685 Repositories
Python cve-search Libraries

Spring4Shell Proof Of Concept/And vulnerable application CVE-2022-22965
Spring4Shell-POC (CVE-2022-22965) Spring4Shell (CVE-2022-22965) Proof Of Concept/Information + A vulnerable Tomcat server with a vulnerable spring4she

Dockerized Spring4Shell (CVE-2022-22965) PoC application and exploit
Spring4Shell PoC Application This is a dockerized application that is vulnerable to the Spring4Shell vulnerability (CVE-2022-22965). Full Java source
CVE-2022-22963 PoC
CVE-2022-22963 CVE-2022-22963 PoC Slight modified for English translation and detection of https://github.com/chaosec2021/Spring-cloud-function-SpEL-R
Official implementation of "Path Planning using Neural A* Search" (ICML-21)
Path Planning using Neural A* Search (ICML 2021) This is a repository for the following paper: Ryo Yonetani*, Tatsunori Taniai*, Mohammadamin Barekata

Spring4Shell - Spring Core RCE - CVE-2022-22965
Spring Core RCE - CVE-2022-22965 After Spring Cloud, on March 29, another heavyweight vulnerability of Spring broke out on the Internet: Spring Core R

One line to host them all. Bootstrap your image search case in minutes.
One line to host them all. Bootstrap your image search case in minutes. Survey NOW gives the world access to customized neural image search in just on

Explorer is a Autonomous (self-hosted) Bittorrent Network Search Engine.
Explorer Explorer is a Autonomous (self-hosted) Bittorrent Network Search Engine. About The Project Screenshots Supported features Number Feature 1 DH
A Safer PoC for CVE-2022-22965 (Spring4Shell)
Safer_PoC_CVE-2022-22965 A Safer PoC for CVE-2022-22965 (Spring4Shell) Functionality Creates a file called CVE_2022-22965_exploited.txt in the tomcat
Exploit and Check Script for CVE 2022-1388
F5-CVE-2022-1388-Exploit Exploit and Check Script for CVE 2022-1388 Usage Check against single host python3 CVE-2022-1388.py -v true -u target_url At

😭 WSOB is a python tool created to exploit the new vulnerability on WSO2 assigned as CVE-2022-29464.
😭 WSOB (CVE-2022-29464) 😭 WSOB is a python tool created to exploit the new vulnerability on WSO2 assigned as CVE-2022-29464. CVE-2022-29464 details:

Display, filter and search log messages in your terminal
Textualog Display, filter and search logging messages in the terminal. This project is powered by rich and textual. Some of the ideas and code in this

Melissa Songs is a telegram bot to easily find songs sending music snippets and search tracks 💃🏽🎵
Find songs on Telegram, like on Shazam... 😎 Open on telegram · Report Bug · Request Feature ⬇️ Installation To get a local copy installed and working
POC for CVE-2022-1388
CVE-2022-1388 POC for CVE-2022-1388 affecting multiple F5 products. Follow the Horizon3.ai Attack Team on Twitter for the latest security research: Ho
H&M Fashion Image similarity search with Weaviate and DocArray
H&M Fashion Image similarity search with Weaviate and DocArray This example shows how to do image similarity search using DocArray and Weaviate as Doc

Optical Character Recognition + Instance Segmentation for russian and english languages
Распознавание рукописного текста в школьных тетрадях Соревнование, проводимое в рамках олимпиады НТО, разработанное Сбером. Платформа ODS. Результаты
![ISNAS-DIP: Image Specific Neural Architecture Search for Deep Image Prior [CVPR 2022]](https://github.com/ozgurkara99/ISNAS-DIP/raw/main/docs/method.jpg)
ISNAS-DIP: Image Specific Neural Architecture Search for Deep Image Prior [CVPR 2022]
ISNAS-DIP: Image-Specific Neural Architecture Search for Deep Image Prior (CVPR 2022) Metin Ersin Arican*, Ozgur Kara*, Gustav Bredell, Ender Konukogl

