318 Repositories
Python memory-hacking Libraries
![[NeurIPS-2020] Self-paced Contrastive Learning with Hybrid Memory for Domain Adaptive Object Re-ID.](https://github.com/yxgeee/SpCL/raw/master/figs/framework.png)
[NeurIPS-2020] Self-paced Contrastive Learning with Hybrid Memory for Domain Adaptive Object Re-ID.
Self-paced Contrastive Learning (SpCL) The official repository for Self-paced Contrastive Learning with Hybrid Memory for Domain Adaptive Object Re-ID
Memory game in Python
Concentration - Memory Game Concentration is a memory game written in Python, inspired by memory-game. Description As stated in the introduction of th
GUI Pancakeswap 2 and Uniswap 3 SNIPER BOT 🥇 🏆 🥇
GUI Pancakeswap V2 and Uniswap V3 trading client (and bot) MOST ADVANCE TRADING BOT SUPPORT WINDOWS LINUX MAC (BUY TOKEN ON LAUNCH)

Find exposed API keys based on RegEx and get exploitation methods for some of keys that are found
dora Features Blazing fast as we are using ripgrep in backend Exploit/PoC steps for many of the API key, allowing to write a good report for bug bount
Article Reranking by Memory-enhanced Key Sentence Matching for Detecting Previously Fact-checked Claims.
MTM This is the official repository of the paper: Article Reranking by Memory-enhanced Key Sentence Matching for Detecting Previously Fact-checked Cla
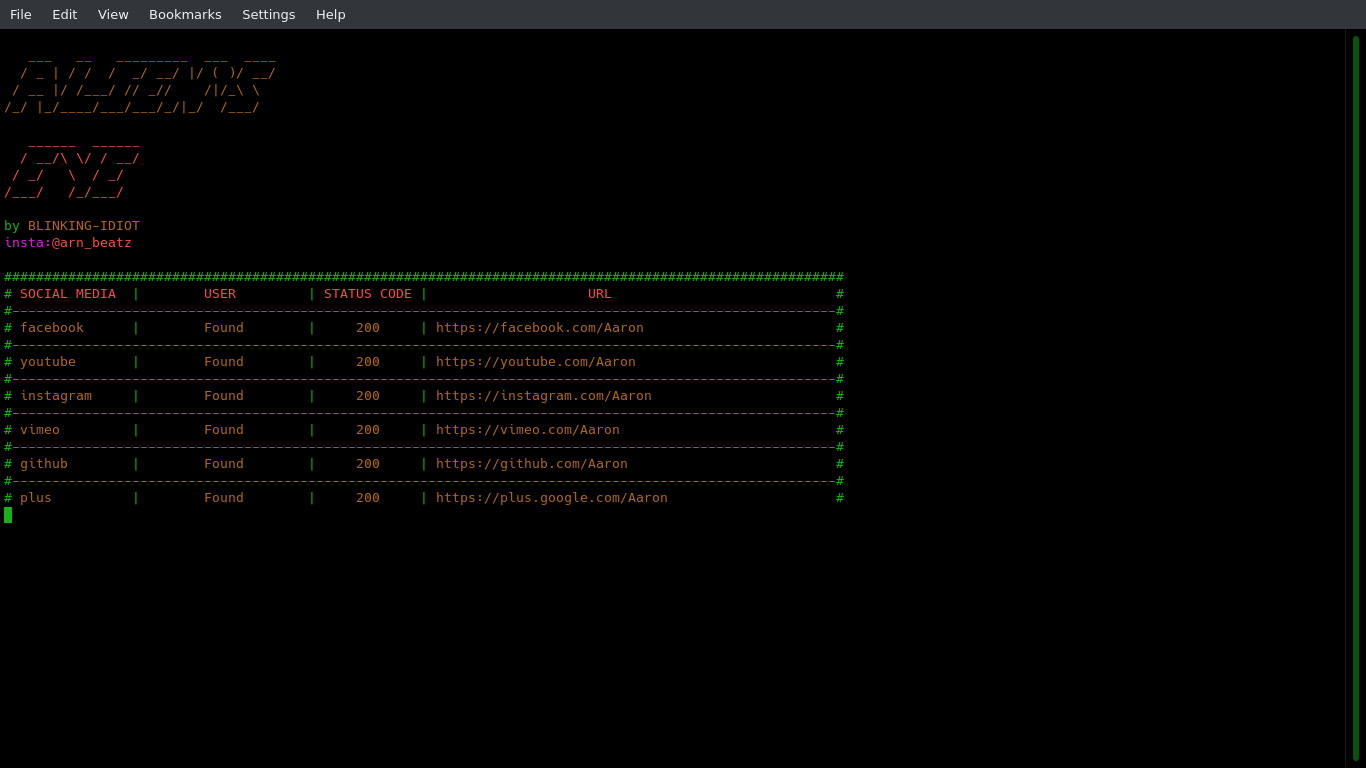
Find all social media accounts with a username!
Aliens_eye FIND ALL SOCIAL MEDIA ACCOUNTS WITH A USERNAME! OSINT To install: Open terminal and type: git clone https://github.com/BLINKING-IDIOT/Alien
Library for Memory Trace Statistics in Python
Memory Search Library for Memory Trace Statistics in Python The library uses tracemalloc as a core module, which is why it is only available for Pytho
A universal memory dumper using Frida
Fridump Fridump (v0.1) is an open source memory dumping tool, primarily aimed to penetration testers and developers. Fridump is using the Frida framew
d4rk Ghost is all in one hacking framework For red team Pentesting
