137 Repositories
Python Red-Key Libraries

DLLirant is a tool to automatize the DLL Hijacking researches on a specified binary.
DLLirant DLLirant is a tool to automatize the DLL Hijacking researches on a specified binary. Live Demo How to install You need to install Visual Stud
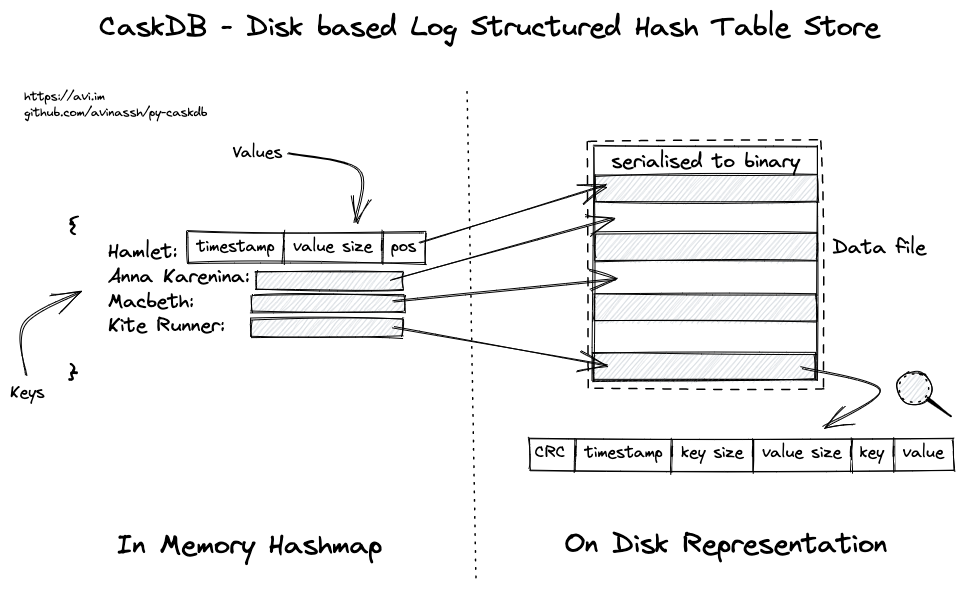
CaskDB is a disk-based, embedded, persistent, key-value store based on the Riak's bitcask paper, written in Python.
CaskDB - Disk based Log Structured Hash Table Store CaskDB is a disk-based, embedded, persistent, key-value store based on the Riak's bitcask paper, w