CVE-2022-1388 F5 BIG-IP iControl REST Auth Bypass RCE
CVE-2022-1388 CVE-2022-1388 F5 BIG-IP iControl REST Auth Bypass RCE. POST /mgmt/tm/util/bash HTTP/1.1 Host: Accept-Encoding: gzip, deflate Accept: */

As-ViT: Auto-scaling Vision Transformers without Training
As-ViT: Auto-scaling Vision Transformers without Training [PDF] Wuyang Chen, Wei Huang, Xianzhi Du, Xiaodan Song, Zhangyang Wang, Denny Zhou In ICLR 2
Framework for evaluating ANNS algorithms on billion scale datasets.
Billion-Scale ANN http://big-ann-benchmarks.com/ Install The only prerequisite is Python (tested with 3.6) and Docker. Works with newer versions of Py
HTTP Protocol Stack Remote Code Execution Vulnerability CVE-2022-21907
CVE-2022-21907 Description POC for CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability. create by antx at 2022-01-17. Detail HTTP

CLIPfa: Connecting Farsi Text and Images
CLIPfa: Connecting Farsi Text and Images OpenAI released the paper Learning Transferable Visual Models From Natural Language Supervision in which they

Red Team Toolkit is an Open-Source Django Offensive Web-App which is keeping the useful offensive tools used in the red-teaming together.
RedTeam Toolkit Note: Only legal activities should be conducted with this project. Red Team Toolkit is an Open-Source Django Offensive Web-App contain
Dome - Subdomain Enumeration Tool. Fast and reliable python script that makes active and/or passive scan to obtain subdomains and search for open ports.
DOME - A subdomain enumeration tool Check the Spanish Version Dome is a fast and reliable python script that makes active and/or passive scan to obtai

CVE-2022-22965 : about spring core rce
CVE-2022-22965: Spring-Core-Rce EXP 特性: 漏洞探测(不写入 webshell,简单字符串输出) 自定义写入 webshell 文件名称及路径 不会追加写入到同一文件中,每次检测写入到不同名称 webshell 文件 支持写入 冰蝎 webshell 代理支持,可

LightHuBERT: Lightweight and Configurable Speech Representation Learning with Once-for-All Hidden-Unit BERT
LightHuBERT LightHuBERT: Lightweight and Configurable Speech Representation Learning with Once-for-All Hidden-Unit BERT | Github | Huggingface | SUPER
Dieser Scanner findet Websites, die nicht direkt in Suchmaschinen auftauchen, aber trotzdem erreichbar sind.
Deep Web Scanner Dieses Script findet Websites, die per IPv4-Adresse erreichbar sind und speichert deren Metadaten. Die Ausgabe im Terminal wird nach
CVE-2022-22965 - CVE-2010-1622 redux
CVE-2022-22965 - vulnerable app and PoC Trial & error $ docker rm -f rce; docker build -t rce:latest . && docker run -d -p 8080:8080 --name rce rce:la

S2-062 (CVE-2021-31805) / S2-061 / S2-059 RCE
CVE-2021-31805 Remote code execution S2-062 (CVE-2021-31805) Due to Apache Struts2's incomplete fix for S2-061 (CVE-2020-17530), some tag attributes c

SIGIR'22 paper: Axiomatically Regularized Pre-training for Ad hoc Search
Introduction This codebase contains source-code of the Python-based implementation (ARES) of our SIGIR 2022 paper. Chen, Jia, et al. "Axiomatically Re

A Human-in-the-Loop workflow for creating HD images from text
A Human-in-the-Loop? workflow for creating HD images from text DALL·E Flow is an interactive workflow for generating high-definition images from text
Laravel RCE (CVE-2021-3129)
CVE-2021-3129 - Laravel RCE About The script has been made for exploiting the Laravel RCE (CVE-2021-3129) vulnerability. This script allows you to wri

PSTR: End-to-End One-Step Person Search With Transformers (CVPR2022)
PSTR (CVPR2022) This code is an official implementation of "PSTR: End-to-End One-Step Person Search With Transformers (CVPR2022)". End-to-end one-step

