100 Repositories
Python Grafana-0Day-Vuln-POC Libraries

Dockerized Spring4Shell (CVE-2022-22965) PoC application and exploit
Spring4Shell PoC Application This is a dockerized application that is vulnerable to the Spring4Shell vulnerability (CVE-2022-22965). Full Java source
Everything I needed to understand what was going on with "Spring4Shell" - translated source materials, exploit, links to demo apps, and more.
springcore-0day-en These are all my notes from the alleged confirmed! 0day dropped on 2022-03-29. This vulnerability is commonly referred to as "Sprin
CVE-2022-22963 PoC
CVE-2022-22963 CVE-2022-22963 PoC Slight modified for English translation and detection of https://github.com/chaosec2021/Spring-cloud-function-SpEL-R

Pocsploit is a lightweight, flexible and novel open source poc verification framework
Pocsploit is a lightweight, flexible and novel open source poc verification framework
A Safer PoC for CVE-2022-22965 (Spring4Shell)
Safer_PoC_CVE-2022-22965 A Safer PoC for CVE-2022-22965 (Spring4Shell) Functionality Creates a file called CVE_2022-22965_exploited.txt in the tomcat
POC for CVE-2022-1388
CVE-2022-1388 POC for CVE-2022-1388 affecting multiple F5 products. Follow the Horizon3.ai Attack Team on Twitter for the latest security research: Ho

Spring-0day/CVE-2022-22965
CVE-2022-22965 Spring Framework/CVE-2022-22965 Vulnerability ID: CVE-2022-22965/CNVD-2022-23942/QVD-2022-1691 Reproduce the vulnerability docker pull
Backend app for visualizing CANedge log files in Grafana (directly from local disk or S3)
CANedge Grafana Backend - Visualize CAN/LIN Data in Dashboards This project enables easy dashboard visualization of log files from the CANedge CAN/LIN
Files related to PoC||GTFO 21:21 - NSA’s Backdoor of the PX1000-Cr
Files related to PoC||GTFO 21:21 - NSA’s Backdoor of the PX1000-Cr 64bit2key.py

Backup dc registry - A simple POC that abuses Backup Operator privileges to remote dump SAM, SYSTEM, and SECURITY
Backup Operator Registry Backup to Domain Compromise A simple POC that abuses Ba
AnonStress-Stored-XSS-Exploit - An exploit and demonstration on how to exploit a Stored XSS vulnerability in anonstress
AnonStress Stored XSS Exploit An exploit and demonstration on how to exploit a S

Automatically capture your Ookla Speedtest metrics and display them in a Grafana dashboard
Speedtest All-In-One Automatically capture your Ookla Speedtest metrics and display them in a Grafana dashboard. Getting Started About This Code This

PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1
CVE-2021-45897 PoC for CVE-2021-45897 aka SCRMBT-#180 - RCE via Email-Templates (Authenticated only) in SuiteCRM = 8.0.1 This vulnerability was repor
Piglet-shaders - PoC of custom shaders for Piglet
Piglet custom shader PoC This is a PoC for compiling Piglet fragment shaders usi

This is a simple PoC for the newly found Polkit error names PwnKit
A Python3 and a BASH PoC for CVE-2021-4034 by Kim Schulz
Simple tool downloads public PoC (refer from nomi-sec)
PoC Collection This is the little script to collect the proof-of-concept which is refered from nomi-sec. The repository now is only develop for linux-
CVE-2022-21907 Vulnerability PoC
CVE-2022-21907 Description POC for CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability. create by antx at 2022-01-17, just some sm

Proof of concept of CVE-2022-21907 Double Free in http.sys driver, triggering a kernel crash on IIS servers
CVE-2022-21907 - Double Free in http.sys driver Summary An unauthenticated attacker can send an HTTP request with an "Accept-Encoding" HTTP request he
POC of CVE-2021-26084, which is Atlassian Confluence Server OGNL Pre-Auth RCE Injection Vulneralibity.
CVE-2021-26084 Description POC of CVE-2021-26084, which is Atlassian Confluence Server OGNL(Object-Graph Navigation Language) Pre-Auth RCE Injection V

JWT Key Confusion PoC (CVE-2015-9235) Written for the Hack the Box challenge - Under Construction
JWT Key Confusion PoC (CVE-2015-9235) Written for the Hack the Box challenge - Under Construction This script performs a Java Web Token Key Confusion