Red Team Toolkit is an Open-Source Django Offensive Web-App which is keeping the useful offensive tools used in the red-teaming together.
RedTeam Toolkit Note: Only legal activities should be conducted with this project. Red Team Toolkit is an Open-Source Django Offensive Web-App contain
AWS CloudSaga - Simulate security events in AWS
AWS CloudSaga - Simulate security events in AWS AWS CloudSaga is for customers to test security controls and alerts within their Amazon Web Services (
36 key ergo split keyboard, designed around the Seeeduino Xiao platform
Slice36 Minimalist Split Keyboard 36 key ergo split keyboard, designed around the Seeeduino Xiao platform. Inspired by the Corne, Ferris, Ben Vallack'
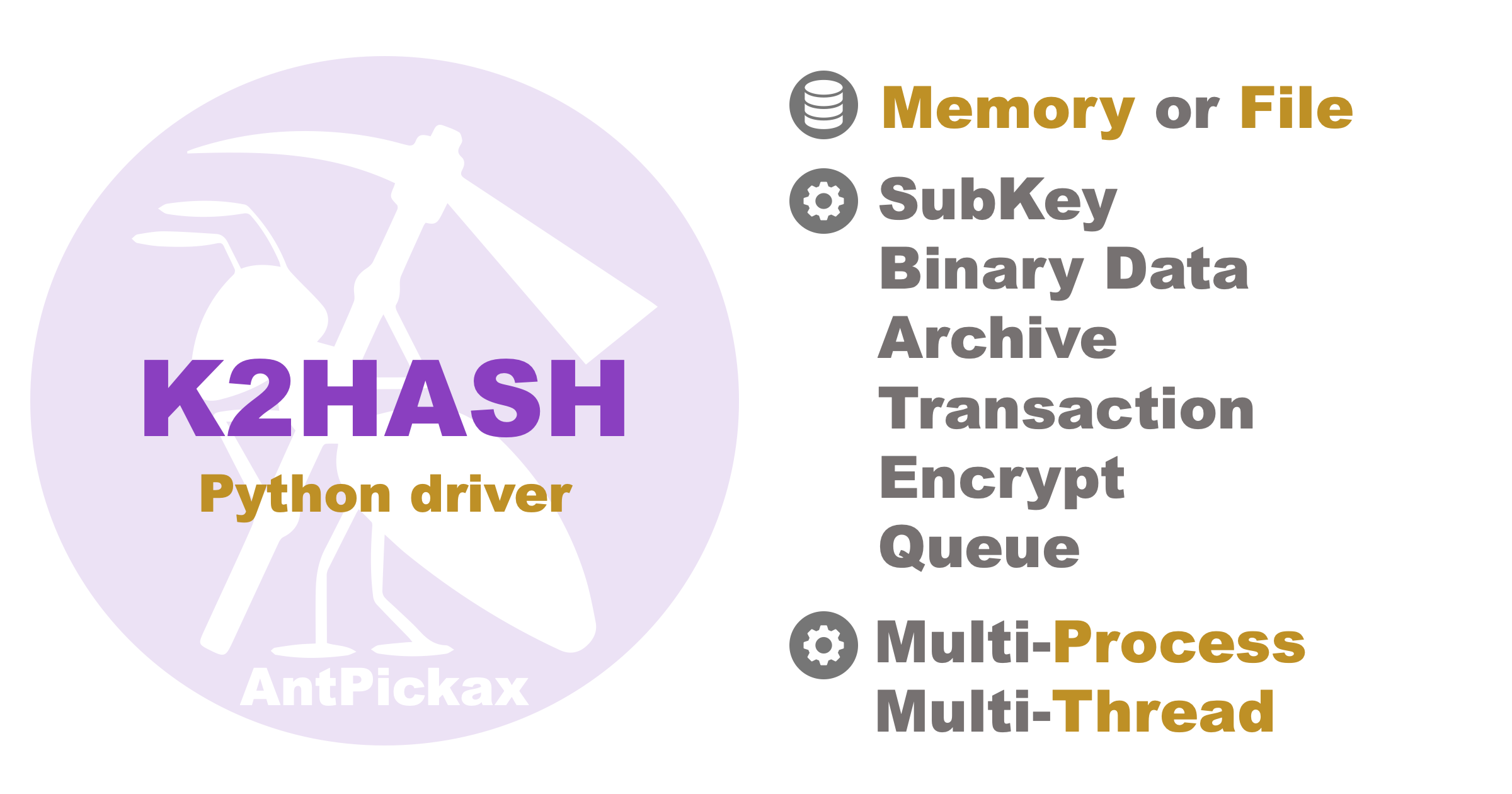
K2HASH Python library - NoSQL Key Value Store(KVS) library
k2hash_python Overview k2hash_python is an official python driver for k2hash. Install Firstly you must install the k2hash shared library: curl -o- htt
The Begin button and menu for the Meadows operating system. The start button for UNIX/Linux.
By: Seanpm2001, Meadows Et; Al. Top README.md Read this article in a different language Sorted by: A-Z Sorting options unavailable ( af Afrikaans Afri
DexterRedTool - Dexter's Red Team Tool that creates cronjob/task scheduler to consistently creates users
DexterRedTool Author: Dexter Delandro CSEC 473 - Spring 2022 This tool persisten
Viperdb - A tiny log-structured key-value database written in pure Python
ViperDB 🐍 ViperDB is a lightweight embedded key-value store written in pure Pyt

Key-control - A tool for add keys to your Termux app
Key-Control Is a tool for add keys to your Termux app. Cara Penginstalan $ pkg u
BROS: A Pre-trained Language Model Focusing on Text and Layout for Better Key Information Extraction from Documents
BROS (BERT Relying On Spatiality) is a pre-trained language model focusing on text and layout for better key information extraction from documents. Given the OCR results of the document image, which are text and bounding box pairs, it can perform various key information extraction tasks, such as extracting an ordered item list from receipts
Credit Card And SK Checker Written In Python
💳 Credit Card Checker (CC Checker) & Mass SK Checker & Generator 💳
A Python implementation of red-black trees
Python red-black trees A Python implementation of red-black trees. This code was originally copied from programiz.com, but I have made a few tweaks to
En- and decrypting text-messages by creating a key with of the fibonacci-sequence
En- and decrypting text-messages by creating a key with of the fibonacci-sequence. This key helps to create mathematical functions, whose zeros should generates the encrypted message.

