale Filters for Semantic Segmentation (DMNet ICCV'2019) Introduction Official implementation of Dynamic Multi-scale Filters for Semant
Cobalt Strike 4.4 dos CVE-2021-36798
CVE-2021-36798 CVE-2021-36798 Cobalt Strike 4.3 dos 用法 python3 CVE-2021-36798.py BeaconURL 打瘫Cobalt Strike 只需要一个包 已测试 4.3 4.2 参考: https://labs.sent

This repo contain builders of cab file, html file, and docx file for CVE-2021-40444 exploit
CVE-2021-40444 builders This repo contain builders of cab file, html file, and docx file for CVE-2021-40444 exploit. This repo is just for testing, re
Confluence OGNL injection
CVE-2021-26084 Confluence OGNL injection CVE-2021-26084 is an Object-Graph Navigation Language (OGNL) injection vulnerability in the Atlassian Conflue

CVE-2021-26084 Remote Code Execution on Confluence Servers
CVE-2021-26084 CVE-2021-26084 Remote Code Execution on Confluence Servers. Dork Fofa: app="ATLASSIAN-Confluence" Usage Show help information. python P
A Python replicated exploit for Webmin 1.580 /file/show.cgi Remote Code Execution
CVE-2012-2982 John Hammond | September 4th, 2021 Checking searchsploit for Webmin 1.580 I only saw a Metasploit module for the /file/show.cgi Remote C
CVE-2021-36798 Exp: Cobalt Strike 4.4 Dos
A denial of service (DoS) vulnerability (CVE-2021-36798) was found in Cobalt Strike. The vulnerability was fixed in the scope of the 4.4 release. More

CVE-2021-26084 - Confluence Pre-Auth RCE OGNL injection
CVE-2021-26084 - Confluence Pre-Auth RCE OGNL injection Usage usage: cve-2021-26084_confluence_rce.py [-h] --url URL [--cmd CMD] [--shell] CVE-2021-2

Adaptive Pyramid Context Network for Semantic Segmentation (APCNet CVPR'2019)
Adaptive Pyramid Context Network for Semantic Segmentation (APCNet CVPR'2019) Introduction Official implementation of Adaptive Pyramid Context Network
This is the writeup of all the challenges from Advent-of-cyber-2019 of TryHackMe
Advent-of-cyber-2019-writeup This is the writeup of all the challenges from Advent-of-cyber-2019 of TryHackMe https://tryhackme.com/shivam007/badges/c
Strapi Framework Vulnerable to Remote Code Execution
CVE-2019-19609 Strapi Framework Vulnerable to Remote Code Execution well, I didnt found any exploit for CVE-2019-19609 so I wrote one. :/ Usage pytho

The source code of CVPR 2019 paper "Deep Exemplar-based Video Colorization".
Deep Exemplar-based Video Colorization (Pytorch Implementation) Paper | Pretrained Model | Youtube video 🔥 | Colab demo Deep Exemplar-based Video Col
Automatic ProxyShell Exploit
proxyshell-auto usage: proxyshell.py [-h] -t T Automatic Exploit ProxyShell optional arguments: -h, --help show this help message and exit -t T

Implementation detail for paper "Multi-level colonoscopy malignant tissue detection with adversarial CAC-UNet"
Multi-level-colonoscopy-malignant-tissue-detection-with-adversarial-CAC-UNet Implementation detail for our paper "Multi-level colonoscopy malignant ti

Accurate 3D Face Reconstruction with Weakly-Supervised Learning: From Single Image to Image Set (CVPRW 2019). A PyTorch implementation.
Accurate 3D Face Reconstruction with Weakly-Supervised Learning: From Single Image to Image Set —— PyTorch implementation This is an unofficial offici

A PyTorch implementation of "Graph Wavelet Neural Network" (ICLR 2019)
Graph Wavelet Neural Network ⠀⠀ A PyTorch implementation of Graph Wavelet Neural Network (ICLR 2019). Abstract We present graph wavelet neural network

A PyTorch implementation of "SimGNN: A Neural Network Approach to Fast Graph Similarity Computation" (WSDM 2019).
SimGNN ⠀⠀⠀ A PyTorch implementation of SimGNN: A Neural Network Approach to Fast Graph Similarity Computation (WSDM 2019). Abstract Graph similarity s