Automated tool to find & created Exploit Poc for Clickjacking Vulnerability
ClickJackPoc This tool will help you automate finding Clickjacking Vulnerability by just passing a file containing list of Targets . Once the Target i
Bug Alert: a service for alerting security and IT professionals of high-impact and 0day vulnerabilities
Bug Alert Bug Alert is a service for alerting security and IT professionals of h
⚡ PoC: Hide a c&c botnet in the discord client. (Proof Of Concept)
Discord-BotnetClient Embed C&C botnet into the discord client. Working trought websocket c&c server. How to use. pip3 install websocket_server colored
Details,PoC and patches for CVE-2021-45383 & CVE-2021-45384
CVE-2021-45383 & CVE-2021-45384 There are several network-layer vulnerabilities in the official server of Minecraft: Bedrock Edition (aka Bedrock Serv

Small project demonstrating the use of Grafana and InfluxDB for monitoring the speed of an internet connection
Speedtest monitor for Grafana A small project that allows internet speed monitoring using Grafana, InfluxDB 2 and Speedtest. Demo Requirements Docker

MS-FSRVP coercion abuse PoC
ShadowCoerce MS-FSRVP coercion abuse PoC Credits: Gilles LIONEL (a.k.a. Topotam)

Smarthome Dashboard with Grafana & InfluxDB
Smarthome Dashboard with Grafana & InfluxDB This is a complete overhaul of my Raspberry Dashboard done with Flask. I switched from sqlite to InfluxDB
PoC encrypted diary in Python 3
Encrypted diary Sample program to store confidential data. Provides encryption in the form of AES-256 with bcrypt KDF. Does not provide authentication

Vuln Scanner With Python
VulnScanner Features Web Application Firewall (WAF) detection. Cross Site Scripting (XSS) tests. SQL injection time based test. SQL injection error ba
A flexible data historian based on InfluxDB, Grafana, MQTT and more. Free, open, simple.
Kotori Telemetry data acquisition and sensor networks for humans. Documentation: https://getkotori.org/ Source Code: https://github.com/daq-tools/koto
proof-of-concept running docker container from omero web
docker-from-omero-poc proof-of-concept running docker container from omero web How-to Edit test_script.py so that the BaseClient is created pointing t
log4j2 dos exploit,CVE-2021-45105 exploit,Denial of Service poc
说明 about author: 我超怕的 blog: https://www.cnblogs.com/iAmSoScArEd/ github: https://github.com/iAmSOScArEd/ date: 2021-12-20 log4j2 dos exploit log4j2 do
Get MODBUS data from Sofar (K-TLX) inverter through LSW-3 or LSE module
SOFAR Inverter + LSW-3/LSE Small utility to read data from SOFAR K-TLX inverters through the Solarman (LSW-3/LSE) datalogger. Two scripts to get inver