d4rk ghost is all in one Hacking framework For red team Pentesting it contains all modules , information_gathering exploitation + vulnerability scanning + ddos attacks with 12 methods + proxy scraper and wordpress vulnerability scanning and more
Robot Hacking Manual (RHM). From robotics to cybersecurity. Papers, notes and writeups from a journey into robot cybersecurity.
RHM: Robot Hacking Manual Download in PDF RHM v0.4 ┃ Read online The Robot Hacking Manual (RHM) is an introductory series about cybersecurity for robo
Memory Efficient Attention (O(sqrt(n)) for Jax and PyTorch
Memory Efficient Attention This is unofficial implementation of Self-attention Does Not Need O(n^2) Memory for Jax and PyTorch. Implementation is almo
BLEND: A Fast, Memory-Efficient, and Accurate Mechanism to Find Fuzzy Seed Matches
BLEND is a mechanism that can efficiently find fuzzy seed matches between sequences to significantly improve the performance and accuracy while reducing the memory space usage of two important applications: 1) finding overlapping reads and 2) read mapping. Described by Firtina et al.
A Python dictionary implementation designed to act as an in-memory cache for FaaS environments
faas-cache-dict A Python dictionary implementation designed to act as an in-memory cache for FaaS environments. Formally you would describe this a mem
labsecurity is a framework and its use is for ethical hacking and computer security
labsecurity labsecurity is a framework and its use is for ethical hacking and computer security. Warning This tool is only for educational purpose. If
Tools hacking termux in the name ant-attack
Hello friends, I am ama.player0000. Web developer, software, Android command line (termux). (1)=Well, ant-attack tool is a tool to attack sites and disable them. (2)=You can use those CCTV servers, switch controls, slow down WI-FI, send packets around by dongle or hotspot. [*[*[*=I said a very important point at the bottom of the page, be sure to read it !! *]*]*]
Memory-Augmented Model Predictive Control
Memory-Augmented Model Predictive Control This repository hosts the source code for the journal article "Composing MPC with LQR and Neural Networks fo