RedTeam-Security - In this repo you will get the information of Red Team Security related links
OSINT Passive Discovery Amass - https://github.com/OWASP/Amass (Attack Surface M

Wordle-Python - A simple low-key clone of the popular game WORDLE made with python and a 2D Graphics module Pygame
Wordle-Python A simple low-key clone of the popular game WORDLE made with python
Credit Card And SK Checker Written In Python
Credit Card And SK Checker Written In Python
PyCache - simple key:value server written with Python
PyCache simple key:value server written with Python and client is here run server python -m pycache.server or from pycache.server import start_server

This is the key combo trainer for League of Legends and Dota 2 players.
This is the key combo trainer for League of Legends and Dota 2 players. Place the mouse cursor on the blue point and press the key combo from the upper-left side of the screen.
Computer Vision Paper Reviews with Key Summary of paper, End to End Code Practice and Jupyter Notebook converted papers
Computer-Vision-Paper-Reviews Computer Vision Paper Reviews with Key Summary along Papers & Codes. Jonathan Choi 2021 The repository provides 100+ Pap
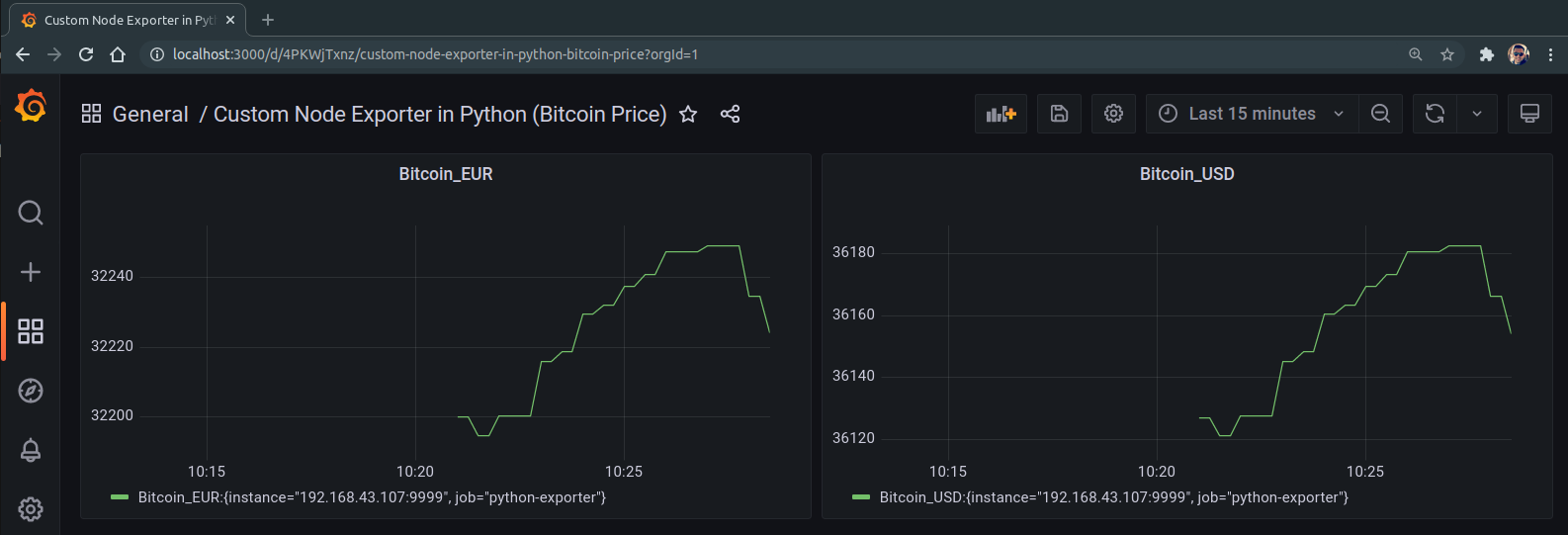
Import some key/value data to Prometheus custom-built Node Exporter in Python
About the app In one particilar project, i had to import some key/value data to Prometheus. So i have decided to create my custom-built Node Exporter
UUID_ApiGenerator - This an API that will return a key-value pair of randomly generated UUID
This an API that will return a key-value pair of randomly generated UUID. Key will be a timestamp and value will be UUID. While the