Log4j vuln fuzz/scan with python
Log4jFuzz log4j vuln fuzz/scan USE // it's use localhost udp server to check target vuln. python3 log4jFuzz.py [option] optional arguments: -u URL,
A small POC plugin for launching dumpulator emulation within IDA, passing it addresses from your IDA view using the context menu.
Dumpulator-IDA Currently proof-of-concept This project is a small POC plugin for launching dumpulator emulation within IDA, passing it addresses from
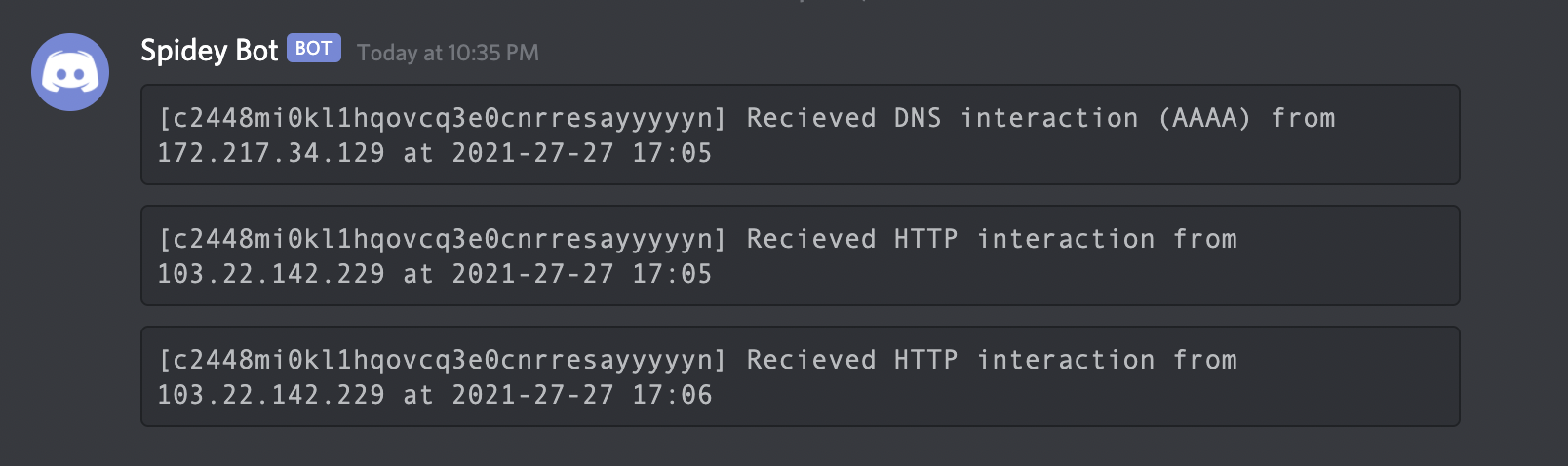
POC for detecting the Log4Shell (Log4J RCE) vulnerability
Interactsh An OOB interaction gathering server and client library Features • Usage • Interactsh Client • Interactsh Server • Interactsh Integration •
Log4j minecraft with python
Apache-Log4j Apache Log4j 远程代码执行 攻击者可直接构造恶意请求,触发远程代码执行漏洞。漏洞利用无需特殊配置,经阿里云安全团队验证,Apache Struts2、Apache Solr、Apache Druid、Apache Flink等均受影响 Steps 【Import
POC for detecting the Log4Shell (Log4J RCE) vulnerability.
log4shell-poc-py POC for detecting the Log4Shell (Log4J RCE) vulnerability. Run on a system with python3 python3 log4shell-poc.py pathToTargetFile

Log4j rce test environment and poc
log4jpwn log4j rce test environment See: https://www.lunasec.io/docs/blog/log4j-zero-day/ Experiments to trigger in various software products mentione
Log4j JNDI inj. vuln scanner
Log-4-JAM - Log 4 Just Another Mess Log4j JNDI inj. vuln scanner Requirements pip3 install requests_toolbelt Usage # make sure target list has http/ht
A Docker based LDAP RCE exploit demo for CVE-2021-44228 Log4Shell
log4j-poc An LDAP RCE exploit for CVE-2021-44228 Log4Shell Description This demo Tomcat 8 server has a vulnerable app deployed on it and is also vulne
An All-In-One Pure Python PoC for CVE-2021-44228
Python Log4RCE An all-in-one pure Python3 PoC for CVE-2021-44228. Configure Replace the global variables at the top of the script to your configuratio