Buff A simple BOF library I wrote under an hour to help me automate with BOF attack
What is Buff? A simple BOF library I wrote under an hour to help me automate with BOF attack. It comes with fuzzer and a generic method to generate ex

Asyncio cache manager for redis, memcached and memory
aiocache Asyncio cache supporting multiple backends (memory, redis and memcached). This library aims for simplicity over specialization. All caches co

♟️ QR Code display for P4wnP1 (SSH, VNC, any text / URL)
♟️ Display QR Codes on P4wnP1 (p4wnsolo-qr) 🟢 QR Code display for P4wnP1 w/OLED (SSH, VNC, P4wnP1 WebGUI, any text / URL / exfiltrated data) Note: Th

In-memory Graph Database and Knowledge Graph with Natural Language Interface, compatible with Pandas
CogniPy for Pandas - In-memory Graph Database and Knowledge Graph with Natural Language Interface Whats in the box Reasoning, exploration of RDF/OWL,

Official PyTorch implementation of RIO
Image-Level or Object-Level? A Tale of Two Resampling Strategies for Long-Tailed Detection Figure 1: Our proposed Resampling at image-level and obect-

Generate a wordlist to fuzz amounts or any other numerical values.
Generate a wordlist to fuzz amounts or any other numerical values. Based on Common Security Issues in Financially-Oriented Web Applications.
Simples brute forcer de diretorios para web pentest.
🦑 dirbruter Simples brute forcer de diretorios para web pentest. ❕ Atenção Não ataque sites privados. Isto é illegal. 🖥️ Pré-requisitos Ultima versã
A begginer reverse shell tool python.
A begginer tools for hacking. The theme of this repository is to bring some ready-made open-source tools for anyone new to the world of hacking. This
End-To-End Memory Network using Tensorflow
MemN2N Implementation of End-To-End Memory Networks with sklearn-like interface using Tensorflow. Tasks are from the bAbl dataset. Get Started git clo
CC CAMERA HACKING TOOL
CAM-HACK CC CAMERA HACKING TOOL Installation On Termux $ apt update
A begginer reverse shell tool python.
A begginer reverse shell tool python. Este programa é para apenas estudo e conhecimento. Não use isso em outra pessoas. Não me responsabilizo por uso
GUI Pancakeswap V2 and Uniswap V3 trading client (and bot)MOST ADVANCE TRADING BOT SUPPORT WINDOWS LINUX MAC
GUI Pancakeswap 2 and Uniswap 3 trading client (and bot) (MOST ADVANCE TRADING BOT SUPPORT WINDOWS LINUX MAC) UPDATE: MUTI TRADE TOKEN ENABLE ,TRADE 1

Implementation of N-Grammer, augmenting Transformers with latent n-grams, in Pytorch
N-Grammer - Pytorch Implementation of N-Grammer, augmenting Transformers with latent n-grams, in Pytorch Install $ pip install n-grammer-pytorch Usage
NotesToCommands - a fully customizable notes / command template program, allowing users to instantly execute terminal commands
NotesToCommands is a fully customizable notes / command template program, allowing users to instantly execute terminal commands with dynamic arguments grouped into sections in their notes/files. It was originally created for pentesting uses, to avoid the needed remembrance and retyping of sets of commands for various attacks.

Great script for sending and spaming emails! gmail, yahoo, outlook, hotmail.
• License • Issues • Project • Wikipedia • Я не несу ответственности за ваши действия. Скачивая программное обеспечение из этого репозитория, вы согла

This project is created to visualize the system statistics such as memory usage, CPU usage, memory accessible by process and much more using Kibana Dashboard with Elasticsearch.
System Stats Visualizer This project is created to visualize the system statistics such as memory usage, CPU usage, memory accessible by process and m
Tsunami-Fi is simple multi-tool bash application for Wi-Fi attacks
🪴 Tsunami-Fi 🪴 Русская версия README 🌿 Description 🌿 Tsunami-Fi is simple multi-tool bash application for Wi-Fi WPS PixieDust and NullPIN attack,

End-2-end speech synthesis with recurrent neural networks
Introduction New: Interactive demo using Google Colaboratory can be found here TTS-Cube is an end-2-end speech synthesis system that provides a full p

Shell hunter for AF
AF-ShellHunter AF-ShellHunter: Auto shell lookup AF-ShellHunter its a script designed to automate the search of WebShell's in AF Team How to pip3 ins
MTBLLS Ethical Hacking Tool Announcement of v2.0
MTBLLS Ethical Hacking Tool Announcement of v2.0 MTBLLS is a Free and Open-Source Ethical Hacking Tool developed by GhostTD (SkyWtkh) The tool can onl
FIVE, Vulnerability Scanner And Mass Exploiter, made for pentesting.
$ FIVE - FIVE is a Pentesting Framework to Test the Security & Integrity of a Website, or Multiple Websites. $ Info FIVE Was Made After Vulnnr to Prod
Train Dense Passage Retriever (DPR) with a single GPU
Gradient Cached Dense Passage Retrieval Gradient Cached Dense Passage Retrieval (GC-DPR) - is an extension of the original DPR library. We introduce G
A protocol or procedure that connects an ever-changing IP address to a fixed physical machine address
p0znMITM ARP Poisoning Tool What is ARP? Address Resolution Protocol (ARP) is a protocol or procedure that connects an ever-changing IP address to a f