High-fidelity 3D Model Compression based on Key Spheres
High-fidelity 3D Model Compression based on Key Spheres This repository contains the implementation of the paper: Yuanzhan Li, Yuqi Liu, Yujie Lu, Siy

Code to replicate the key results from Exploring the Limits of Out-of-Distribution Detection
Exploring the Limits of Out-of-Distribution Detection In this repository we're collecting replications for the key experiments in the Exploring the Li
Single Red Blood Cell Hydrodynamic Traps Via the Generative Design
Rbc-traps-generative-design - The generative design for single red clood cell hydrodynamic traps using GEFEST framework

A simple API that will return a key-value pair of randomly generated UUID
A simple API that will return a key-value pair of randomly generated UUID. Key will be a timestamp and value will be UUID. While the server is running, whenever the API is called, it should return all the previous UUIDs ever generated by the API alongside a new UUID.

An open source two key macro-pad modeled to look like a cartoony melting popsicle
macropopsicle An open source two key macro-pad modeled to look like a cartoony melting popsicle. Build instructions Parts List -1x Top case half (3D p
Sukoshi is a proof-of-concept Python implant that leverages the MQTT protocol for C2 and uses AWS IoT Core as infrastructure.
Sukoshi | 少し Overview Sukoshi is a proof-of-concept Python implant that leverages the MQTT protocol for C2 and uses AWS IoT Core as infrastructure. It

JWT Key Confusion PoC (CVE-2015-9235) Written for the Hack the Box challenge - Under Construction
JWT Key Confusion PoC (CVE-2015-9235) Written for the Hack the Box challenge - Under Construction This script performs a Java Web Token Key Confusion
Statistical Random Number Generator Attack Against The Kirchhoff-law-johnson-noise (Kljn) Secure Key Exchange Protocol
Statistical Random Number Generator Attack Against The Kirchhoff-law-johnson-noise (Kljn) Secure Key Exchange Protocol

The Qis|krypt⟩ is a software suite of protocols of quantum cryptography and quantum communications
The Qis|krypt⟩ is a software suite of protocols of quantum cryptography and quantum communications, as well, other protocols and algorithms, built using IBM’s open-source Software Development Kit for quantum computing Qiskit. ⚛️ 🔐

This is a key logger based in python which when executed records all the keystrokes of the system it has been executed on .
This is a key logger based in python which when executed records all the keystrokes of the system it has been executed on
A Simple Key-Value Data-store written in Python
mercury-db This is a File Based Key-Value Datastore that supports basic CRUD (Create, Read, Update, Delete) operations developed using Python. The dat

Automatically download and crop key information from the arxiv daily paper. (cpu version)
Automatically download and crop key information from the arxiv daily paper. (cpu version)
Charged's cogs for Red!
Light-Cogs Charged's cogs for Red! Read below for more information. Features and Cogs TechInfo Lots of commands helping you and your devices! Extended
CryptoApp - Python code to pull wallet balances from a variety of different chains through nothing other than your public key.
CryptoApp - Python code to pull wallet balances from a variety of different chains through nothing other than your public key.
Computer-Vision-Paper-Reviews - Computer Vision Paper Reviews with Key Summary along Papers & Codes
Computer-Vision-Paper-Reviews Computer Vision Paper Reviews with Key Summary along Papers & Codes. Jonathan Choi 2021 50+ Papers across Computer Visio
Key Logger - Key Logger using Python
Key_Logger Key Logger using Python This is the basic Keylogger that i have made
Red-mail - Advanced email sending library for Python
Red Mail Next generation email sender What is it? Red Mail is an advanced email
Python program that uses pynput to simulate key presses. Probably only works on Windows.
AutoKey Python program that uses pynput to simulate key presses. Probably only works on Windows. Can be used for pretty much whatever you want except
Key-Value база данных на Tarantool и REST API к ней.
KVmail Key-Value база данных на Tarantool и REST API к ней. Документация к API доступна здесь. Requiremrnts ubuntu 16.04+ python3.6+ supervisord nginx
Home Assistant component to handle key atom
KeyAtome Home Assistant component to handle key atom, a Linky-compatible device made by Total/Direct-Energie. Installation Either use HACS (default),