This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798).
CVE-2021-43798 – Grafana Exploit About This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798
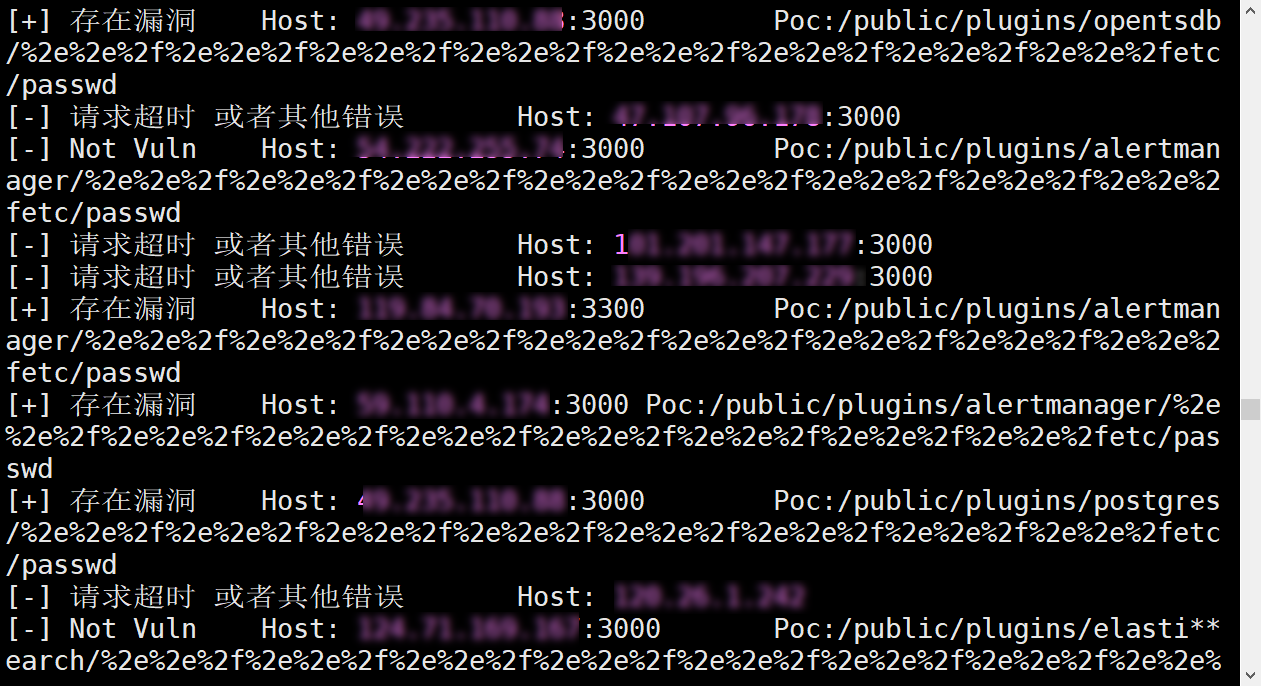
CVE-2021-43798Exp多线程批量验证脚本
Grafana V8.*任意文件读取Exp--多线程批量验证脚本 漏洞描述 Grafana是一个开源的度量分析与可视化套件。经常被用作基础设施的时间序列数据和应用程序分析的可视化,它在其他领域也被广泛的使用包括工业传感器、家庭自动化、天气和过程控制等。其 8.*版本任意文件读取漏洞,该漏洞目前为0d
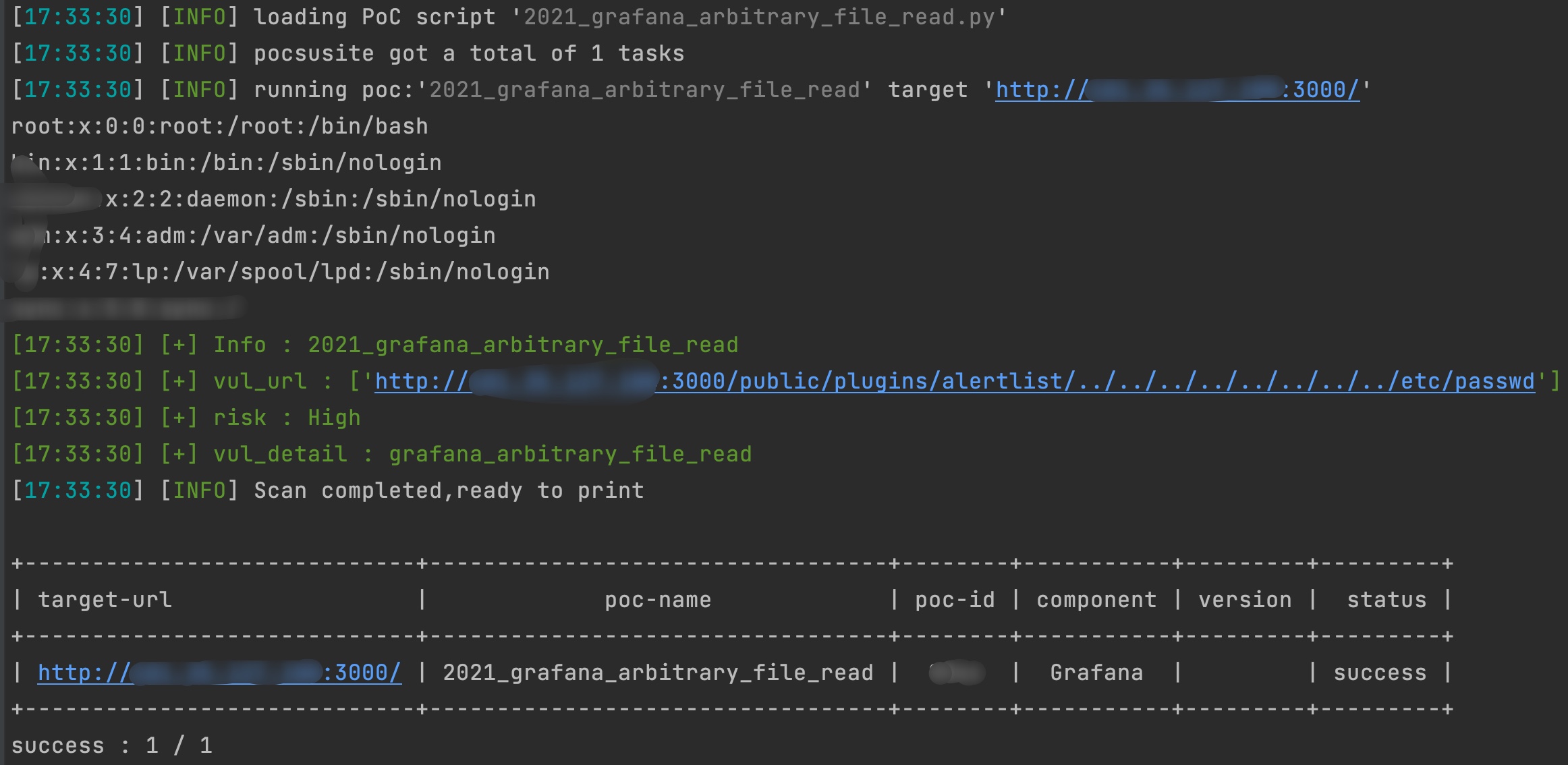
2021 grafana arbitrary file read
2021_grafana_arbitrary_file_read base on pocsuite3 try 40 default plugins of grafana alertlist annolist barchart cloudwatch dashlist elasticsearch gra
Grafana-POC(CVE-2021-43798)
Grafana-Poc 此工具请勿用于违法用途。 一、使用方法:python3 grafana_hole.py 在domain.txt中填入ip:port 二、漏洞影响范围 影响版本: Grafana 8.0.0 - 8.3.0 安全版本: Grafana 8.3.1, 8.2.7, 8.1.8,