Modified GPT using average pooling to reduce the softmax attention memory constraints.
NLP-GPT-Upsampling This repository contains an implementation of Open AI's GPT Model. In particular, this implementation takes inspiration from the Ny
GUI Pancakeswap2 and Uniswap3 trading client (and bot)
GUI Pancakeswap2 and Uniswap3 trading client (and bot) (MOST ADVANCE TRADING BOT SUPPORT WINDOWS LINUX MAC) (AUTO BUY TOKEN ON LUNCH AFTER ADD LIQUIDI

Fast subdomain scanner, Takes arguments from a Json file ("args.json") and outputs the subdomains.
Fast subdomain scanner, Takes arguments from a Json file ("args.json") and outputs the subdomains. File Structure core/ colors.py db/ wordlist.txt REA
A library for low-memory inferencing in PyTorch.
Pylomin Pylomin (PYtorch LOw-Memory INference) is a library for low-memory inferencing in PyTorch. Installation ... Usage For example, the following c
A simple, lightweight Discord bot running with only 512 MB memory on Heroku
Haruka This used to be a music bot, but people keep using it for NSFW content. Can't everyone be less horny? Bot commands See the built-in help comman

Memory tests solver with using OpenCV
Human Benchmark project This project is OpenCV based programs which are puzzle solvers for 7 different games for https://humanbenchmark.com/. made as
Long Expressive Memory (LEM)
Long Expressive Memory for Sequence Modeling This repository contains the implementation to reproduce the numerical experiments of the paper Long Expr

Prevent `CUDA error: out of memory` in just 1 line of code.
🐨 Koila Koila solves CUDA error: out of memory error painlessly. Fix it with just one line of code, and forget it. 🚀 Features 🙅 Prevents CUDA error
![[IEEE Transactions on Computational Imaging] Self-Gated Memory Recurrent Network for Efficient Scalable HDR Deghosting](https://github.com/Susmit-A/HDRRNN/raw/master/github_images/overview.png)
[IEEE Transactions on Computational Imaging] Self-Gated Memory Recurrent Network for Efficient Scalable HDR Deghosting
Few-shot Deep HDR Deghosting This repository contains code and pretrained models for our paper: Self-Gated Memory Recurrent Network for Efficient Scal
Our implementation used for the MICCAI 2021 FLARE Challenge titled 'Efficient Multi-Organ Segmentation Using SpatialConfiguartion-Net with Low GPU Memory Requirements'.
Efficient Multi-Organ Segmentation Using SpatialConfiguartion-Net with Low GPU Memory Requirements Our implementation used for the MICCAI 2021 FLARE C

NetMiaou is an crossplatform hacking tool that can do reverse shells, send files, create an http server or send and receive tcp packet
NetMiaou is an crossplatform hacking tool that can do reverse shells, send files, create an http server or send and receive tcp packet

This is tools hacking for scan vuln in port web, happy using
Xnuvers007 PortInjection this is tools hacking for scan vuln in port web, happy using view/show python 3.9 solo coder (tangerang) 19 y/o installation
WpDisect is a wordpress hacking tool that finds vulnerabilities in wordpress.
wpdisect WpDisect is a wordpress hacking tool that finds misconfigurations in wordpress. Prerequisites You need to download wordpress in the wpdisect
This repo will have a small amount of Chrome tools that can be used for DFIR, Hacking, Deception, whatever your heart desires.
Chrome-Tools Overview Welcome to the repo. This repo will have a small amount of Chrome tools that can be used for DFIR, Hacking, Deception, whatever

Turdshovel is an interactive CLI tool that allows users to dump objects from .NET memory dumps
Turdshovel Description Turdshovel is an interactive CLI tool that allows users to dump objects from .NET memory dumps without having to fully understa

This is the official PyTorch implementation for "Mesa: A Memory-saving Training Framework for Transformers".
A Memory-saving Training Framework for Transformers This is the official PyTorch implementation for Mesa: A Memory-saving Training Framework for Trans
Colin O'Flynn's Hacakday talk at Remoticon 2021 support repo.
Hardware Hacking Resources This repo holds some of the examples used in Colin's Hardware Hacking talk at Remoticon 2021. You can see the very sketchy
A fast, efficient universal vector embedding utility package.
Magnitude: a fast, simple vector embedding utility library A feature-packed Python package and vector storage file format for utilizing vector embeddi

This is the official PyTorch implementation for "Mesa: A Memory-saving Training Framework for Transformers".
Mesa: A Memory-saving Training Framework for Transformers This is the official PyTorch implementation for Mesa: A Memory-saving Training Framework for

🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.
🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.