Oh-My-PickleDB is an open source key-value store using Python's json module.
OH-MY-PICKLEDB oh-my-pickleDB is a lightweight, fast, and intuitive data manager written in python 📝 Table of Contents About Getting Started Deployme
A python package that computes an optimal motion plan for approaching a red light
redlight_approach redlight_approach is a Python package that computes an optimal motion plan during traffic light approach. RLA_demo.mov Given the par
Project Faros is a reference implimentation of Red Hat OpenShift 4 on small footprint, bare-metal clusters.
Project Faros Project Faros is a reference implimentation of Red Hat OpenShift 4 on small footprint, bare-metal clusters. The project includes referen

Simple encryption-at-rest with key rotation support for Python.
keyring Simple encryption-at-rest with key rotation support for Python. N.B.: keyring is not for encrypting passwords--for that, you should use someth
Simple bitcoin ticker for the Pimorono Inky pHAT Red.
bitcoin-ticker Simple bitcoin ticker for the Pimorono Inky pHAT Red. Equipment Raspberry Pi Zero W v1.1 or Pi 2 model b v1.1 Pimorono Inky pHAT Red (S
The Ultimate Widevine Content Ripper (KEY Extract + Download + Decrypt) is REBORN
NARROWVINE-REBORN ** UPDATE 21.12.01 ** As expected Google patched its ChromeCDM Whitebox exploit by Satsuoni with a force-update on the ChromeCDM. Th
A desktop application developed in Python with PyQt5 to predict demand and help monitor and schedule brewing processes for Barnaby's Brewhouse.
brewhouse-management A desktop application developed in Python with PyQt5 to predict demand and help monitor and schedule brewing processes for Barnab
Article Reranking by Memory-enhanced Key Sentence Matching for Detecting Previously Fact-checked Claims.
MTM This is the official repository of the paper: Article Reranking by Memory-enhanced Key Sentence Matching for Detecting Previously Fact-checked Cla
d4rk Ghost is all in one hacking framework For red team Pentesting
d4rk ghost is all in one Hacking framework For red team Pentesting it contains all modules , information_gathering exploitation + vulnerability scanning + ddos attacks with 12 methods + proxy scraper and wordpress vulnerability scanning and more
Highly decentralized and censorship-resistant way to store key data
Beacon coin Beacon coin is a Chia singelton coin that can store data that needs to be: always available censorship resistant versioned potentially imm

Cogs for Red-DiscordBot
Redbot cogs for Red-DiscordBot authored by Kreusada This is my repository for Red Discord-Bot. I built these cogs because these were the features that
A simple way to create a request to the coinpayment API with a valid HMAC using your private key and command
Coinpayments Verify TXID Created for Astral Discord bot A simple way to create a request to the coinpayment API with a valid HMAC using your private k

Full Spectrum Bioinformatics - a free online text designed to introduce key topics in Bioinformatics using the Python
Full Spectrum Bioinformatics is a free online text designed to introduce key topics in Bioinformatics using the Python programming language. The text is written in interactive Jupyter Notebooks, which allow you to try out and modify example code and analyses.

A Persistent Embedded Graph Database for Python
Cog - Embedded Graph Database for Python cogdb.io New release: 2.0.5! Installing Cog pip install cogdb Cog is a persistent embedded graph database im

Cogs for Red-DiscordBot
matcha-cogs Cogs for Red-DiscordBot. Installation [p]repo add matcha-cogs
Multidict is dict-like collection of key-value pairs where key might be occurred more than once in the container.
multidict Multidict is dict-like collection of key-value pairs where key might be occurred more than once in the container. Introduction HTTP Headers
Python-dotenv reads key-value pairs from a .env file and can set them as environment variables.
python-dotenv Python-dotenv reads key-value pairs from a .env file and can set them as environment variables. It helps in the development of applicati

Redis Python Client - The Python interface to the Redis key-value store.
redis-py The Python interface to the Redis key-value store. Installation | Contributing | Getting Started | Connecting To Redis Installation redis-py
A wrapper for The Movie Database API v3 and v4 that only uses the read access token (not api key).
fulltmdb A wrapper for The Movie Database API v3 and v4 that only uses the read access token (not api key). Installation Use the package manager pip t
Dynamic key remapper for Wayland Window System, especially for Sway
wayremap Dynamic keyboard remapper for Wayland. It works on both X Window Manager and Wayland, but focused on Wayland as it intercepts evdev input and
A Python library to wrap age and minisign to provide key management, encryption/decryption and signing/verification functionality.
A Python library to wrap age and minisign to provide key management, encryption/decryption and signing/verification functionality.
Create Discord Accounts Semi-Automatically Without Captcha Solving API Key
Discord-Account-Generator Create Discord Accounts Semi-Automatically without captcha solving api key IMPORTANT: Your chromedriver version should be th
Sign data using symmetric-key algorithm encryption.
Sign data using symmetric-key algorithm encryption. Validate signed data and identify possible validation errors. Uses sha-(1, 224, 256, 385 and 512)/hmac for signature encryption. Custom hash algorithms are allowed. Useful shortcut functions for signing (and validating) dictionaries and URLs.