A PyTorch implementation of "Predict then Propagate: Graph Neural Networks meet Personalized PageRank" (ICLR 2019).
APPNP ⠀ A PyTorch implementation of Predict then Propagate: Graph Neural Networks meet Personalized PageRank (ICLR 2019). Abstract Neural message pass

An implementation of "MixHop: Higher-Order Graph Convolutional Architectures via Sparsified Neighborhood Mixing" (ICML 2019).
MixHop and N-GCN ⠀ A PyTorch implementation of "MixHop: Higher-Order Graph Convolutional Architectures via Sparsified Neighborhood Mixing" (ICML 2019)

A Pytorch implementation of "Splitter: Learning Node Representations that Capture Multiple Social Contexts" (WWW 2019).
Splitter ⠀⠀ A PyTorch implementation of Splitter: Learning Node Representations that Capture Multiple Social Contexts (WWW 2019). Abstract Recent inte

A PyTorch implementation of "Capsule Graph Neural Network" (ICLR 2019).
CapsGNN ⠀⠀ A PyTorch implementation of Capsule Graph Neural Network (ICLR 2019). Abstract The high-quality node embeddings learned from the Graph Neur

Send CVE information to the specified mailbox (from Github)
Send CVE information to the specified mailbox (from Github)

A PyTorch implementation of "Semi-Supervised Graph Classification: A Hierarchical Graph Perspective" (WWW 2019)
SEAL ⠀⠀⠀ A PyTorch implementation of Semi-Supervised Graph Classification: A Hierarchical Graph Perspective (WWW 2019) Abstract Node classification an