This repo contains implementation of different architectures for emotion recognition in conversations.
Emotion Recognition in Conversations Updates 🔥 🔥 🔥 Date Announcements 03/08/2021 🎆 🎆 We have released a new dataset M2H2: A Multimodal Multiparty
ZipFly is a zip archive generator based on zipfile.py
ZipFly is a zip archive generator based on zipfile.py. It was created by Buzon.io to generate very large ZIP archives for immediate sending out to clients, or for writing large ZIP archives without memory inflation.

Like htop (CPU and memory usage), but for your case LEDs. 😄
Like htop (CPU and memory usage), but for your case LEDs. 😄
Una simple herramienta para rastrear IP programada en Python
Spyrod-v2 Una simple herramienta para rastrear IP programada en Python Instalacion apt install git -y cd $HOME git clone https://github.com/Euronymou5
InvTorch: memory-efficient models with invertible functions
InvTorch: Memory-Efficient Invertible Functions This module extends the functionality of torch.utils.checkpoint.checkpoint to work with invertible fun
Code for the paper "Attention Approximates Sparse Distributed Memory"
Attention Approximates Sparse Distributed Memory - Codebase This is all of the code used to run analyses in the paper "Attention Approximates Sparse D

DC540 hacking challenge 0x00005a.
dc540-0x00005a DC540 hacking challenge 0x00005a. PROMOTIONAL VIDEO - WATCH NOW HERE ON YOUTUBE CRITICAL PART 5A VIDEO - WATCH NOW HERE ON YOUTUBE Prio
Ducky Script is the payload language of Hak5 gear.
Ducky Script is the payload language of Hak5 gear. Since its introduction with the USB Rubber Ducky in 2010, Ducky Script has grown in capability while maintaining simplicity. Aided by Bash for logic and conditional operations, Ducky Script provides multi-vector functions for all Hak5 payload platforms.
Collection Of Discord Hacking Tools / Fun Stuff / Exploits That Is Completely Made Using Python.
Venom Collection Of Discord Hacking Tools / Fun Stuff / Exploits That Is Completely Made Using Python. Report Bug · Request Feature Contributing Well,
Demo of using DataLoader to prevent out of memory
Demo of using DataLoader to prevent out of memory
A OSINT tool coded in python
Argus Welcome to Argus, a OSINT tool coded in python. Disclaimer I Am not responsible what you do with the information that is given to you by my tool
Installation of hacking tools
Tools-Spartan This is a program that makes it easy for you to download and install tools used in Kali Linux, there are tons of tools available.
Meilleur outil de hacking Zapp en 2021 pour Termux
WhatsApp-Tool Meilleur outil de hacking Zapp en 2021 pour Termux Cet outil est le seul prennant en compte les dernières mises à jour de WhatsApp. FONC
A customisable game where you have to quickly click on black tiles in order of appearance while avoiding clicking on white squares.
W.I.P-Aim-Memory-Game A customisable game where you have to quickly click on black tiles in order of appearance while avoiding clicking on white squar
A simple python code for hacking profile views
This code for hacking profile views. Not recommended to adding profile views in profile. This code is not illegal code. This code is for beginners.
Xteam All in one Instagram,Android,phishing osint and wifi hacking tool available
Xteam All in one Instagram,Android,phishing osint and wifi hacking tool available
Mr.Holmes is a information gathering tool (OSINT)
🔍 Mr.Holmes Mr.Holmes is a information gathering tool (OSINT). Is main purpose is to gain information about domains,username and phone numbers with t

Facebook account cloning/hacking advanced tool + dictionary attack added | Facebook automation tool
loggef Facebook automation tool, Facebook account hacking and cloning advanced tool + dictionary attack added Warning Use this tool for educational pu
A Simple but Powerful cross-platform port scanning & and network automation tool.
DEDMAP is a Simple but Powerful, Clever and Flexible Cross-Platform Port Scanning tool made with ease to use and convenience in mind. Both TCP
Gmail Accounts Hacking
gmail-hack Gmail Accounts Hacking Gemail-Hack python script for Hack gmail account brute force What is brute force attack? In brute force attack,scrip

A windows post exploitation tool that contains a lot of features for information gathering and more.
Crowbar - A windows post exploitation tool Status - ✔️ This project is now considered finished. Any updates from now on will most likely be new script