Fetching Cryptocurrency Prices from Coingecko and Displaying them on Grafana
cryptocurrency-prices-grafana Fetching Cryptocurrency Prices from Coingecko and Displaying them on Grafana About This stack consists of: Prometheus (t

OpenSource Poc && Vulnerable-Target Storage Box.
reapoc OpenSource Poc && Vulnerable-Target Storage Box. We are aming to collect different normalized poc and the vulerable target to verify it. Now re
Proof of concept to check if hosts are vulnerable to CVE-2021-41773
CVE-2021-41773 PoC Proof of concept to check if hosts are vulnerable to CVE-2021-41773. Description (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CV
Exploit grafana Pre-Auth LFI
Grafana-LFI-8.x Exploit grafana Pre-Auth LFI How to use python3
POC using subprocess lib in Python 🐍
POC subprocess ☞ POC using the subprocess library with Python. References: https://github.com/GuillaumeFalourd/poc-subprocess https://geekflare.com/le
Grafana-0Day-Vuln-POC
Grafana V8.0+版本存在未授权任意文件读取 0Day漏洞 - POC 1 漏洞信息 1.1 基本信息 漏洞厂商:Grafana 厂商官网:https://grafana.com/ 1.2 漏洞描述 Grafana是一个跨平台、开源的数据可视化网络应用程序平台。用户配置连接的数据源之后,Gr
FIVE, Vulnerability Scanner And Mass Exploiter, made for pentesting.
$ FIVE - FIVE is a Pentesting Framework to Test the Security & Integrity of a Website, or Multiple Websites. $ Info FIVE Was Made After Vulnnr to Prod
This is a partial and quick and dirty proof of concept implementation of the following specifications to configure a tor client to use trusted exit relays only.
This is a partial and quick and dirty proof of concept implementation of the following specifications to configure a tor client to use trusted exit re

This is tools hacking for scan vuln in port web, happy using
Xnuvers007 PortInjection this is tools hacking for scan vuln in port web, happy using view/show python 3.9 solo coder (tangerang) 19 y/o installation
A simple cli utility for importing or exporting dashboard json definitions using the Grafana HTTP API.
grafana-dashboard-manager A simple cli utility for importing or exporting dashboard json definitions using the Grafana HTTP API. This may be useful fo
Vulnerability Exploitation Code Collection Repository
Introduction expbox is an exploit code collection repository List CVE-2021-41349 Exchange XSS PoC = Exchange 2013 update 23 = Exchange 2016 update 2