A PyTorch implementation of "Cluster-GCN: An Efficient Algorithm for Training Deep and Large Graph Convolutional Networks" (KDD 2019).
ClusterGCN ⠀⠀ A PyTorch implementation of "Cluster-GCN: An Efficient Algorithm for Training Deep and Large Graph Convolutional Networks" (KDD 2019). A
STEAL - Learning Semantic Boundaries from Noisy Annotations (CVPR 2019)
STEAL This is the official inference code for: Devil Is in the Edges: Learning Semantic Boundaries from Noisy Annotations David Acuna, Amlan Kar, Sanj
Universal Adversarial Triggers for Attacking and Analyzing NLP (EMNLP 2019)
Universal Adversarial Triggers for Attacking and Analyzing NLP This is the official code for the EMNLP 2019 paper, Universal Adversarial Triggers for
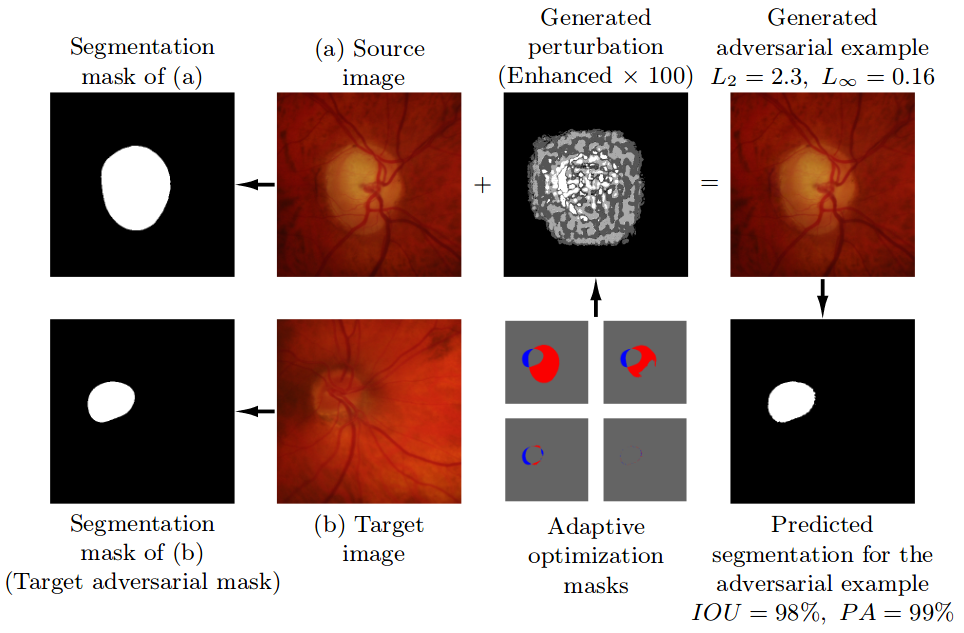
Pre-trained model, code, and materials from the paper "Impact of Adversarial Examples on Deep Learning Models for Biomedical Image Segmentation" (MICCAI 2019).
Adaptive Segmentation Mask Attack This repository contains the implementation of the Adaptive Segmentation Mask Attack (ASMA), a targeted adversarial
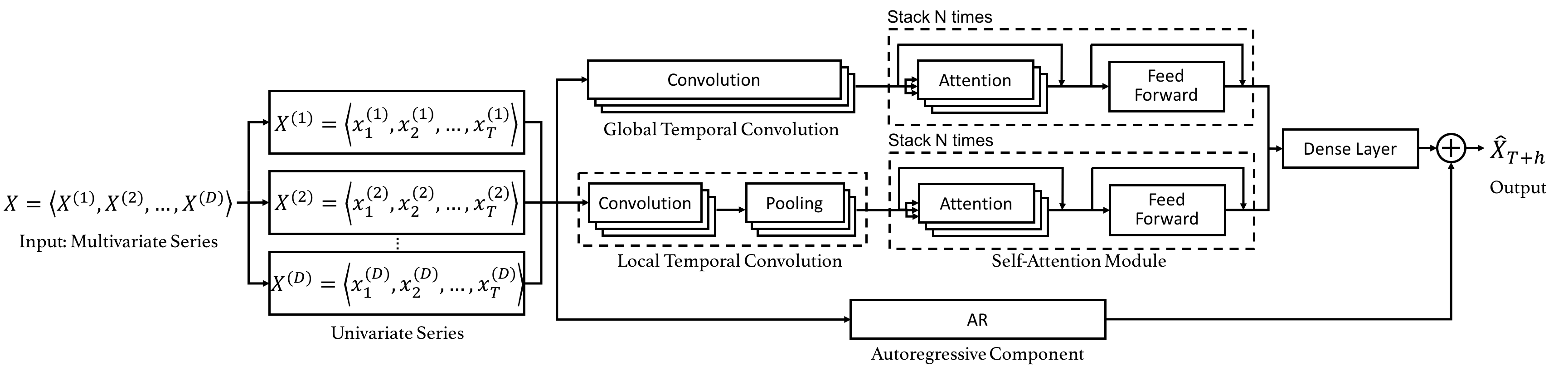
Code for the CIKM 2019 paper "DSANet: Dual Self-Attention Network for Multivariate Time Series Forecasting".
Dual Self-Attention Network for Multivariate Time Series Forecasting 20.10.26 Update: Due to the difficulty of installation and code maintenance cause
Argument Injection in Dragonfly Ruby Gem
CVE-2021-33564 PoC Exploit script for CVE-2021-33564 (Argument Injection in Dragonfly Ruby Gem). Usage Arbitrary File Read python3 poc.py -u https://

Privilege escalation with polkit - CVE-2021-3560
Polkit-exploit - CVE-2021-3560 Privilege escalation with polkit - CVE-2021-3560 Summary CVE-2021-3560 is an authentication bypass on polkit, which all
Polkit - Local Privilege Escalation (CVE-2021-3560)
CVE-2021-3560 Polkit - Local Privilege Escalation Original discovery by kevin_backhouse from GitHub Security Lab References https://github.blog/2021-0

Receive notifications/alerts on the most recent disclosed CVE's.
Receive notifications on the most recent disclosed CVE's.