Fast pattern fetcher, Takes a URLs list and outputs the URLs which contains the parameters according to the specified pattern.
Fast Pattern Fetcher (fpf) Coded with 3 by HS Devansh Raghav Fast Pattern Fetcher, Takes a URLs list and outputs the URLs which contains the paramete
python's memory-saving dictionary data structure
ConstDict python代替的Dict数据结构 若字典不会增加字段,只读/原字段修改 使用ConstDict可节省内存 Dict()内存主要消耗的地方: 1、Dict扩容机制,预留内存空间 2、Dict也是一个对象,内部会动态维护__dict__,增加slot类属性可以节省内容 节省内存大小
A (completely native) python3 wifi brute-force attack using the 100k most common passwords (2021)
wifi-bf [LINUX ONLY] A (completely native) python3 wifi brute-force attack using the 100k most common passwords (2021) This script is purely for educa

Zero-attacker is an multipurpose hacking tool with over 12 tools
Zero Attacker Zero Attacker is bunch of tools which we made for people.These all tools are for purpose of ethical hacking and discord tools. Who is th

training script for space time memory network
Trainig Script for Space Time Memory Network This codebase implemented training code for Space Time Memory Network with some cyclic features. Requirem
Transform your boring distro into a hacking powerhouse.
Pentizer Transform your boring distro into a hacking powerhouse. Pentizer is a personal project that imports Kali and Parrot repositories in any Debia

SEC'21: Sparse Bitmap Compression for Memory-Efficient Training onthe Edge
Training Deep Learning Models on The Edge Training on the Edge enables continuous learning from new data for deployed neural networks on memory-constr
ICMP Reverse Shell written in Python 3 and with Scapy (backdoor/rev shell)
icmpdoor - ICMP Reverse Shell icmpdoor is an ICMP rev shell written in Python3 and scapy. Tested on Ubuntu 20.04, Debian 10 (Kali Linux), and Windows

Playing memory game is fun and the more harder it is the more challenging it is.
Playing memory game is fun and the more harder it is the more challenging it is. Playing thi sgame make us stress free and also happy. So, I have decided to make a memory Game which people can play while doing work. To pass your time and to be little happy, play this wonderful memory game - **JACKPOT** while doing your work and sitting in front of your computer.
Python Library For Ethical Hacker
Python Library For Ethical Hacker
All in One CRACKER911181's Tool. This Tool For Hacking and Pentesting. 🎭
All in One CRACKER911181's Tool. This Tool For Hacking and Pentesting. 🎭
Space Time Recurrent Memory Network - Pytorch
Space Time Recurrent Memory Network - Pytorch (wip) Implementation of Space Time Recurrent Memory Network, recurrent network competitive with attentio
PyTorch implementation of Memory-based semantic segmentation for off-road unstructured natural environments.
MemSeg: Memory-based semantic segmentation for off-road unstructured natural environments Introduction This repository is a PyTorch implementation of
Harmonic Memory Networks for Graph Completion
HMemNetworks Code and documentation for Harmonic Memory Networks, a series of models for compositionally assembling representations of graph elements

Hacking and Learning consistently for 100 days straight af.
#100DaysOfHacking Hacking and Learning consistently for 100 days straight af. [yes, no breaks except mental-break ones, Obviously.] This Repo is one s
Rasberry Pie GPIO memory game. Press the corresponding key to the lit LED.
RPie-keyboard-game Rasberry Pie GPIO memory game. Press the corresponding key to the lit LED. Randem LED (general output) is lit up on rasberrypi rand
xxnx its a simple smtp tool for mails spaming
xxnx its a simple smtp tool for mails spaming what is smpt? Simple Mail Transfer Protocol or smtp service. The Simple Mail Transfer Protocol (SMTP) is
CPython extension implementing Shared Transactional Memory with native-looking interface
CPython extension implementing Shared Transactional Memory with native-looking interface
Sonoff NSPanel protocol and hacking information. Tasmota Berry driver for NSPanel
NSPanel Hacking Sonoff NSPanel protocol and hacking information and Tasmota Berry driver. NSPanel protocol manual Tasmota driver nspanel.be Installati
Application for easy configuration of swap file and swappiness priority in slackware and others linux distributions.
Swap File Program created with the objective of assisting in the configuration of swap file in Distributions such as Slackware. Required packages: pyt