Rundeck / Grafana / Prometheus / Rundeck Exporter integration demo
Rundeck / Prometheus / Grafana integration demo via Rundeck Exporter This is a demo environment that shows how to monitor a Rundeck instance using Run
On the 11/11/21 the apache 2.4.49-2.4.50 remote command execution POC has been published online and this is a loader so that you can mass exploit servers using this.
ApacheRCE ApacheRCE is a small little python script that will allow you to input the apache version 2.4.49-2.4.50 and then input a list of ip addresse

A System Metrics Monitoring Tool Built using Python3 , rabbitmq,Grafana and InfluxDB. Setup using docker compose. Use to monitor system performance with graphical interface of grafana , storage of influxdb and message queuing of rabbitmq
SystemMonitoringRabbitMQGrafanaInflux This repository has code to setup a system monitoring tool The tools used are the follows Python3.6 Docker Rabbi

Home solar infrastructure (with Peimar Inverter) monitoring based on Raspberry Pi 3 B+ using Grafana, InfluxDB, Custom Python Collector and Shelly EM.
raspberry-solar-mon Home solar infrastructure (with Peimar Inverter) monitoring based on Raspberry Pi 3 B+ using Grafana, InfluxDB, Custom Python Coll

the metasploit script(POC) about CVE-2021-36260
CVE-2021-36260-metasploit the metasploit script(POC) about CVE-2021-36260. A command injection vulnerability in the web server of some Hikvision produ
The Timescale NFT Starter Kit is a step-by-step guide to get up and running with collecting, storing, analyzing and visualizing NFT data from OpenSea, using PostgreSQL and TimescaleDB.
Timescale NFT Starter Kit The Timescale NFT Starter Kit is a step-by-step guide to get up and running with collecting, storing, analyzing and visualiz

PoC code for stealing the WiFi password of a network with a Lovebox IOT device connected
LoveBoxer PoC code for stealing the WiFi password of a network with a Lovebox IOT device connected. This PoC was is what I used in this blogpost Usage

A Modified version of TCC's Osprey poc framework......
fierce-fish fierce-fish是由TCC(斗象能力中心)出品并维护的开源漏洞检测框架osprey的改写,去掉臃肿功能的精简版本poc框架 PS:真的用不惯其它臃肿的功能,不过作为一个收集漏洞poc && exp的框架还是非常不错的!!! osprey For beginners fr

POC de uma AWS lambda que executa a consulta de preços de criptomoedas, e é implantada na AWS usando Github actions.
Cryptocurrency Prices Overview Instalação Repositório Configuração CI/CD Roadmap Testes Overview A ideia deste projeto é aplicar o conteúdo estudado s

A PoC Corporation Relationship Knowledge Graph System on top of Nebula Graph.
Corp-Rel is a PoC of Corpartion Relationship Knowledge Graph System. It's built on top of the Open Source Graph Database: Nebula Graph with a dataset
Simple PoC script that allows you to exploit telegram's "send with timer" feature by saving any media sent with this functionality.
Simple PoC script that allows you to exploit telegram's "send with timer" feature by saving any media sent with this functionality.
PoC getting concret intel with chardet and charset-normalizer
aiohttp with charset-normalizer Context aiohttp.TCPConnector(limit=16) alpine linux nginx 1.21 python 3.9 aiohttp dev-master chardet 4.0.0 (aiohttp-ch
Host your Python Discord Bot 24/7 for free. POC
🐉 Pandore 🐉 The easiest and fastest way to host your Python3 Discord Bot 24/7 for free! 📚 Documentation 📚 If you encounter any problem while using

Extract data from ThousandEyes REST API and visualize it on your customized Grafana Dashboard.
ThousandEyes Grafana Dashboard Extract data from the ThousandEyes REST API and visualize it on your customized Grafana Dashboard. Deploy Grafana, Infl

the metasploit script(POC/EXP) about CVE-2021-22005 VMware vCenter Server contains an arbitrary file upload vulnerability
CVE-2021-22005-metasploit the metasploit script(POC/EXP) about CVE-2021-22005 VMware vCenter Server contains an arbitrary file upload vulnerability pr
Phoenix Framework is an environment for writing, testing and using exploit code.
Phoenix-Framework Phoenix Framework is an environment for writing, testing and using exploit code. 🖼 Screenshots 🎪 Community PwnWiki Forums 🔑 Licen