Spring-0day/CVE-2022-22965
CVE-2022-22965 Spring Framework/CVE-2022-22965 Vulnerability ID: CVE-2022-22965/CNVD-2022-23942/QVD-2022-1691 Reproduce the vulnerability docker pull
![[arXiv22] Disentangled Representation Learning for Text-Video Retrieval](https://github.com/foolwood/DRL/raw/main/demo/pipeline.png)
[arXiv22] Disentangled Representation Learning for Text-Video Retrieval
Disentangled Representation Learning for Text-Video Retrieval This is a PyTorch implementation of the paper Disentangled Representation Learning for T
A tool to make easy to search for directories in the URL.
Welcome to Brutos Directory Scanner 🚀 The Brutos is a python script used to provide agility in obtaining verifications to informations about related

Ensemble Knowledge Guided Sub-network Search and Fine-tuning for Filter Pruning
Ensemble Knowledge Guided Sub-network Search and Fine-tuning for Filter Pruning This repository is official Tensorflow implementation of paper: Ensemb

spring-cloud-gateway-rce CVE-2022-22947
Spring Cloud Gateway Actuator API SpEL表达式注入命令执行(CVE-2022-22947) 1.installation pip3 install -r requirements.txt 2.Usage $ python3 spring-cloud-gateway
Spring Cloud Gateway 3.0.7 & 3.1.1 Code Injection (RCE)
Spring Cloud Gateway 3.0.7 & 3.1.1 Code Injection (RCE) CVE: CVE-2022-22947 CVSS: 10.0 (Vmware - https://tanzu.vmware.com/security/cve-2022-22947)
GEP (GDB Enhanced Prompt) - a GDB plug-in for GDB command prompt with fzf history search, fish-like autosuggestions, auto-completion with floating window, partial string matching in history, and more!
GEP (GDB Enhanced Prompt) GEP (GDB Enhanced Prompt) is a GDB plug-in which make your GDB command prompt more convenient and flexibility. Why I need th

Grape - A webbrowser with its own Search Engine
Grape 🔎 A Web Browser made entirely in python. Search Engine 🔎 Installation: F

Cve-2022-23131 - Cve-2022-23131 zabbix-saml-bypass-exp
cve-2022-23131 cve-2022-23131 zabbix-saml-bypass-exp replace [zbx_signed_session
Udacity's CS101: Intro to Computer Science - Building a Search Engine
Udacity's CS101: Intro to Computer Science - Building a Search Engine All soluti
CVE-2022-22536 - SAP memory pipes(MPI) desynchronization vulnerability CVE-2022-22536
CVE-2022-22536 SAP memory pipes desynchronization vulnerability(MPI) CVE-2022-22
Sploitus - Command line search tool for sploitus.com. Think searchsploit, but with more POCs
Sploitus Command line search tool for sploitus.com. Think searchsploit, but with
Kroomsa: A search engine for the curious
Kroomsa A search engine for the curious. It is a search algorithm designed to en
Py-instant-search-redis - Source code example for how to build an instant search with redis in python
py-instant-search-redis Source code example for how to build an instant search (

CVE-2022-23046 - SQL Injection Vulnerability on PhpIPAM v1.4.4
CVE-2022-23046 PhpIPAM v1.4.4 allows an authenticated admin user to inject SQL s
GEA - Code for Guided Evolution for Neural Architecture Search
Efficient Guided Evolution for Neural Architecture Search Usage Create a conda e

EmailAll - a powerful Email Collect tool
EmailAll A powerful Email Collect tool 0x1 介绍 😲 EmailAll is a powerful Email Co

B2EA: An Evolutionary Algorithm Assisted by Two Bayesian Optimization Modules for Neural Architecture Search
B2EA: An Evolutionary Algorithm Assisted by Two Bayesian Optimization Modules for Neural Architecture Search This is the offical implementation of the