BuddyPress is an open source WordPress plugin to build a community site. In releases of BuddyPress from 5.0.0 before 7.2.1 it's possible for a non-privileged, regular user to obtain administrator rights by exploiting an issue in the REST API members endpoint. The vulnerability has been fixed in BuddyPress 7.2.1. Existing installations of the plugin should be updated to this version to mitigate the issue.
CVE-2021-21389 BuddyPress 7.2.1 - REST API Privilege Escalation to RCE PoC (Full) Affected version: 5.0.0 to 7.2.0 User requirement: Subscriber user
Pre-Auth Blind NoSQL Injection leading to Remote Code Execution in Rocket Chat 3.12.1
CVE-2021-22911 Pre-Auth Blind NoSQL Injection leading to Remote Code Execution in Rocket Chat 3.12.1 The getPasswordPolicy method is vulnerable to NoS
Unsafe Twig processing of static pages leading to RCE in Grav CMS 1.7.10
CVE-2021-29440 Unsafe Twig processing of static pages leading to RCE in Grav CMS 1.7.10 Grav is a file based Web-platform. Twig processing of static p

CVE-2021-21985 VMware vCenter Server远程代码执行漏洞 EXP (更新可回显EXP)
CVE-2021-21985 CVE-2021-21985 EXP 本文以及工具仅限技术分享,严禁用于非法用途,否则产生的一切后果自行承担。 0x01 利用Tomcat RMI RCE 1. VPS启动JNDI监听 1099 端口 rmi需要bypass高版本jdk java -jar JNDIIn

cve-2021-21985 exploit
cve-2021-21985 exploit 0x01 漏洞点 分析可见: https://attackerkb.com/topics/X85GKjaVER/cve-2021-21985?referrer=home#rapid7-analysis 0x02 exploit 对beans对象进行重新构
This Repo is the official CUDA implementation of ICCV 2019 Oral paper for CARAFE: Content-Aware ReAssembly of FEatures
Introduction This Repo is the official CUDA implementation of ICCV 2019 Oral paper for CARAFE: Content-Aware ReAssembly of FEatures. @inproceedings{Wa
Official repository for Jia, Raghunathan, Göksel, and Liang, "Certified Robustness to Adversarial Word Substitutions" (EMNLP 2019)
Certified Robustness to Adversarial Word Substitutions This is the official GitHub repository for the following paper: Certified Robustness to Adversa
聚合Github上已有的Poc或者Exp,CVE信息来自CVE官网。Auto Collect Poc Or CVE from Github by CVE ID.
PocOrExp in Github 聚合Github上已有的Poc或者Exp,CVE信息来自CVE官网 注意:只通过通用的CVE号聚合,因此对于MS17-010等Windows编号漏洞以及著名的有绰号的漏洞,还是自己检索一下比较好 Usage python3 exp.py -h usage: ex
Apache Solr SSRF(CVE-2021-27905)
Solr-SSRF Apache Solr SSRF #Use [-] Apache Solr SSRF漏洞 (CVE-2021-27905) [-] Options: -h or --help : 方法说明 -u or --url

Image-Scaling Attacks and Defenses
Image-Scaling Attacks & Defenses This repository belongs to our publication: Erwin Quiring, David Klein, Daniel Arp, Martin Johns and Konrad Rieck. Ad
Apache OFBiz rmi反序列化EXP(CVE-2021-26295)
Apache OFBiz rmi反序列化EXP(CVE-2021-26295) 目前仅支持nc弹shell 将ysoserial.jar放置在同目录下,py3运行,根据提示输入漏洞url,你的vps地址和端口 第二次使用建议删除exp.ot 本工具仅用于安全测试,禁止未授权非法攻击站点,否则后果自负

Proof of concept for CVE-2021-24086, a NULL dereference in tcpip.sys triggered remotely.
CVE-2021-24086 This is a proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability "), a NULL dereference in tcpip.sys patc
《Single Image Reflection Removal Beyond Linearity》(CVPR 2019)
Single-Image-Reflection-Removal-Beyond-Linearity Paper Single Image Reflection Removal Beyond Linearity. Qiang Wen, Yinjie Tan, Jing Qin, Wenxi Liu, G
《Deep Single Portrait Image Relighting》(ICCV 2019)
Ratio Image Based Rendering for Deep Single-Image Portrait Relighting [Project Page] This is part of the Deep Portrait Relighting project. If you find

《A-CNN: Annularly Convolutional Neural Networks on Point Clouds》(2019)
A-CNN: Annularly Convolutional Neural Networks on Point Clouds Created by Artem Komarichev, Zichun Zhong, Jing Hua from Department of Computer Science
pip install antialiased-cnns to improve stability and accuracy
Antialiased CNNs [Project Page] [Paper] [Talk] Making Convolutional Networks Shift-Invariant Again Richard Zhang. In ICML, 2019. Quick & easy start Ru
Code for: Gradient-based Hierarchical Clustering using Continuous Representations of Trees in Hyperbolic Space. Nicholas Monath, Manzil Zaheer, Daniel Silva, Andrew McCallum, Amr Ahmed. KDD 2019.
gHHC Code for: Gradient-based Hierarchical Clustering using Continuous Representations of Trees in Hyperbolic Space. Nicholas Monath, Manzil Zaheer, D