A multi-platform HTTP(S) Reverse Shell Server and Client in Python 3
Phantom - A multi-platform HTTP(S) Reverse Shell Server and Client Phantom is a multi-platform HTTP(S) Reverse Shell server and client in Python 3. Bi
This is the face keypoint train code of project face-detection-project
face-key-point-pytorch 1. Data structure The structure of landmarks_jpg is like below: |--landmarks_jpg |----AFW |------AFW_134212_1_0.jpg |------AFW_
New time-based UUID formats which are suited for use as a database key
uuid6 New time-based UUID formats which are suited for use as a database key. This module extends immutable UUID objects (the UUID class) with the fun
A webapp that timestamps key moments in a football clip
A look into what we're building Demo.mp4 Prerequisites Python 3 Node v16+ Steps to run Create a virtual environment. Activate the virtual environment.

Blinder is a tool that will help you simplify the exploitation of blind SQL injection
Blinder Have you found a blind SQL injection? Great! Now you need to export it, but are you too lazy to sort through the values? Most likely,

OpenMMLab Text Detection, Recognition and Understanding Toolbox
Introduction English | 简体中文 MMOCR is an open-source toolbox based on PyTorch and mmdetection for text detection, text recognition, and the correspondi
Use Flask API to wrap Facebook data. Grab the wapper of Facebook public pages without an API key.
Facebook Scraper Use Flask API to wrap Facebook data. Grab the wapper of Facebook public pages without an API key. (Currently working 2021) Setup Befo

Ultra-lightweight human body posture key point CNN model. ModelSize:2.3MB HUAWEI P40 NCNN benchmark: 6ms/img,
Ultralight-SimplePose Support NCNN mobile terminal deployment Based on MXNET(=1.5.1) GLUON(=0.7.0) framework Top-down strategy: The input image is t
AWS Tags As A Database is a Python library using AWS Tags as a Key-Value database.
AWS Tags As A Database is a Python library using AWS Tags as a Key-Value database. This database is completely free* 💸

Python client SDK designed to simplify integrations by automating key generation and certificate enrollment using Venafi machine identity services.
This open source project is community-supported. To report a problem or share an idea, use Issues; and if you have a suggestion for fixing the issue,

Serverless Public Key Infrastructure Framework
Ottr: Serverless Public Key Infrastructure Framework Ottr is a serverless framework for Public Key Infrastructure (PKI) that aims to provide a robust
Code for reproducing key results in the paper "InfoGAN: Interpretable Representation Learning by Information Maximizing Generative Adversarial Nets"
Status: Archive (code is provided as-is, no updates expected) InfoGAN Code for reproducing key results in the paper InfoGAN: Interpretable Representat
Python script to generate Vale linting rules from word usage guidance in the Red Hat Supplementary Style Guide
ssg-vale-rules-gen Python script to generate Vale linting rules from word usage guidance in the Red Hat Supplementary Style Guide. These rules are use
Kats, a kit to analyze time series data, a lightweight, easy-to-use, generalizable, and extendable framework to perform time series analysis, from understanding the key statistics and characteristics, detecting change points and anomalies, to forecasting future trends.
Description Kats is a toolkit to analyze time series data, a lightweight, easy-to-use, and generalizable framework to perform time series analysis. Ti