Search & download music from a certain streaming service
Search & download music from a certain streaming service
pwncat module that automatically exploits CVE-2021-4034 (pwnkit)
pwncat_pwnkit Introduction The purpose of this module is to attempt to exploit CVE-2021-4034 (pwnkit) on a target when using pwncat. There is no need

DrNAS: Dirichlet Neural Architecture Search
This paper proposes a novel differentiable architecture search method by formulating it into a distribution learning problem. We treat the continuously relaxed architecture mixing weight as random variables, modeled by Dirichlet distribution.
One-Shot Neural Ensemble Architecture Search by Diversity-Guided Search Space Shrinking
One-Shot Neural Ensemble Architecture Search by Diversity-Guided Search Space Shrinking This is an official implementation for NEAS presented in CVPR

CATE: Computation-aware Neural Architecture Encoding with Transformers
CATE: Computation-aware Neural Architecture Encoding with Transformers Code for paper: CATE: Computation-aware Neural Architecture Encoding with Trans
A curated list of automated deep learning (including neural architecture search and hyper-parameter optimization) resources.
Awesome AutoDL A curated list of automated deep learning related resources. Inspired by awesome-deep-vision, awesome-adversarial-machine-learning, awe

SGPT: Multi-billion parameter models for semantic search
SGPT: Multi-billion parameter models for semantic search This repository contains code, results and pre-trained models for the paper SGPT: Multi-billi
Create a semantic search engine with a neural network (i.e. BERT) whose knowledge base can be updated
Create a semantic search engine with a neural network (i.e. BERT) whose knowledge base can be updated. This engine can later be used for downstream tasks in NLP such as Q&A, summarization, generation, and natural language understanding (NLU).
A Python script that can be used to check if a SAP system is affected by CVE-2022-22536
Vulnerability assessment for CVE-2022-22536 This repository contains a Python script that can be used to check if a SAP system is affected by CVE-2022
Geowifi 📡 💘 🌎 Search WiFi geolocation data by BSSID and SSID on different public databases.
Geowifi 📡 💘 🌎 Search WiFi geolocation data by BSSID and SSID on different public databases.
This repository contains python code necessary to replicated the experiments performed in our paper "Invariant Ancestry Search"
InvariantAncestrySearch This repository contains python code necessary to replicated the experiments performed in our paper "Invariant Ancestry Search

FLIght SCheduling OPTimization - a simple optimization library for flight scheduling and related problems in the discrete domain
Fliscopt FLIght SCheduling OPTimization 🛫 or fliscopt is a simple optimization library for flight scheduling and related problems in the discrete dom
An unofficial API for lyricsfreak.com using django and django rest framework.
An unofficial API for lyricsfreak.com using django and django rest framework.

Using A * search algorithm and GBFS search algorithm to solve the Romanian problem
Romanian-problem-using-Astar-and-GBFS Using A * search algorithm and GBFS search algorithm to solve the Romanian problem Romanian problem: The agent i
Basic sort and search algorithms written in python.
Basic sort and search algorithms written in python. These were all developed as part of my Computer Science course to demonstrate understanding so they aren't 100% efficent
Genetic algorithms are heuristic search algorithms inspired by the process that supports the evolution of life.
Genetic algorithms are heuristic search algorithms inspired by the process that supports the evolution of life. The algorithm is designed to replicate the natural selection process to carry generation, i.e. survival of the fittest of beings.
Download Web-10K data by querying Bing Image Search
gpv2-web10k This repository contains the script to download images from the Web-10K dataset. The script takes in a list of queries, queries Bing Image
A chess engine with basic AI capabilities (search for best move using MinMax algorithm)
A chess engine with basic AI capabilities (search for best move using MinMax algorithm)
YouTube-Discord-Bot - Discord Bot to Search YouTube
YouTube Bot Info YouTube Bot is a discord bot where you can search for anything
TG-searcherBot - Search any channel/chat from keyword
TG-searcherBot Search any channel/chat from keyword. Commands /start - Starts th

PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1
CVE-2021-45897 PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1 This vulnerability was repor
PortSwigger Burp Plugin for the Log4j (CVE-2021-44228)
yLog4j This is Y-Sec's @PortSwigger Burp Plugin for the Log4j CVE-2021-44228 vulnerability. The focus of yLog4j is to support mass-scanning of the Log
8 Puzzle with A* , Greedy & BFS Search in Python
8_Puzzle 8 Puzzle with A* , Greedy & BFS Search in Python Python Install Python from here. Pip Install pip from here. How to run? 🚀 Install 8_Puzzle
Searches the word list in Wordle based on search pattern.
Wordle Searcher Searches the word list in Wordle based on search pattern. Warning: like all forms of cheating, it trivializes the game, and robs you o

Search stock images (e.g. via Unsplash) and save them to your Wagtail image library.
Wagtail Stock Images Search stock images (e.g. via Unsplash) and save them to your Wagtail image library. Requirements Python 3 Django = 2 Wagtail =
Tensorflow Implementation of A Generative Flow for Text-to-Speech via Monotonic Alignment Search
Tensorflow Implementation of A Generative Flow for Text-to-Speech via Monotonic Alignment Search
The following links explain a bit the idea of semantic search and how search mechanisms work by doing retrieve and rerank
Main Idea The following links explain a bit the idea of semantic search and how search mechanisms work by doing retrieve and rerank Semantic Search Re
Debugging with Stack Overflow: Web Search Behavior in Novice and Expert Programmers
Debugging with Stack Overflow: ICSE SEET, 2022 This is the GitHub repository associated with the 2022 ICSE SEET paper, Debugging with Stack Overflow:
![Pytorch implementation code for [Neural Architecture Search for Spiking Neural Networks]](https://user-images.githubusercontent.com/41351363/142759748-50d0e9bf-4654-4831-97eb-5bfb4d30c21e.png)
Pytorch implementation code for [Neural Architecture Search for Spiking Neural Networks]
Neural Architecture Search for Spiking Neural Networks Pytorch implementation code for [Neural Architecture Search for Spiking Neural Networks] (https
This code is part of the reproducibility package for the SANER 2022 paper "Generating Clarifying Questions for Query Refinement in Source Code Search".
Clarifying Questions for Query Refinement in Source Code Search This code is part of the reproducibility package for the SANER 2022 paper "Generating
Semantic code search implementation using Tensorflow framework and the source code data from the CodeSearchNet project
Semantic Code Search Semantic code search implementation using Tensorflow framework and the source code data from the CodeSearchNet project. The model

DropNAS: Grouped Operation Dropout for Differentiable Architecture Search
DropNAS: Grouped Operation Dropout for Differentiable Architecture Search DropNAS, a grouped operation dropout method for one-level DARTS, with better
TightVNC Vulnerability.
CVE-2022-23967 In TightVNC 1.3.10, there is an integer signedness error and resultant heap-based buffer overflow in InitialiseRFBConnection in rfbprot
Weaviate demo with the text2vec-openai module
Weaviate demo with the text2vec-openai module This repository contains an example of how to use the Weaviate text2vec-openai module. When using this d
Reverse-ikea-image-search - A simple image of ikea search using jina.ai
IKEA Reverse Image Search This is a demo project to fetch ikea product images(IK
Canim1 - Simple python tool to search for packages without m1 wheels in poetry lockfiles
canim1 Usage Clone the repo. Run poetry install. Then you can use the tool: ❯ po

This is a simple PoC for the newly found Polkit error names PwnKit
A Python3 and a BASH PoC for CVE-2021-4034 by Kim Schulz
Python exploit code for CVE-2021-4034 (pwnkit)
Python3 code to exploit CVE-2021-4034 (PWNKIT). This was an exercise in "can I make this work in Python?", and not meant as a robust exploit. It Works
Postgres full text search options (tsearch, trigram) examples
postgres-full-text-search Postgres full text search options (tsearch, trigram) examples. Create DB CREATE DATABASE ftdb; To feed db with an example