CVE-2021-22986 & F5 BIG-IP RCE
Vuln Impact This vulnerability allows for unauthenticated attackers with network access to the iControl REST interface, through the BIG-IP management
TextField: Learning A Deep Direction Field for Irregular Scene Text Detection (TIP 2019)
TextField: Learning A Deep Direction Field for Irregular Scene Text Detection Introduction The code and trained models of: TextField: Learning A Deep
[CIKM 2019] Code and dataset for "Fi-GNN: Modeling Feature Interactions via Graph Neural Networks for CTR Prediction"
FiGNN for CTR prediction The code and data for our paper in CIKM2019: Fi-GNN: Modeling Feature Interactions via Graph Neural Networks for CTR Predicti

ProxyLogon(CVE-2021-26855+CVE-2021-27065) Exchange Server RCE(SSRF-GetWebShell)
ProxyLogon For Python3 ProxyLogon(CVE-2021-26855+CVE-2021-27065) Exchange Server RCE(SSRF-GetWebShell) usage: python ProxyLogon.py --host=exchang
Sudo Baron Samedit Exploit
CVE-2021-3156 (Sudo Baron Samedit) This repository is CVE-2021-3156 exploit targeting Linux x64. For writeup, please visit https://datafarm-cybersecur
CVE-2021-26855: PoC (Not a HoneyPoC for once!)
Exch-CVE-2021-26855 ProxyLogon is the formally generic name for CVE-2021-26855, a vulnerability on Microsoft Exchange Server that allows an attacker b

ProxyLogon Full Exploit Chain PoC (CVE-2021–26855, CVE-2021–26857, CVE-2021–26858, CVE-2021–27065)
ExProlog ProxyLogon Full Exploit Chain PoC (CVE-2021–26855, CVE-2021–26857, CVE-2021–26858, CVE-2021–27065) Usage: exprolog.py [OPTIONS] ExProlog -
ProxyLogon Pre-Auth SSRF To Arbitrary File Write
ProxyLogon Pre-Auth SSRF To Arbitrary File Write For Education and Research Usage: C:\python proxylogon.py mail.evil.corp [email protected] At
PoC for CVE-2021-26855 -Just a checker-
CVE-2021-26855 PoC for CVE-2021-26855 -Just a checker- Usage python3 CVE-2021-26855.py -u https://mail.example.com -c example.burpcollaborator.net # C

An official implementation of "SFNet: Learning Object-aware Semantic Correspondence" (CVPR 2019, TPAMI 2020) in PyTorch.
PyTorch implementation of SFNet This is the implementation of the paper "SFNet: Learning Object-aware Semantic Correspondence". For more information,
PoC of proxylogon chain SSRF(CVE-2021-26855) to write file by testanull, censored by github
CVE-2021-26855 PoC of proxylogon chain SSRF(CVE-2021-26855) to write file by testanull, censored by github Why does github remove this exploit because

Microsoft Exchange Server SSRF漏洞(CVE-2021-26855)
Microsoft_Exchange_Server_SSRF_CVE-2021-26855 zoomeye dork:app:"Microsoft Exchange Server" 使用Seebug工具箱及pocsuite3编写的脚本Microsoft_Exchange_Server_SSRF_CV
CVE-2021-26855 SSRF Exchange Server
CVE-2021-26855 Brute Force EMail Exchange Server Timeline: Monday, March 8, 2021: Update Dumping content...(I'm not done, can u guy help me done this

带回显版本的漏洞利用脚本
CVE-2021-21978 带回显版本的漏洞利用脚本,更简单的方式 0. 漏洞信息 VMware View Planner Web管理界面存在一个上传日志功能文件的入口,没有进行认证且写入的日志文件路径用户可控,通过覆盖上传日志功能文件log_upload_wsgi.py,即可实现RCE 漏洞代码