send sms via grafana alert webhook
notifier fire alarm What does this project do: the aim of this project is to send alarm notification from grafana alert manager via kavenegar api. sta
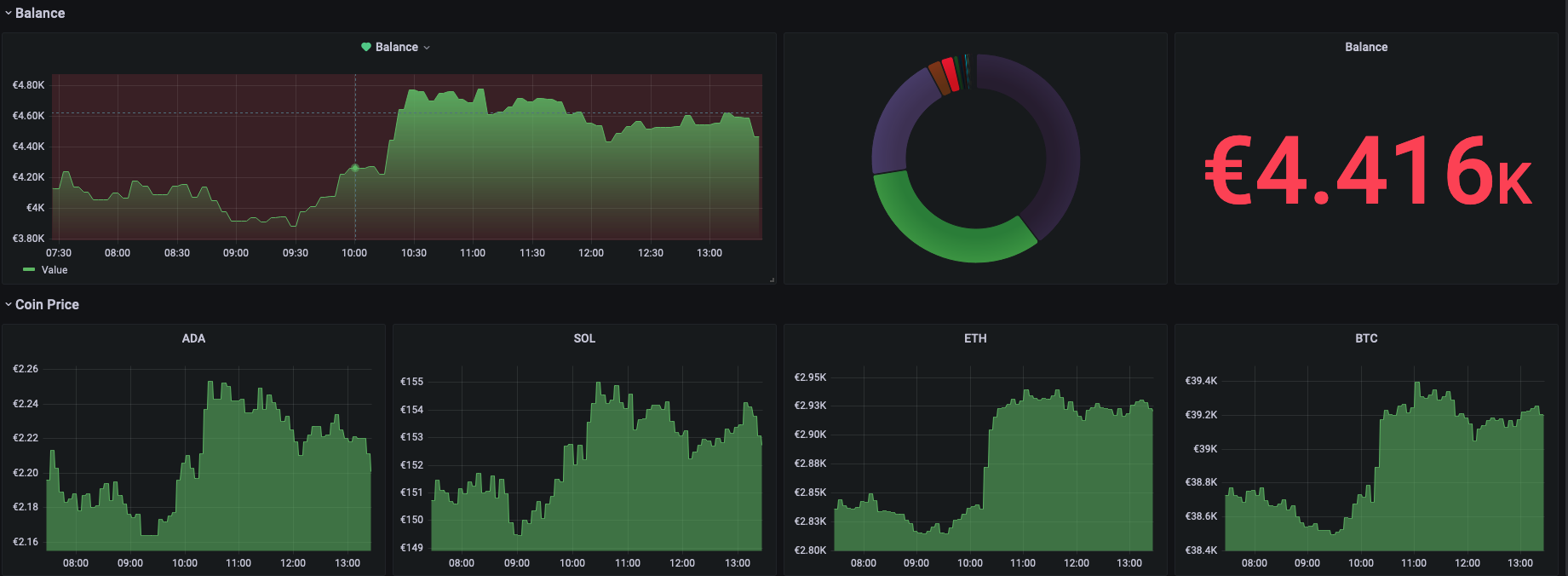
Run with one command grafana, prometheus, and a python script to collect and display cryptocurrency prices and track your wallet balance.
CryptoWatch Track your favorite crypto coin price and your wallet balance. Install Create .env: ADMIN_USER=admin ADMIN_PASSWORD=admin Configure you

CVE-2021-40346 integer overflow enables http smuggling
CVE-2021-40346-POC CVE-2021-40346 integer overflow enables http smuggling Reference: https://jfrog.com/blog/critical-vulnerability-in-haproxy-cve-2021
Discord exploit allowing you to be unbannable.
Discord-Ban-Immunity Discord exploit allowing you to be unbannable. 9/3/2021 Found in late August. Found by Passive and Me. Explanation If a user gets

Watch your Docker registry project size, then monitor it with Grafana.
Watch your Docker registry project size, then monitor it with Grafana.
Now patched 0day for force reseting an accounts password
Animal Jam 0day No-Auth Force Password Reset via API Now patched 0day for force reseting an accounts password Used until patched to cause anarchy. Pro

Übersicht remote command execution 0day exploit
Übersicht RCE 0day Unauthenticated remote command execution 0day exploit for Übersicht. Description Übersicht is a desktop widget application for m