DeepCO3: Deep Instance Co-segmentation by Co-peak Search and Co-saliency
[CVPR19] DeepCO3: Deep Instance Co-segmentation by Co-peak Search and Co-saliency (Oral paper) Authors: Kuang-Jui Hsu, Yen-Yu Lin, Yung-Yu Chuang PDF:
CVE-2022-21907 Vulnerability PoC
CVE-2022-21907 Description POC for CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability. create by antx at 2022-01-17, just some sm
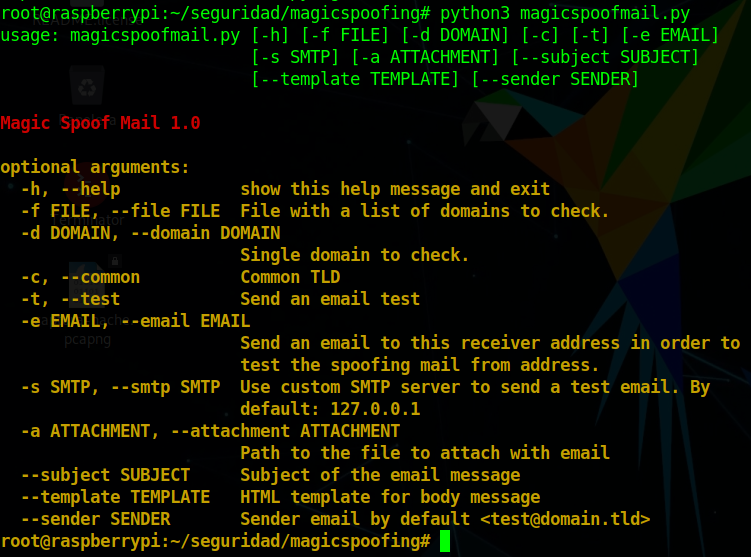
Magicspoofing - A python3 script for search possible misconfiguration in a DNS related to security protections of email service from the domain name
A python3 script for search possible misconfiguration in a DNS related to security protections of email service from the domain name. This project is for educational use, we are not responsible for its misuse.
A fast, efficiency python package for searching and getting search results with many different search engines
search A fast, efficiency python package for searching and getting search results with many different search engines. Installation To install the pack
A Simple Telegram Inline Torrent Search Bot by @infotechIT
Torrent-Search-RoBot A Simple Telegram Inline Torrent Search Bot by @infotechIT. Torrent API Using api.infotech.wtf API Host Bot Deploy to Heroku Clic

GNES enables large-scale index and semantic search for text-to-text, image-to-image, video-to-video and any-to-any content form
GNES is Generic Neural Elastic Search, a cloud-native semantic search system based on deep neural network.
This repository detects a system vulnerable to CVE-2022-21907 and protects against this vulnerability if desired
This repository detects a system vulnerable to CVE-2022-21907 and protects against this vulnerability if desired

Proof of concept of CVE-2022-21907 Double Free in http.sys driver, triggering a kernel crash on IIS servers
CVE-2022-21907 - Double Free in http.sys driver Summary An unauthenticated attacker can send an HTTP request with an "Accept-Encoding" HTTP request he

This project is an Algorithm Visualizer where a user can visualize algorithms like Bubble Sort, Merge Sort, Quick Sort, Selection Sort, Linear Search and Binary Search.
Algo_Visualizer This project is an Algorithm Visualizer where a user can visualize common algorithms like "Bubble Sort", "Merge Sort", "Quick Sort", "
Used Logistic Regression, Random Forest, and XGBoost to predict the outcome of Search & Destroy games from the Call of Duty World League for the 2018 and 2019 seasons.
Call of Duty World League: Search & Destroy Outcome Predictions Growing up as an avid Call of Duty player, I was always curious about what factors led

Cross-modal Retrieval using Transformer Encoder Reasoning Networks (TERN). With use of Metric Learning and FAISS for fast similarity search on GPU
Cross-modal Retrieval using Transformer Encoder Reasoning Networks This project reimplements the idea from "Transformer Reasoning Network for Image-Te