A small project where I identify notes and key harmonies in a piece of music and use them further to recreate and generate the same piece of music through Python
A small project where I identify notes and key harmonies in a piece of music and use them further to recreate and generate the same piece of music through Python
This is a package that allows you to create a key-value vault for storing variables in a global context
This is a package that allows you to create a key-value vault for storing variables in a global context. It allows you to set up a keyring with pre-defined constants which act as keys for the vault. These constants are then what is stored inside the vault. A key is just a string, but the value that the key is mapped to can be assigned to any type of object in Python. If the object is serializable (like a list or a dict), it can also be writen to a JSON file You can then use a decorator to annotate functions that you want to have use this vault to either store return variables in or to extract variables to be used as input for the function.
Red Light Green Light Robot
Red Light Green Light Robot The primary problem addressed by our project is robotic follower behavior i.e. maintaining distance from a moving target.
test application for the licence key web app.
licence_software_test_app Make sure you set your database values in a .env file to the folder. Install MYSQL connector: pip install mysql-connector-py
A program will generate a eth key pair that has the public key that starts with a defined amount of 0
ETHAdressGenerator This short program will generate a eth key pair that has the public key that starts with a defined amount of 0 Requirements Python
A Simple Python KeyLogger App
✨ Kurulum Uygulamayı bilgisayarınızda kullana bilmek için bazı işlemler yapmanız gerekiyor. Aşağıdaki yönlendirmeleri takip ederek bunu yapabilirsiniz
The project of phase's key role in complex and real NN
Phase-in-NN This is the code for our project at Princeton (co-authors: Yuqi Nie, Hui Yuan). The paper title is: "Neural Network is heterogeneous: Phas
CRI Scrape is a tool for get general info about Italian Red Cross in GAIA Platform
CRI Scrape CRI Scrape is a tool for get general info about Italian Red Cross in GAIA Platform Disclaimer This code is only for educational purpose. So
Structure Information is the Key: Self-Attention RoI Feature Extractor in 3D Object Detection
Structure Information is the Key: Self-Attention RoI Feature Extractor in 3D Object Detection abstract:Unlike 2D object detection where all RoI featur

Automatically download and crop key information from the arxiv daily paper.
Arxiv daily 速览 功能:按关键词筛选arxiv每日最新paper,自动获取摘要,自动截取文中表格和图片。 1 测试环境 Ubuntu 16+ Python3.7 torch 1.9 Colab GPU 2 使用演示 首先下载权重baiduyun 提取码:il87,放置于code/Pars
Pytorch implementation of RED-SDS (NeurIPS 2021).
Recurrent Explicit Duration Switching Dynamical Systems (RED-SDS) This repository contains a reference implementation of RED-SDS, a non-linear state s

Team Enigma at ArgMining 2021 Shared Task: Leveraging Pretrained Language Models for Key Point Matching
Team Enigma at ArgMining 2021 Shared Task: Leveraging Pretrained Language Models for Key Point Matching This is our attempt of the shared task on Quan
Rasberry Pie GPIO memory game. Press the corresponding key to the lit LED.
RPie-keyboard-game Rasberry Pie GPIO memory game. Press the corresponding key to the lit LED. Randem LED (general output) is lit up on rasberrypi rand
A simple Outline Server Access Key Copy and Paste Web Interface
Outline Keychain A simple Outline Server Access Key Copy and Paste Web Interface Developed for key and password export and copy & paste for other Shad
A python implementation of the windows 95 product key check.
Windows 95 Product Key Check Info: This is a python implementation of the windows 95 product key check. This was just a bit of fun and a massive 5 hou

Key information extraction from invoice document with Graph Convolution Network
Key Information Extraction from Scanned Invoices Key information extraction from invoice document with Graph Convolution Network Related blog post fro
Generate Random ETH addresses and Private Keys and Saved to file.
ethgen.py Generate Random ETH addresses and Private Keys and Saved to file. ETH address the file is stored in ETH-address.txt. ETH private keys the fi
D(HE)ater is a security tool can perform DoS attack by enforcing the DHE key exchange.
D(HE)ater D(HE)ater is an attacking tool based on CPU heating in that it forces the ephemeral variant of Diffie-Hellman key exchange (DHE) in given cr
A simple key-based text encryption process that encrypts a string based in a list of characteres pairs.
Simple Cipher Encrypter About | New Features | Exemple | How To Use | License ℹ️ About A simple key-based text encryption process that encrypts a stri

PICK: Processing Key Information Extraction from Documents using Improved Graph Learning-Convolutional Networks
Code for the paper "PICK: Processing Key Information Extraction from Documents using Improved Graph Learning-Convolutional Networks" (ICPR 2020)

Deep Learning Interviews book: Hundreds of fully solved job interview questions from a wide range of key topics in AI.
This book was written for you: an aspiring data scientist with a quantitative background, facing down the gauntlet of the interview process in an increasingly competitive field. For most of you, the interview process is the most significant hurdle between you and a dream job.