GitScanner is a script to make it easy to search for Exposed Git through an advanced Google search.
GitScanner Legal disclaimer Usage of GitScanner for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to
CURSO PROMETHEUS E GRAFANA: Observability in a real world
Curso de monitoração com o Prometheus Esse curso ensina como usar o Prometheus como uma ferramenta integrada de monitoração, entender seus conceitos,
ProxyShell POC Exploit : Exchange Server RCE (ACL Bypass + EoP + Arbitrary File Write)
ProxyShell Install git clone https://github.com/ktecv2000/ProxyShell cd ProxyShell virtualenv -p $(which python3) venv source venv/bin/activate pip3 i
Uncover the full name of a target on Linkedin.
Revealin Uncover the full name of a target on Linkedin. It's just a little PoC exploiting a design flaw. Useful for OSINT. Screenshot Usage $ git clon

🍃 A comprehensive monitoring and alerting solution for the status of your Chia farmer and harvesters.
chia-monitor A monitoring tool to collect all important metrics from your Chia farming node and connected harvesters. It can send you push notificatio

Python library to decrypt Airtag reports, as well as a InfluxDB/Grafana self-hosted dashboard example
Openhaystack-python This python daemon will allow you to gather your Openhaystack-based airtag reports and display them on a Grafana dashboard. You ca

A Prometheus exporter for monitoring & analyzing Grafana Labs' technical documentation
grafana-docs-exporter A Prometheus exporter for monitoring & analyzing Grafana Labs' technical documentation Here is the public endpoint.

Restful Api developed with Flask using Prometheus and Grafana for monitoring and containerization with Docker :rocket:
Hephaestus 🚀 In Greek mythology, Hephaestus was either the son of Zeus and Hera or he was Hera's parthenogenous child. ... As a smithing god, Hephaes
A bare-bones POC container runner in python
pybox A proof-of-concept bare-bones container written in 50 lines of python code. Provides namespace isolation and resource limit control Usage Insta
A python script and steps to display locations of peers connected to qbittorrent
A python script (along with instructions) to display the locations of all the peers your qBittorrent client is connected to in a Grafana worldmap dash
聚合Github上已有的Poc或者Exp,CVE信息来自CVE官网。Auto Collect Poc Or CVE from Github by CVE ID.
PocOrExp in Github 聚合Github上已有的Poc或者Exp,CVE信息来自CVE官网 注意:只通过通用的CVE号聚合,因此对于MS17-010等Windows编号漏洞以及著名的有绰号的漏洞,还是自己检索一下比较好 Usage python3 exp.py -h usage: ex

ProxyLogon(CVE-2021-26855+CVE-2021-27065) Exchange Server RCE(SSRF-GetWebShell)
ProxyLogon For Python3 ProxyLogon(CVE-2021-26855+CVE-2021-27065) Exchange Server RCE(SSRF-GetWebShell) usage: python ProxyLogon.py --host=exchang
CVE-2021-26855: PoC (Not a HoneyPoC for once!)
Exch-CVE-2021-26855 ProxyLogon is the formally generic name for CVE-2021-26855, a vulnerability on Microsoft Exchange Server that allows an attacker b

ProxyLogon Full Exploit Chain PoC (CVE-2021–26855, CVE-2021–26857, CVE-2021–26858, CVE-2021–27065)
ExProlog ProxyLogon Full Exploit Chain PoC (CVE-2021–26855, CVE-2021–26857, CVE-2021–26858, CVE-2021–27065) Usage: exprolog.py [OPTIONS] ExProlog -
PoC for CVE-2021-26855 -Just a checker-
CVE-2021-26855 PoC for CVE-2021-26855 -Just a checker- Usage python3 CVE-2021-26855.py -u https://mail.example.com -c example.burpcollaborator.net # C
PoC of proxylogon chain SSRF(CVE-2021-26855) to write file by testanull, censored by github
CVE-2021-26855 PoC of proxylogon chain SSRF(CVE-2021-26855) to write file by testanull, censored by github Why does github remove this exploit because

A demo of Prometheus+Grafana for monitoring an ML model served with FastAPI.
ml-monitoring Jeremy Jordan This repository provides an example setup for monitoring an ML system deployed on Kubernetes.

JSON Interoperability Vulnerability Labs
JSON Interoperability Vulnerability Labs Description These are the companion labs to my research article "An Exploration of JSON Interoperability Vuln

PoC for CVE-2020-6207 (Missing Authentication Check in SAP Solution Manager)
PoC for CVE-2020-6207 (Missing Authentication Check in SAP Solution Manager) This script allows to check and exploit missing authentication checks in

Exploit Discord's cache system to remote upload payloads on Discord users machines
Exploit Discord's cache system to hide payloads PoC Remote upload embedded payload from image using EOF to Discord users machines through cache. Depen