威胁情报播报
Threat-Broadcast 威胁情报播报 运行环境 项目介绍 从以下公开的威胁情报来源爬取并整合最新信息: 360:https://cert.360.cn/warning 奇安信:https://ti.qianxin.com/advisory/ 红后:https://redqueen.tj-u

com_media allowed paths that are not intended for image uploads to RCE
CVE-2021-23132 com_media allowed paths that are not intended for image uploads to RCE. CVE-2020-24597 Directory traversal in com_media to RCE Two CVEs

Vulmap 是一款 web 漏洞扫描和验证工具, 可对 webapps 进行漏洞扫描, 并且具备漏洞利用功能
Vulmap 是一款 web 漏洞扫描和验证工具, 可对 webapps 进行漏洞扫描, 并且具备漏洞利用功能

Proof of Concept Exploit for vCenter CVE-2021-21972
CVE-2021-21972 Proof of Concept Exploit for vCenter CVE-2021-21972
CVE-2021-21972
CVE-2021-21972 % python3 /tmp/CVE_2021_21972.py -i /tmp/urls.txt -n 8 -e [*] Creating tmp.tar containing ../../../../../home/vsphere-ui/.ssh/authoriz
Exploit for CVE-2021-3129
laravel-exploits Exploit for CVE-2021-3129
Gitlab RCE - Remote Code Execution
Gitlab RCE - Remote Code Execution RCE for old gitlab version = 11.4.7 & 12.4.0-12.8.1 LFI for old gitlab versions 10.4 - 12.8.1 This is an exploit f
Update of uncaptcha2 from 2019
YouTube Video Proof of Concept I created a new YouTube Video with technical Explanation for breaking Google's Audio reCAPTCHAs: Click on the image bel

PoC for CVE-2020-6207 (Missing Authentication Check in SAP Solution Manager)
PoC for CVE-2020-6207 (Missing Authentication Check in SAP Solution Manager) This script allows to check and exploit missing authentication checks in

DNSpooq - dnsmasq cache poisoning (CVE-2020-25686, CVE-2020-25684, CVE-2020-25685)
dnspooq DNSpooq PoC - dnsmasq cache poisoning (CVE-2020-25686, CVE-2020-25684, CVE-2020-25685) For educational purposes only Requirements Docker compo

an impacket-dependent script exploiting CVE-2019-1040
dcpwn an impacket-dependent script exploiting CVE-2019-1040, with code partly borrowed from those security researchers that I'd like to say thanks to.
WebLogic T3/IIOP RCE ExternalizableHelper.class of coherence.jar
CVE-2020-14756 WebLogic T3/IIOP RCE ExternalizableHelper.class of coherence.jar README project base on https://github.com/Y4er/CVE-2020-2555 and weblo
S2-061 的payload,以及对应简单的PoC/Exp
S2-061 脚本皆根据vulhub的struts2-059/061漏洞测试环境来写的,不具普遍性,还望大佬多多指教 struts2-061-poc.py(可执行简单系统命令) 用法:python struts2-061-poc.py http://ip:port command 例子:python
Apache Flink 目录遍历漏洞批量检测 (CVE-2020-17519)
使用方法&免责声明 该脚本为Apache Flink 目录遍历漏洞批量检测 (CVE-2020-17519)。 使用方法:Python CVE-2020-17519.py urls.txt urls.txt 中每个url为一行,漏洞地址输出在vul.txt中 影响版本: Apache Flink 1

Python JIRA Library is the easiest way to automate JIRA. Support for py27 was dropped on 2019-10-14, do not raise bugs related to it.
Jira Python Library This library eases the use of the Jira REST API from Python and it has been used in production for years. As this is an open-sourc
Backtest 1000s of minute-by-minute trading algorithms for training AI with automated pricing data from: IEX, Tradier and FinViz. Datasets and trading performance automatically published to S3 for building AI training datasets for teaching DNNs how to trade. Runs on Kubernetes and docker-compose. 150 million trading history rows generated from +5000 algorithms. Heads up: Yahoo's Finance API was disabled on 2019-01-03 https://developer.yahoo.com/yql/
Stock Analysis Engine Build and tune investment algorithms for use with artificial intelligence (deep neural networks) with a distributed stack for ru